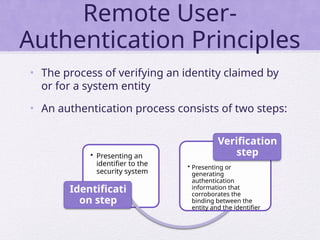
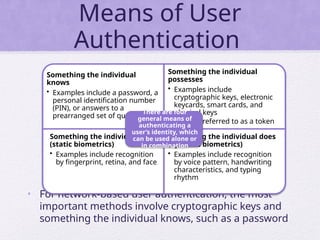
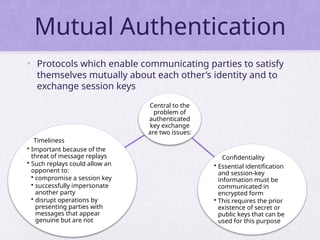
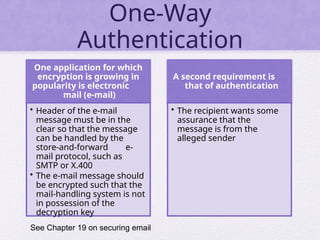
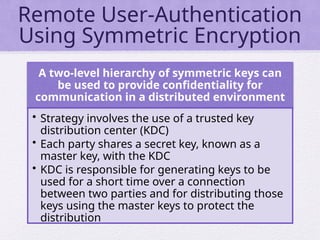
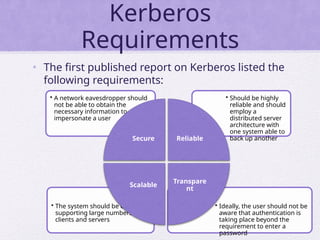
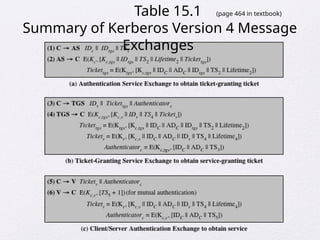
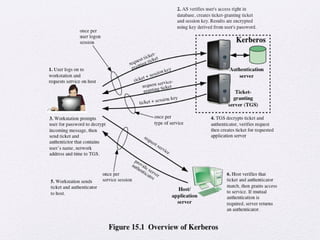
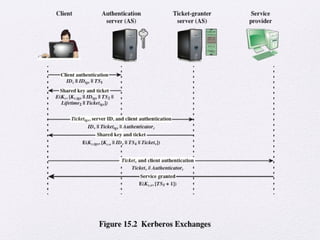
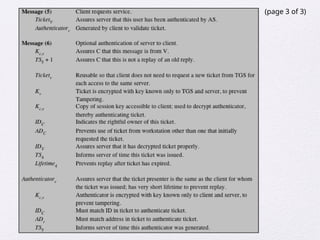
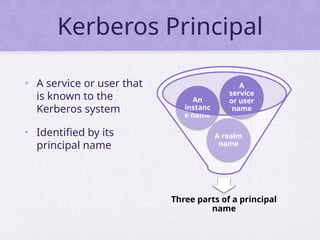
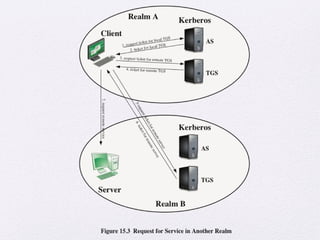
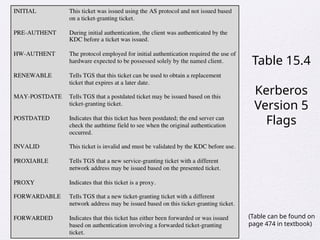
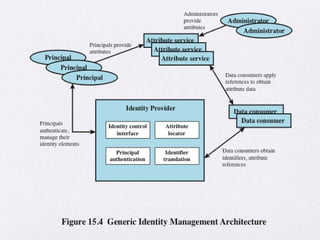
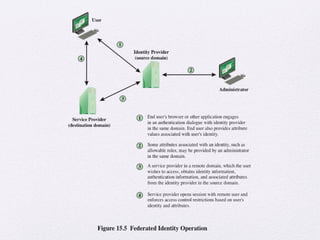
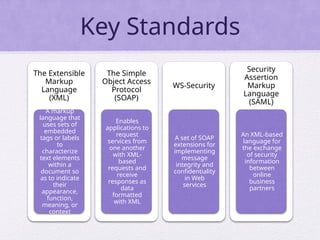
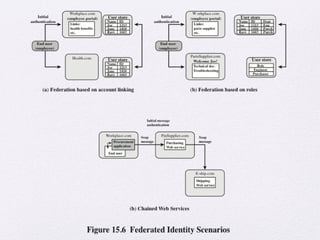
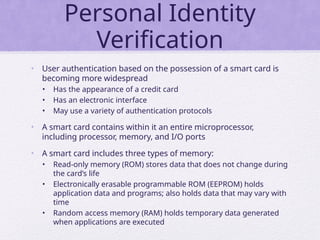
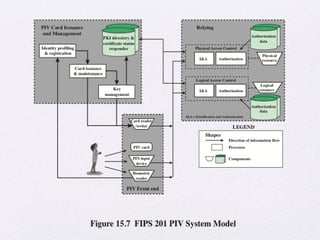
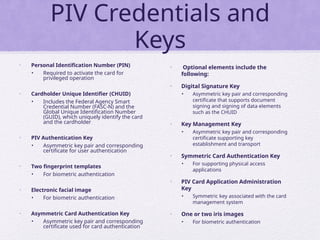
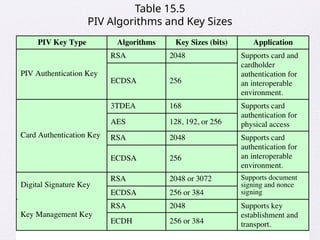
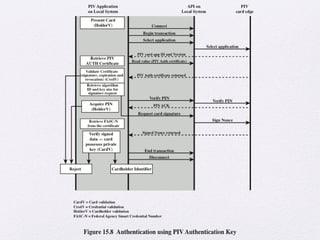
Chapter 15 of 'Cryptography and Network Security' by William Stallings covers user authentication methods, emphasizing the importance of verifying identities via cryptographic keys, passwords, and biometrics. It discusses techniques for mutual and one-way authentication, alongside approaches to combat replay attacks, including timestamps and challenge/response mechanisms. Additionally, it details the Kerberos authentication system and personal identity verification (PIV) standards, showcasing the evolution of authentication practices and technologies.