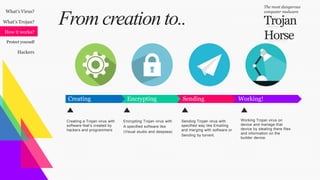
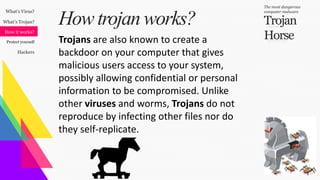
This document discusses Trojan malware and how to protect against it. It describes Trojans as dangerous viruses created by hackers to steal information like credit cards, emails, passwords, and files. Trojans can give hackers backdoor access to computers. They are often spread through email attachments and files. The document provides tips on protecting against Trojans such as using antivirus software, deleting unnecessary files, and avoiding unknown links or USB devices. It also outlines different types of hackers including black hat, gray hat, and white hat hackers.