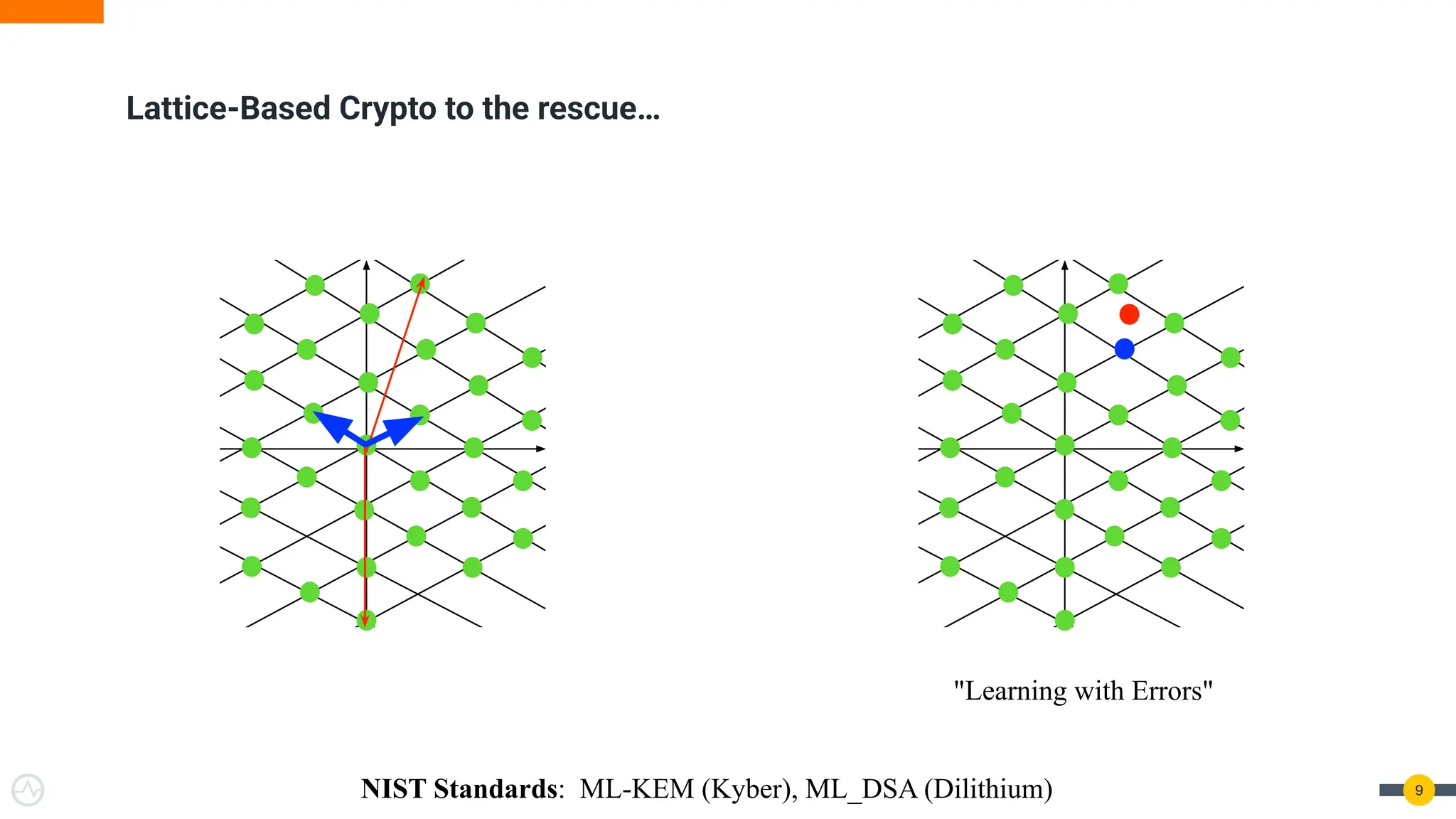
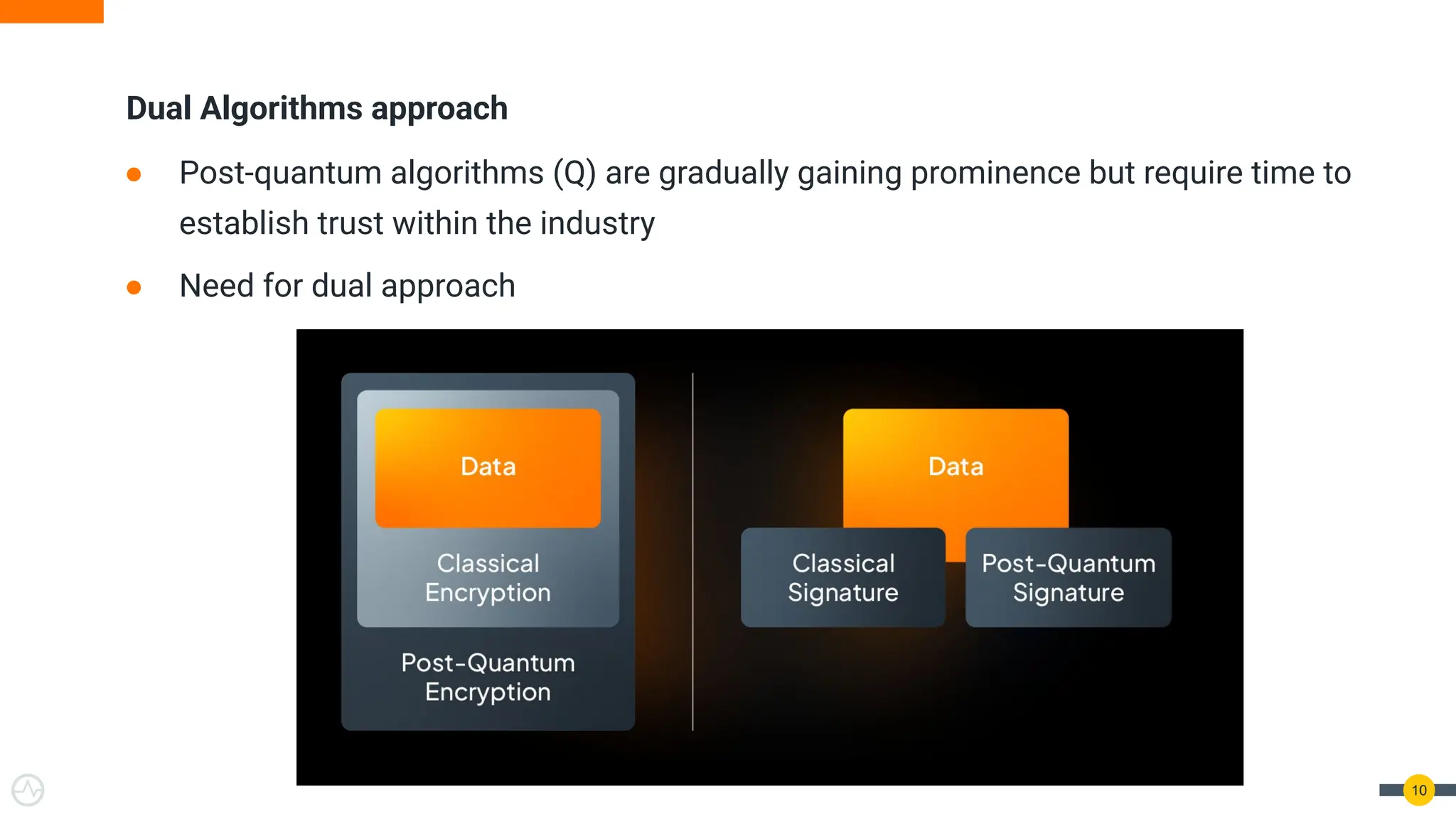
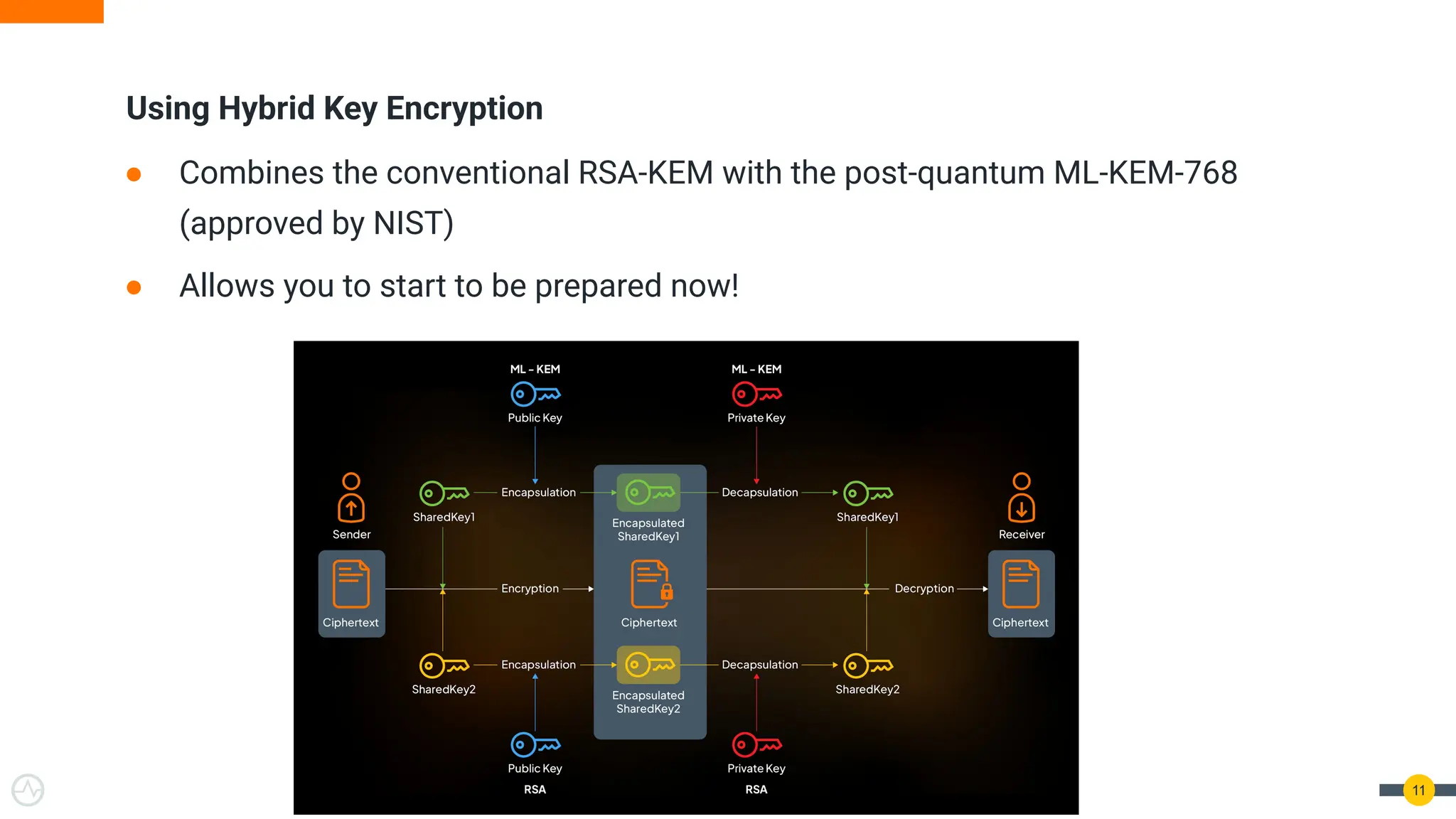
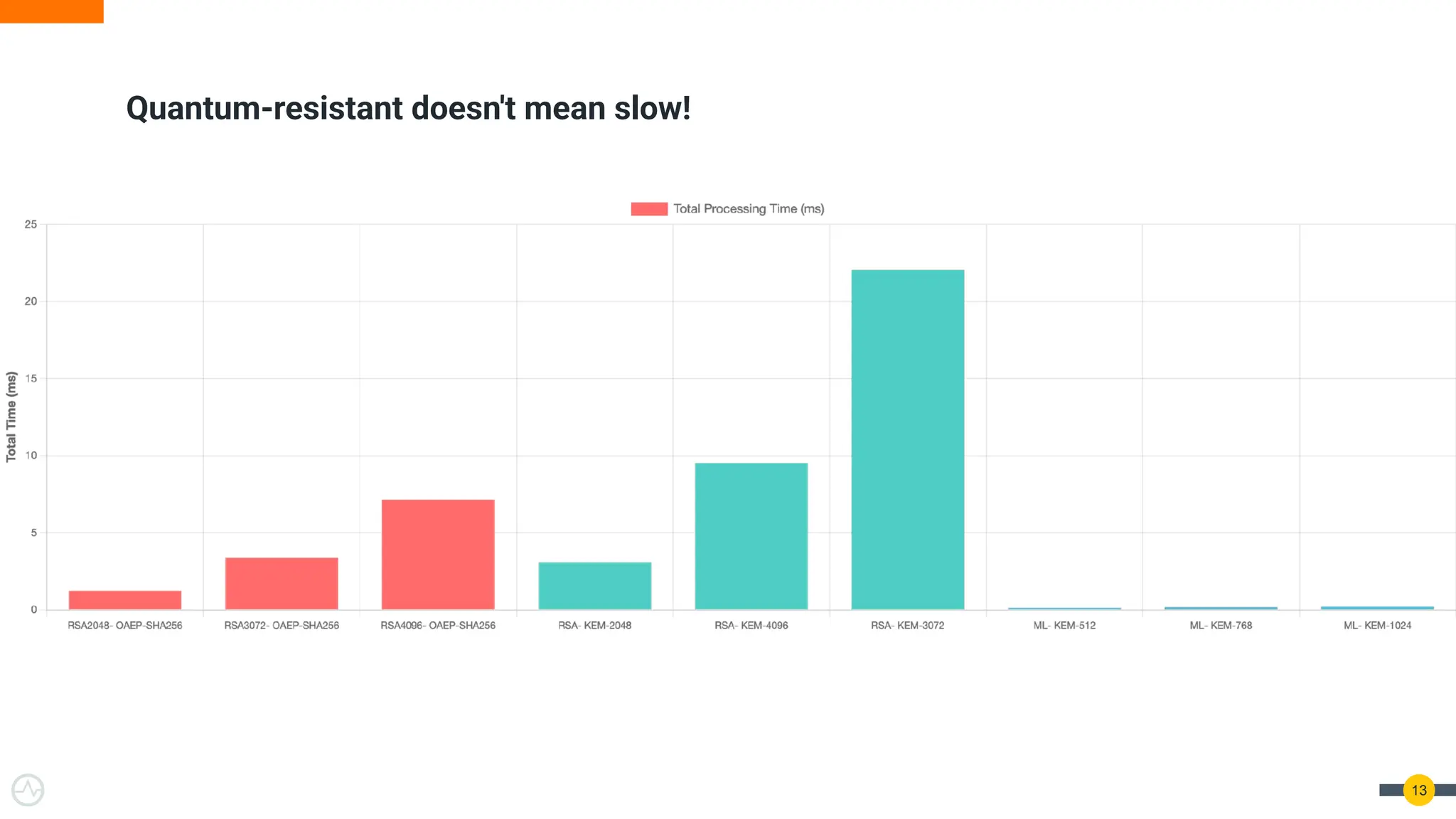
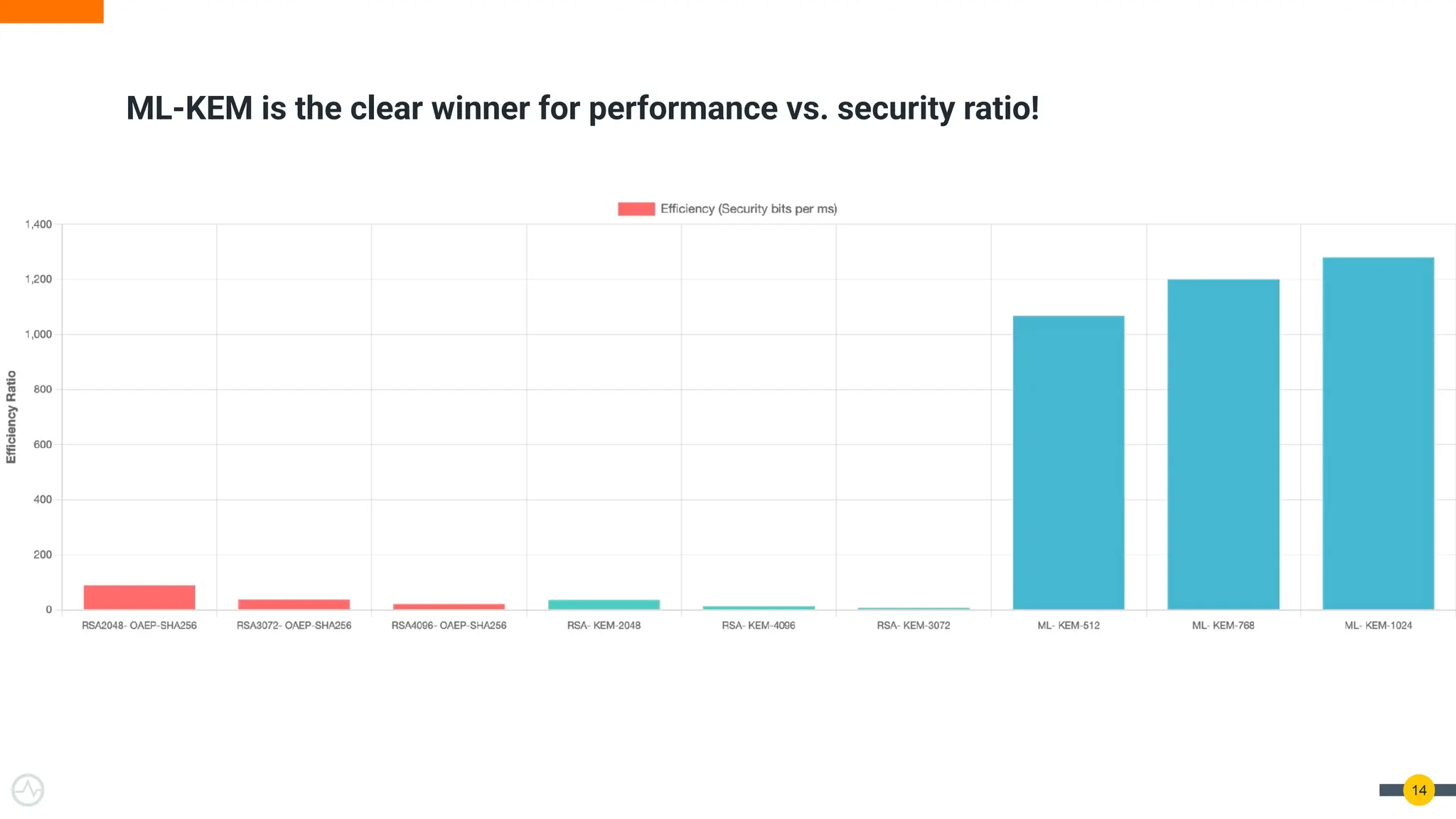
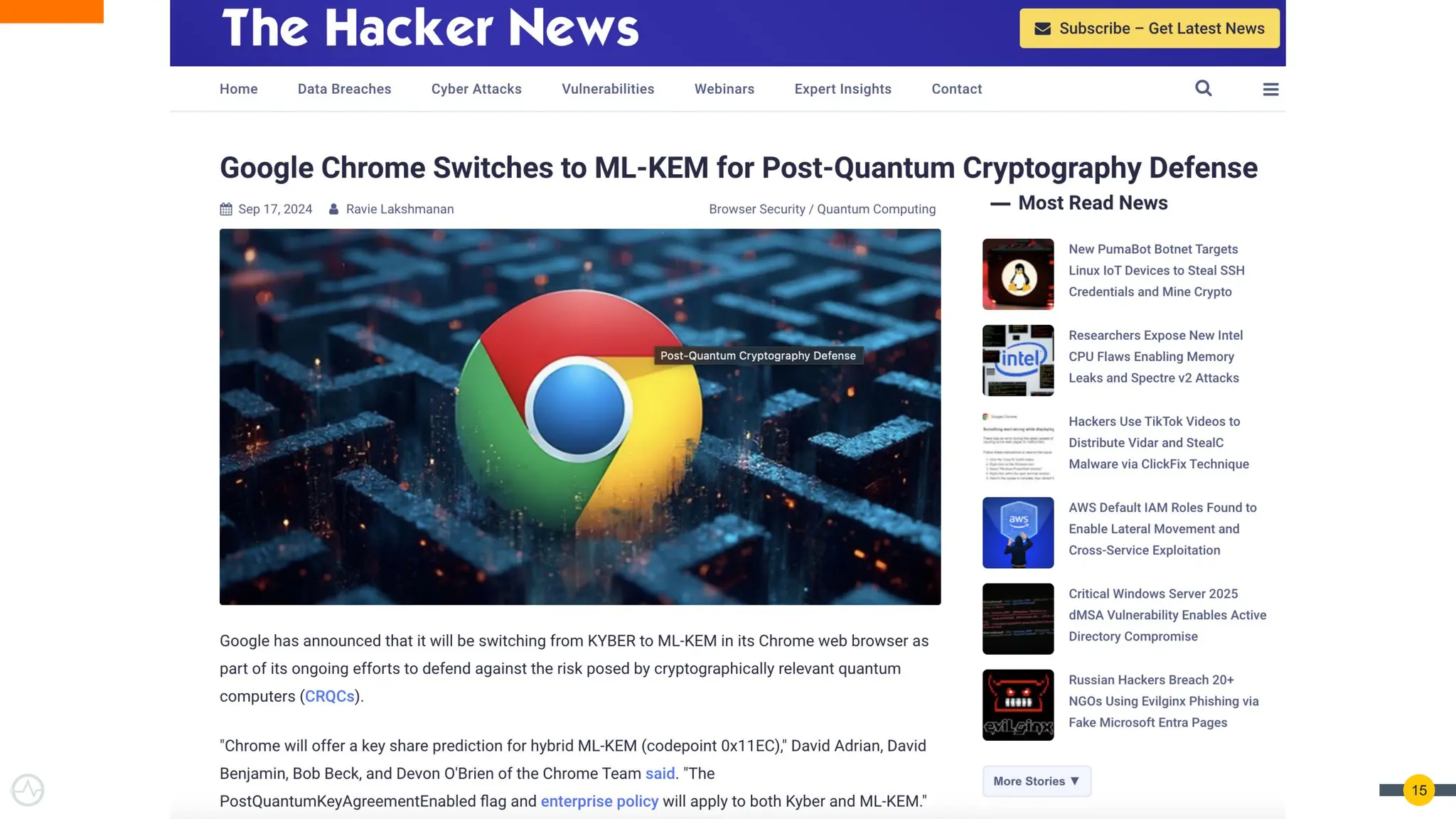
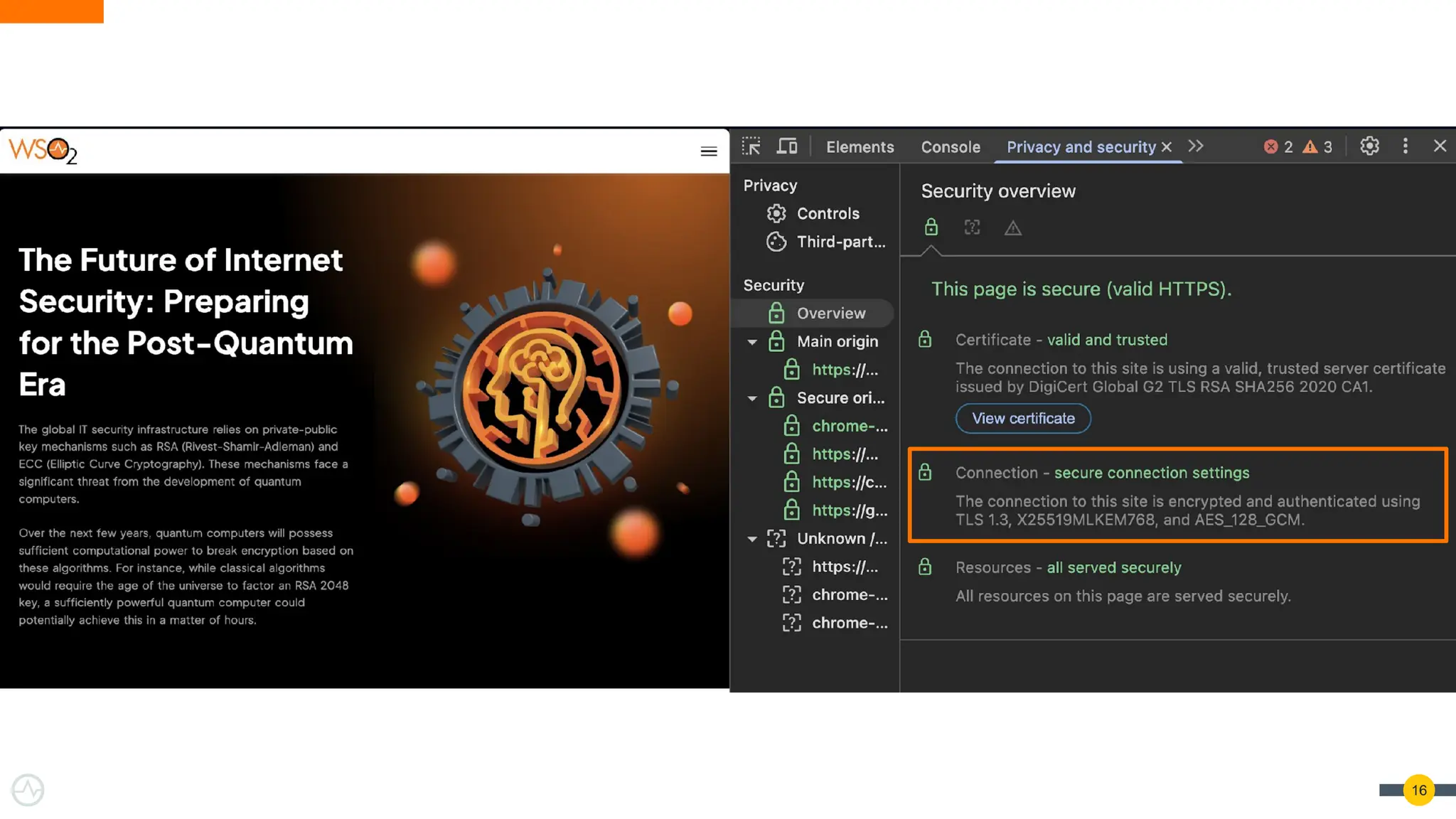
Quantum Threats Are Real — And Already Here
Quantum computing is advancing fast, putting today’s encryption at risk. In this session, Isabelle and Frank explore how attackers are exploiting “harvest now, decrypt later” tactics—and what your organization can do to stay ahead.
Learn about post-quantum cryptography, crypto agility, and learn how to begin migrating now.
https://is.docs.wso2.com/en/latest/deploy/security/configure-post-quantum-tls/