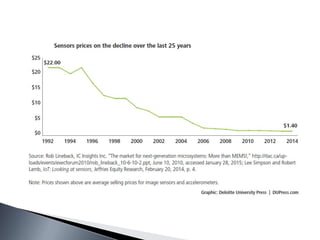
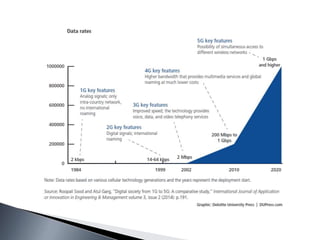
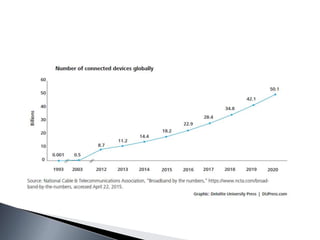
The document outlines the complexities and stages involved in implementing the Internet of Things (IoT), focusing on components such as sensors, networks, standards, intelligent analysis, and actions. It discusses challenges such as data handling, security, and the need for standards, while highlighting the role of cognitive technologies in data analysis and decision-making. The IoT is portrayed as a transformative ecosystem that aims to enhance automation and connectivity in various aspects of life.