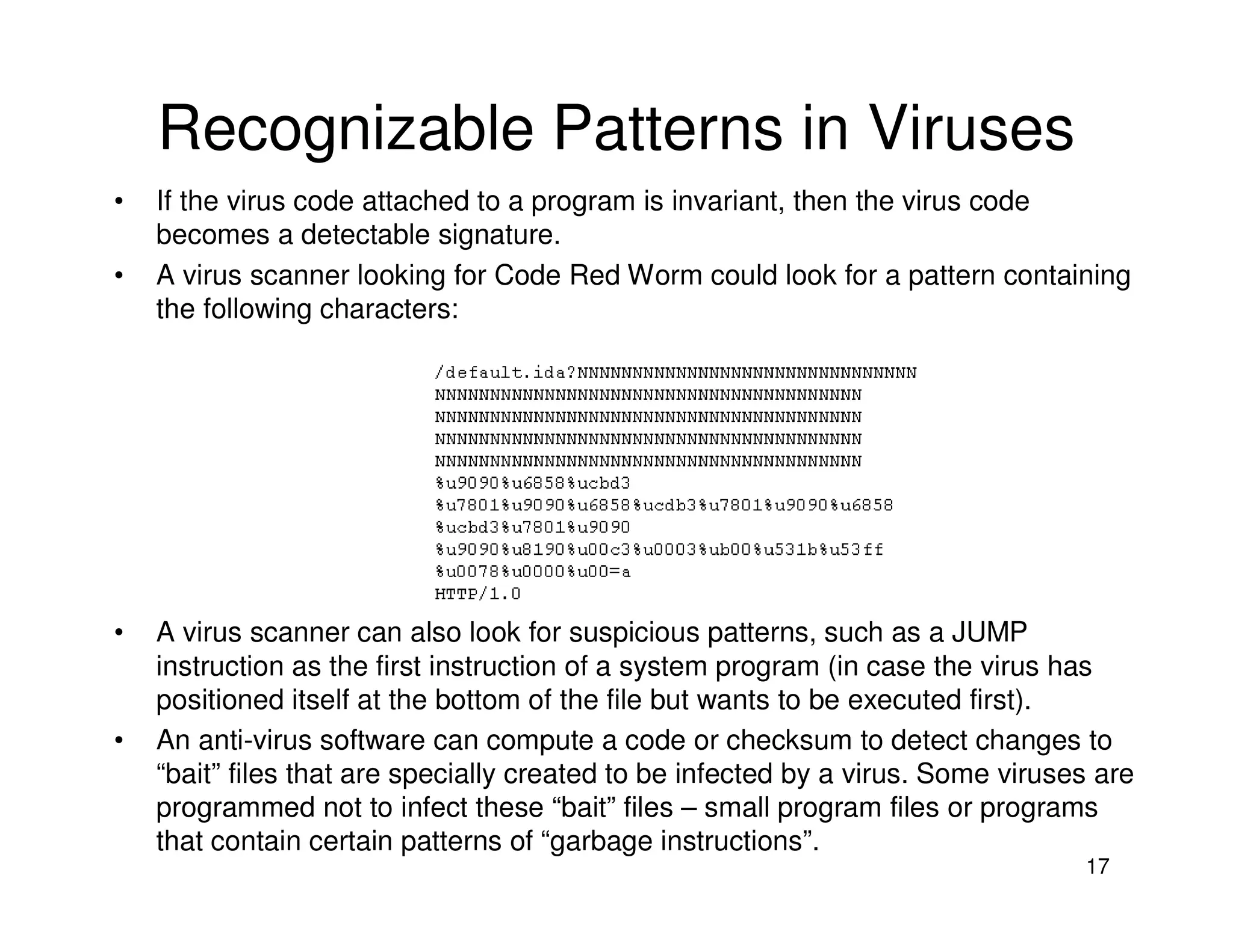
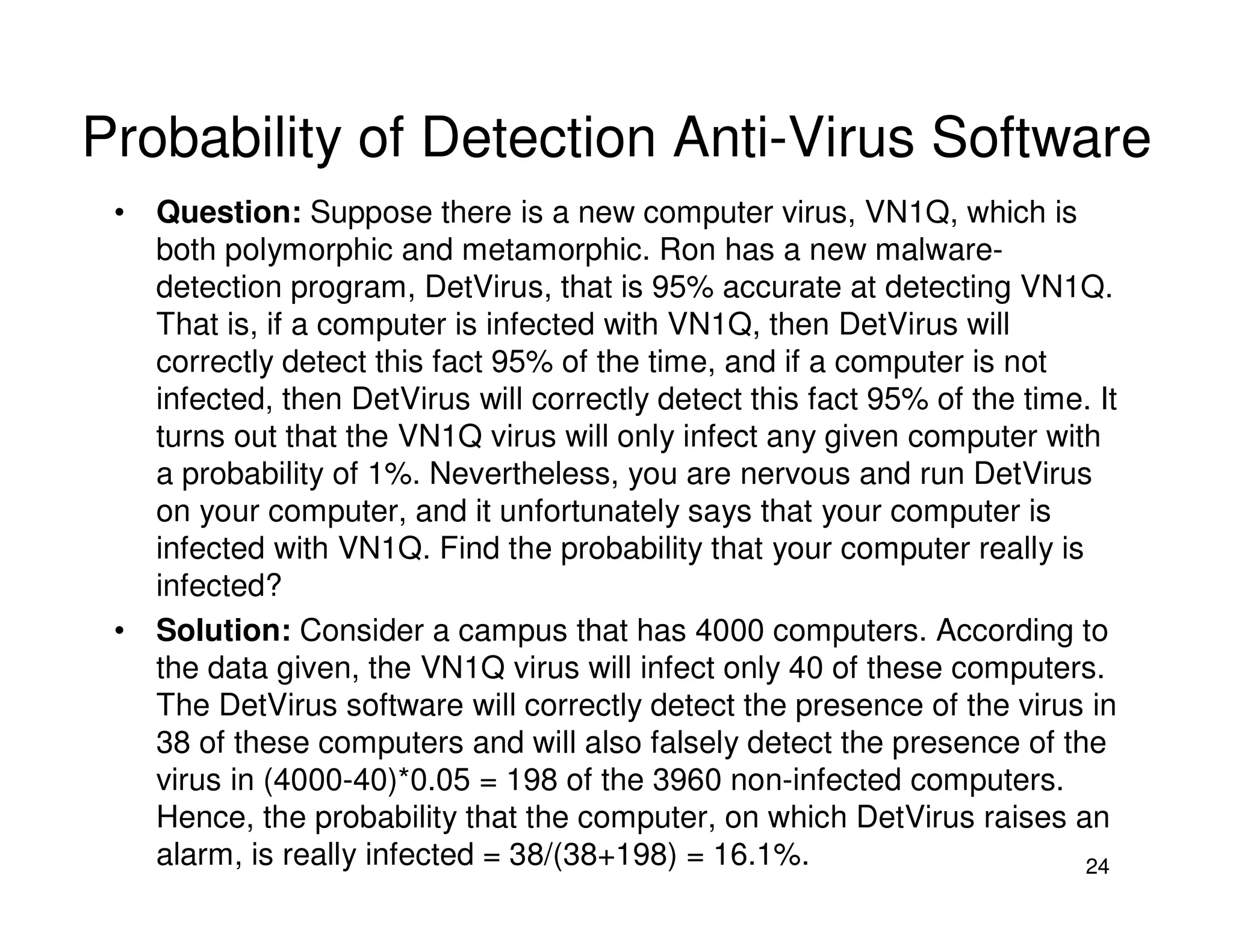
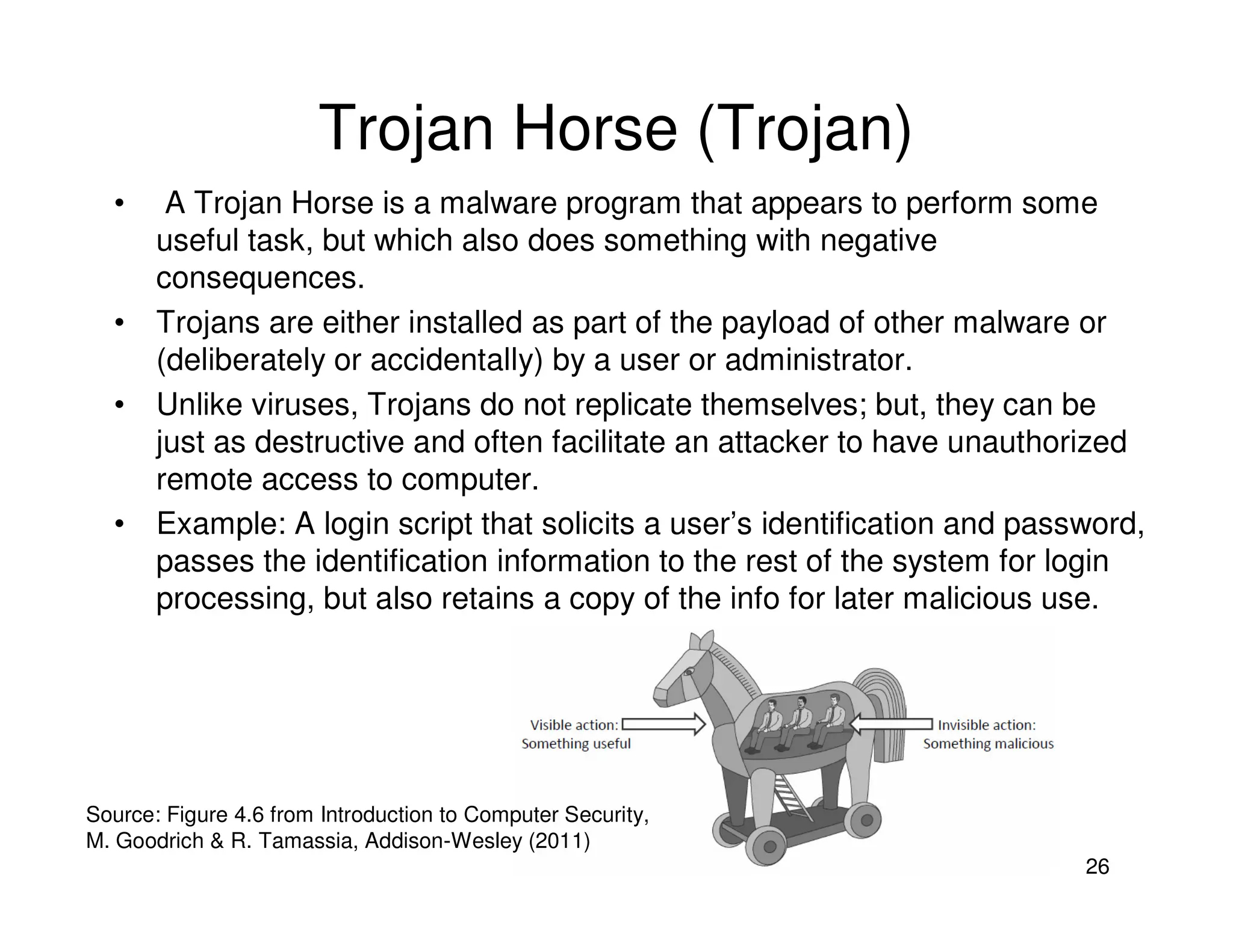
1. Malware refers to malicious software that can damage programs or systems. Viruses are a type of malware that can replicate itself and spread by modifying other programs.
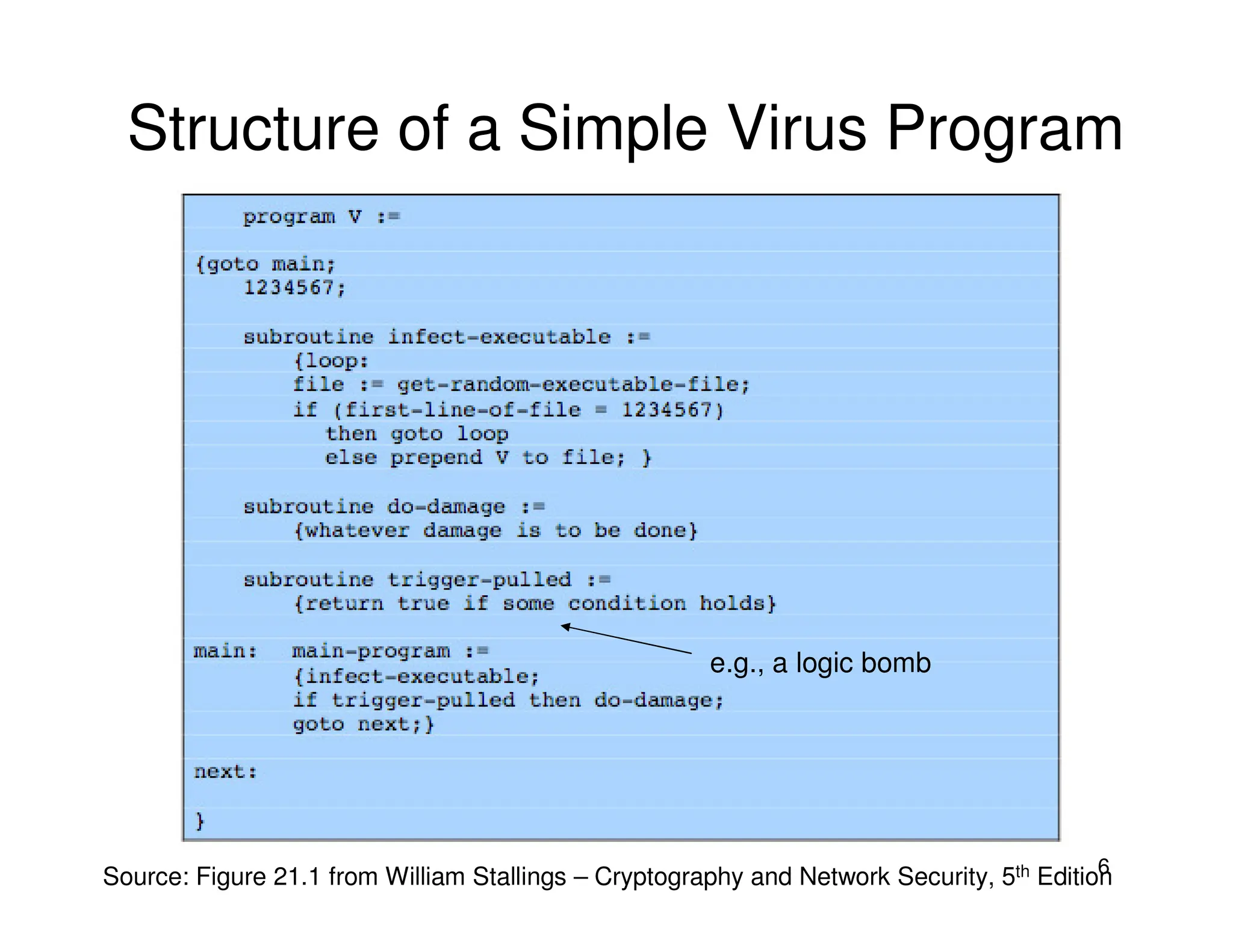
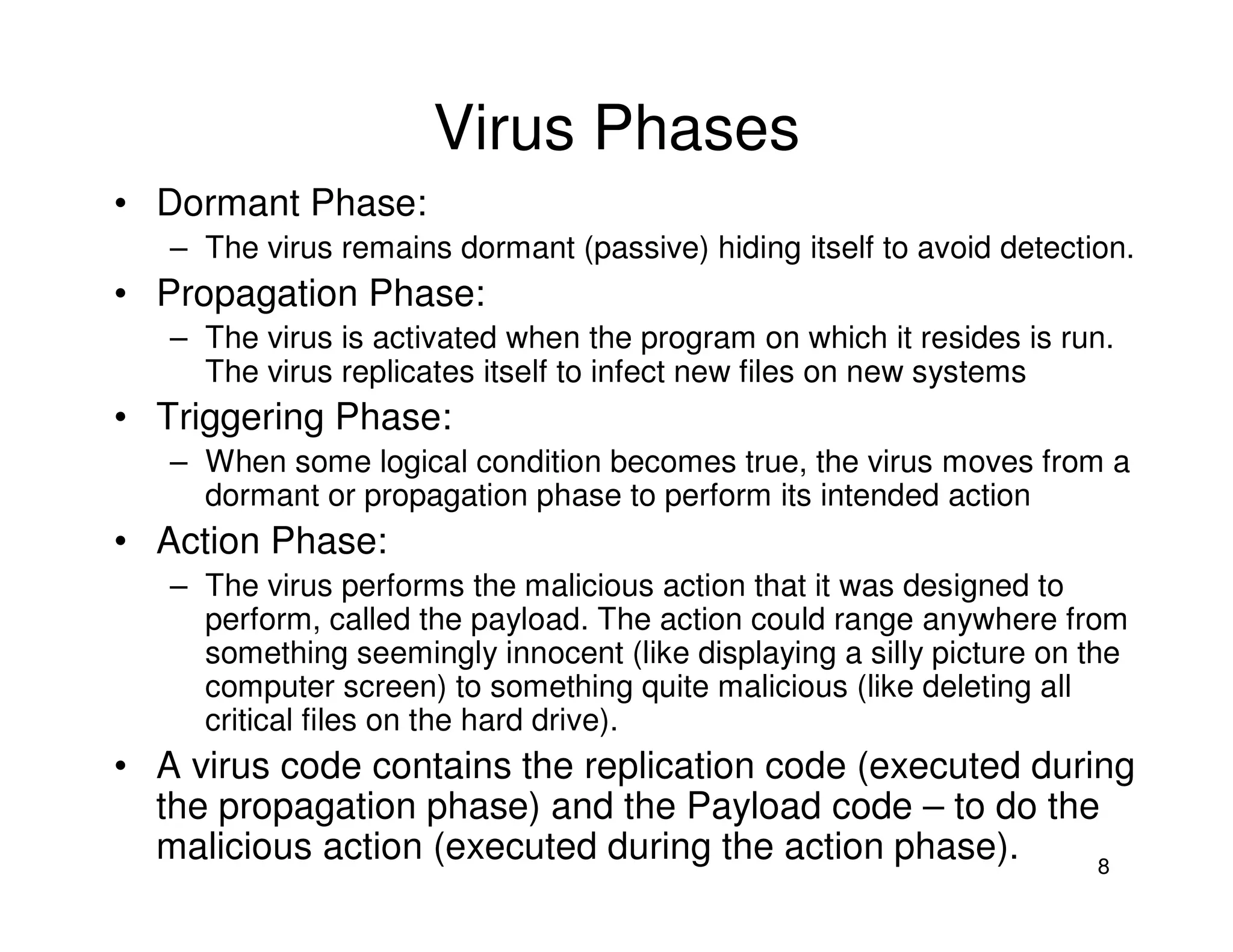
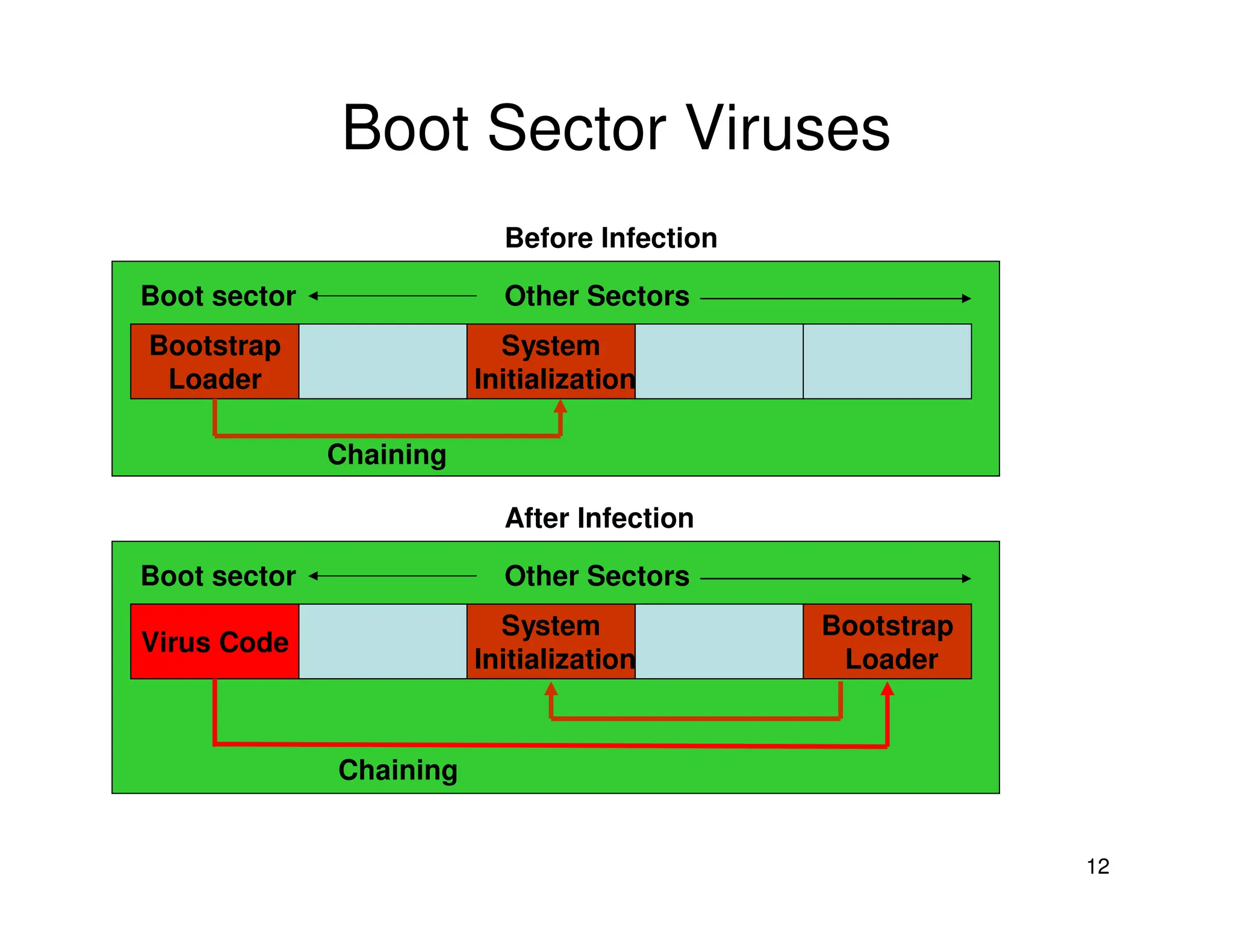
2. Viruses can infect programs by modifying executable files, documents using macros, or boot sectors. They spread through file sharing and email attachments. Viruses have different phases like dormant, propagation, triggering, and action.
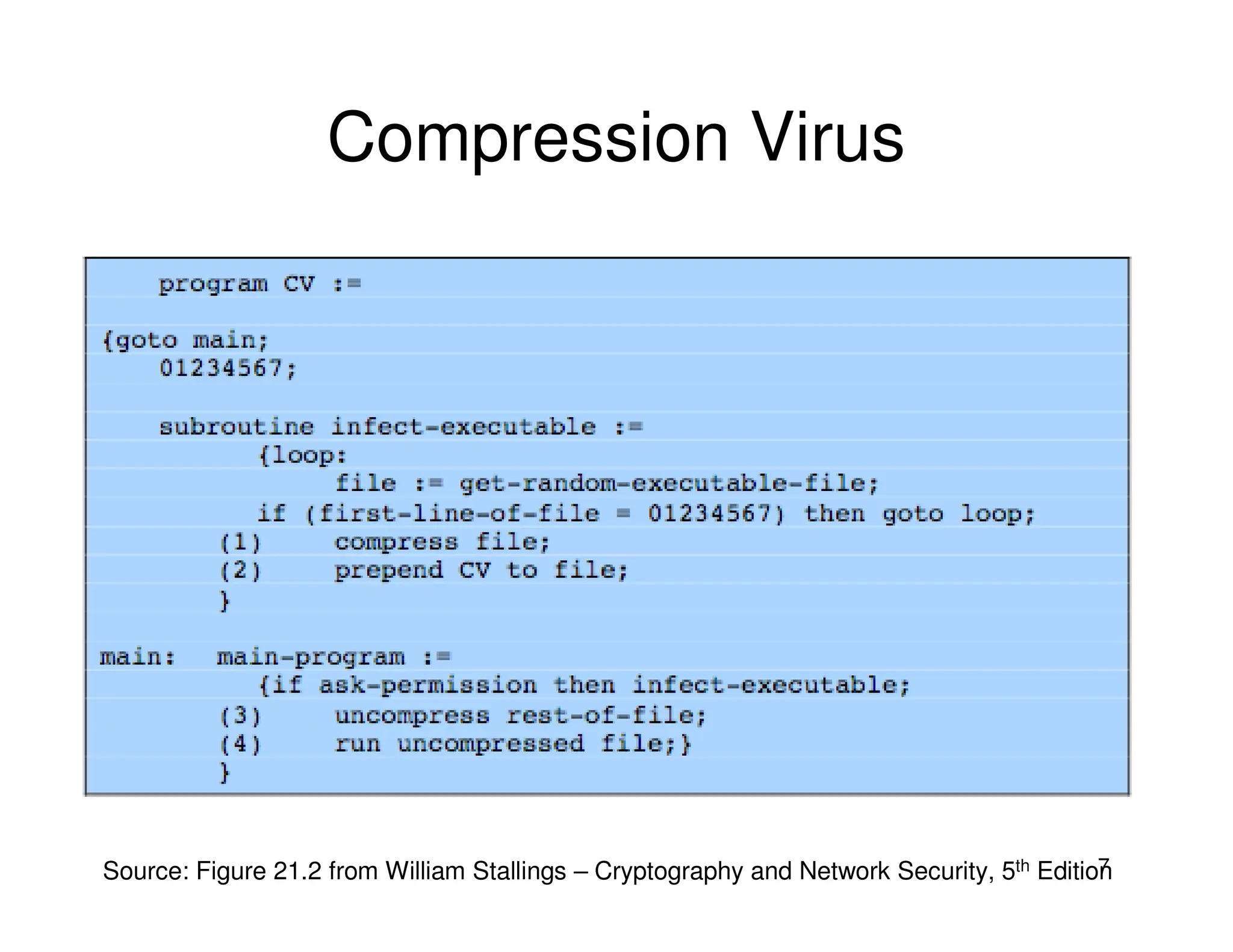
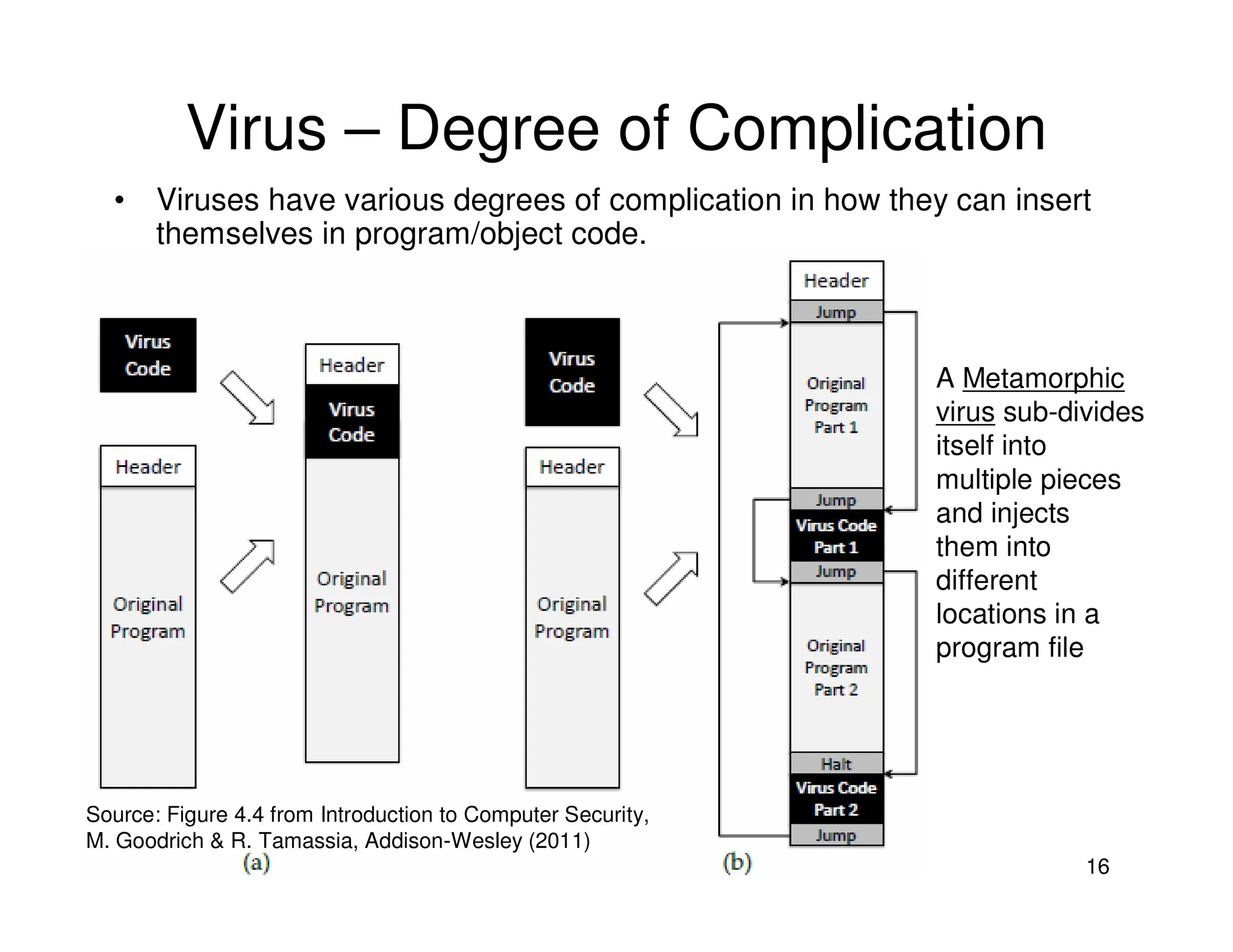
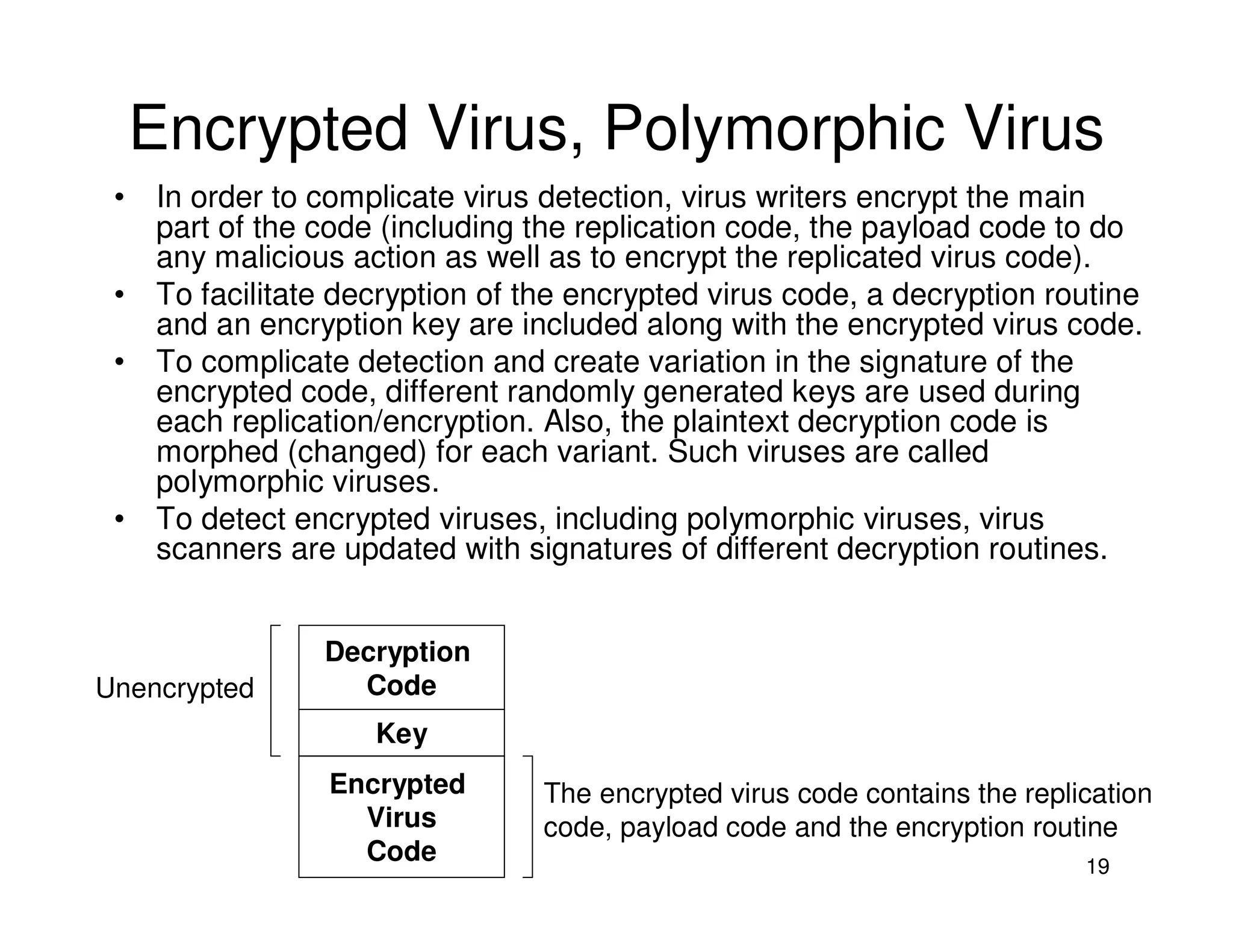
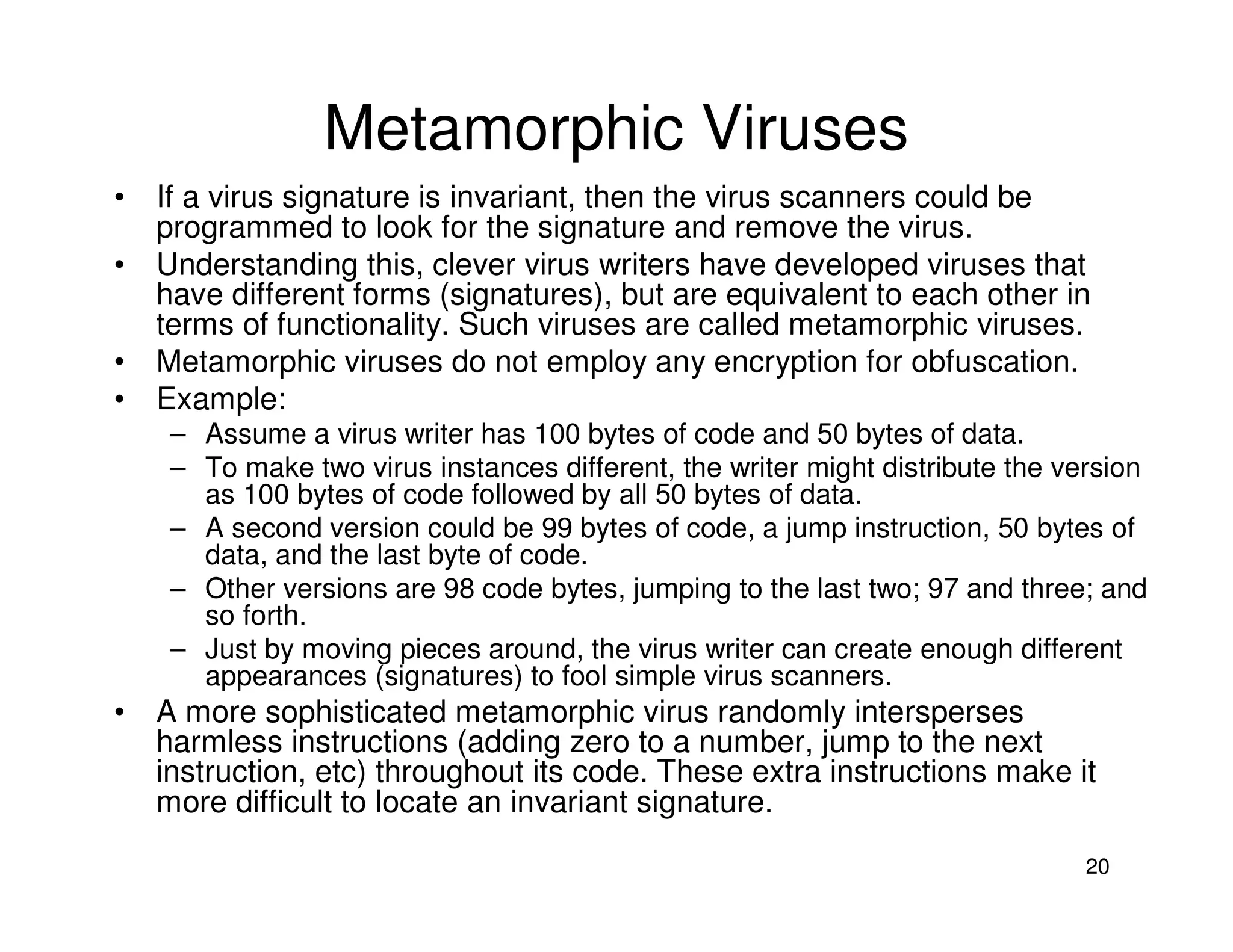
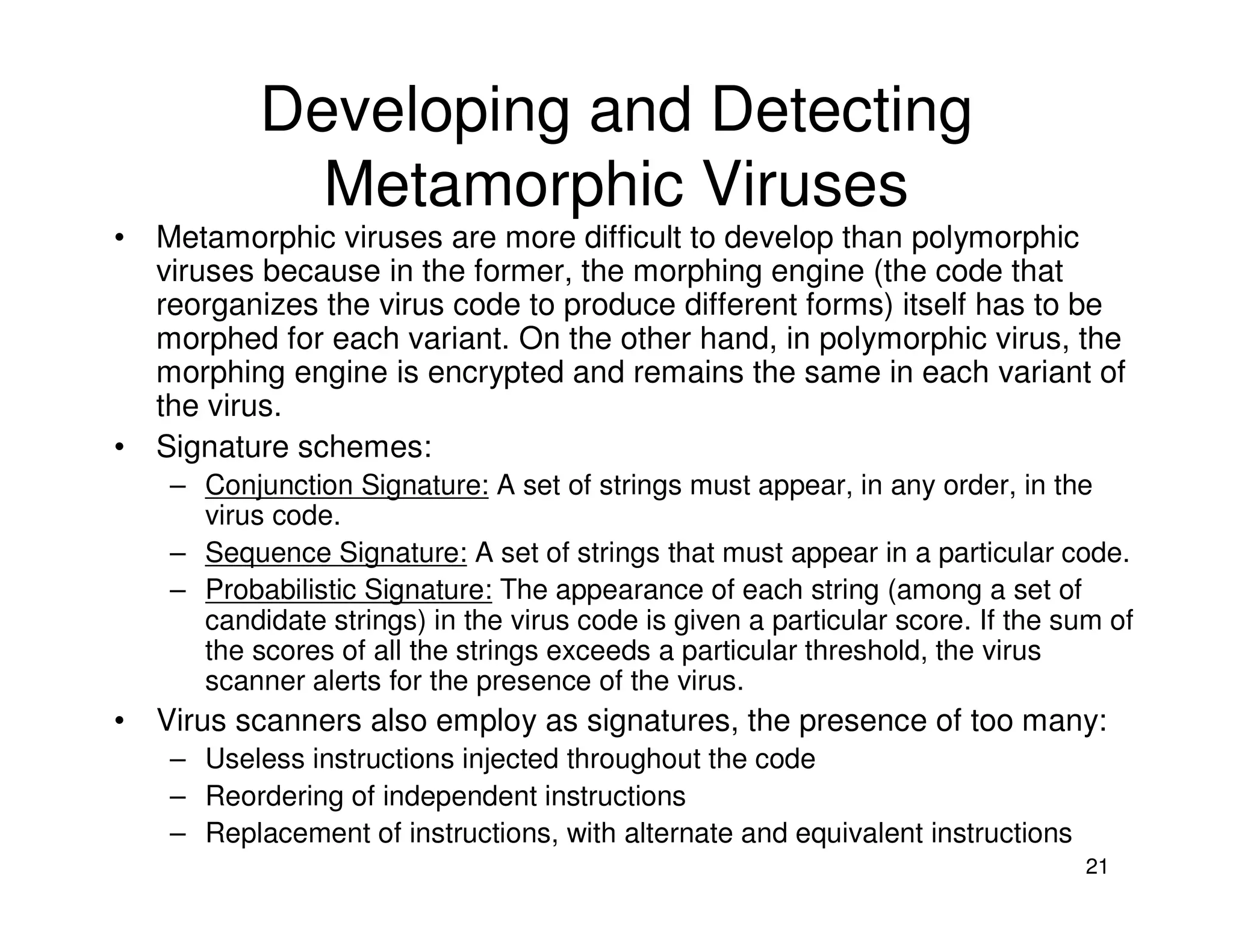
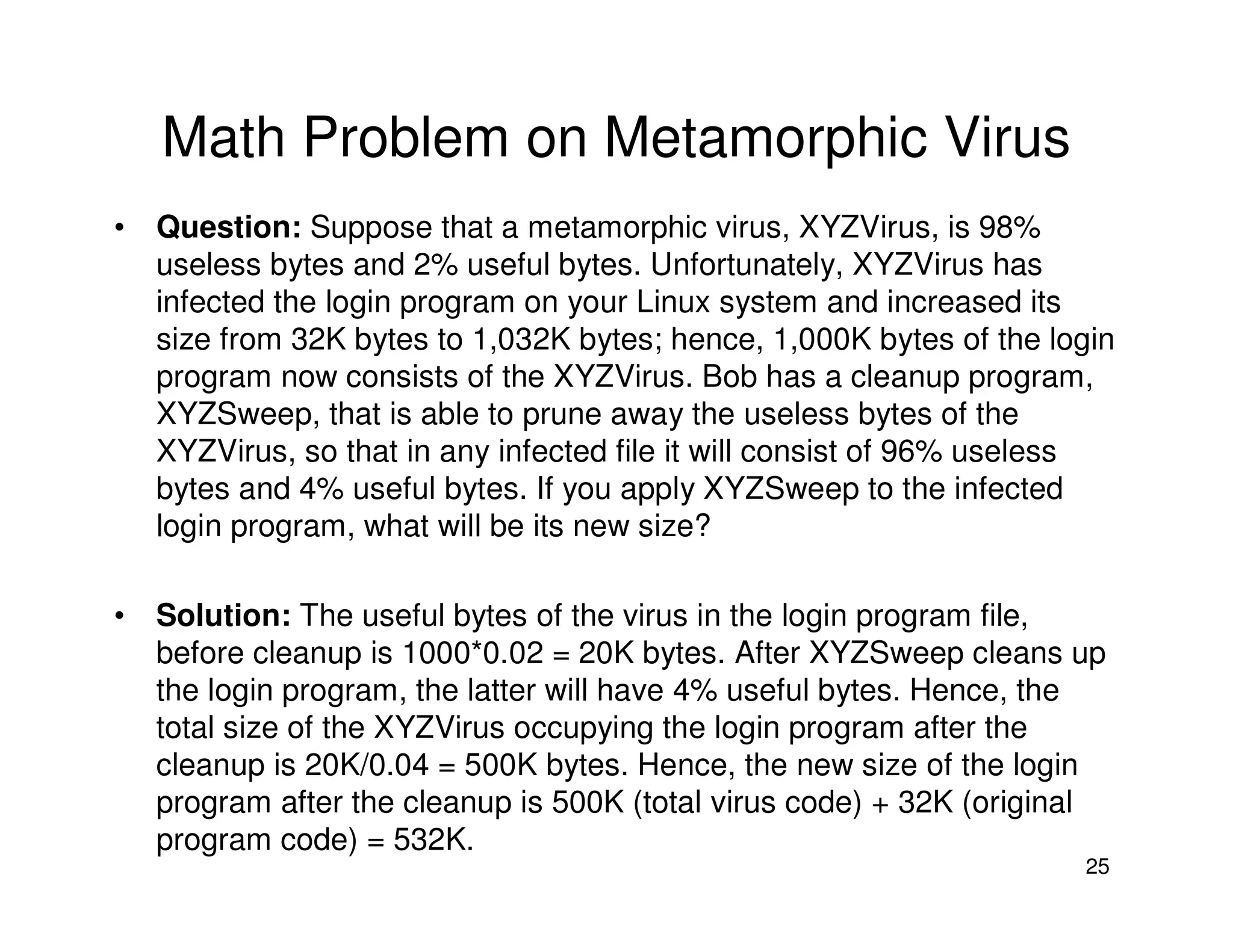
3. Antivirus software uses virus signatures and behavior detection to identify viruses. Infected files may be quarantined to prevent spreading while they are analyzed and removed or restored. More advanced viruses use encryption, polymorphism, and metamorphism to avoid signature detection.