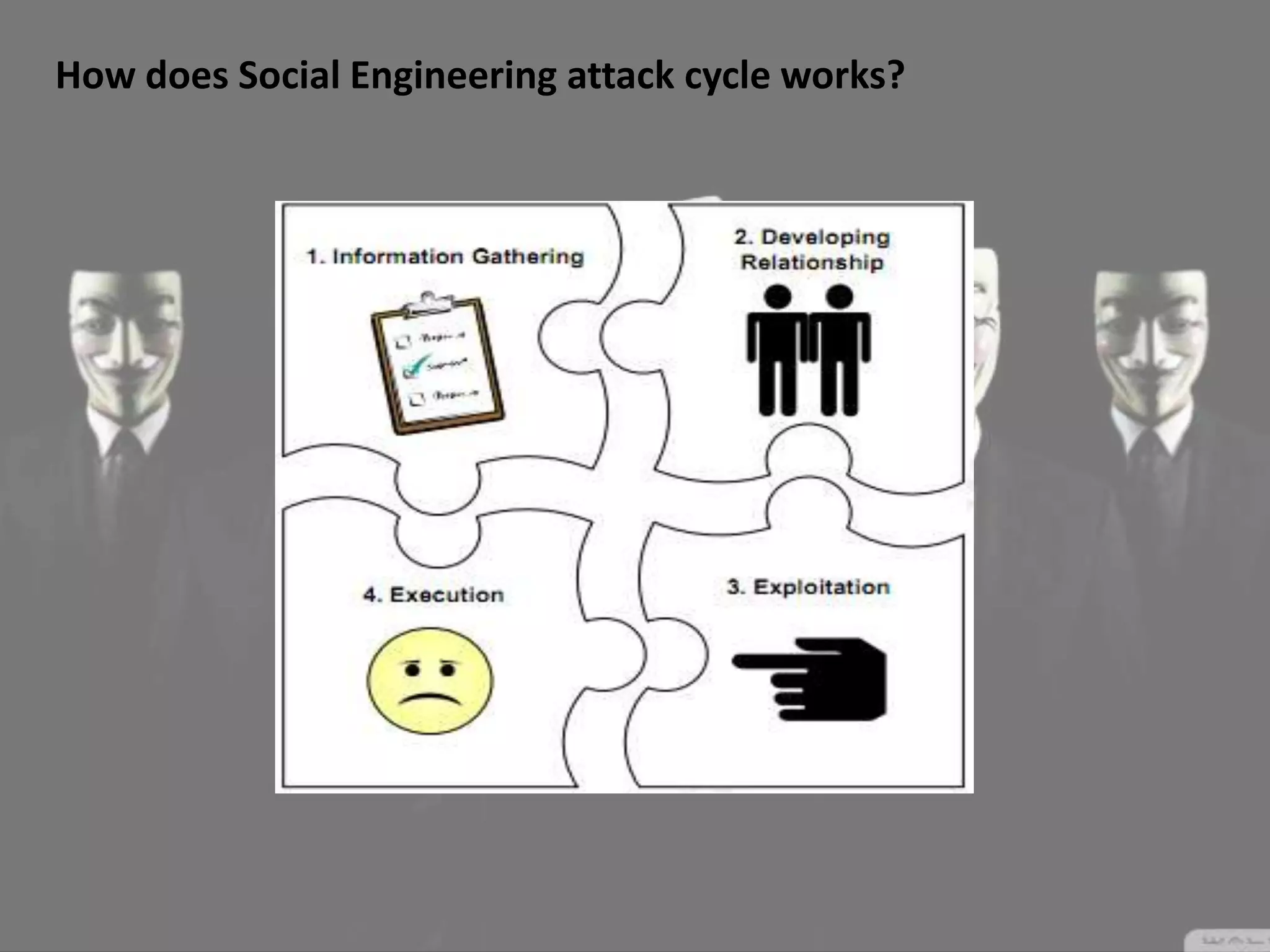
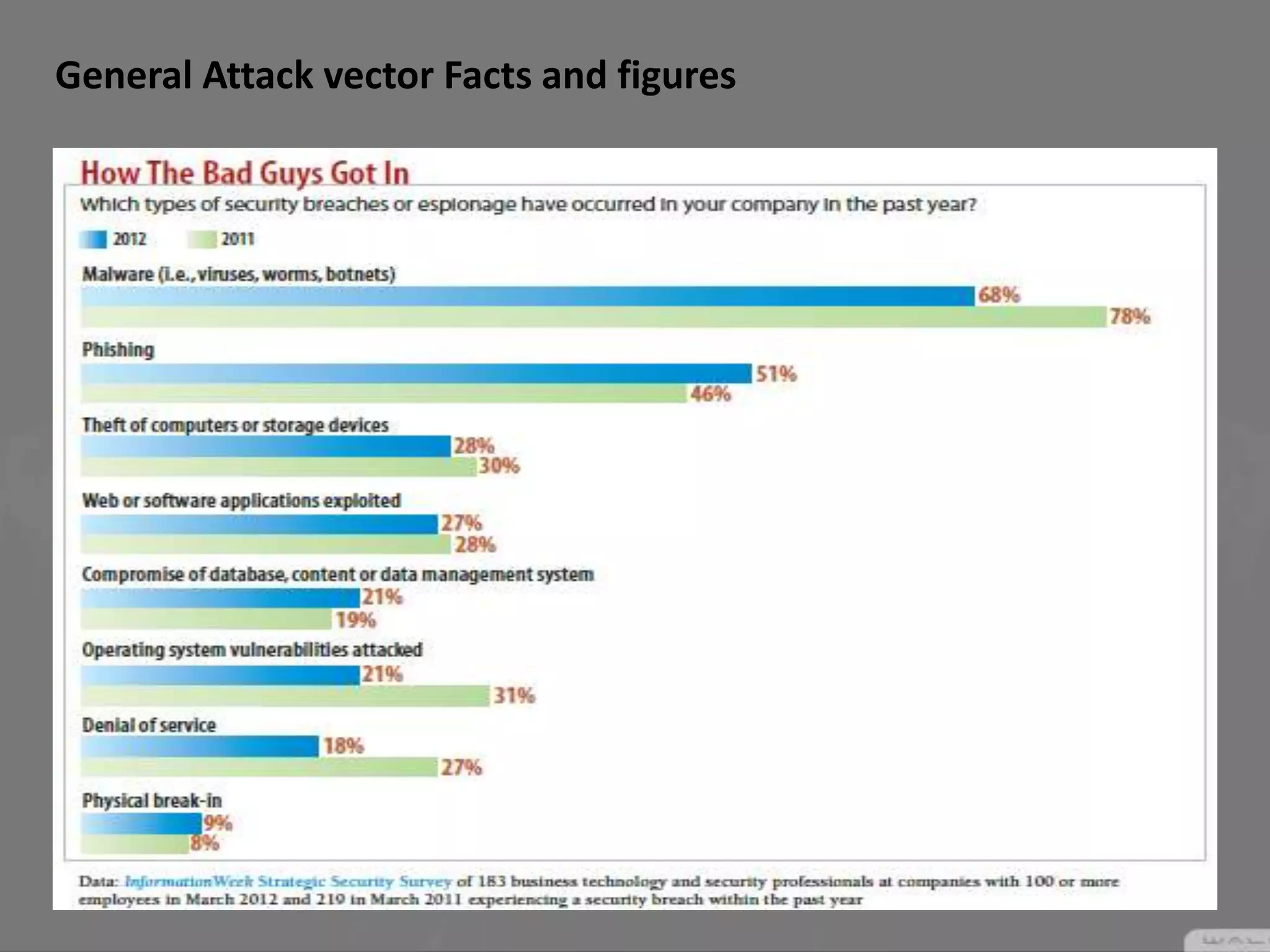
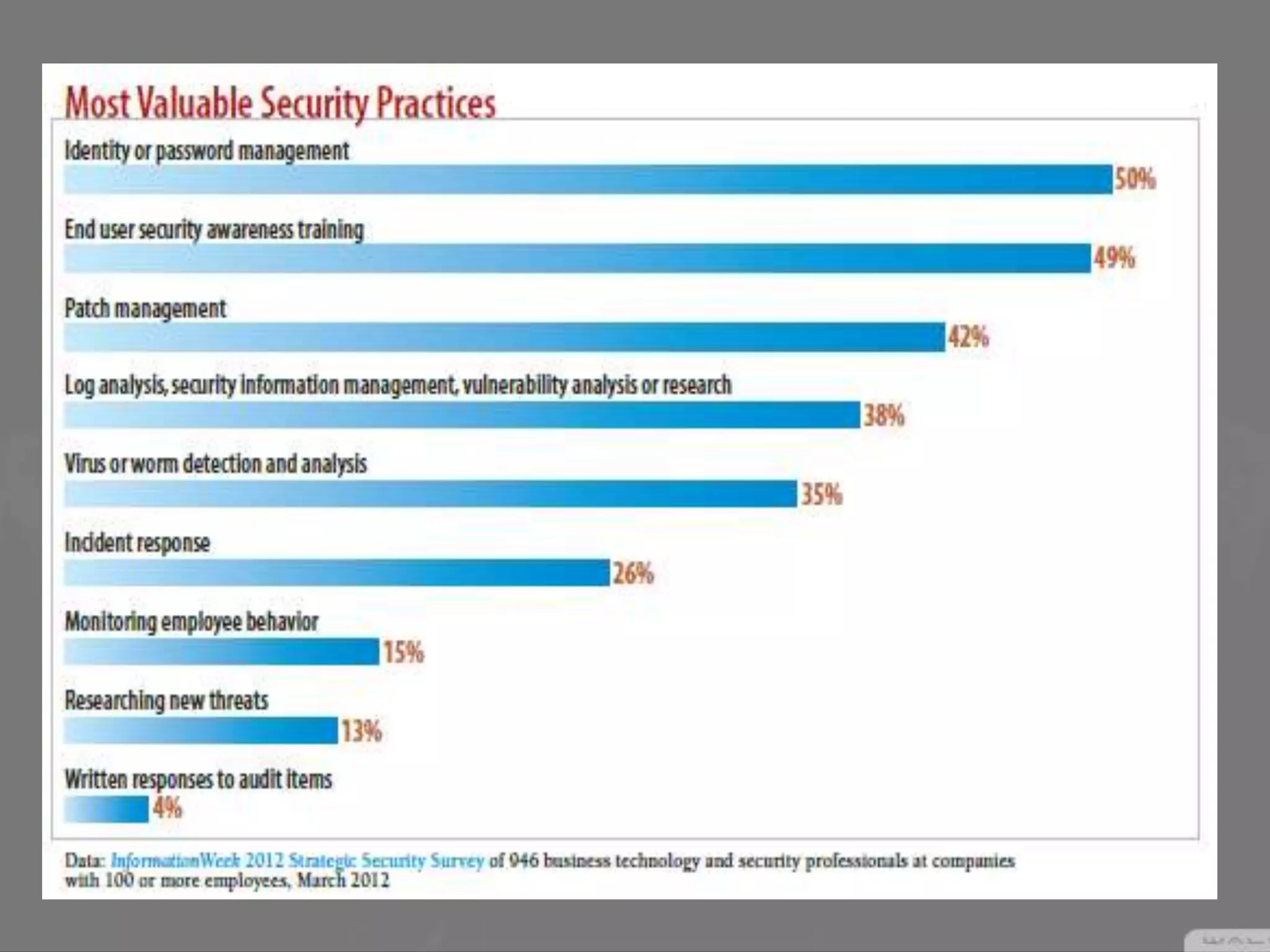
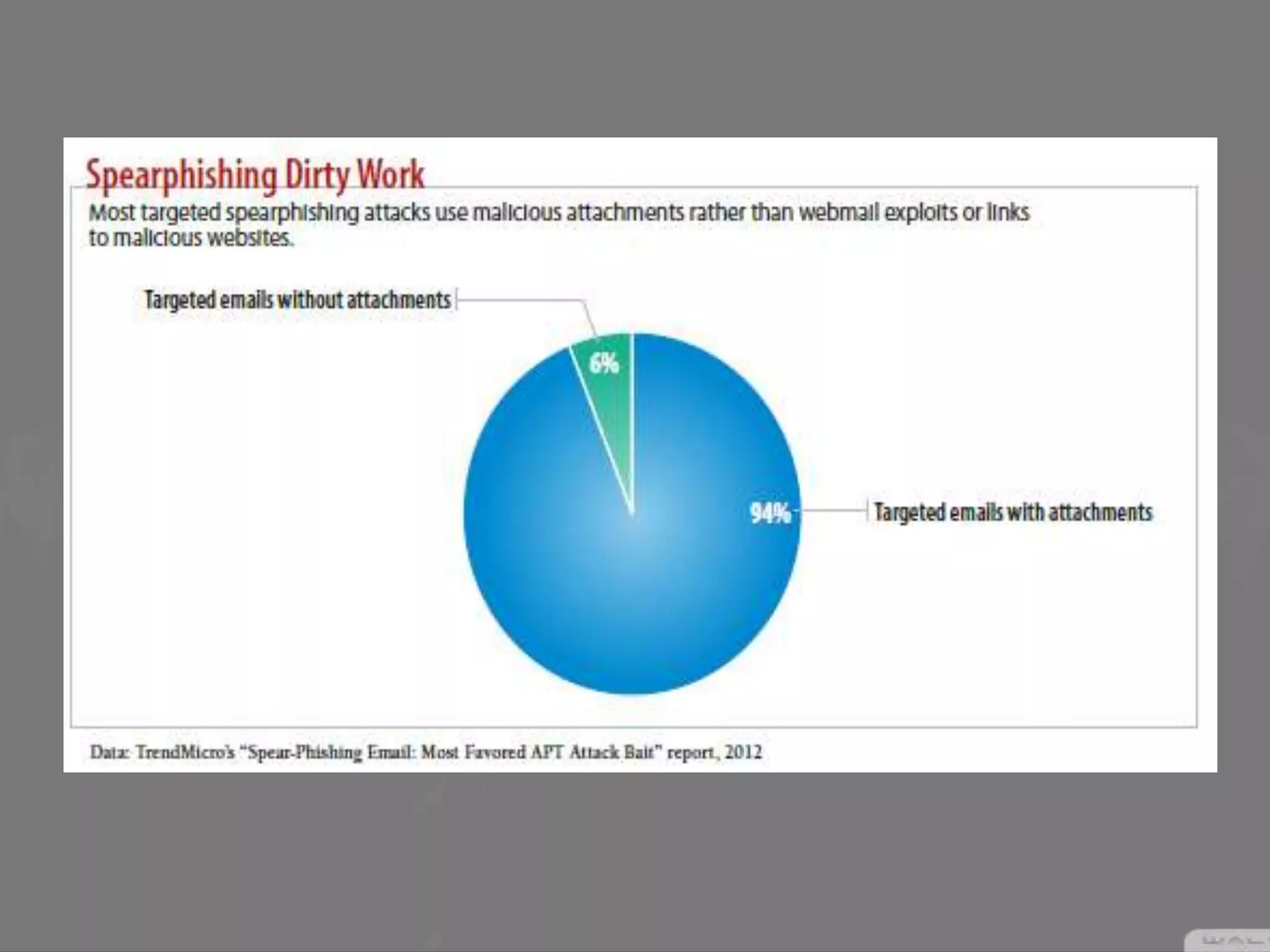
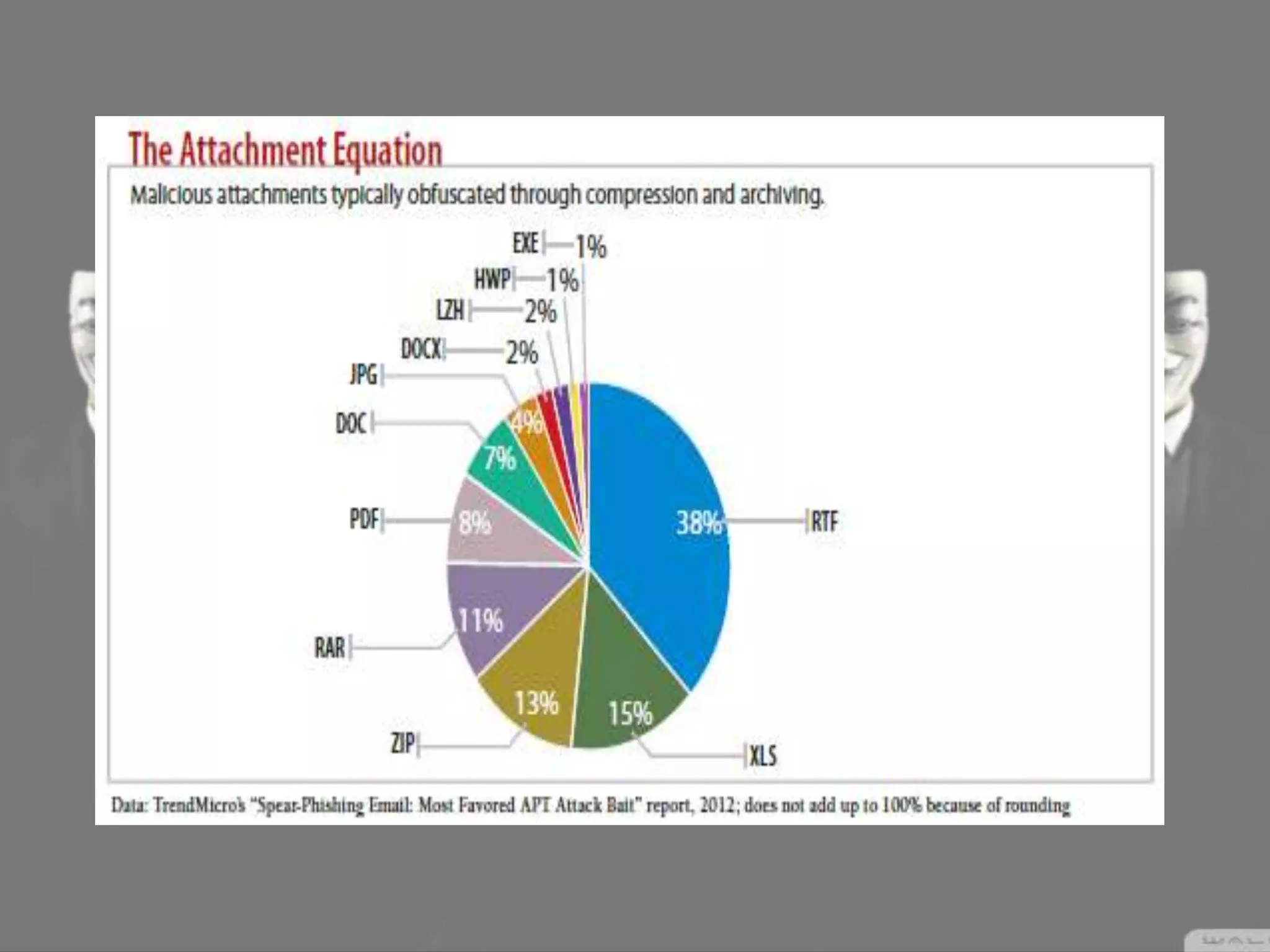
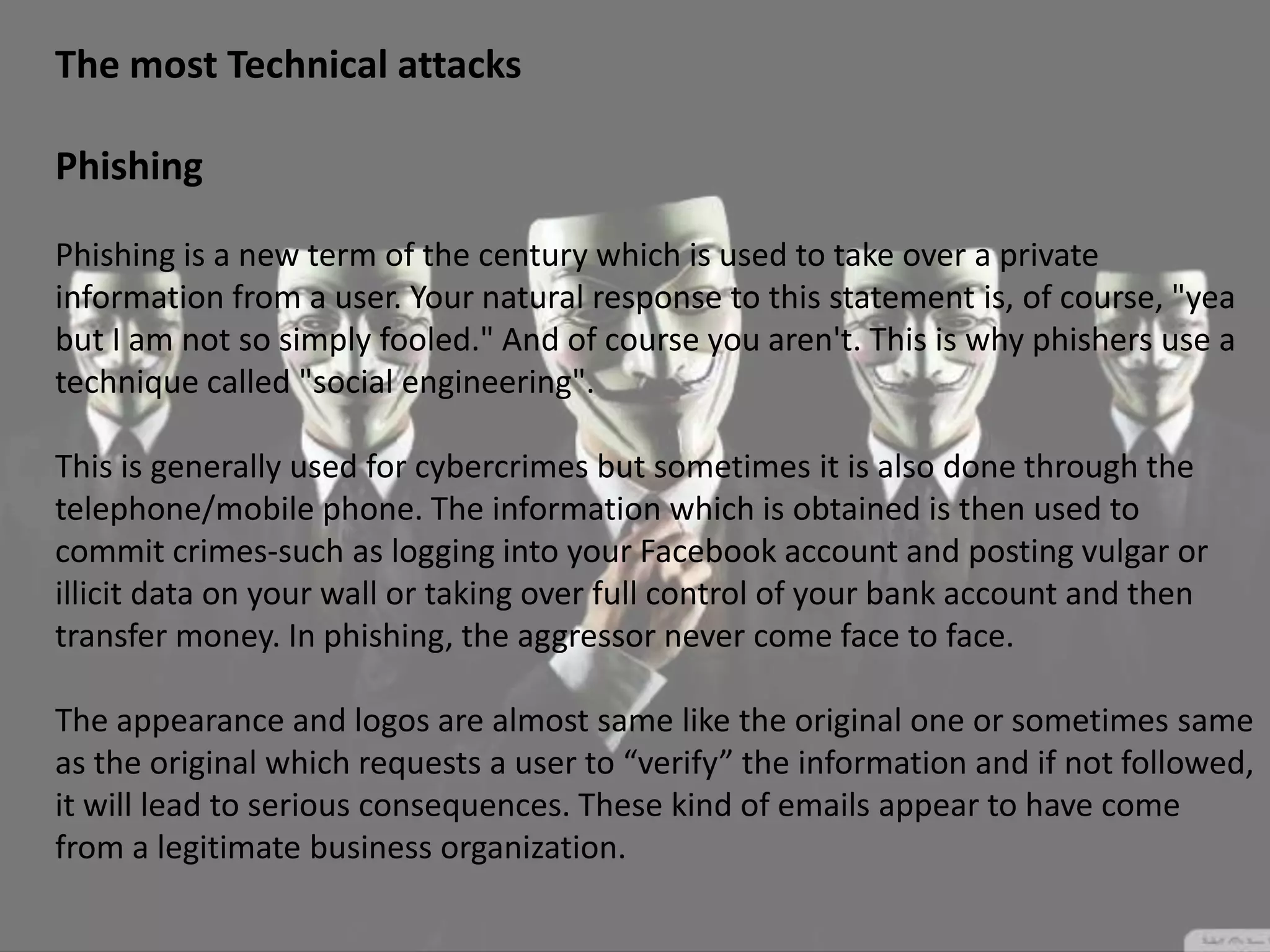
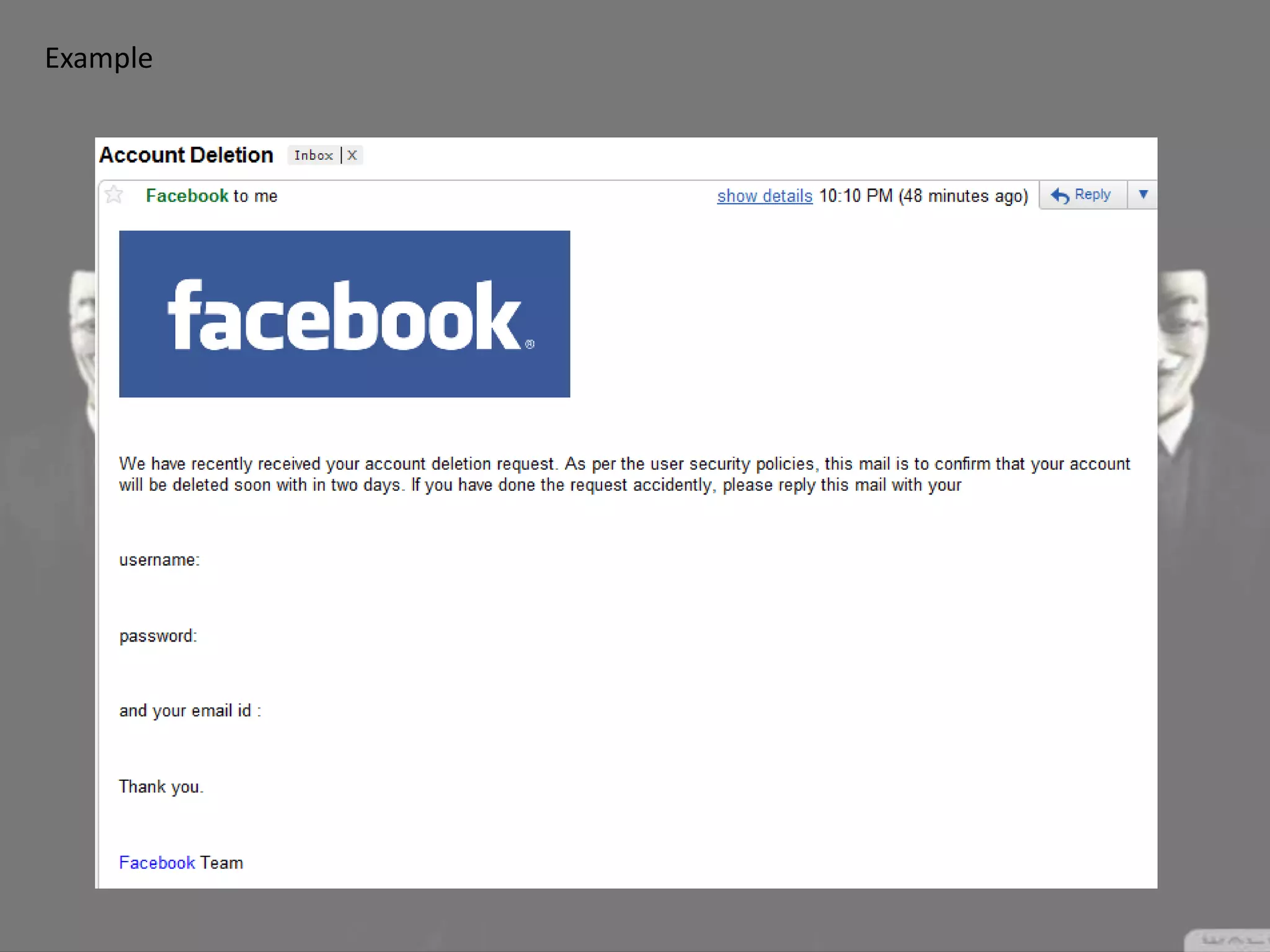
Social engineering is a type of attack that manipulates people into revealing sensitive information or performing actions that violate security policies. It works by exploiting human trust and the natural tendency to help others. Attackers first gather information about targets, then develop relationships to gain trust before exploiting that trust to obtain access or steal information. Common social engineering techniques include phishing emails and calls where attackers pretend to be from technical support. While no system can fully prevent social engineering, organizations can minimize risks by educating users and restricting what sensitive information users provide over the phone or to unknown parties.