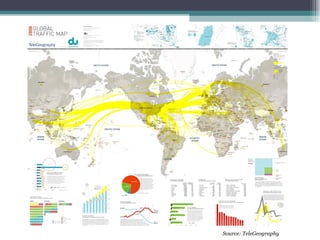
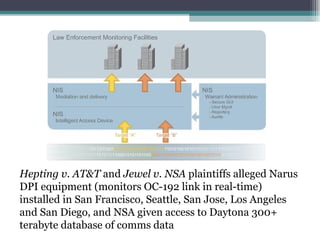
This document discusses the history and future of internet surveillance. It describes the UKUSA intelligence alliance between the US, UK, Canada, Australia and New Zealand for signals intelligence cooperation since WWII. It outlines various programs and methods for intercepting communications signals via satellites, submarines, and undersea cables. It also discusses the interception of data at communication hubs and the increasing collection of social media and other online data. The conclusion recognizes the vast resources spent on surveillance and the challenges of managing exponentially growing data collection.










![Efficacy of data mining
• ~5000 Americans surveilled over 4 years; led to
<10 warrants per year
• “[T]here is not a consensus within the relevant
scientific community nor on the committee
regarding whether any behavioral surveillance
… techniques are ready for use at all in the
counterterrorist context" –US National
Research Council (2008) p.4](https://image.slidesharecdn.com/surveillancehomelandsecurity-1211744495171207-9/85/Internet-surveillance-past-present-and-future-13-320.jpg)





