The document discusses cyber security in banks and outlines several key points:
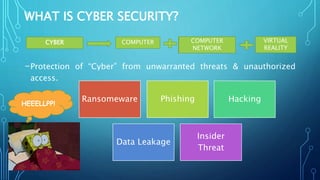
1) It defines cyber security as protecting computer networks and data from unauthorized access and threats.
2) Banks must comply with regulations from financial regulators that require installing security measures like firewalls, encryption, and audits to prevent cyber attacks.
3) The legal protections for banks include the Electronic Transactions Act which recognizes unauthorized access and code alterations as offenses but some say the punishments are too minimal.
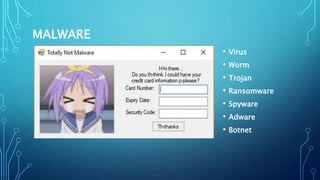
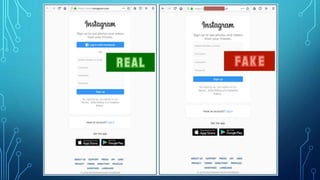
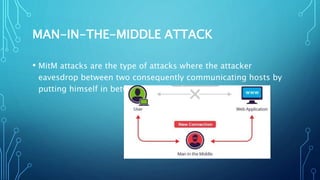
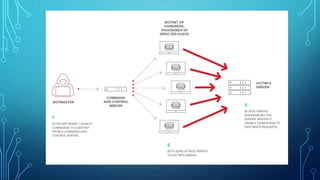
4) Major cyber attack types banks face include social engineering, malware, phishing, man-in-the-middle attacks, denial-of-service attacks, and password attacks.