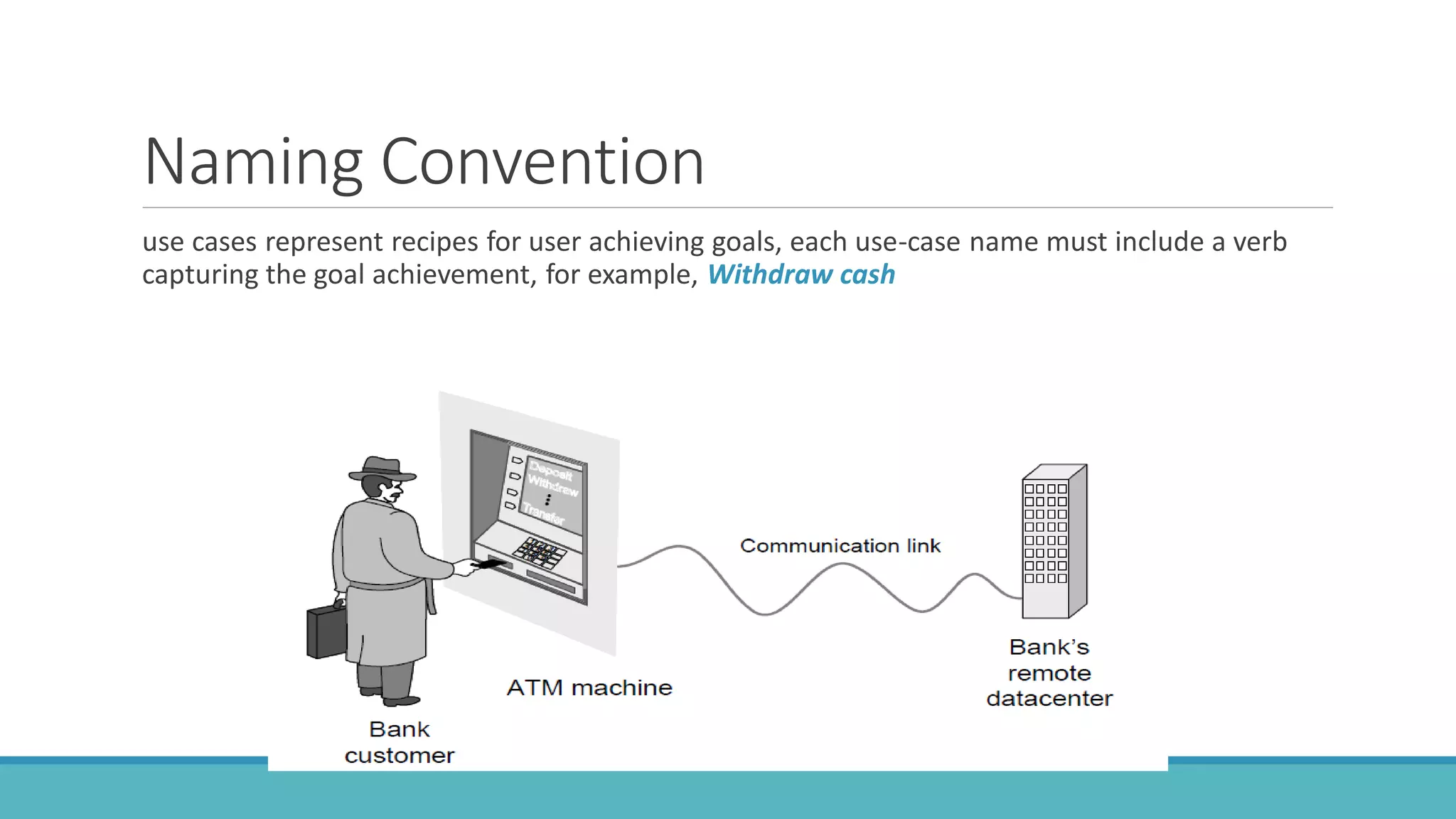
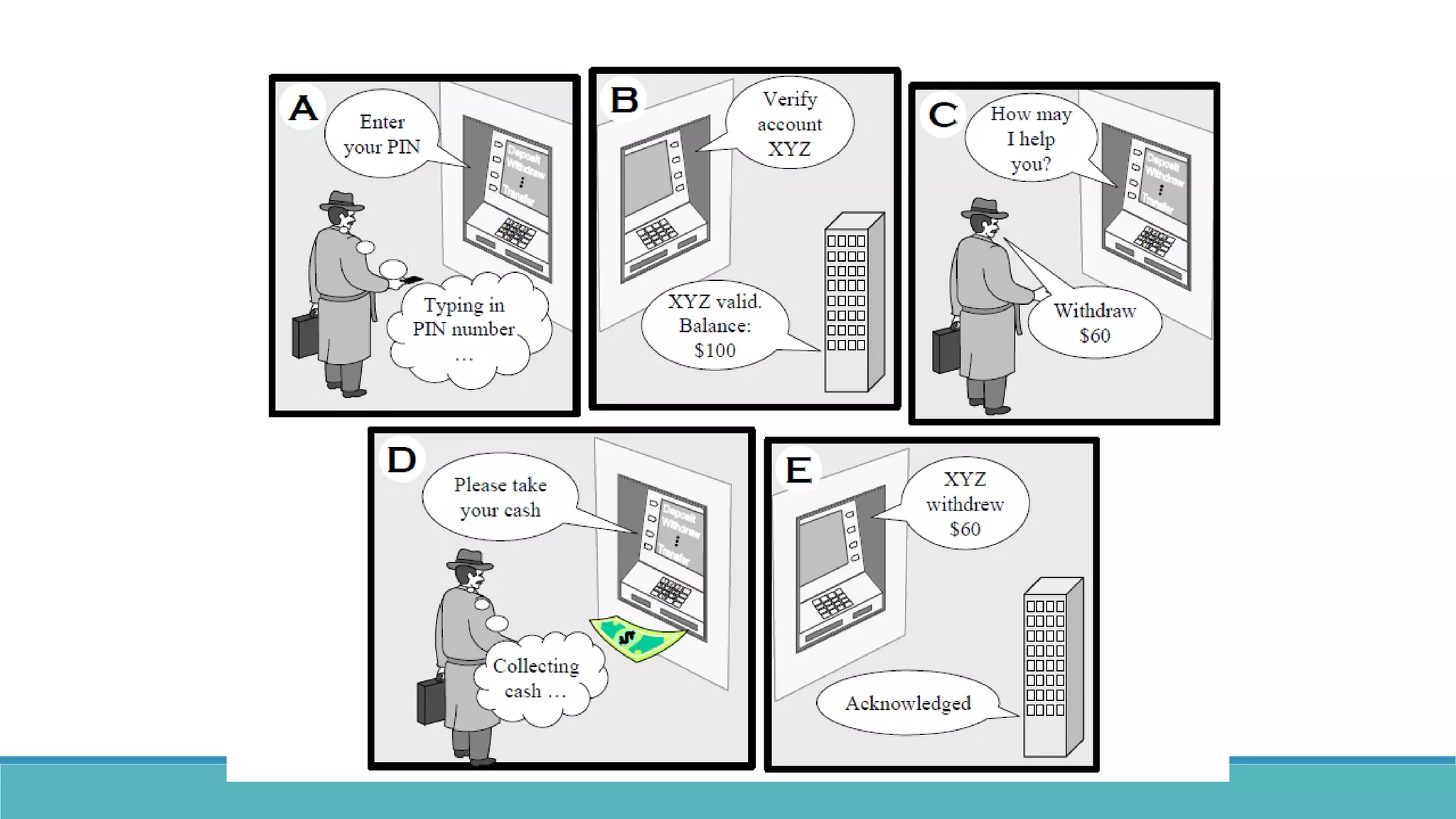
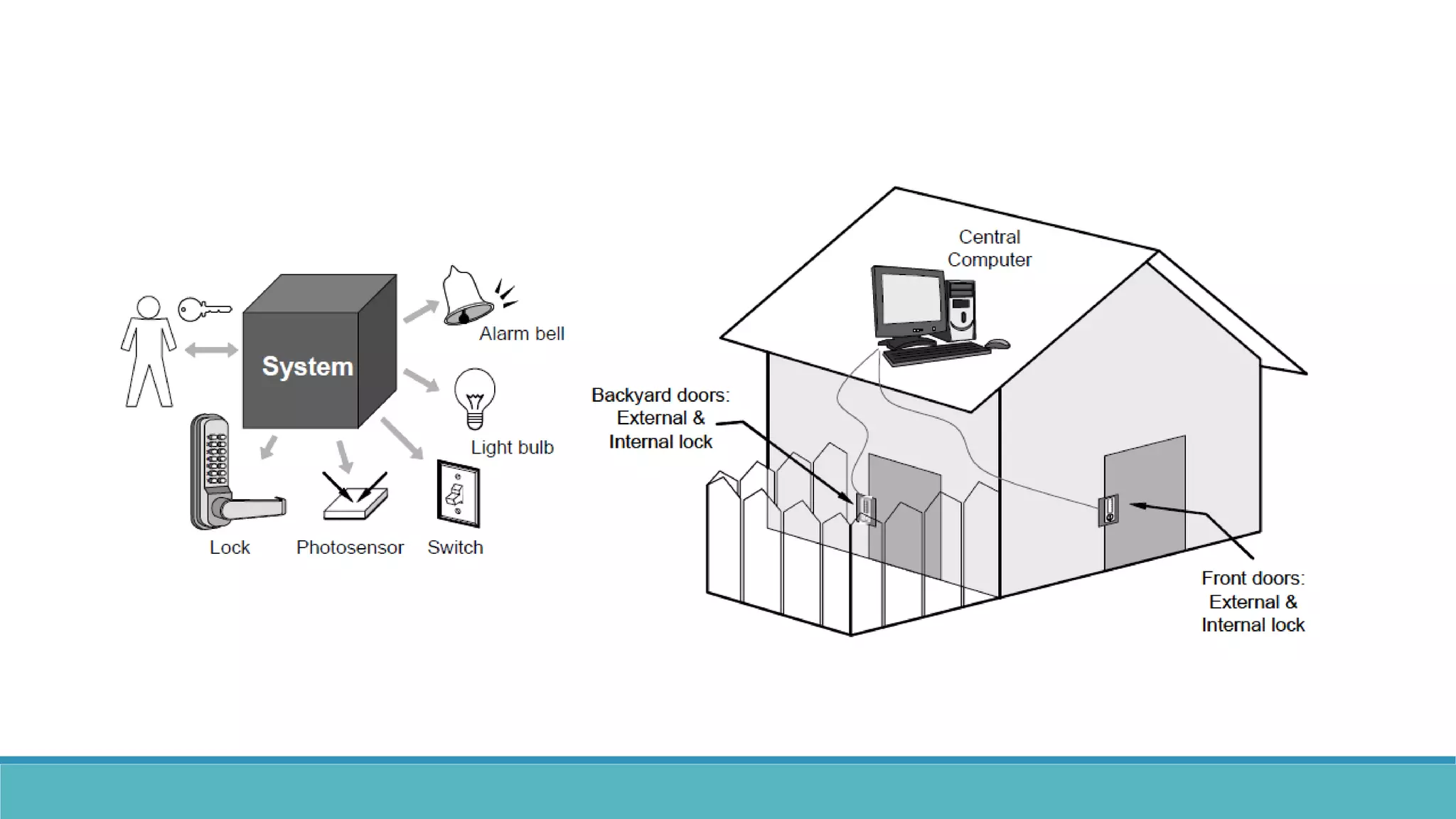
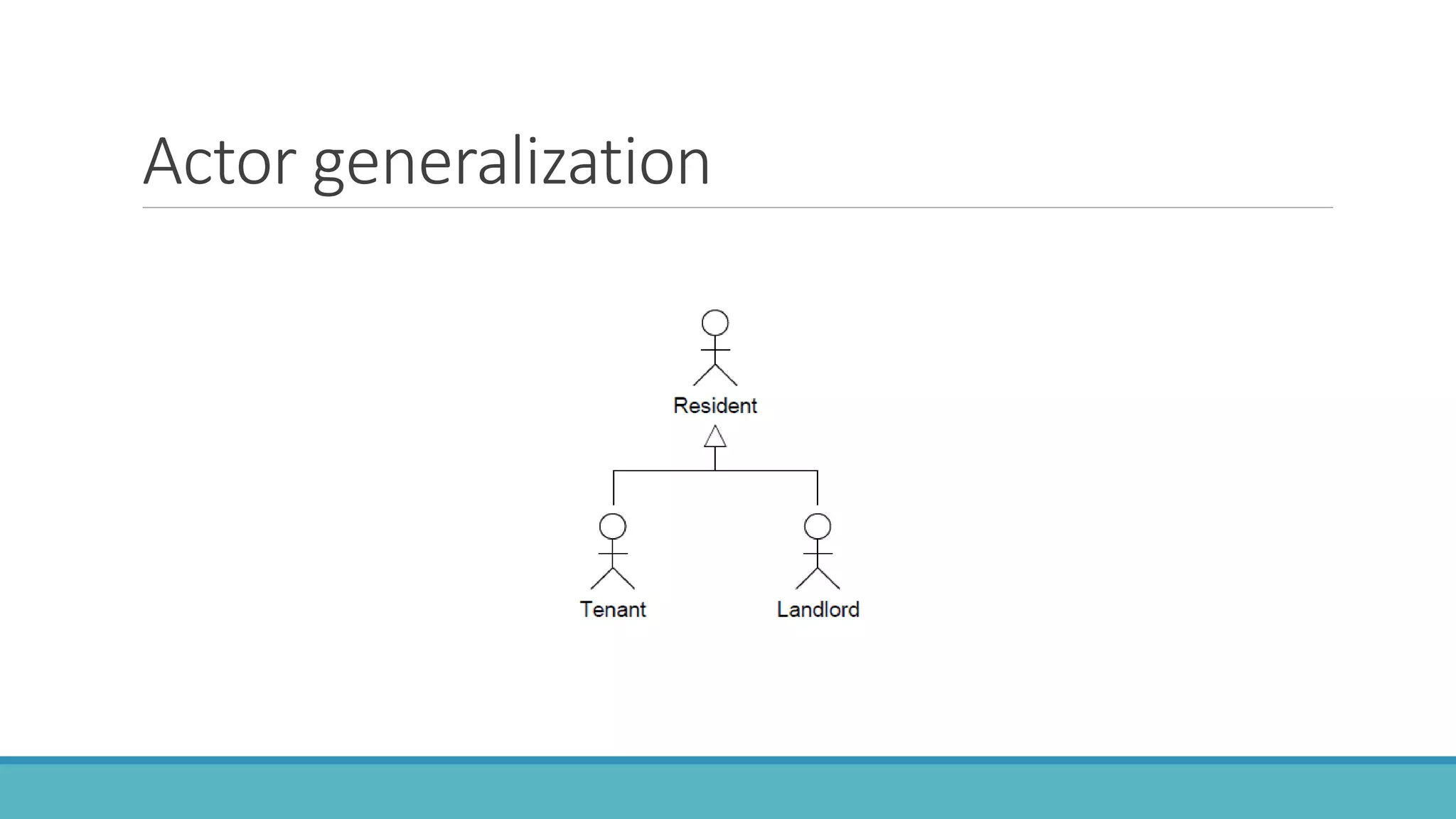
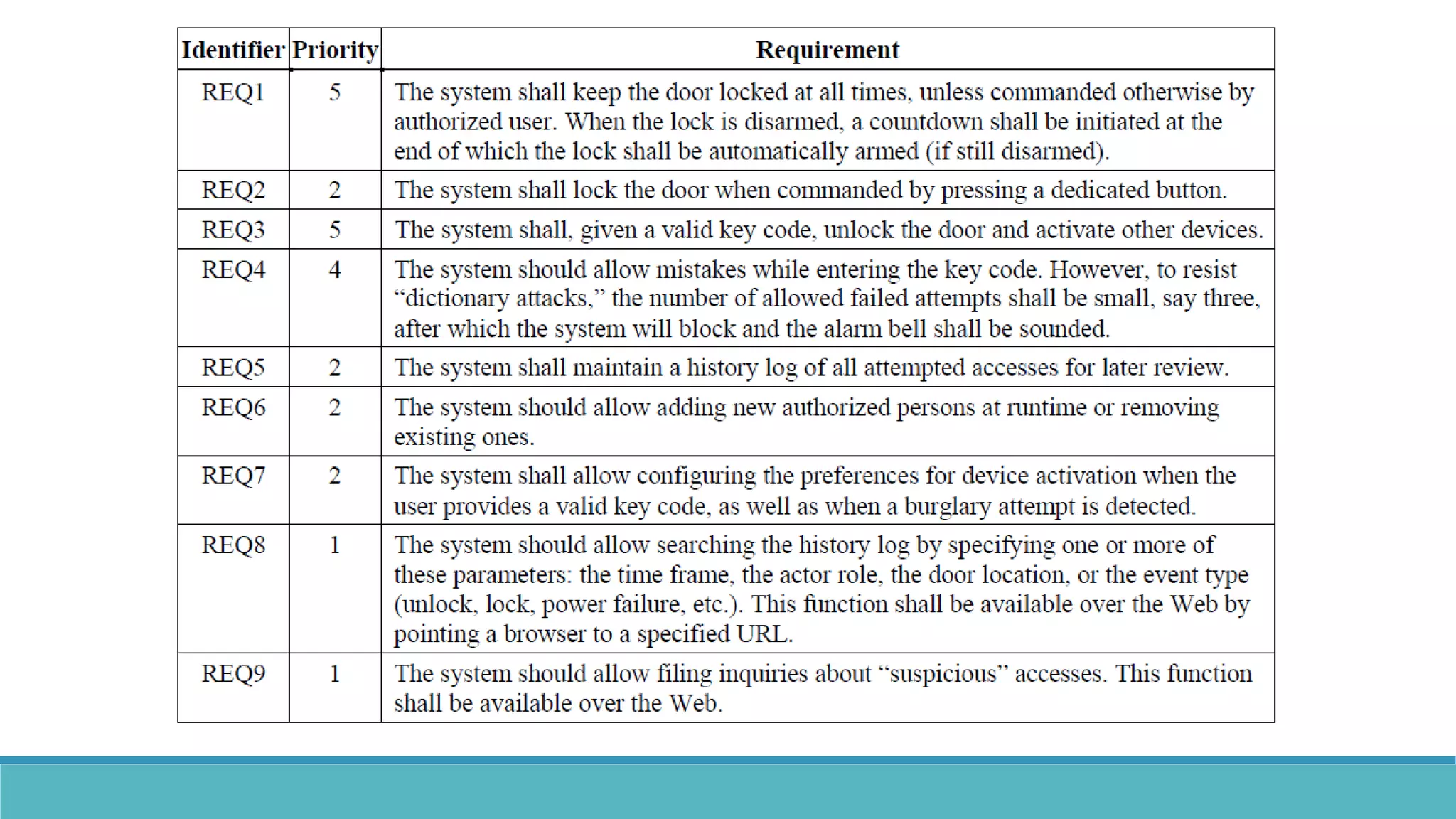
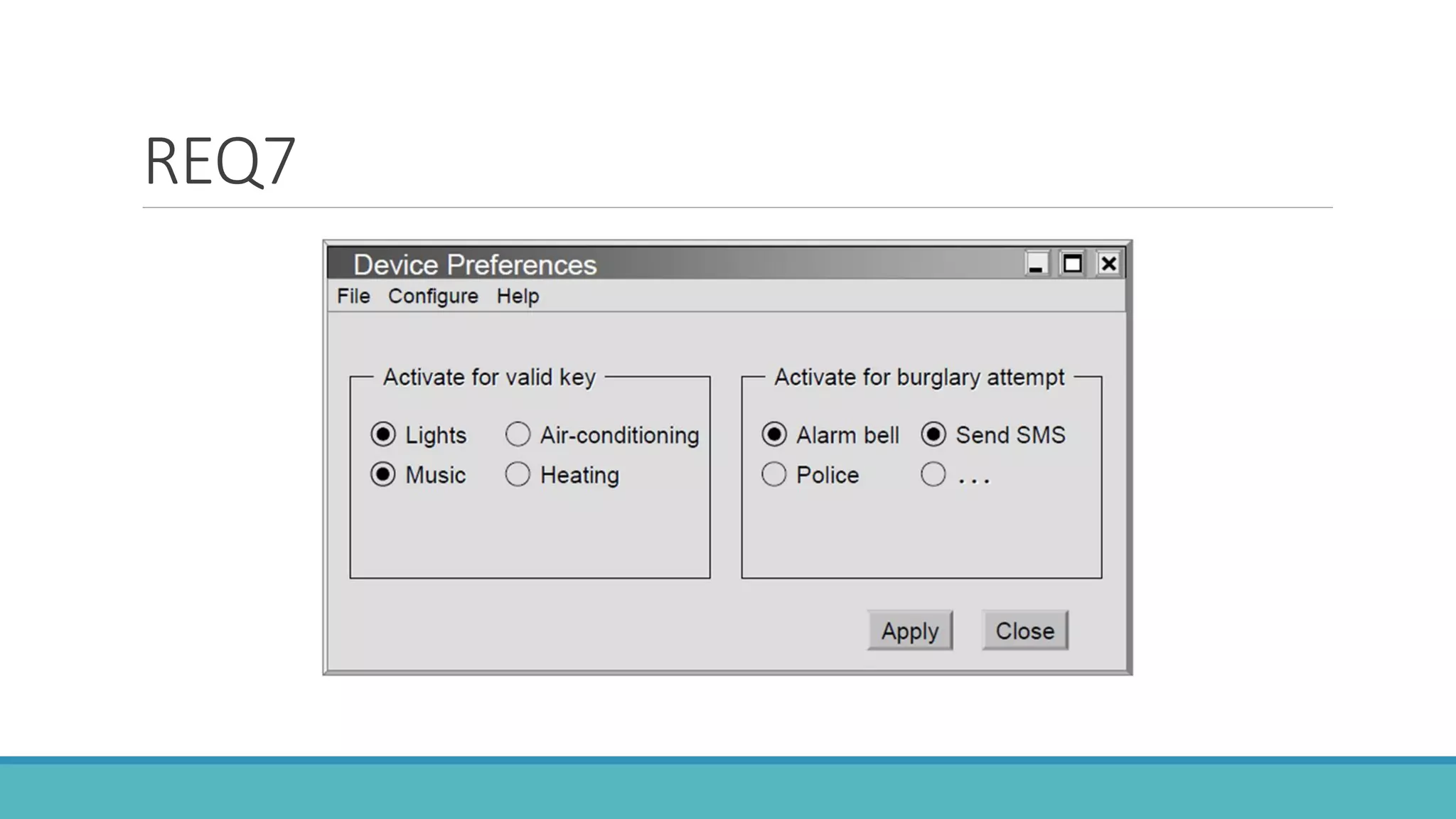
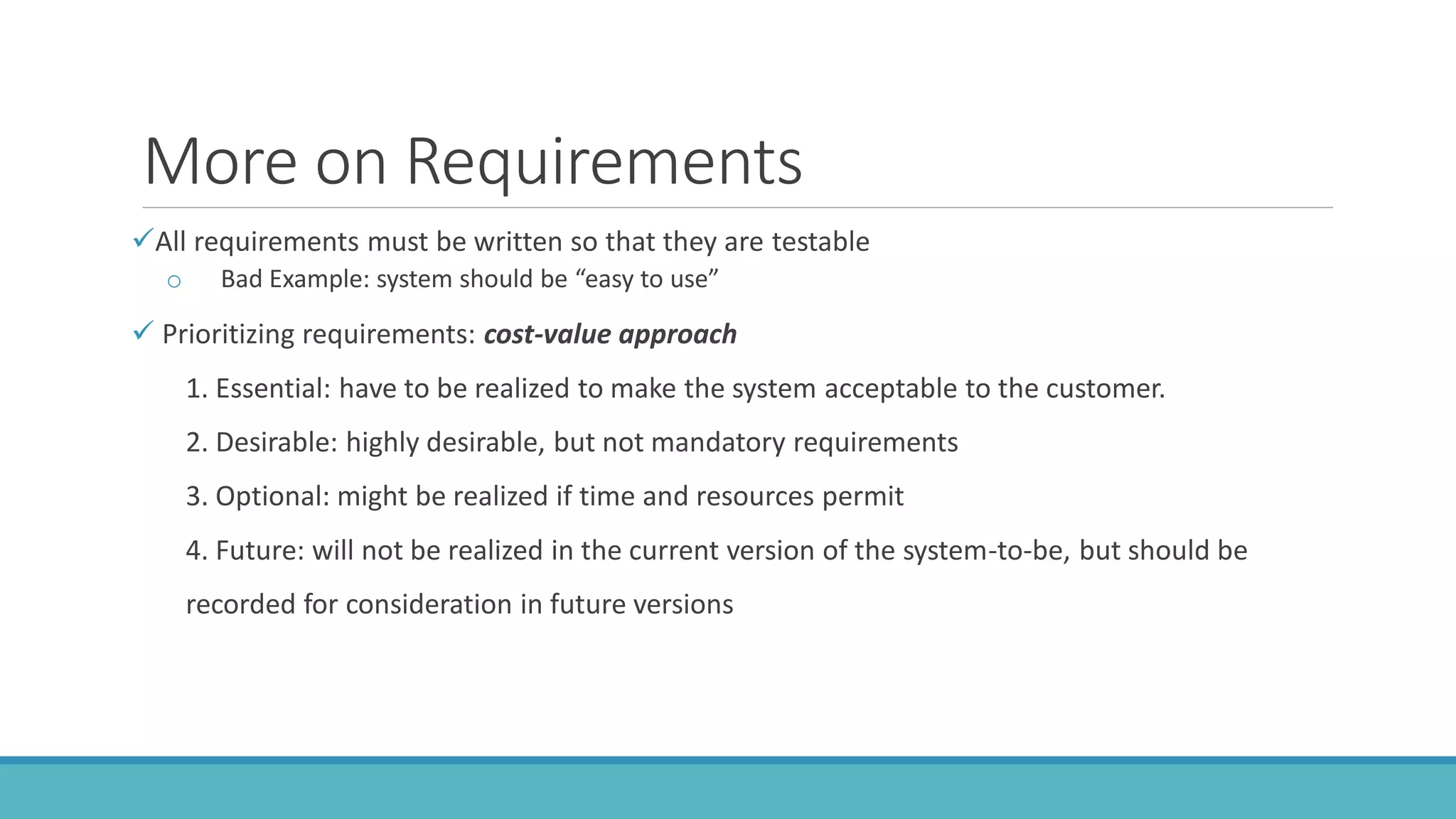
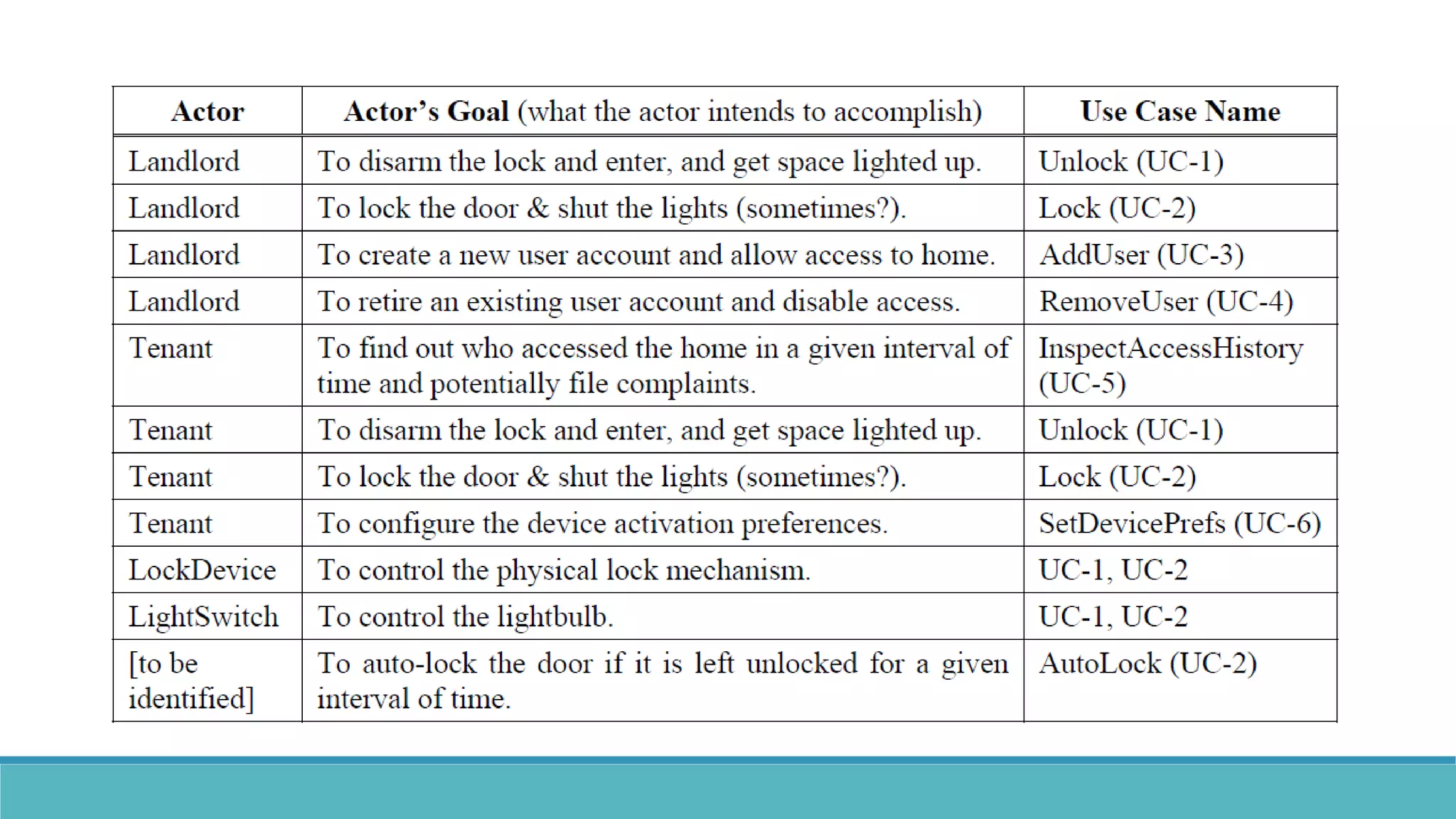
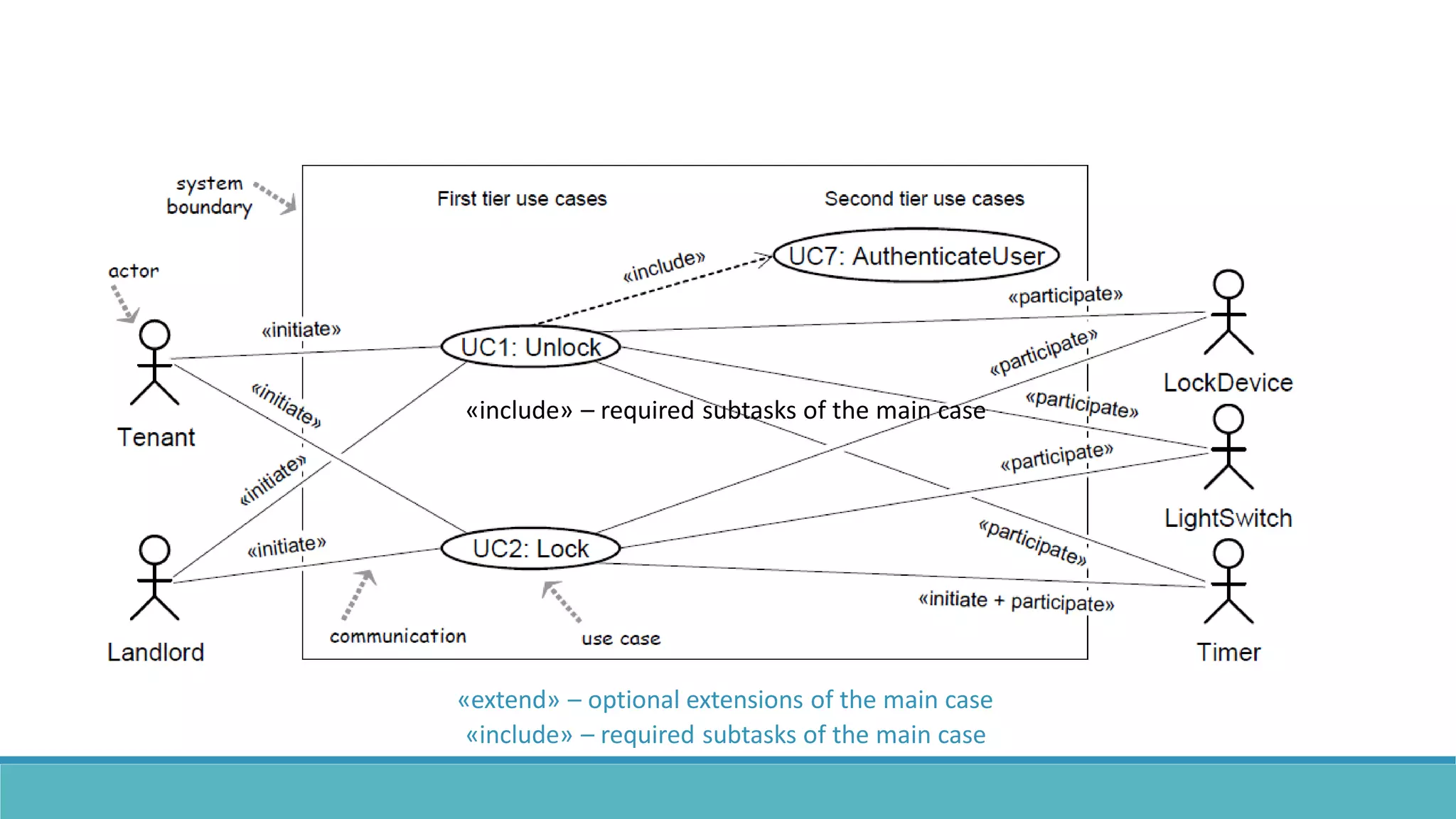
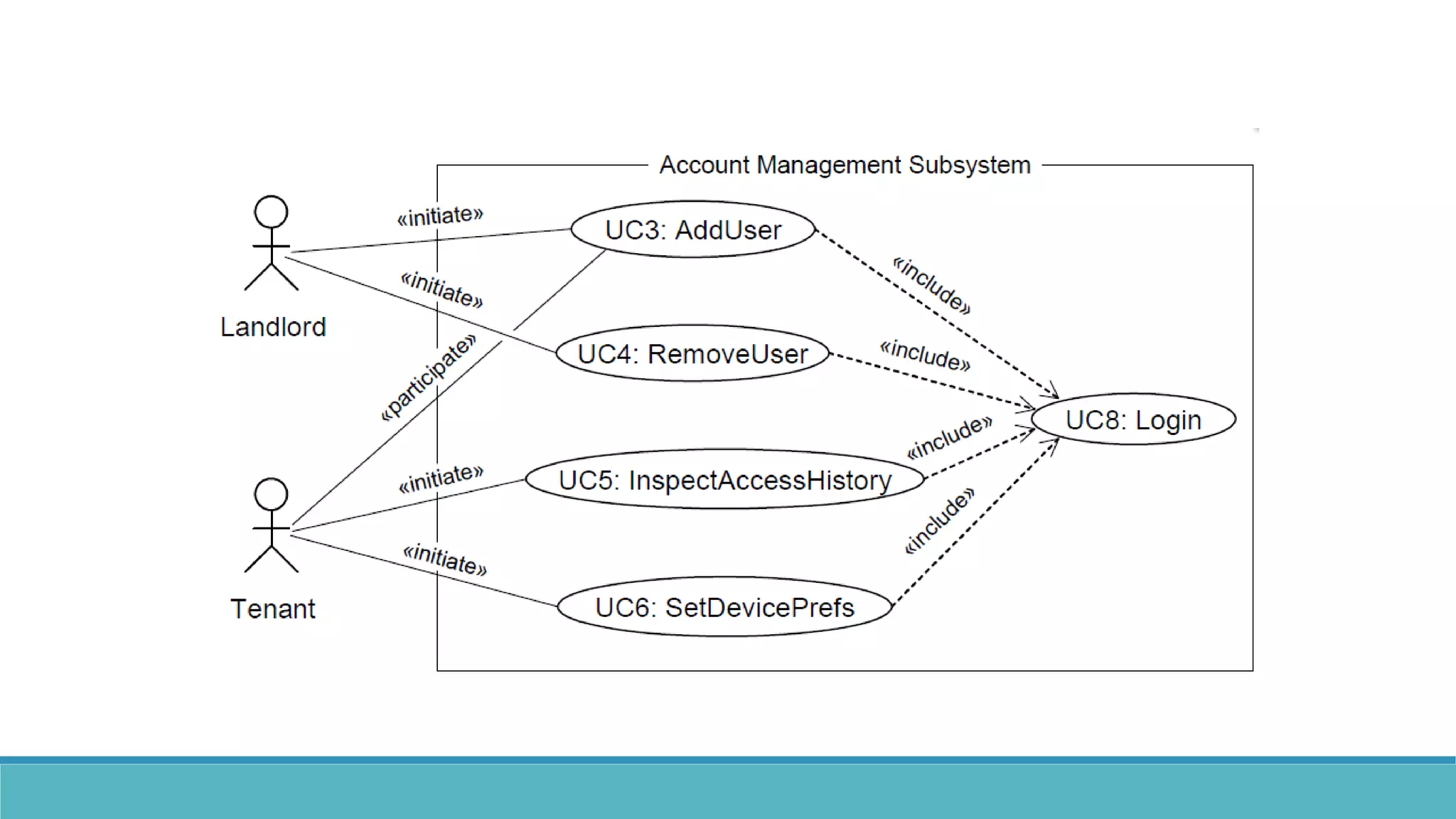
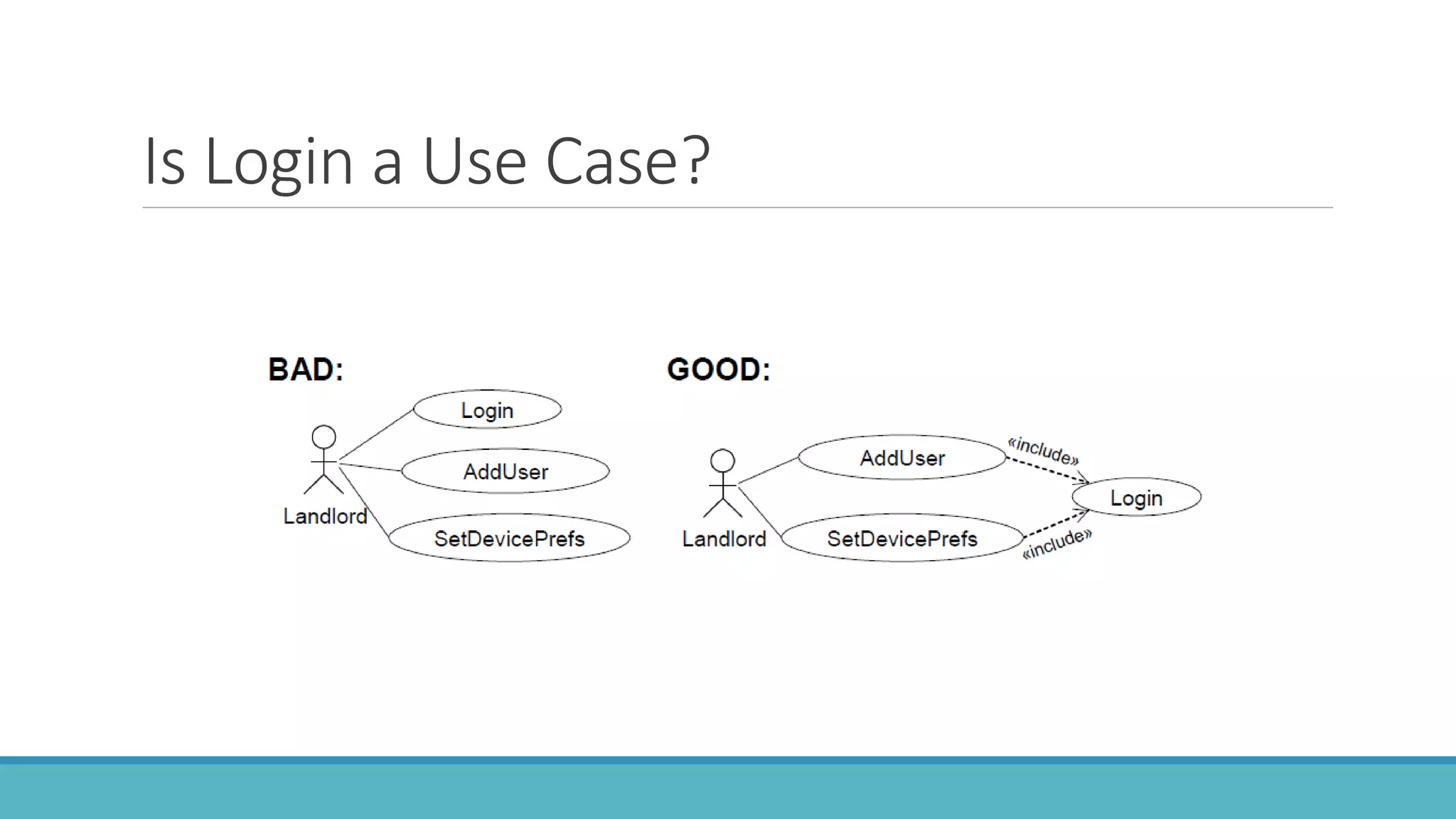
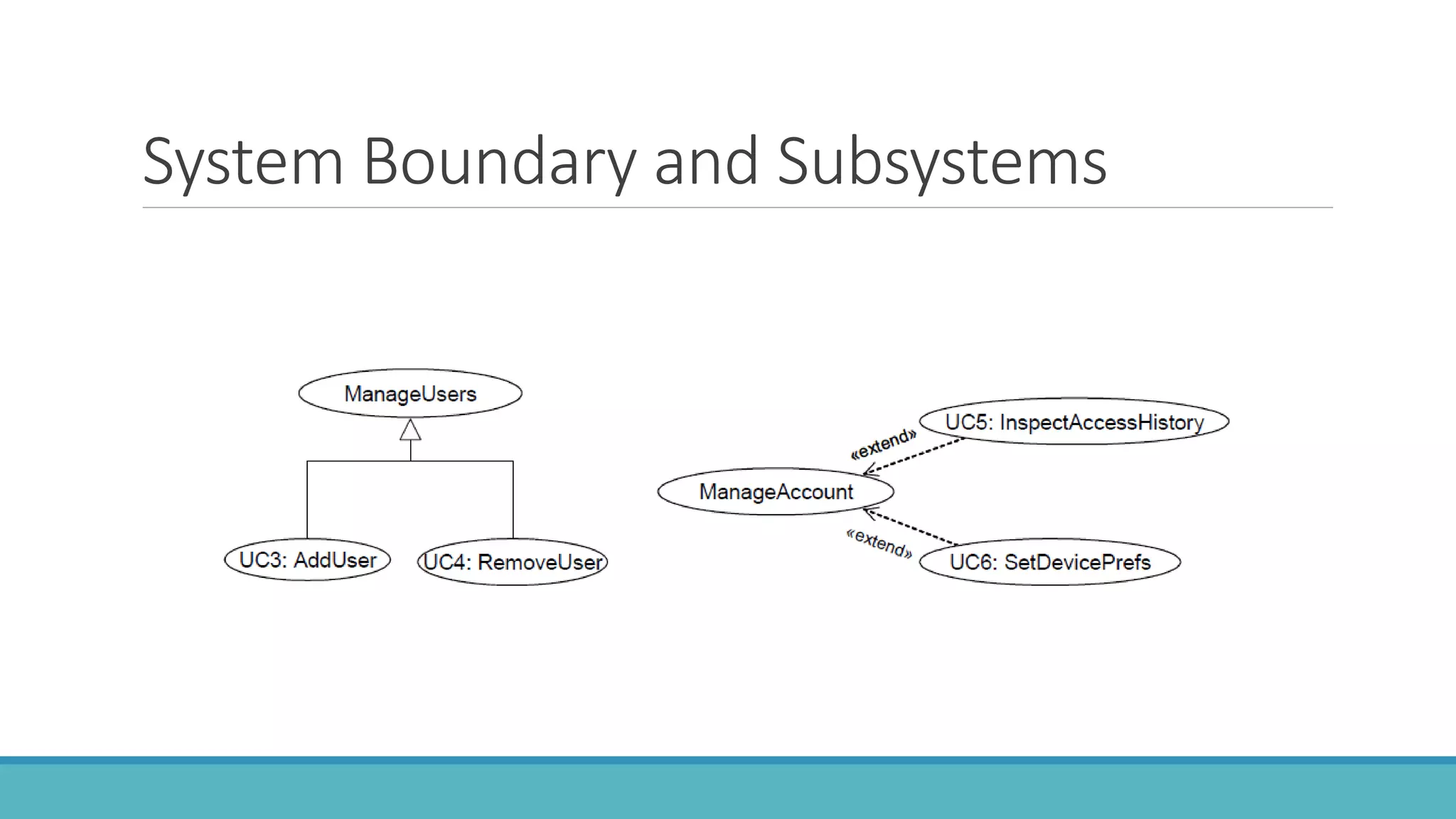
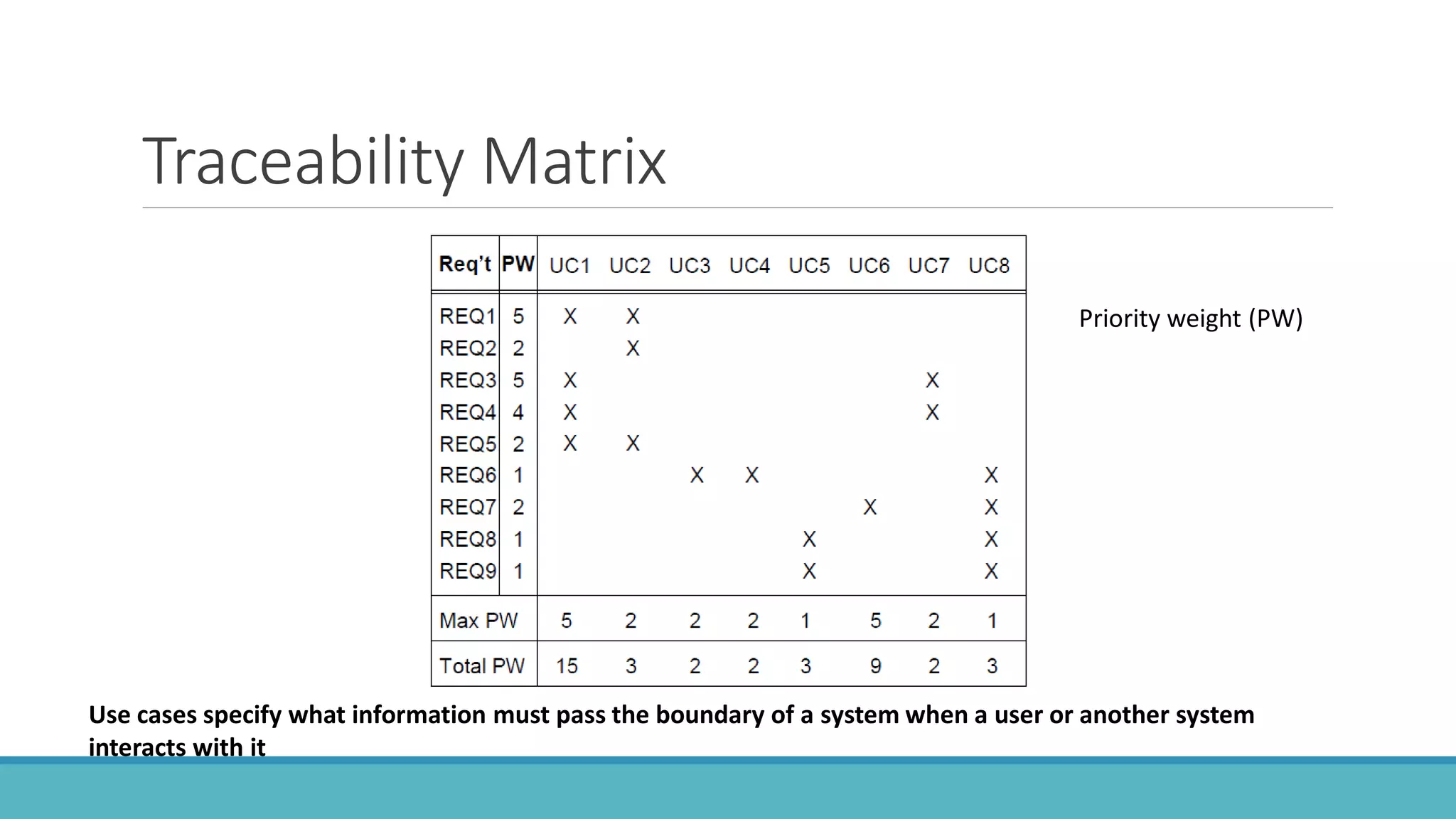
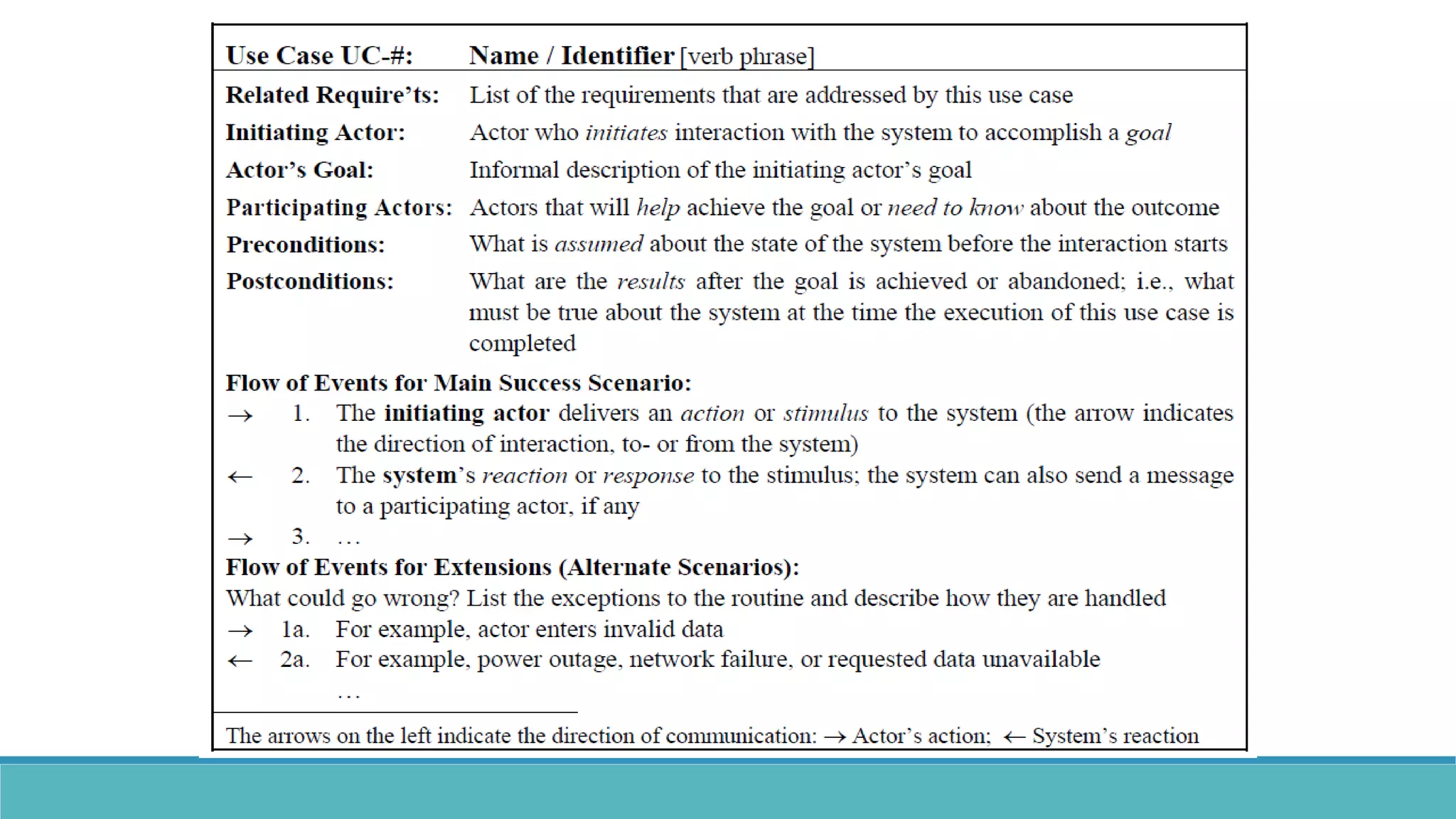
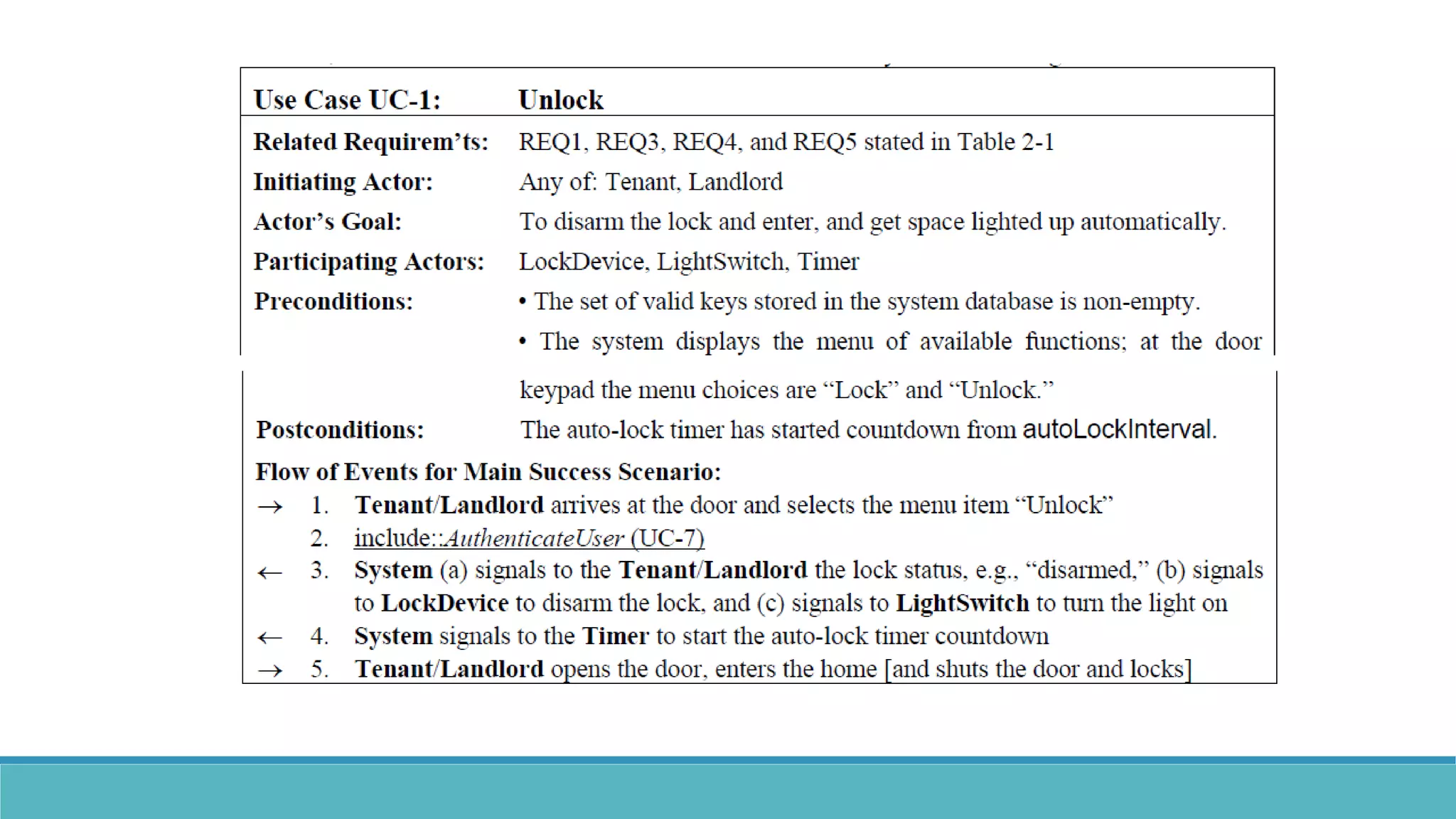
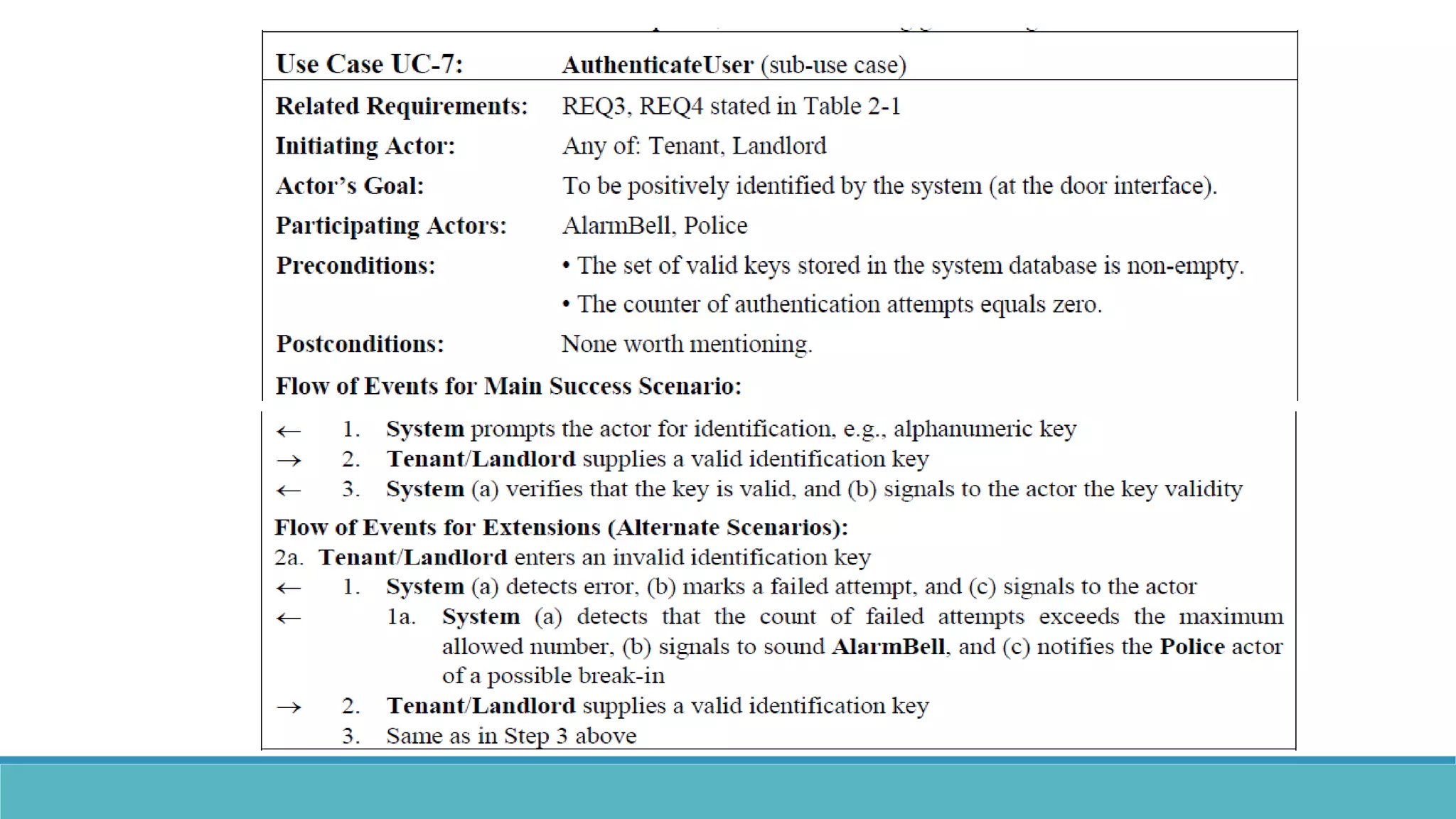
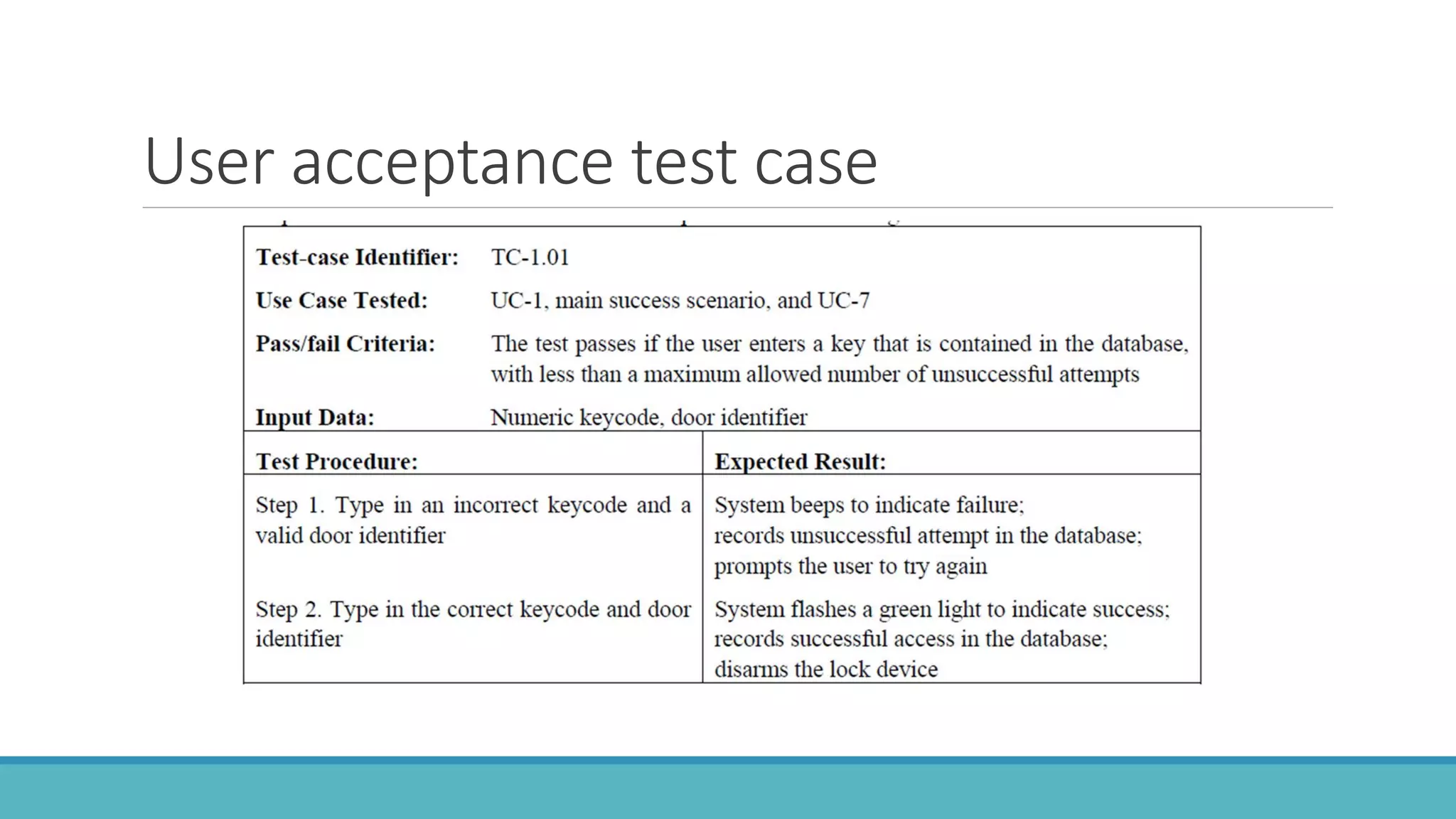
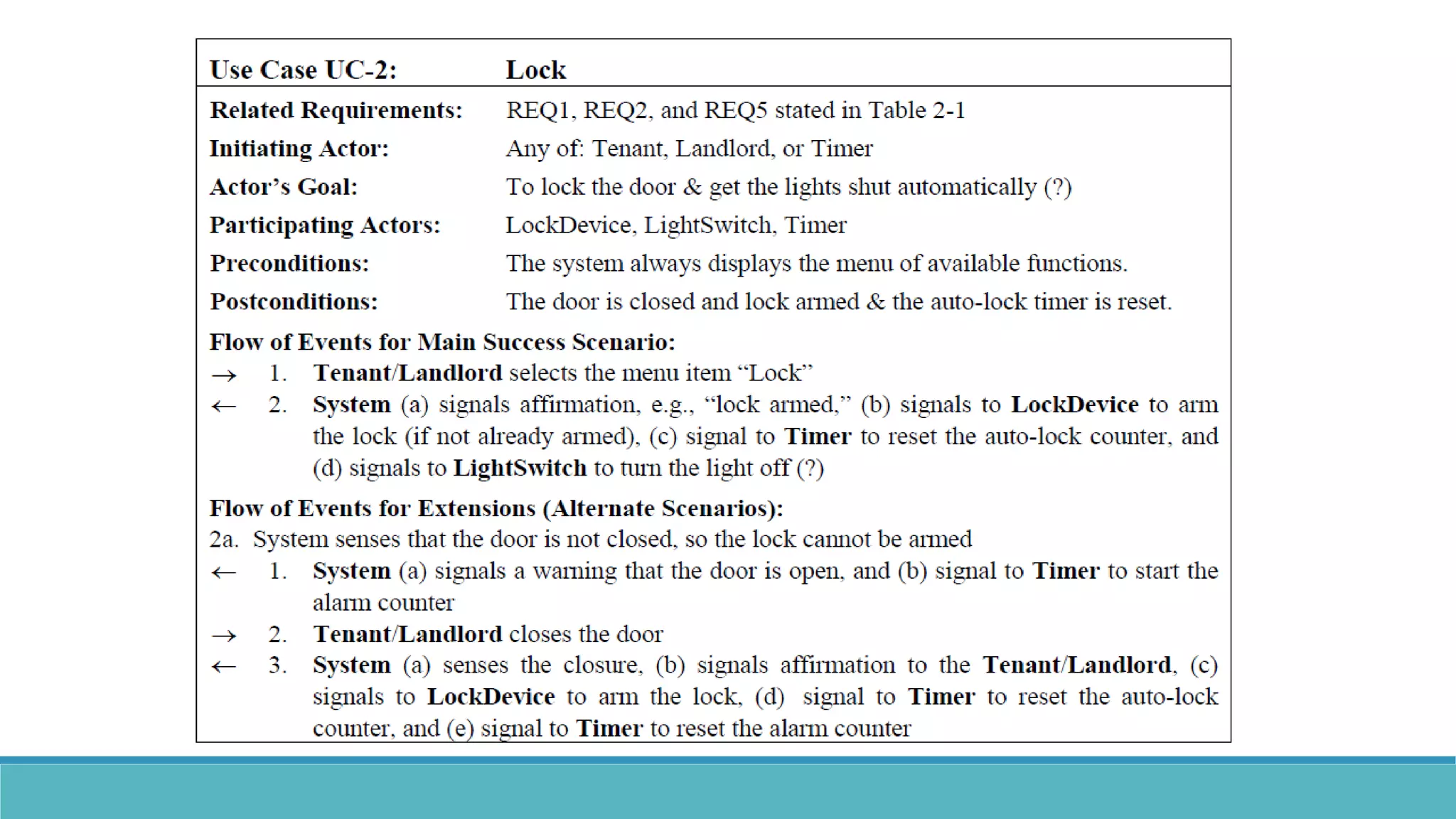
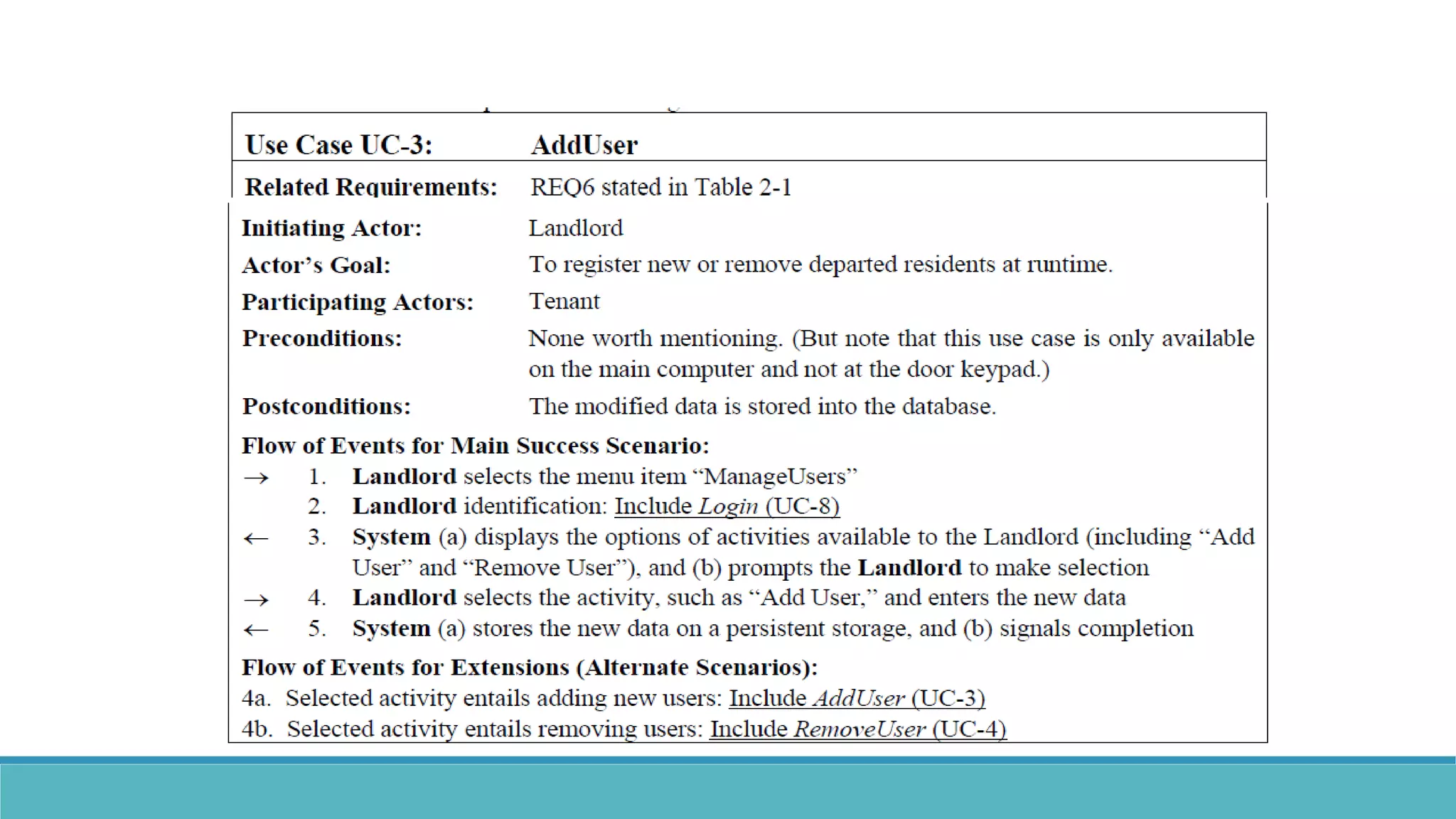
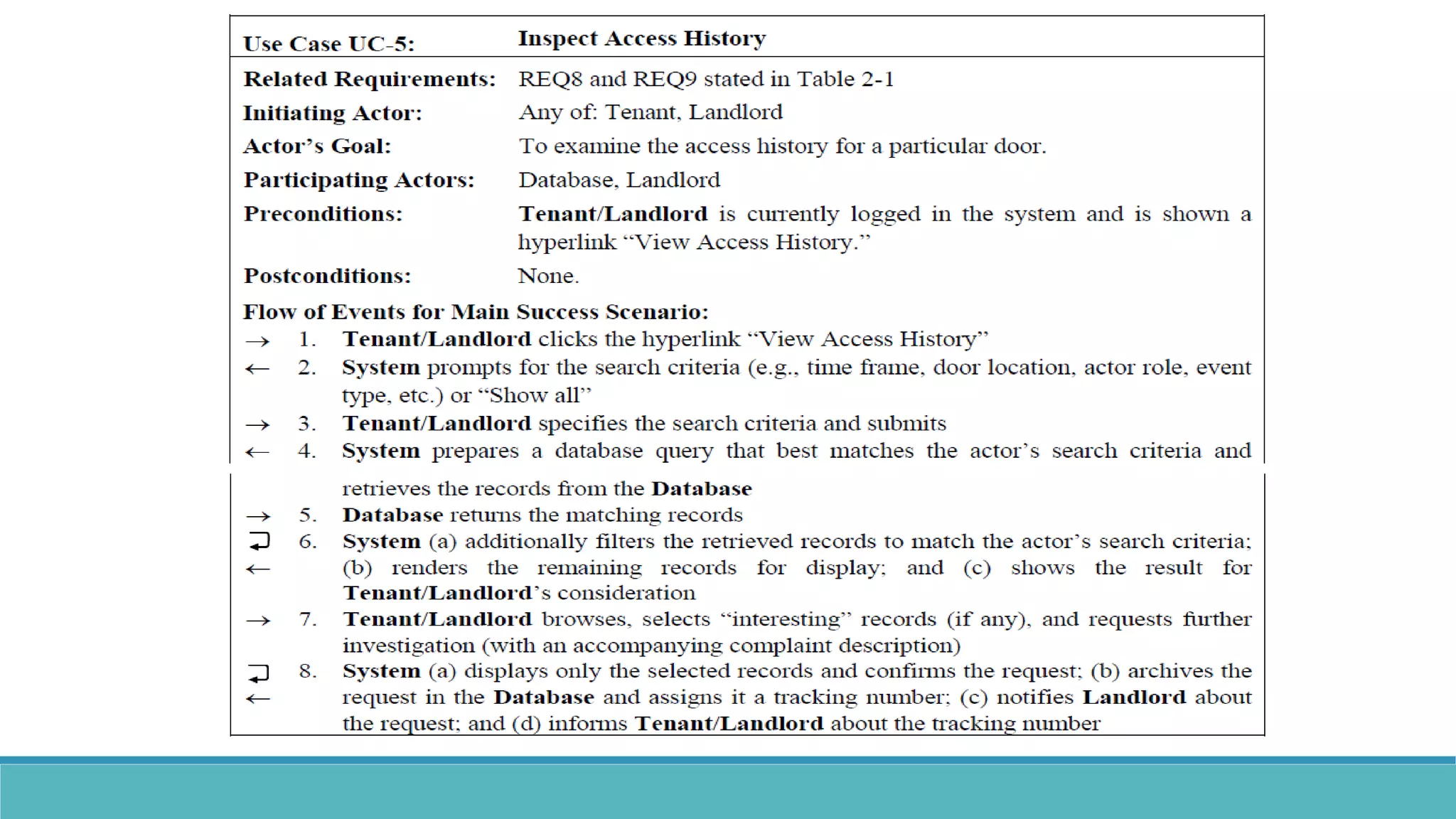
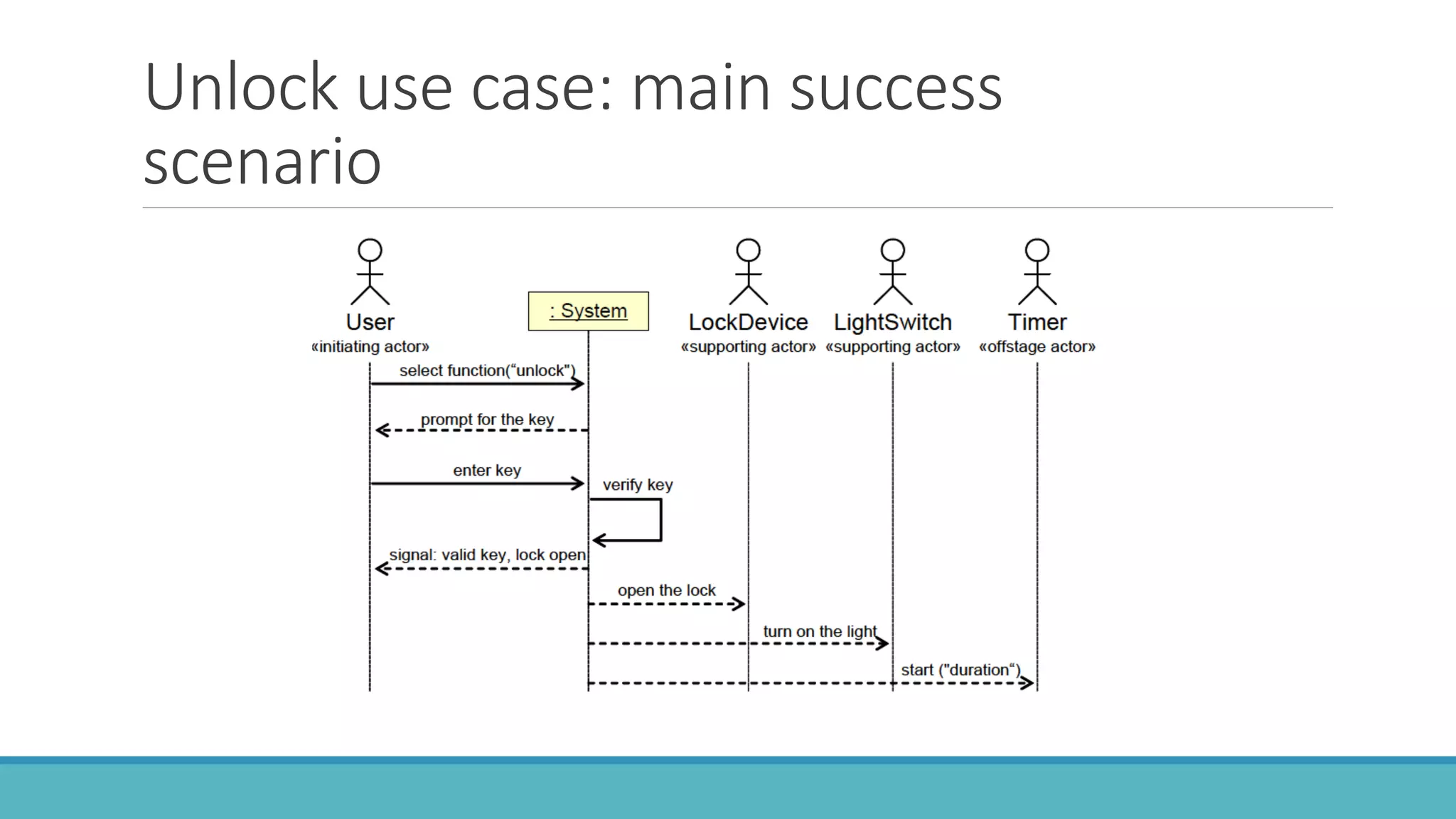
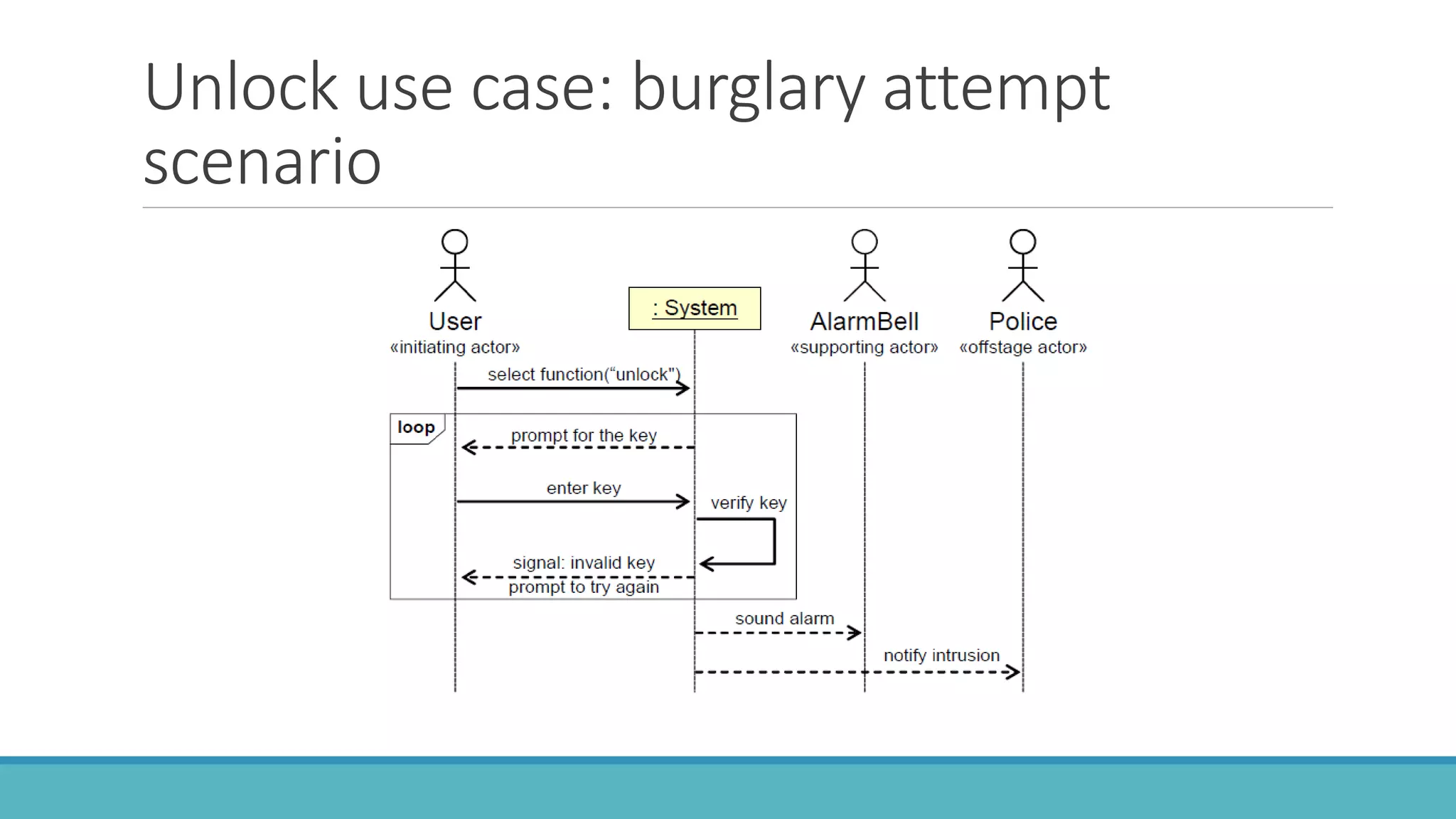
Use case modeling involves describing how users will interact with a system to achieve goals. A use case represents a dialog between a user and the system, specifying what information must pass between them without detailing the system's internal workings. Each use case should have a name that includes a verb describing the user's goal. Actors represent people or systems that interact with the system-to-be to accomplish responsibilities. Sequence diagrams visually depict the information exchanged between actors and the system in specific use case scenarios.