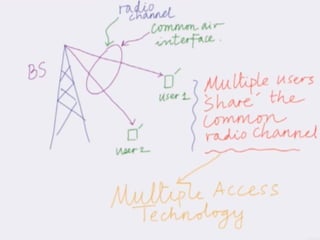
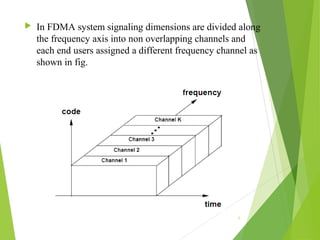
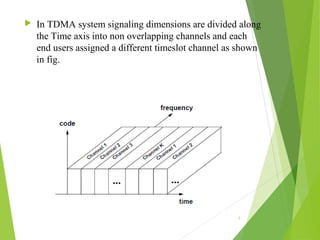
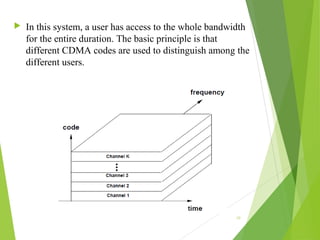
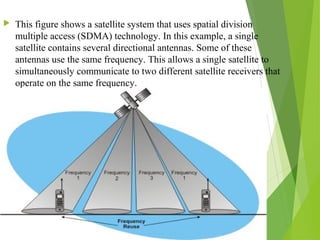
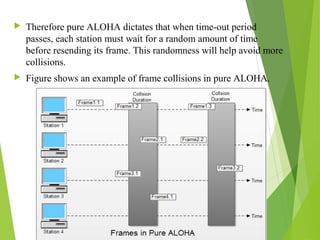
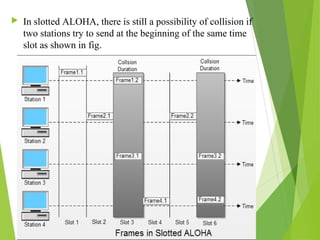
This document discusses multiple access techniques in wireless communication. It describes several techniques including Frequency Division Multiple Access (FDMA), Time Division Multiple Access (TDMA), Code Division Multiple Access (CDMA), and Space Division Multiple Access (SDMA). It also covers packet radio access methods like ALOHA, slotted ALOHA, and Carrier Sense Multiple Access (CSMA). Each technique allows multiple users to share wireless spectrum resources simultaneously through dividing access in frequency, time, code, or space.