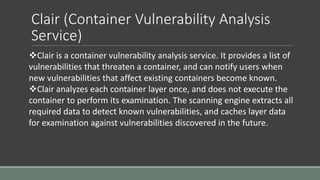
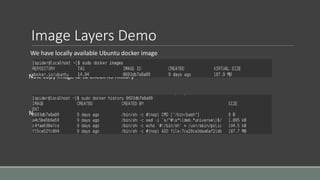
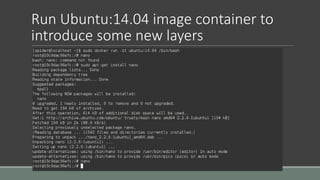
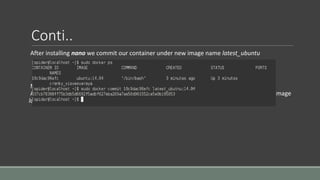
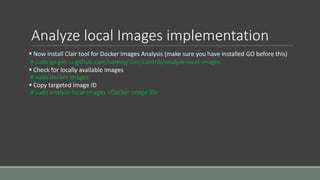
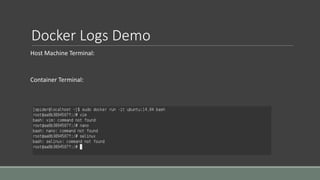
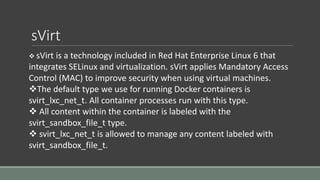
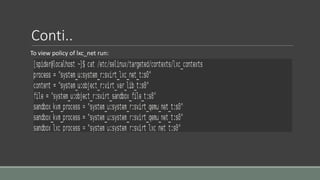
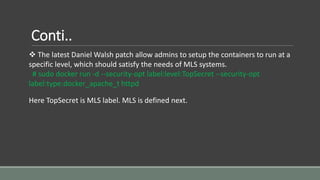
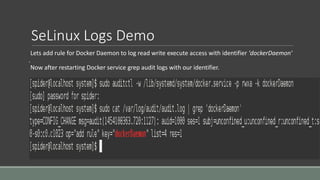
Clair is a container vulnerability analysis service that scans container layers to detect known vulnerabilities without executing the container. It provides a list of vulnerabilities that threaten each container. The analyze-local-images tool allows analyzing local Docker images with Clair by copying an image ID. Logging multiple Docker containers can be automated by sending their logs to Logstash for indexing in Elasticsearch with a Kibana frontend, monitored alongside metrics from Cadvisor. SELinux applies Mandatory Access Control to Docker containers using the svirt_lxc_net_t type to improve security. It isolates processes but allows reading from most host labels.