Embed presentation
Download to read offline

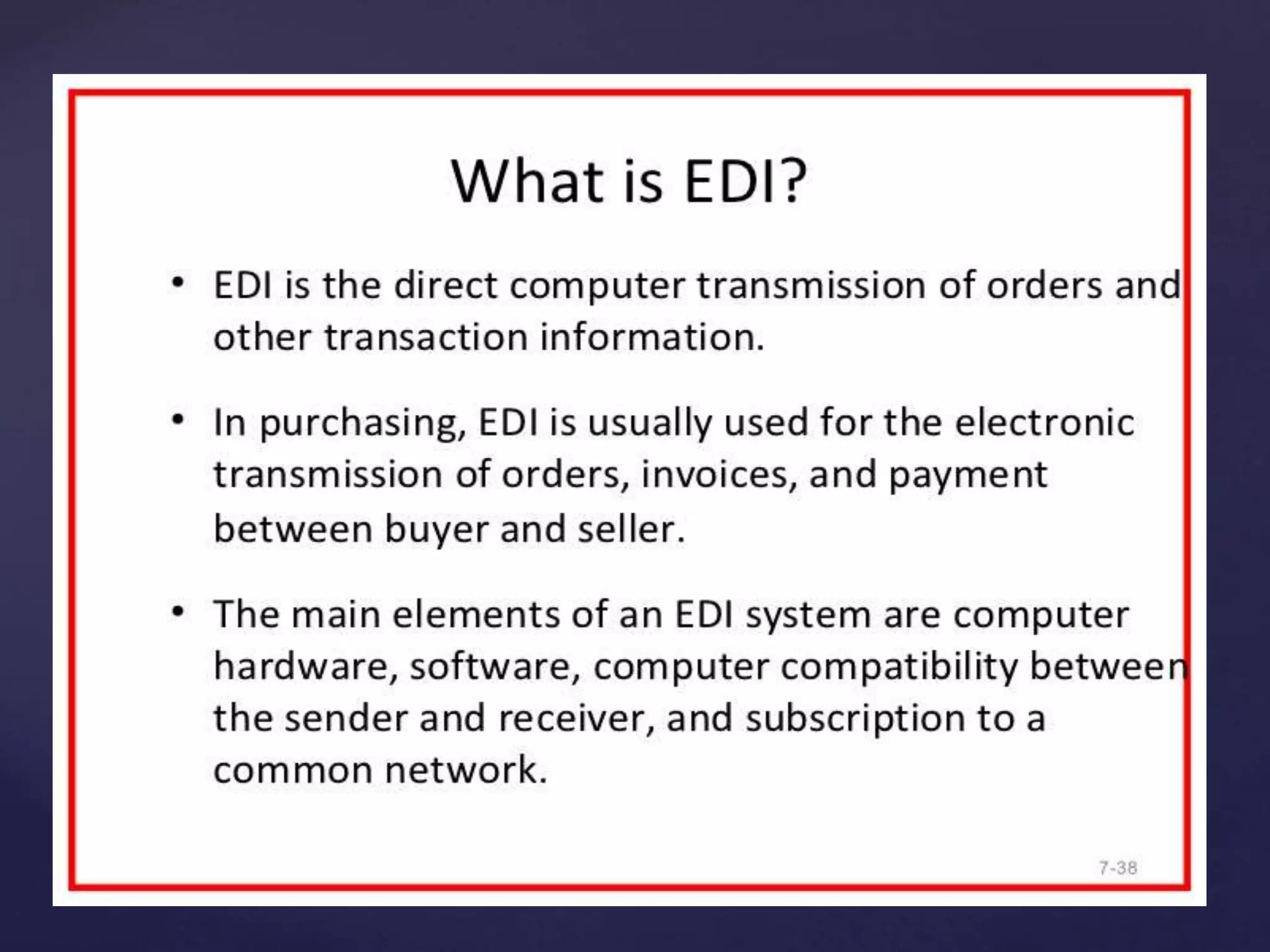
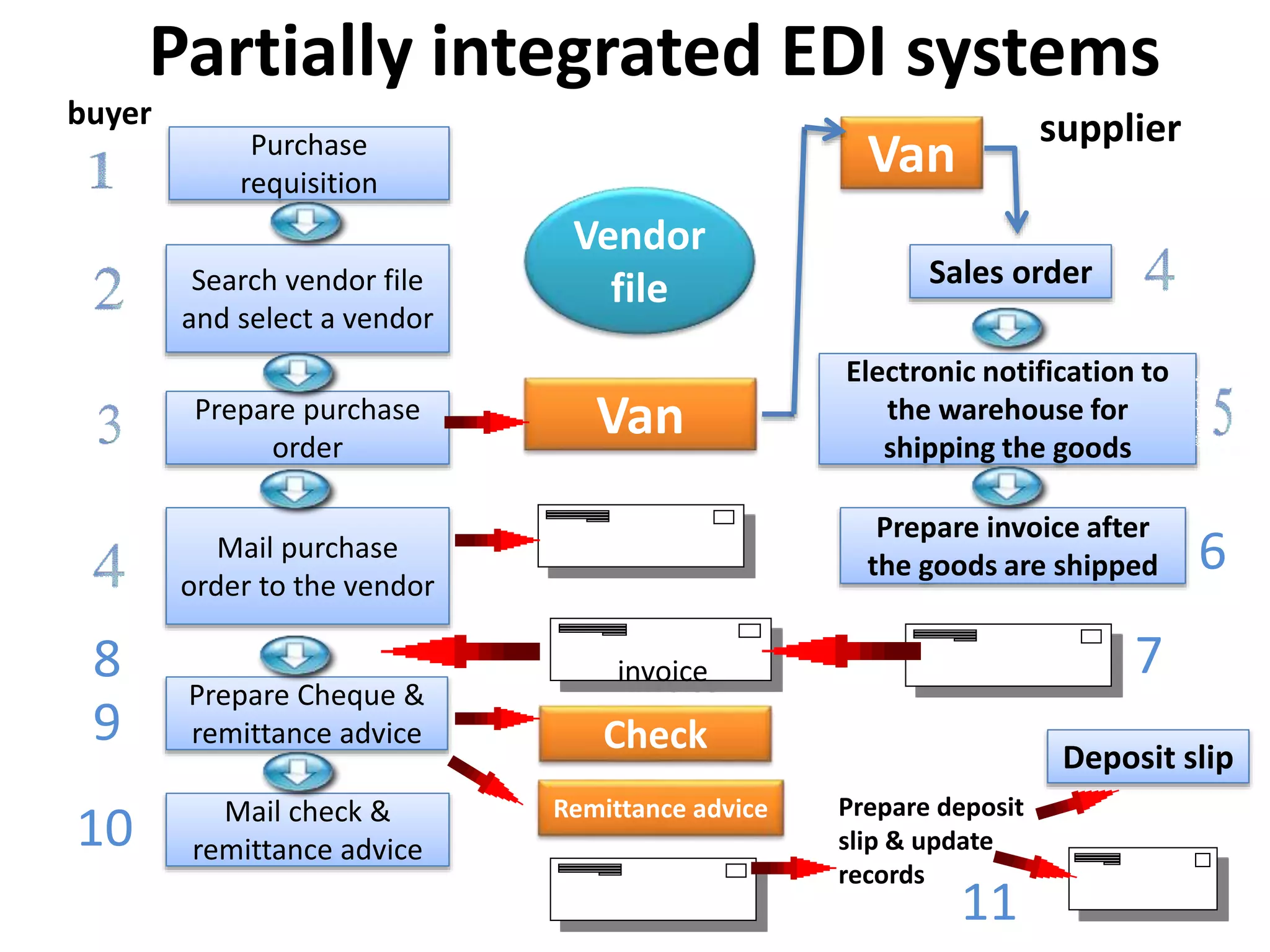
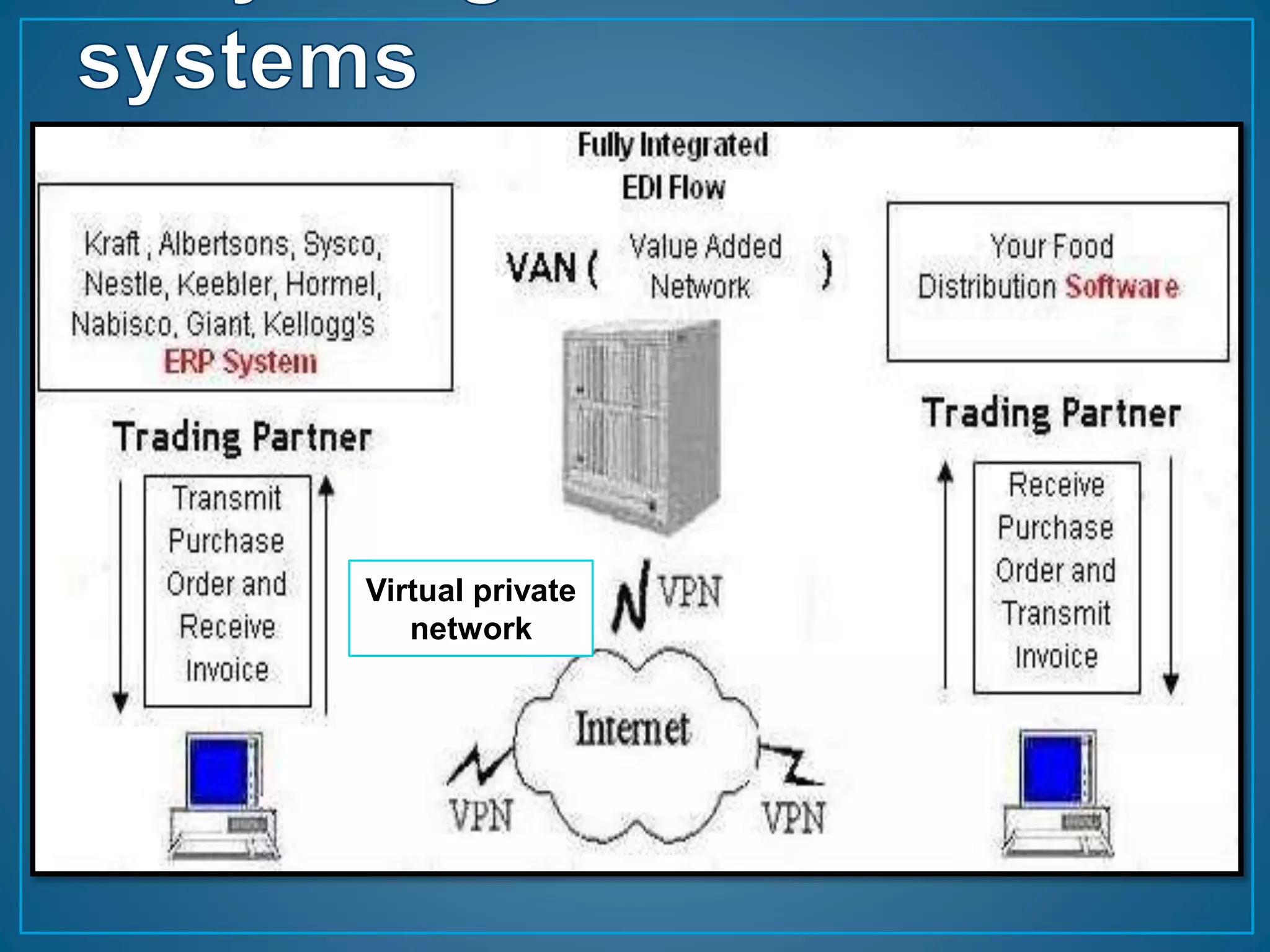

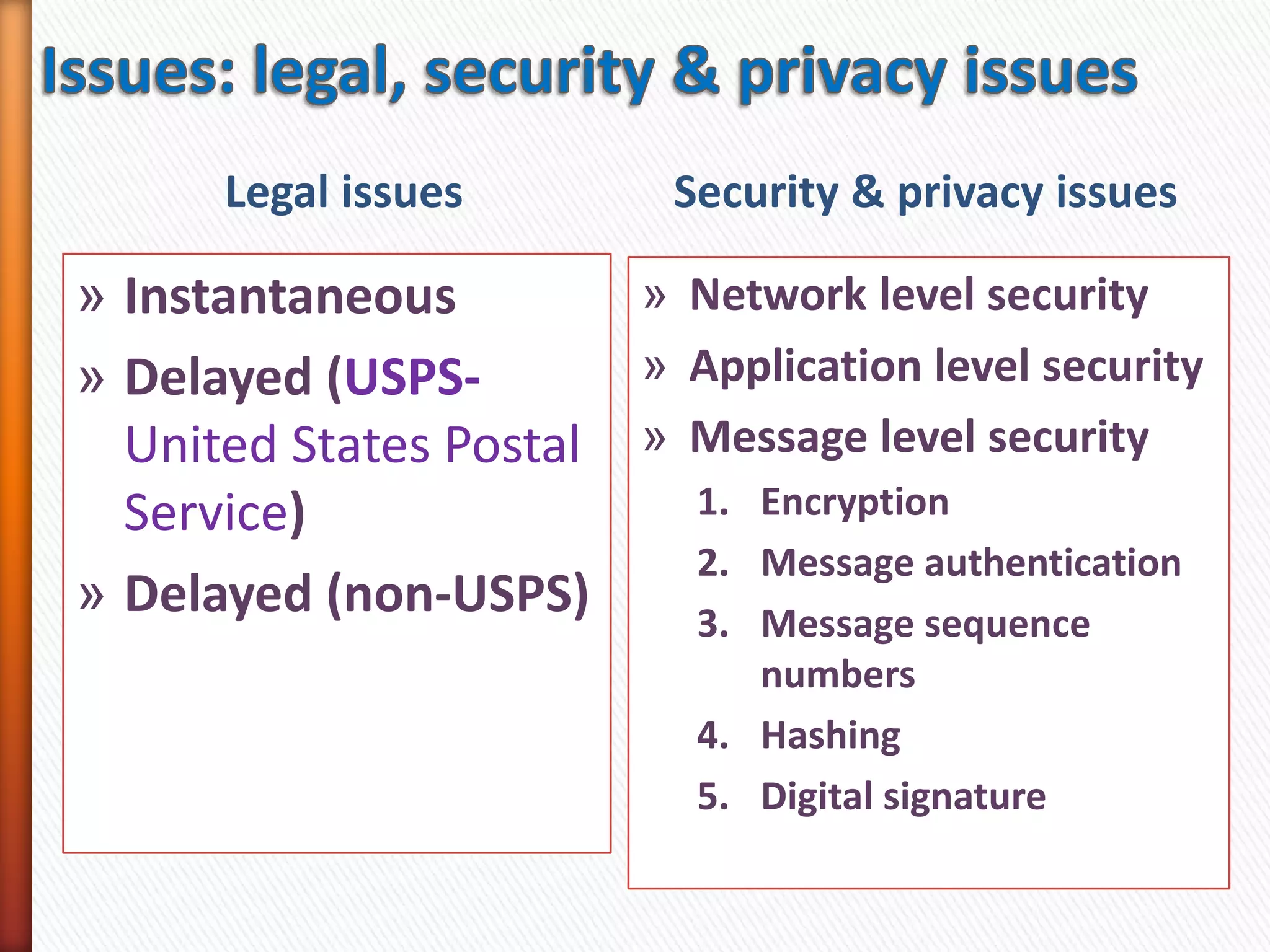
This document discusses electronic data interchange (EDI) and outlines the key steps involved in a partially integrated EDI system. It also lists the pre-requisites for implementing an EDI system, including identifying needs, weighing costs and benefits, selecting partners, and planning implementation. Finally, it addresses some of the legal, security, and privacy issues related to EDI systems.





