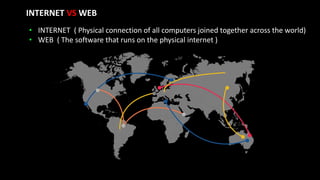
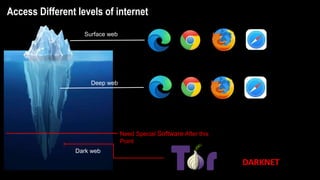
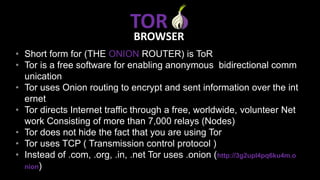
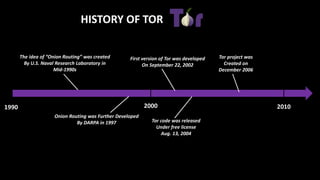
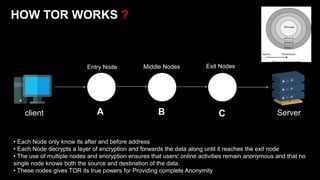
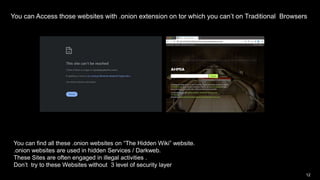
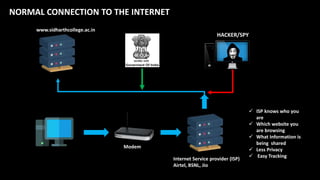
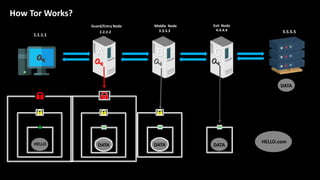
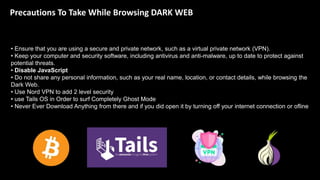
The document provides an overview of the dark web, highlighting the distinctions between the surface web, deep web, and dark web, as well as explaining how Tor, a software that enables anonymous communication through onion routing, works. It discusses the risks and precautions associated with browsing the dark web and lists various illegal activities commonly found on it. Additionally, it addresses the purposes for which Tor is utilized, including anonymity for government, activists, and individuals wishing to protect their identities.