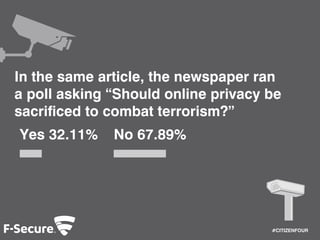
The document discusses the extent of government surveillance revealed by Edward Snowden, highlighting various GCHQ programs that monitor online activities, including webcam captures and text message collection. It also underscores public concern over privacy versus security, with a notable poll showing 67.89% against sacrificing online privacy to combat terrorism. The document concludes by recommending Freedome, a security solution for protecting online privacy, and encourages viewers to watch the film 'Citizenfour' for more insights.