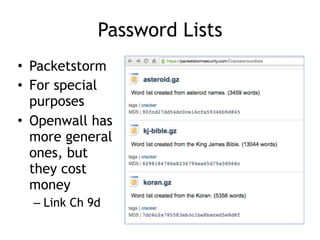
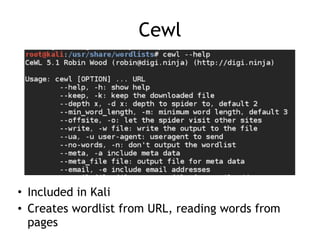
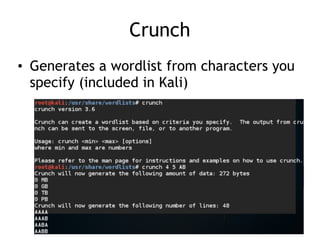
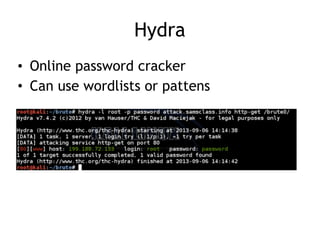
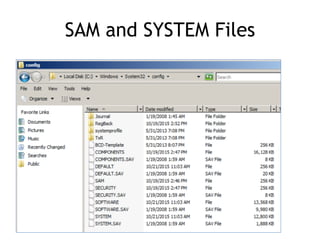
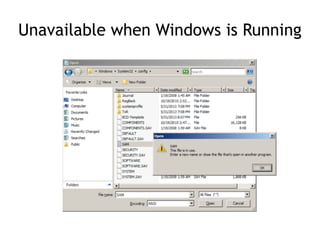
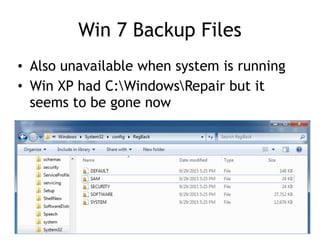
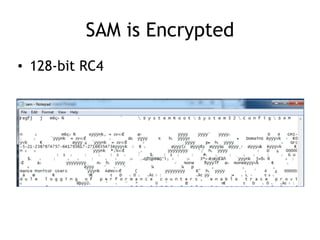
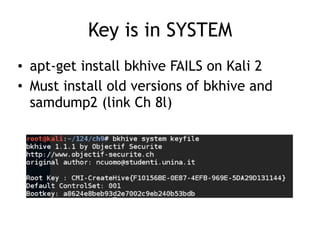
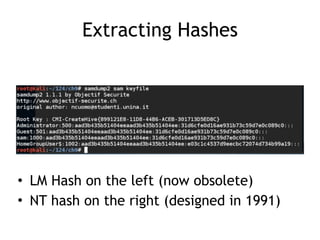
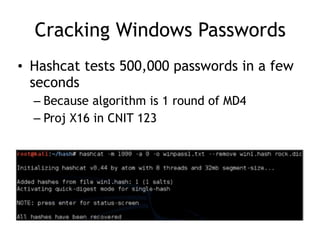
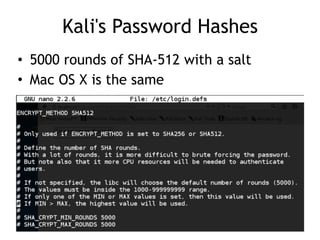
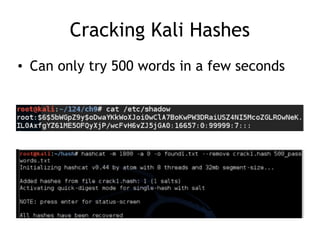
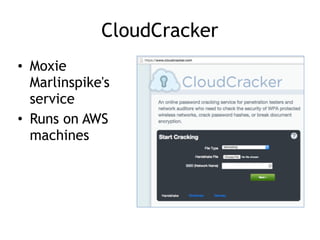
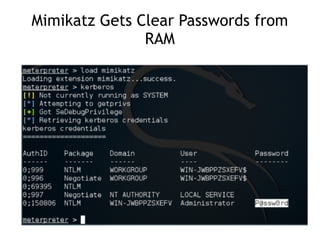
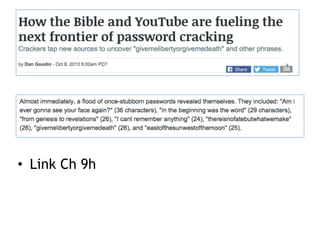
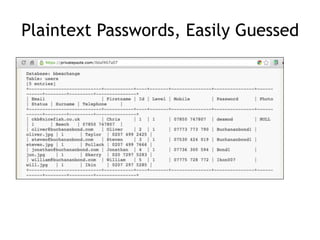
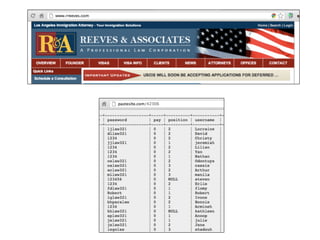
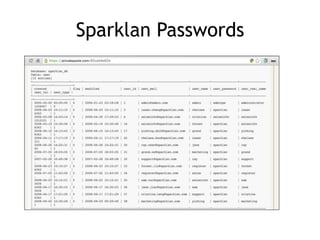
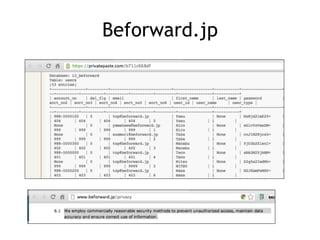
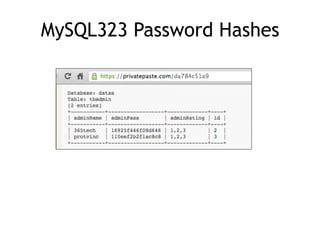
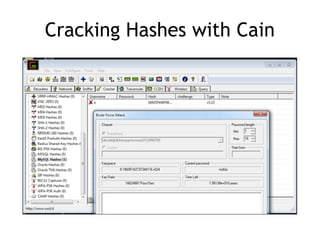
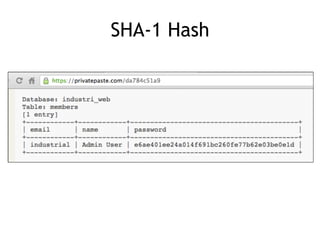
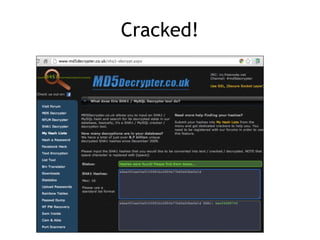
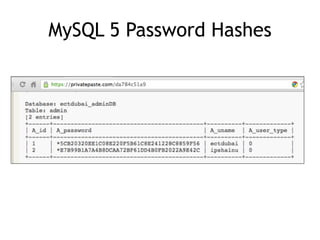
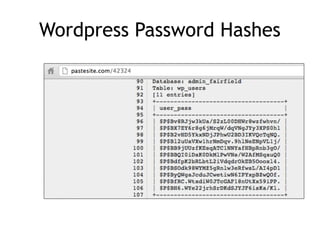
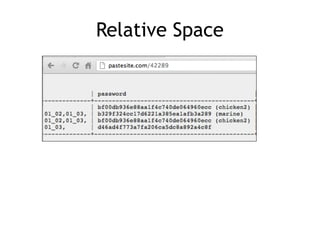
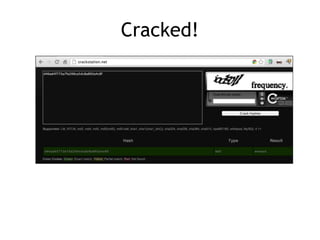
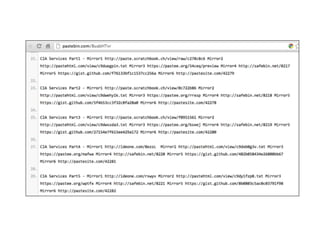
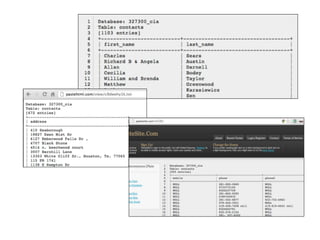
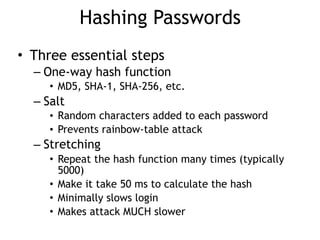
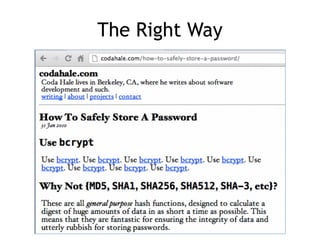
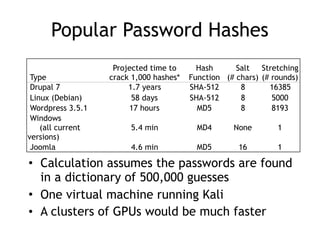
The document discusses advanced ethical hacking techniques, specifically focusing on password attacks, management, and common vulnerabilities. It covers online and offline password attacks, strategies for cracking passwords, and the importance of strong password hashing techniques like salting and stretching. Additionally, it highlights the risks of poor password storage practices and the potential for password recovery from RAM.