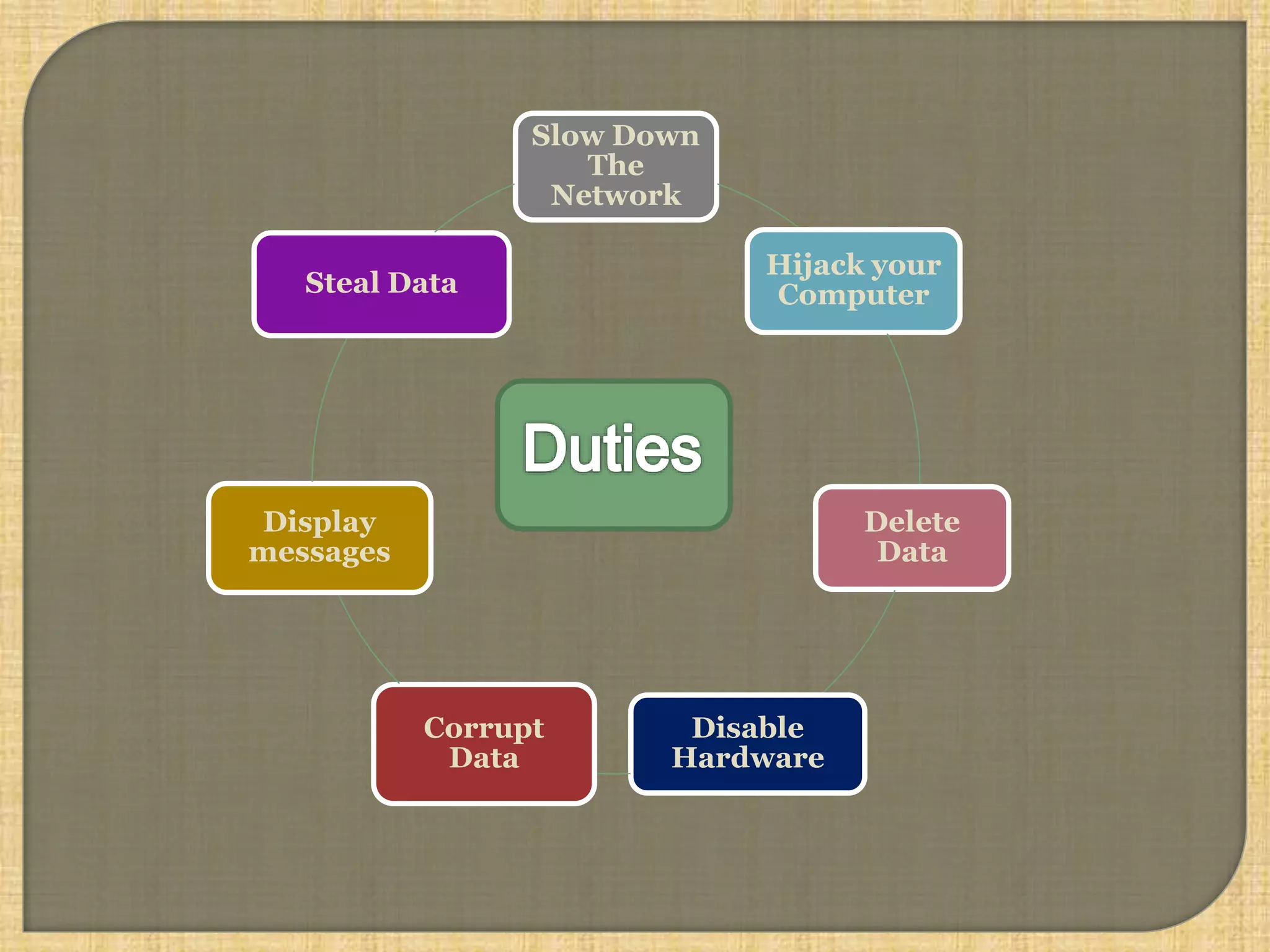
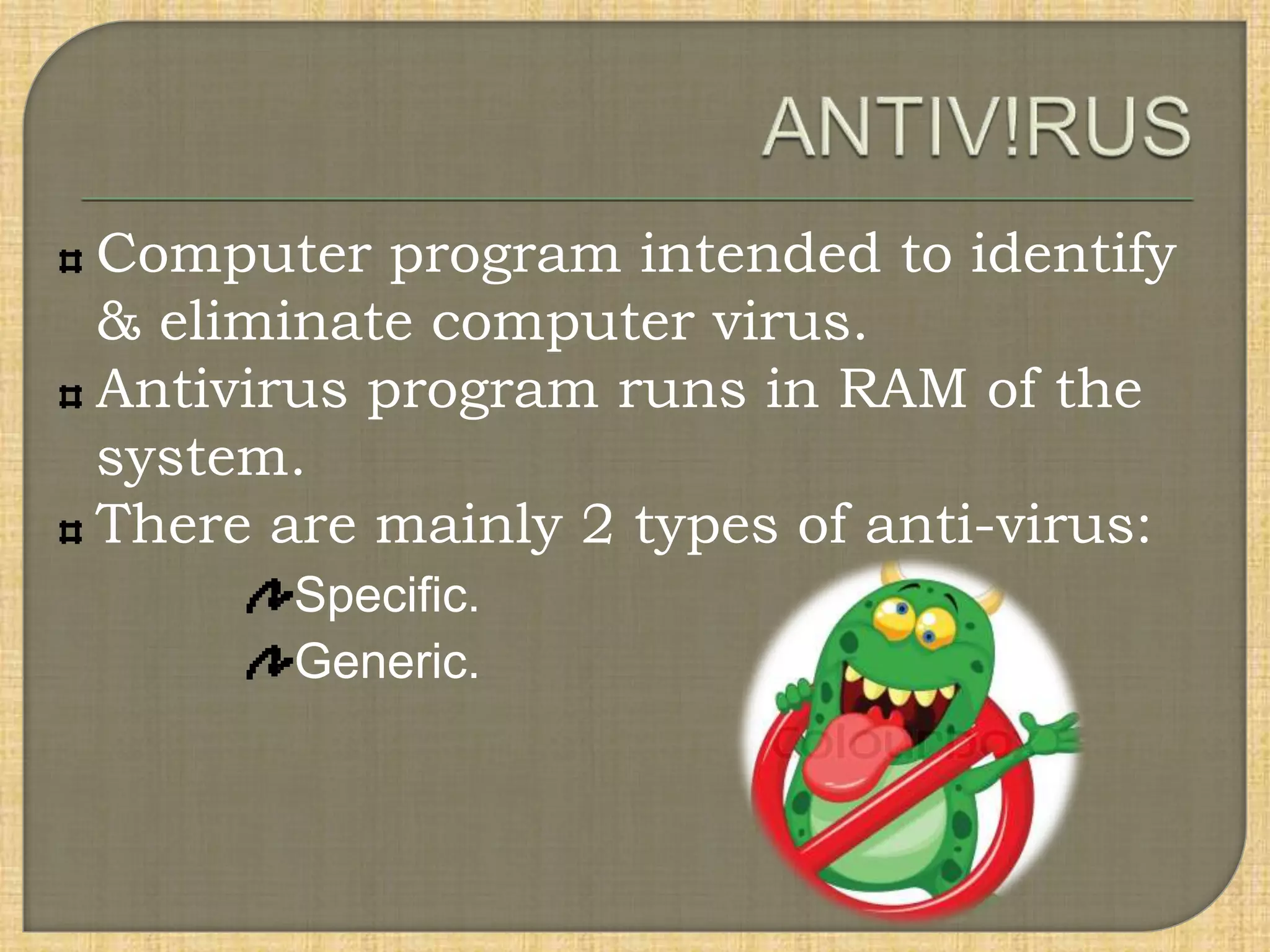
The document outlines various types of computer viruses, including boot, program, macro, and polymorphic viruses, detailing their characteristics and how they propagate. It also discusses the role of antivirus programs in detecting, isolating, and removing these threats from computer systems. Additionally, it emphasizes the importance of keeping antivirus software updated to protect against new virus definitions.