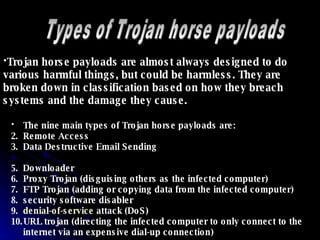
Viruses are malicious software programs that spread from computer to computer by infecting files. There are four main ways viruses spread: through floppy disks, downloading infected files from the internet, opening infected email attachments, and installing infected software. Trojan horses are malicious programs that perform undisclosed and harmful actions without the user's knowledge or consent, such as allowing remote access to the infected computer. Salami attacks involve making small, unnoticeable alterations like deducting small amounts of money from many bank accounts to commit financial crimes without detection. Computer viruses can copy themselves and infect systems without permission, affecting the computer system.