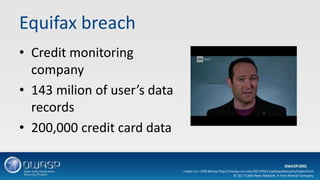
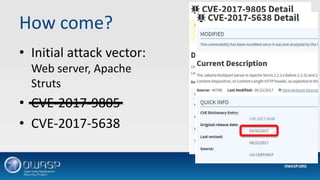
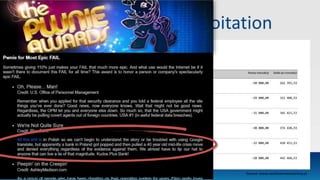
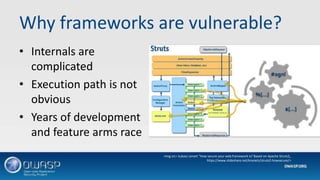
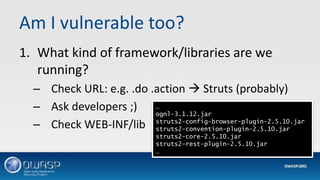
This document discusses vulnerabilities in application frameworks and the importance of monitoring for vulnerabilities in third party libraries and components. It uses the Equifax breach as an example of how vulnerabilities in the Apache Struts framework were exploited to gain access and steal personal data. The document recommends that software developers and IT security teams regularly check all application components for known vulnerabilities and ensure components and libraries are kept up to date with the latest security patches. It also emphasizes the importance of detection mechanisms to identify suspicious activity resulting from exploited vulnerabilities.