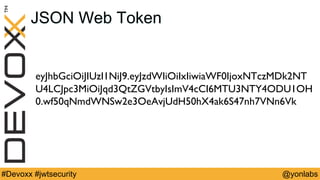
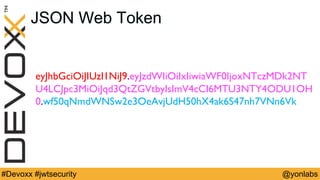
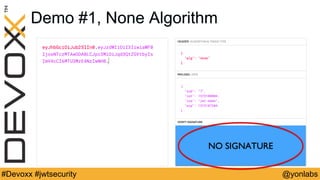
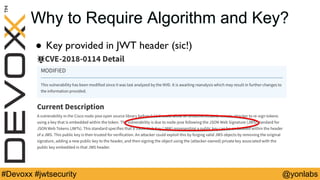
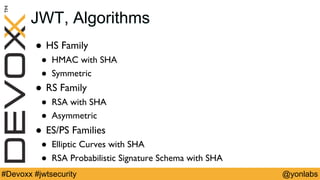
The presentation discusses common security issues with JSON Web Tokens (JWTs) and demonstrates attacks. It covers problems with none algorithms in JWT libraries, password cracking with weak keys, packet sniffing to steal unencrypted tokens, and cross-site scripting to steal tokens from session storage. The presentation provides best practices for algorithms, keys, encryption, timeouts, logouts, and defenses like content security policy to address these issues.