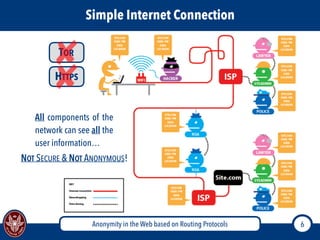
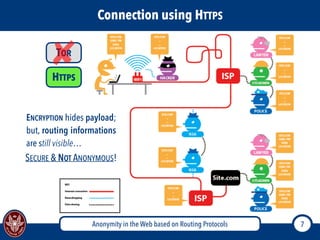
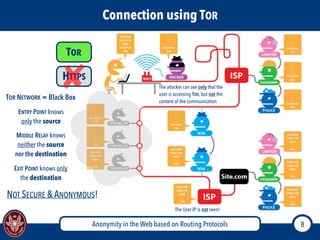
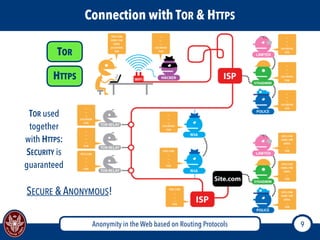
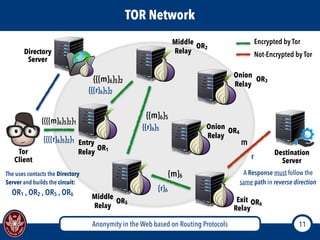
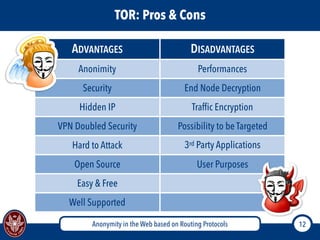
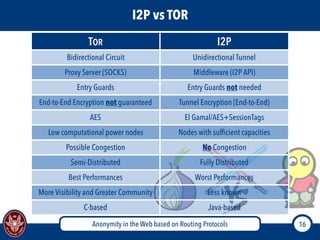
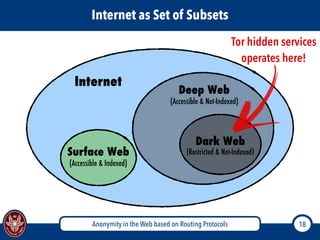
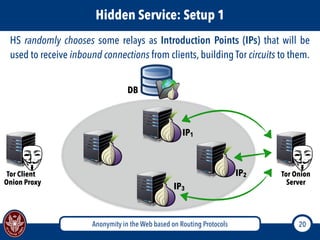
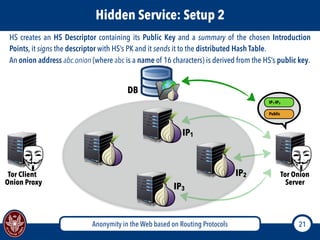
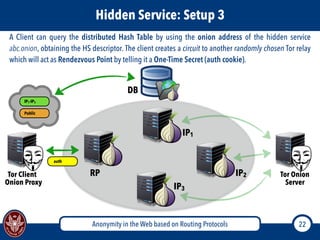
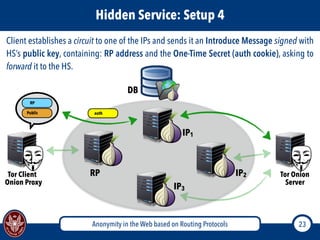
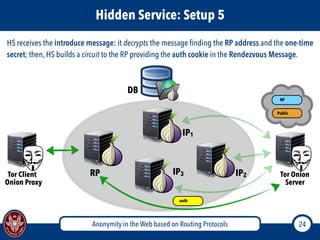
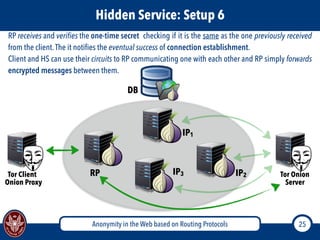
The document discusses the concept of anonymity on the web, focusing on routing protocols like Tor and I2P, which aim to enhance user privacy by concealing location and activity. It provides an overview of how Tor operates, including its architecture, advantages, disadvantages, and potential vulnerabilities to attacks. Additionally, it outlines the setup and functioning of Tor hidden services and compares Tor with I2P's messaging approach.