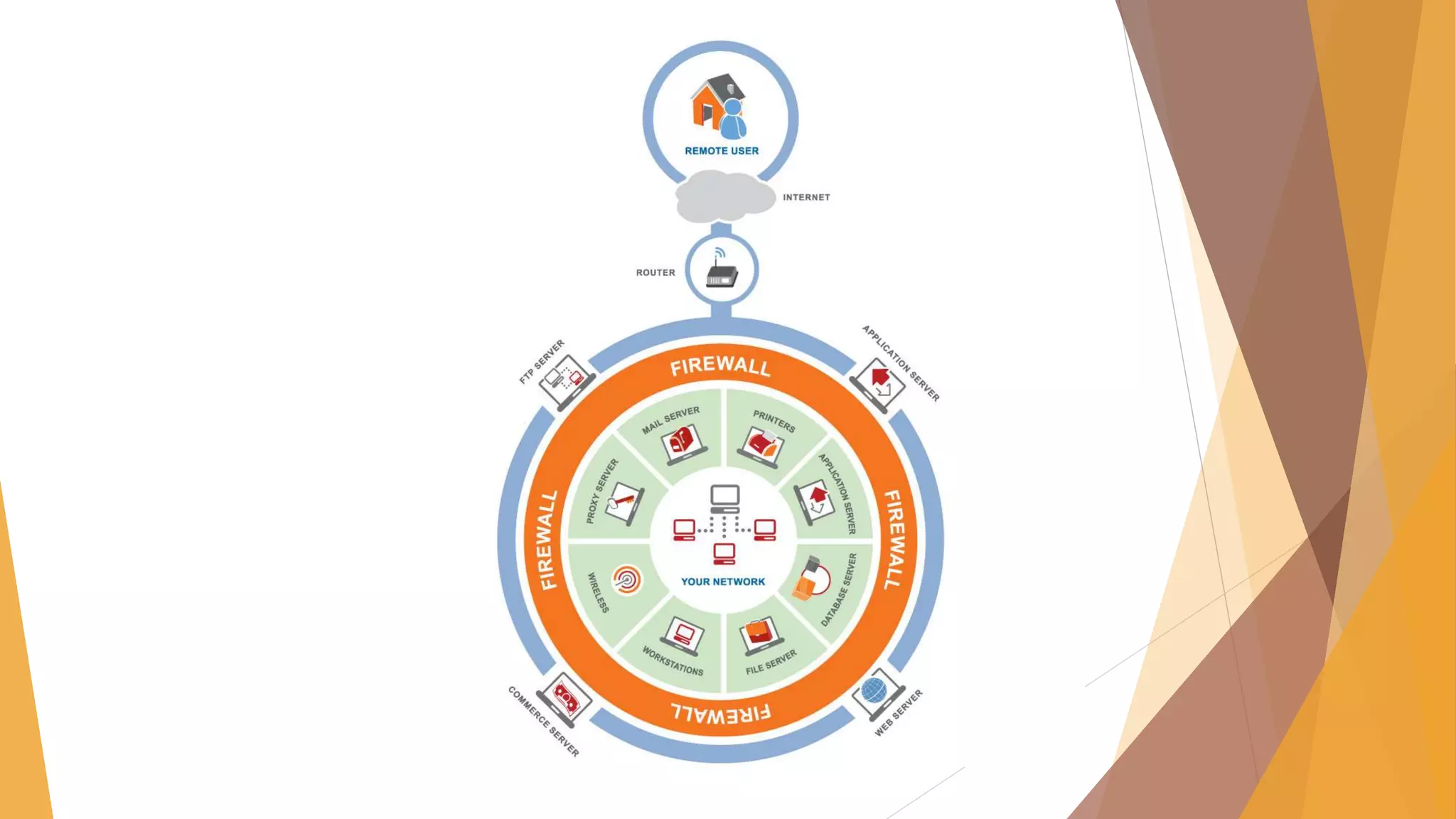
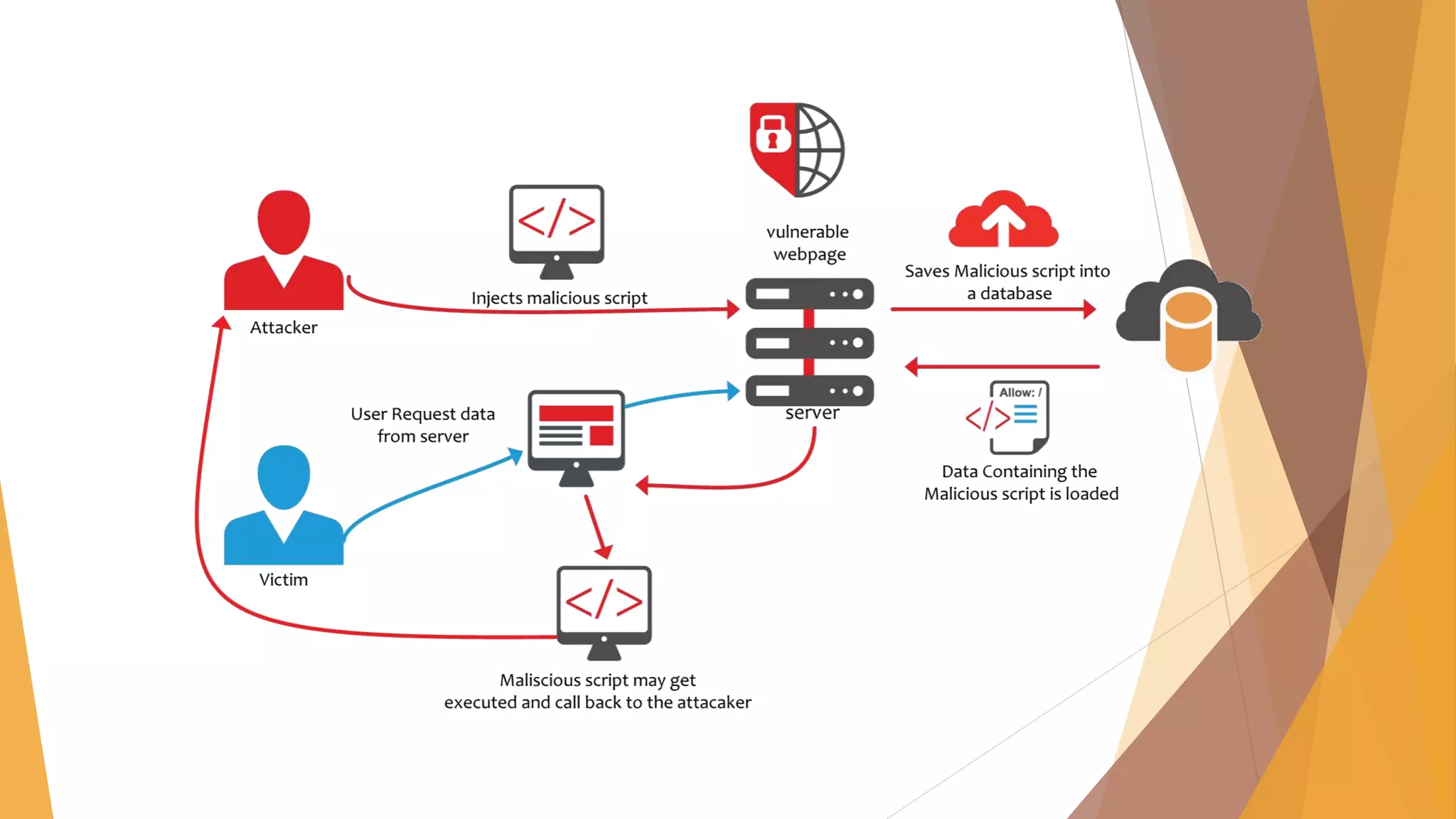
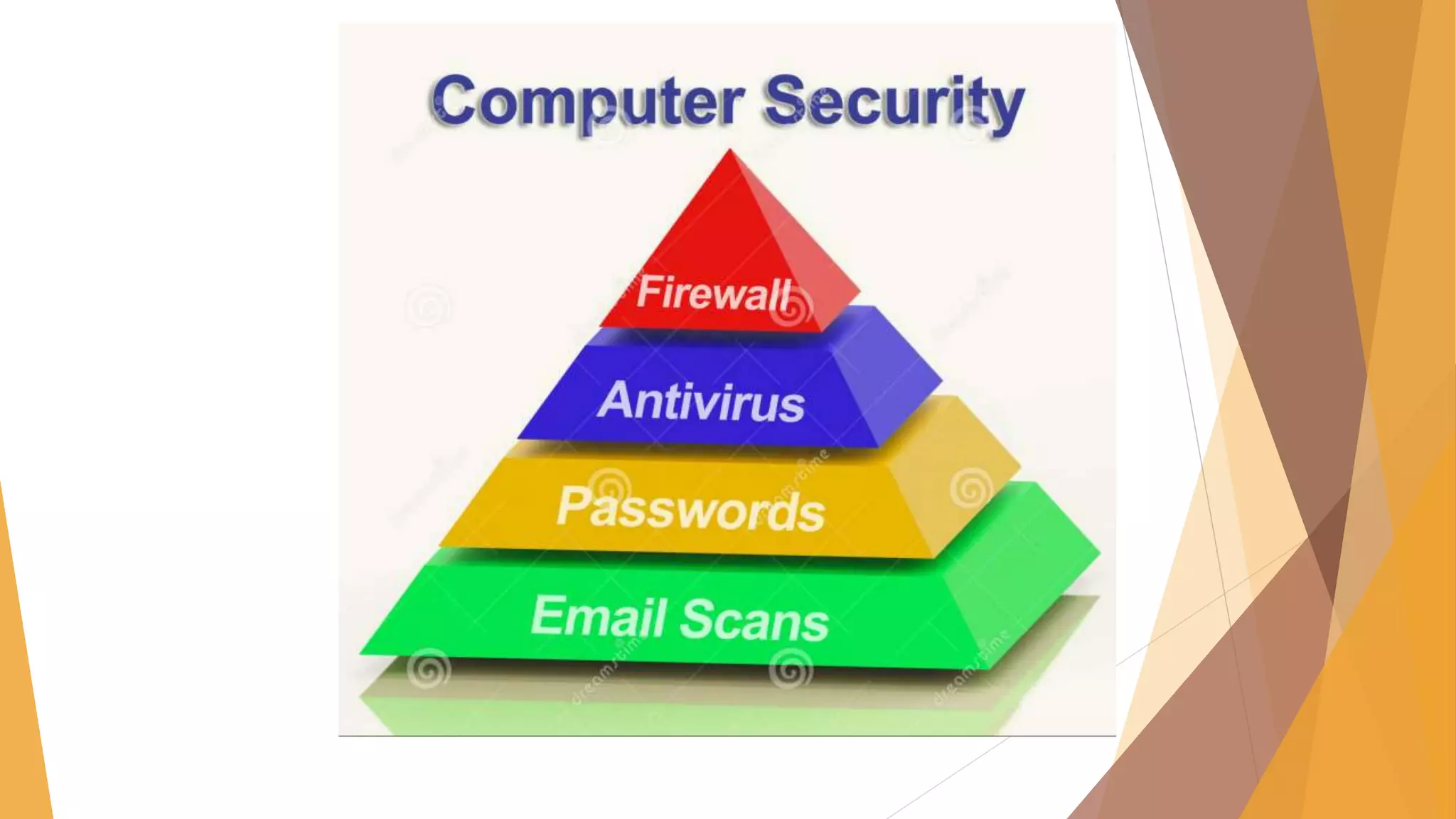
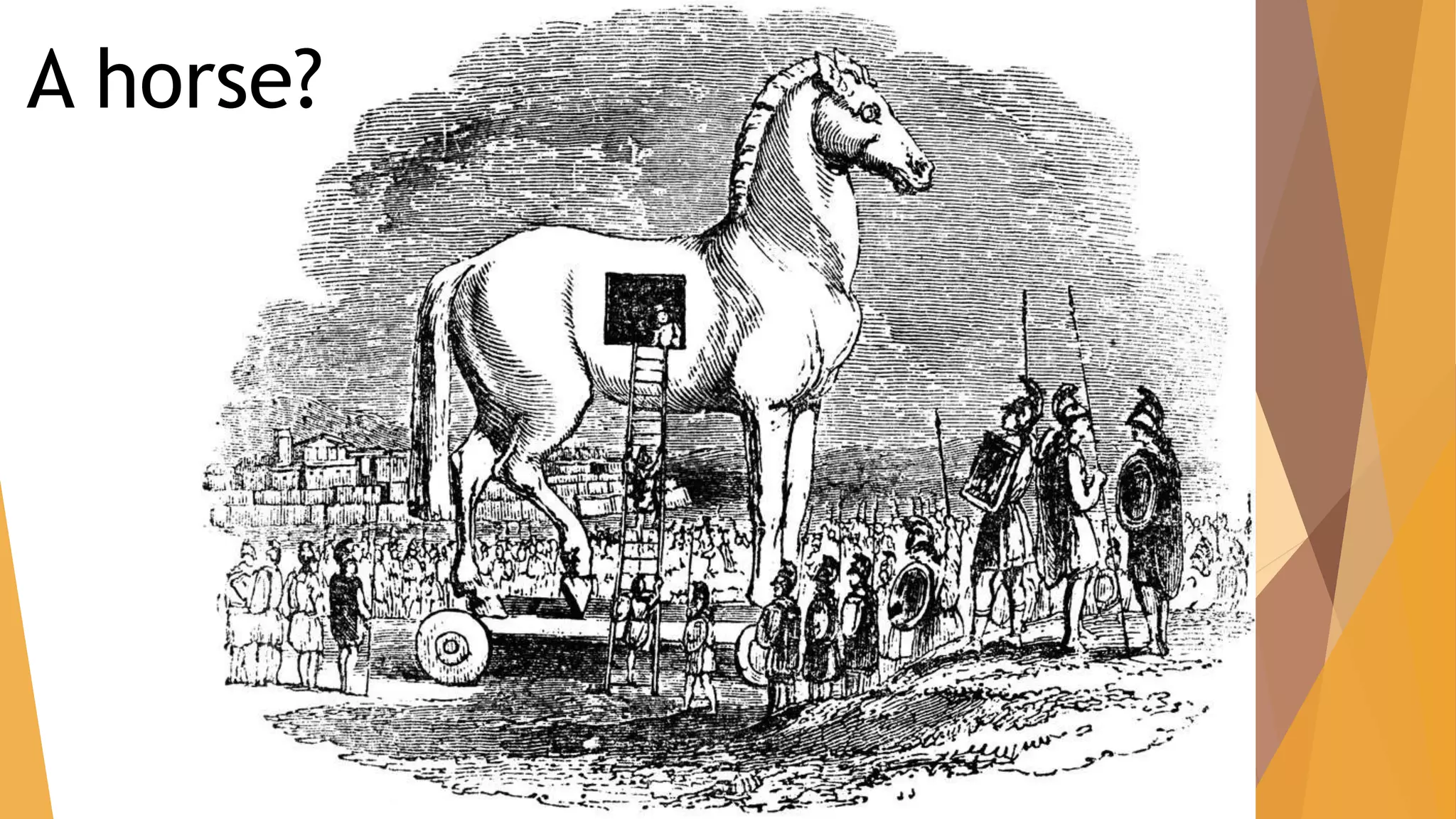
The document provides an overview of network security, detailing its components such as authentication, firewalls, and vulnerability management. It discusses various forms of malware including viruses, trojans, and worms, explaining their methods of operation and the risks they pose to computer systems. Additionally, it touches on the role of hackers and the significance of the Information Technology Amendment Act of 2008 in India, which updates the regulatory framework for cybersecurity.