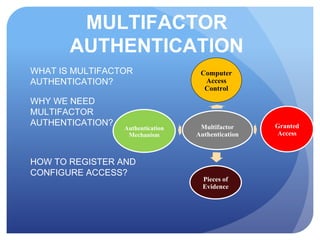
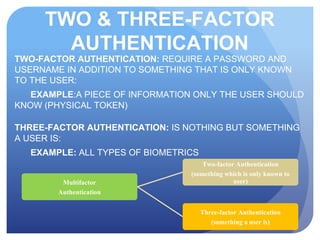
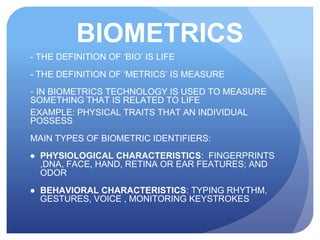
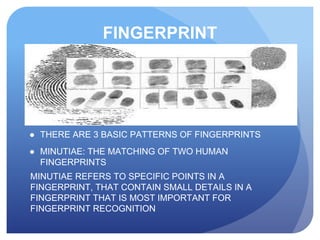
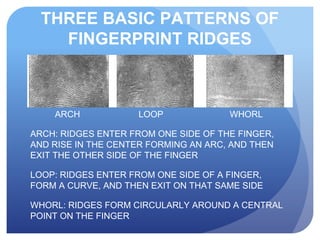
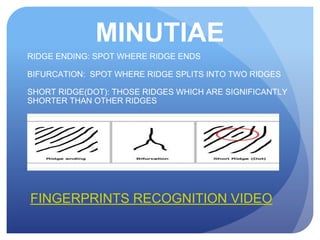
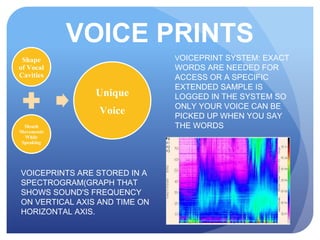
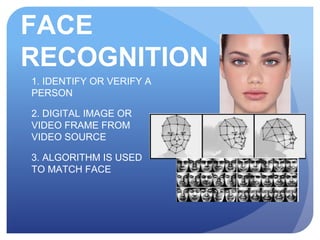
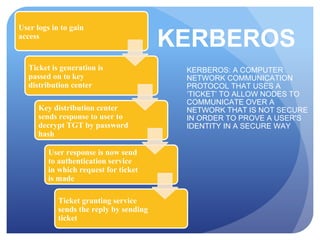
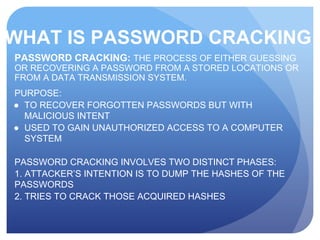
This document discusses access control systems and methodologies. It covers security clearances used by the federal government, multifactor authentication/biometrics, and passwords. Specific access control methods like fingerprints, voiceprints, retina scanning, iris scanning, and face recognition are explained. The document also discusses password cracking techniques and applications used to crack passwords like John the Ripper, Rainbow Crack, and Cain & Abel.