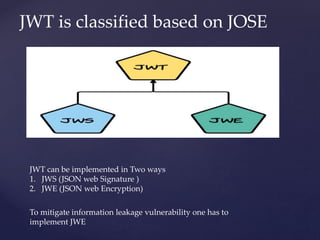
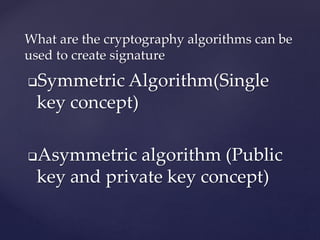
The document discusses JSON Web Tokens (JWT) including their structure, security concerns, and recommendations for safe usage. It details the components of JWTs—the header, payload, and signature—and highlights vulnerabilities such as information leakage and authorization bypass. The author advocates for the use of asymmetric algorithms and proper key management to enhance security when implementing JWTs.



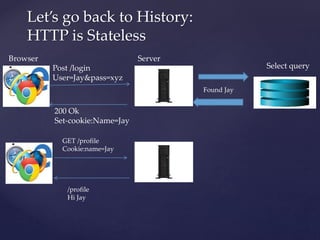
![Select query
Post /login
User=Jay&&pass=xy
200 Ok
Set-cookie:sessionid=6swe.. Set id=6swe…[]
Get /homepage
Cookie:sessionid=6swe…
Browser Server
Storage where reference s
200 ok
response
Found Jay
Id=6swe
..](https://image.slidesharecdn.com/pentestingjwt-190624173216/85/Pentesting-jwt-6-320.jpg)

![Select query
Post /login
User=Jay&&pass=xyz
200 Ok
Set-cookie: eyr…[]
Get /homepage
Cookie: eyr…[]
Write + Sign
Verify + Read
200 ok
response](https://image.slidesharecdn.com/pentestingjwt-190624173216/85/Pentesting-jwt-8-320.jpg)