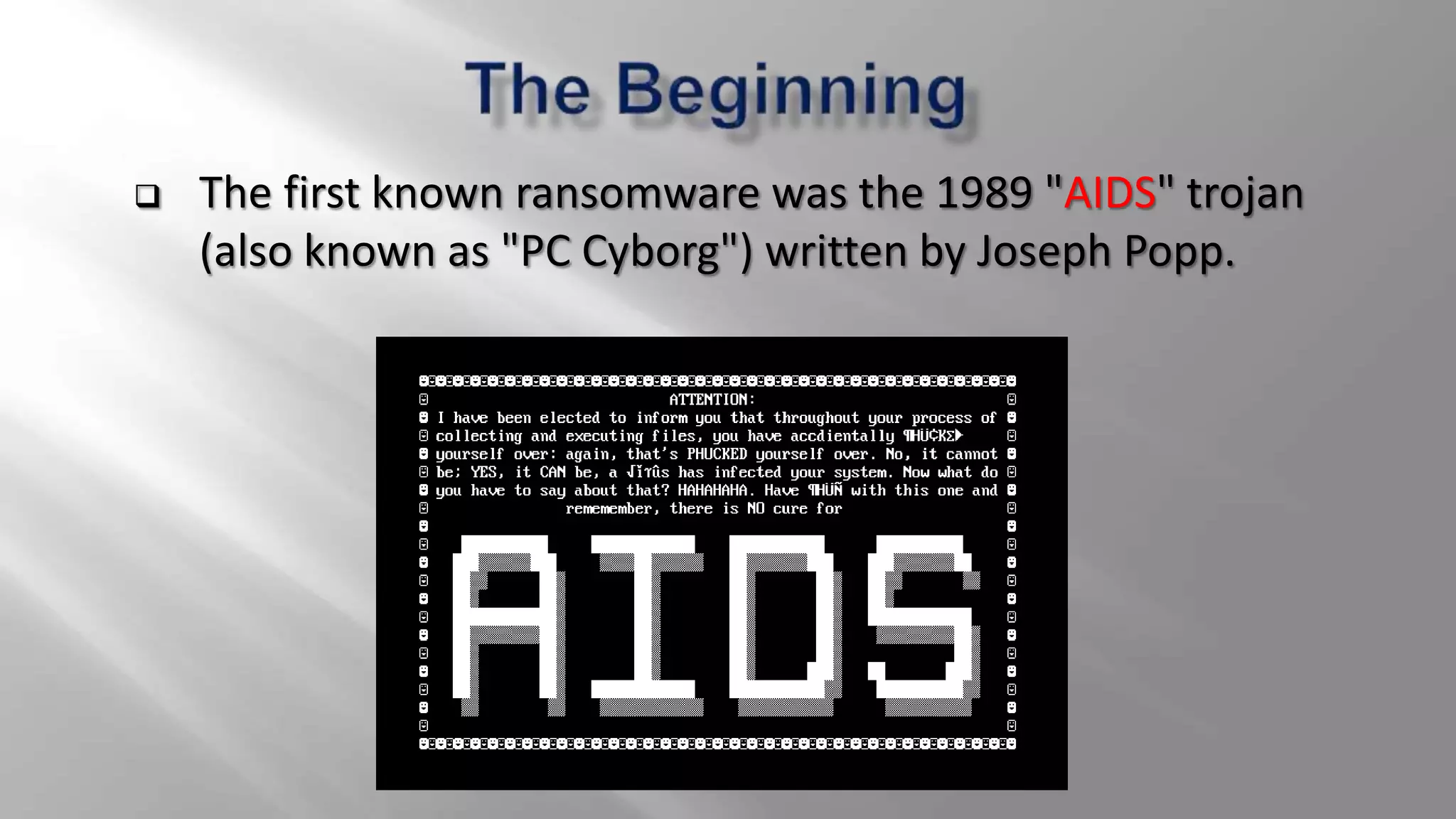
The document discusses ransomware, a type of malware that extorts money from users by locking or encrypting their files. It highlights notable ransomware attacks, particularly the 2017 WannaCry attack that affected over 200,000 computers globally, and offers prevention and recovery measures. Key advice includes keeping software updated, avoiding suspicious emails, and understanding the nature of different ransomware types.