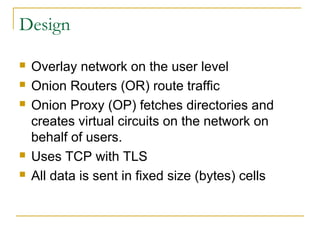
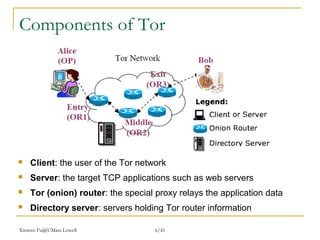
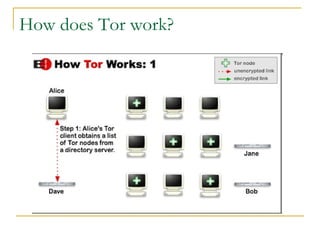
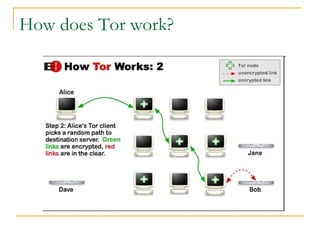
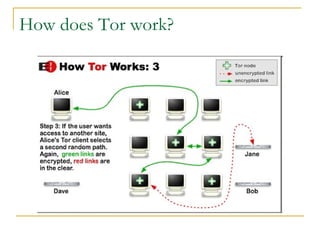
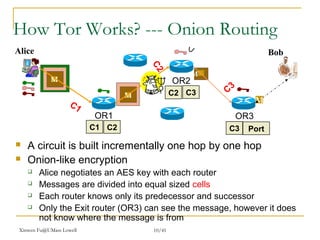
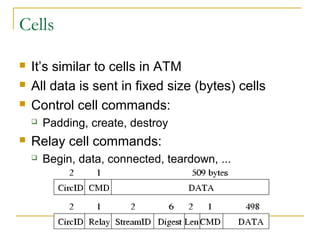
The document outlines the challenges of internet surveillance and the need for end-to-end anonymity, proposing the use of the Tor network as a solution. Tor serves as a distributed anonymous communication service, enabling privacy and allowing users to access blocked services while keeping their locations hidden. The technical details include an onion routing mechanism, components like clients, servers, and routers, as well as additional functionalities such as integrity checking and congestion control.