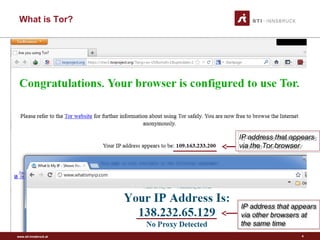
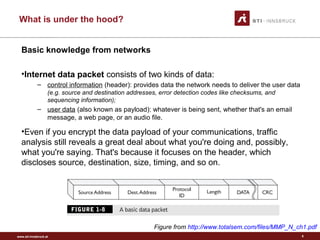
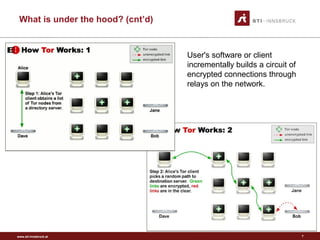
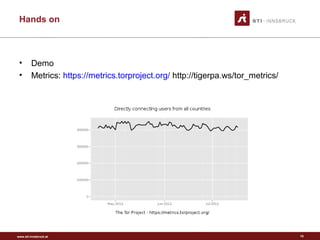
Tor is a free tool that allows users to browse the internet anonymously. It works by routing internet traffic through a network of volunteers around the world, preventing others from seeing what sites a user visits. Originally created by the U.S. Naval Research Laboratory to protect government communications, Tor has since been adopted by normal users, journalists, activists, and others seeking privacy online or wanting to access censored sites. It encrypts data and routes it through several volunteer nodes, removing layers of encryption at each stop to hide a message's origin, destination, and contents from intermediaries.

![www.sti-innsbruck.at
What is Tor?
3
• Tor was originally designed, implemented, and deployed as a third-
generation onion routing project of the U.S. Naval Research Laboratory
[1], for the primary purpose of protecting government communications.
• Tor is a free tool that allows people to use the internet anonymously.
• Basically, Tor protects you by bouncing your communications
around a distributed network of relays run by volunteers all around
the world: it prevents somebody watching your Internet connection
from learning what sites you visit, it prevents the sites you visit from
learning your physical location, and it lets you access sites which
are blocked.
• Tor anonymizes the origin of your traffic!](https://image.slidesharecdn.com/tor-150223063115-conversion-gate01/85/Tor-3-320.jpg)