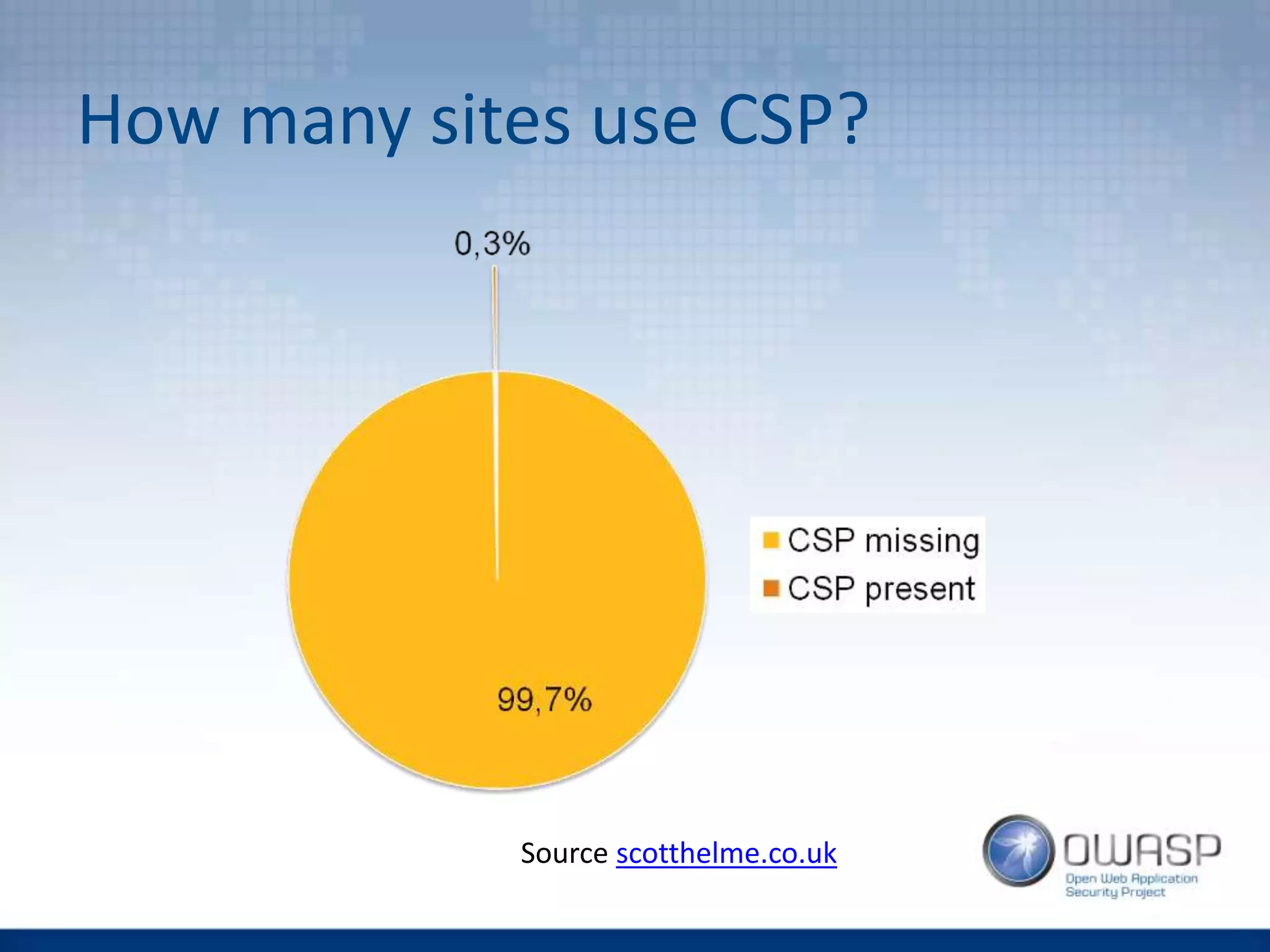
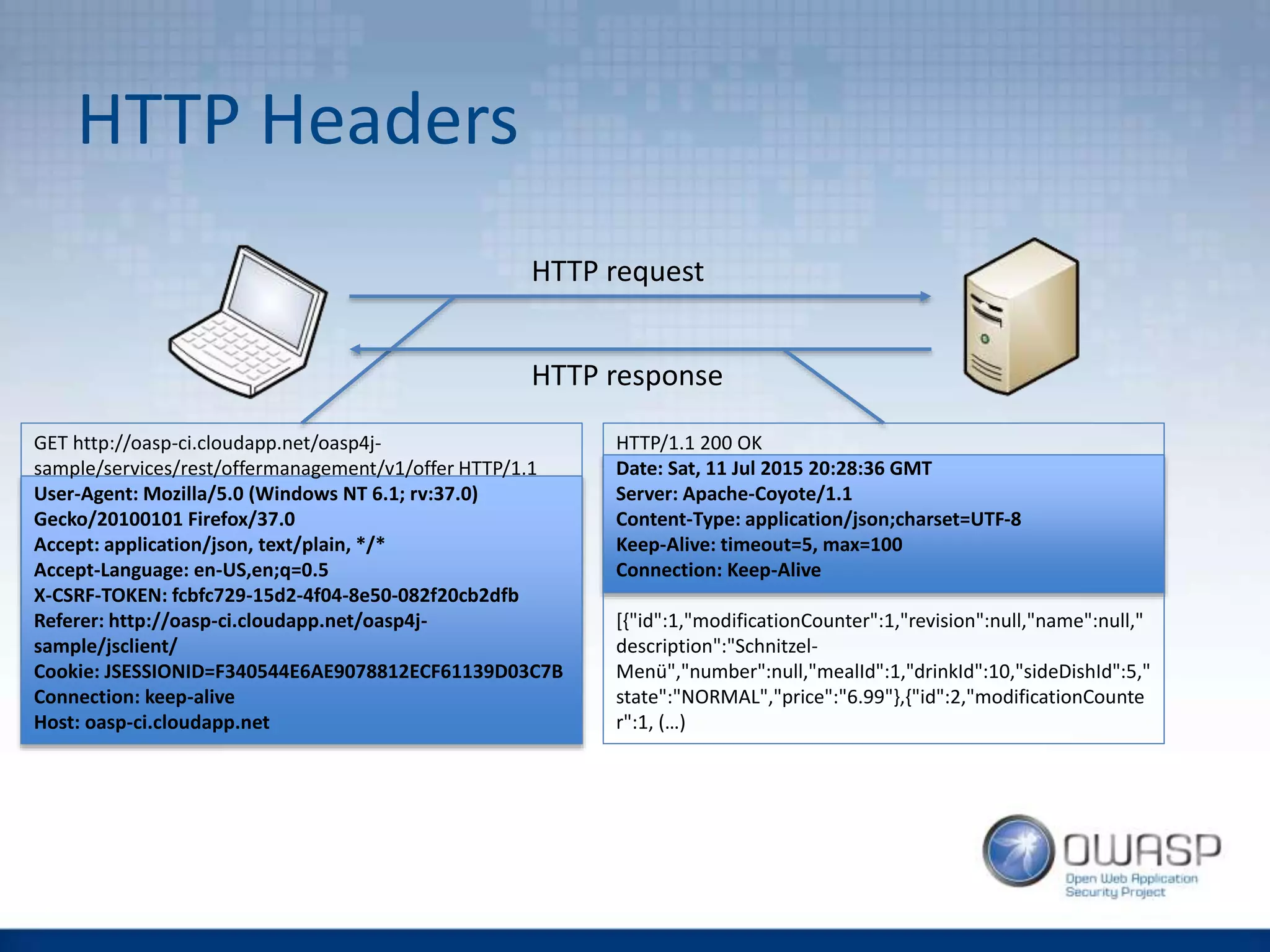
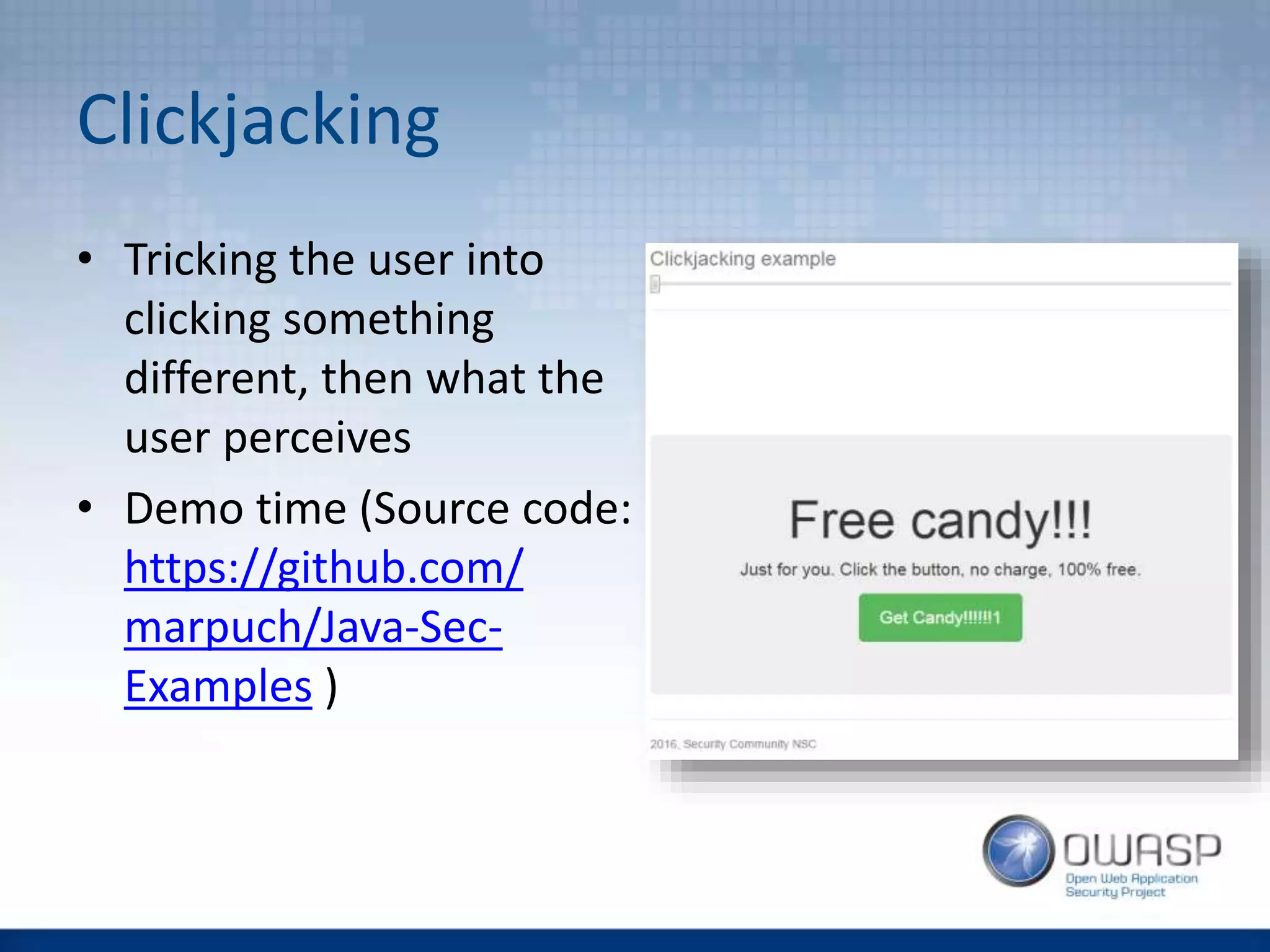
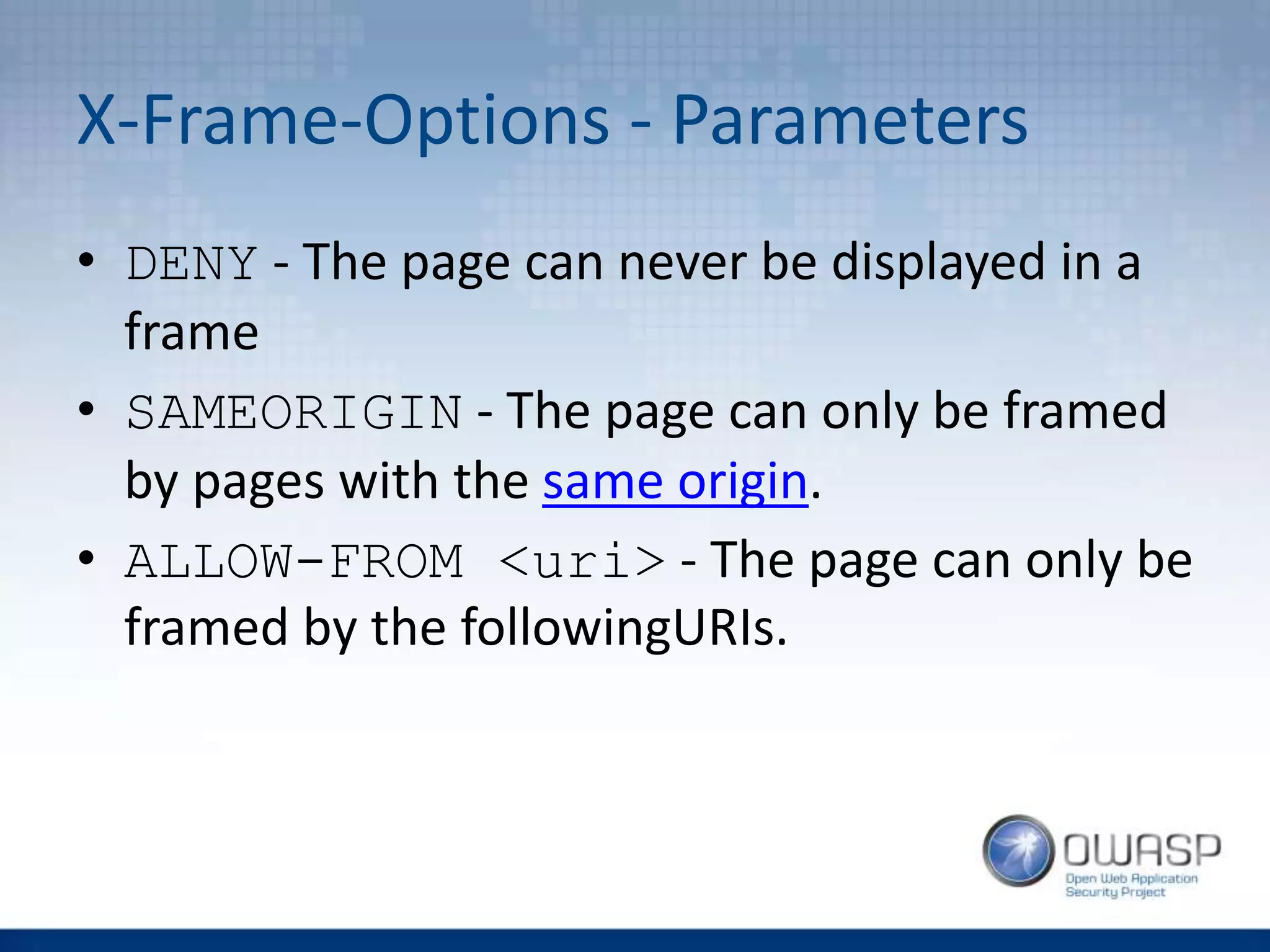
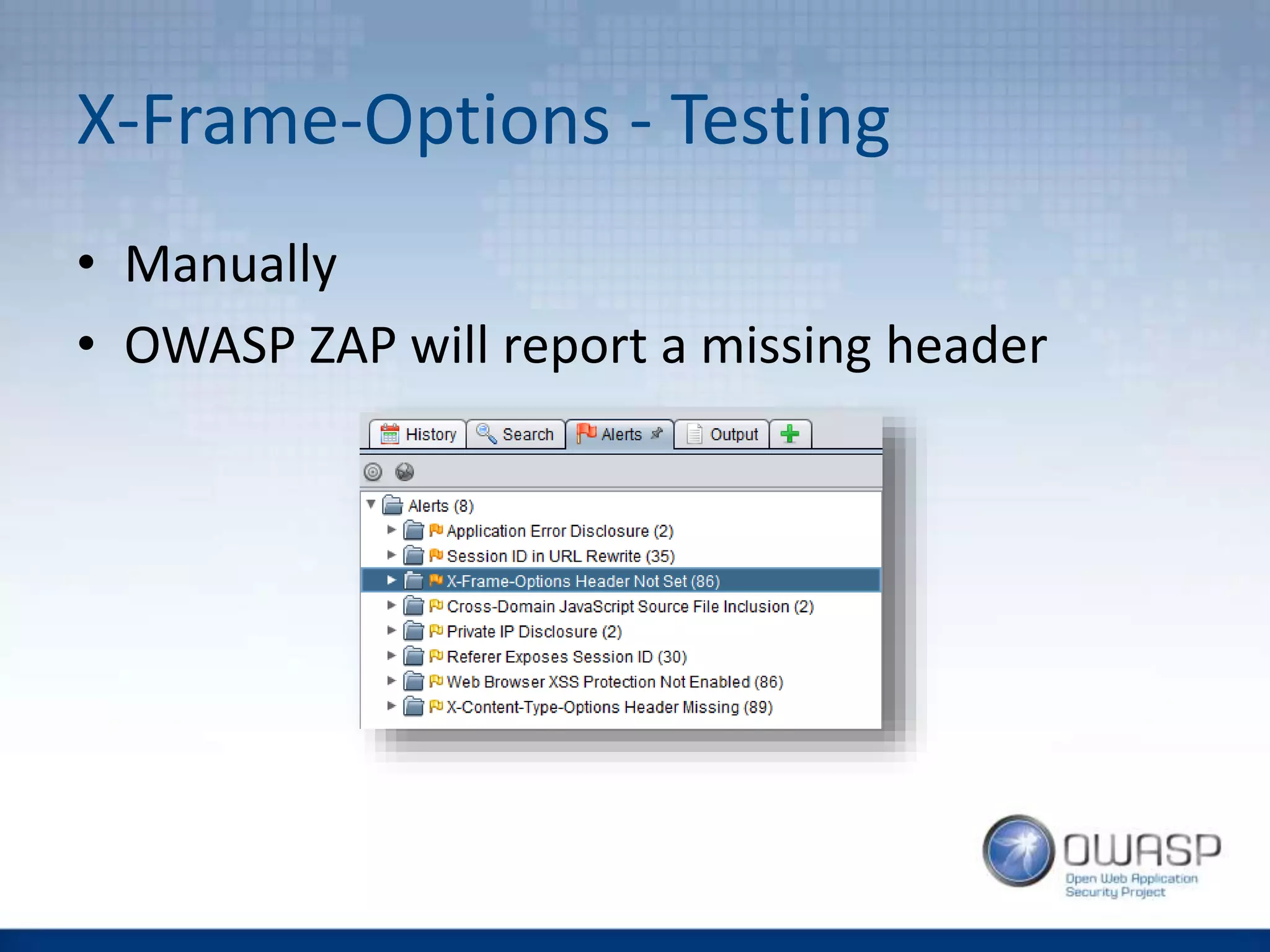
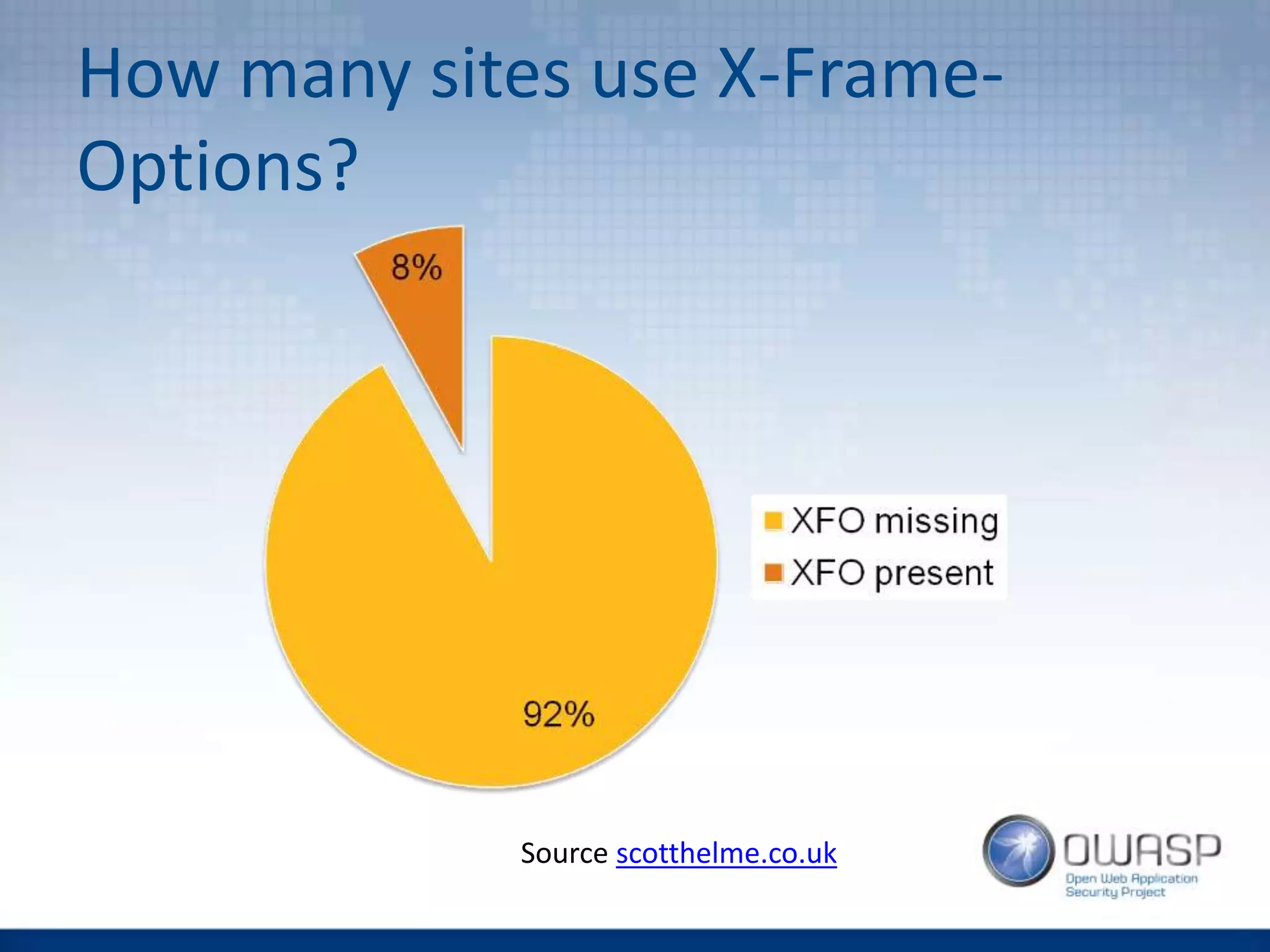
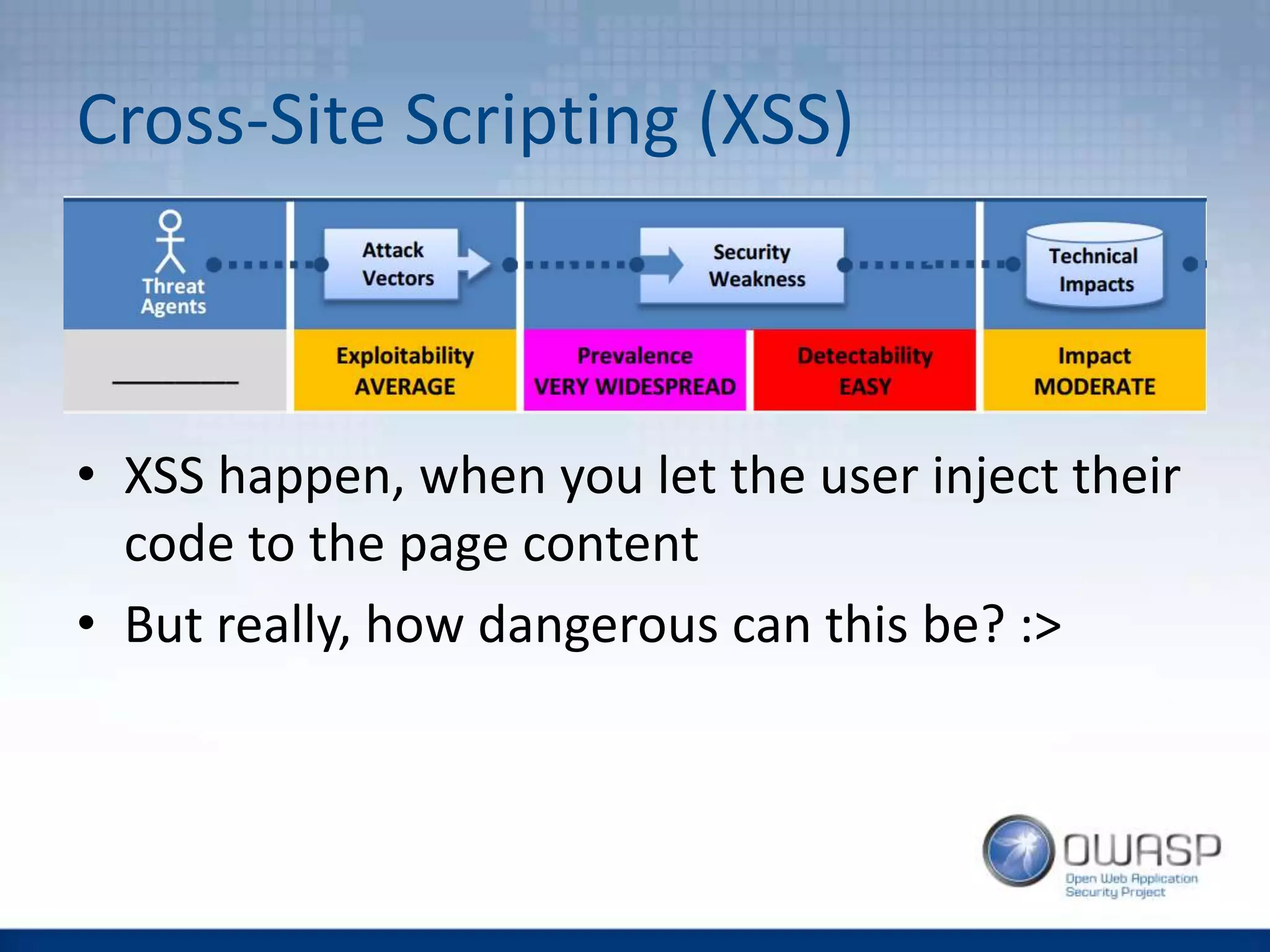
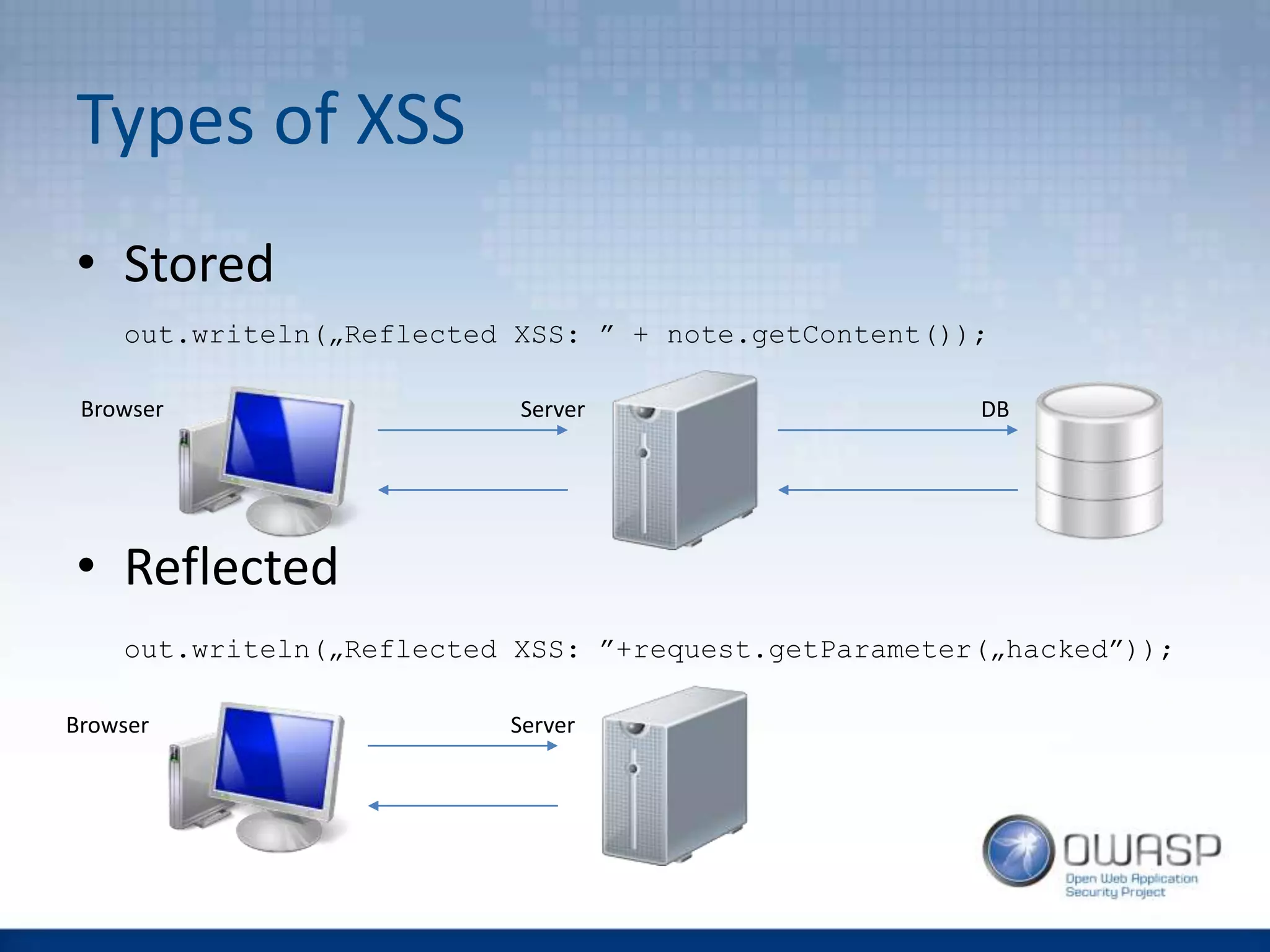
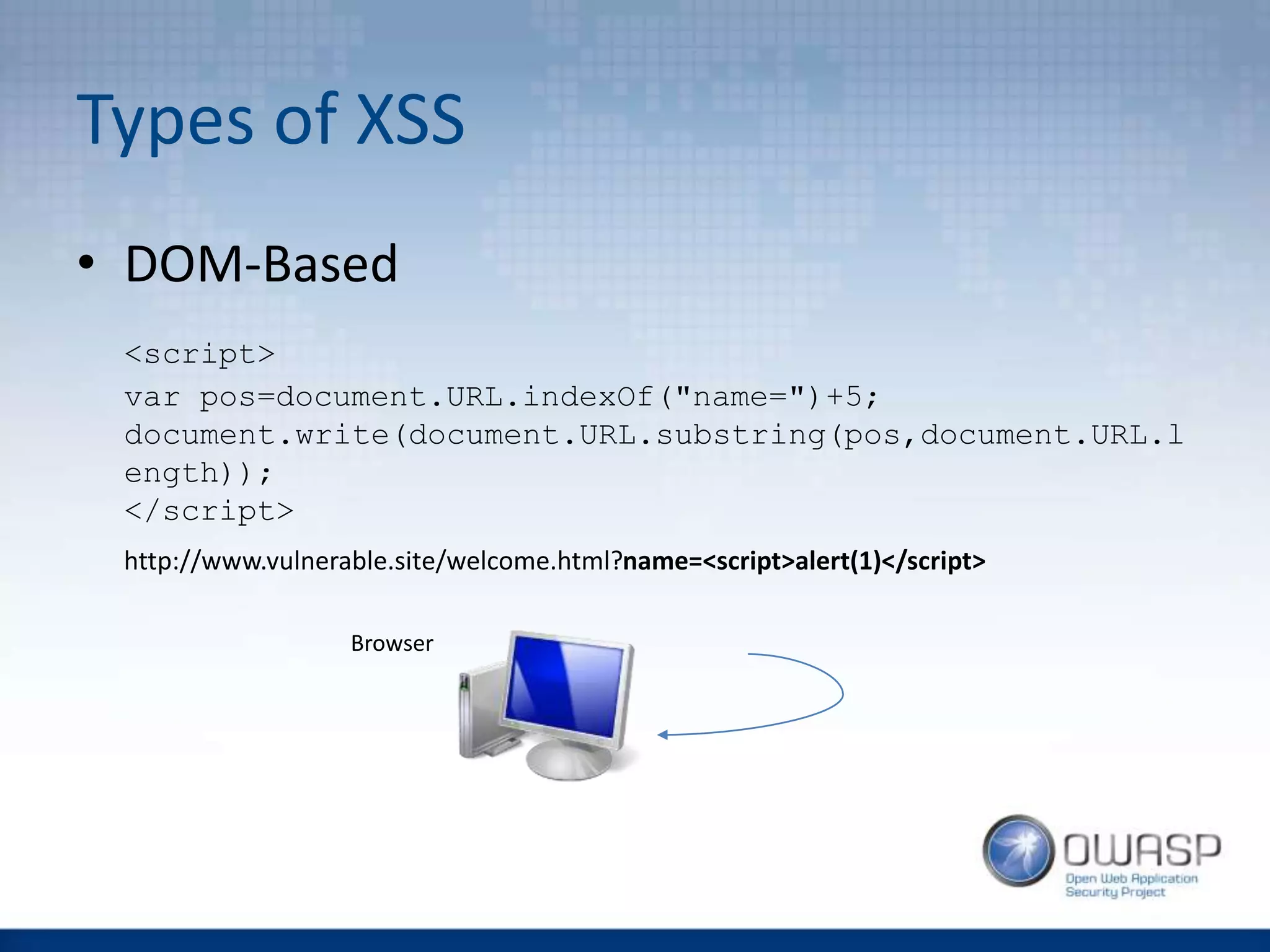
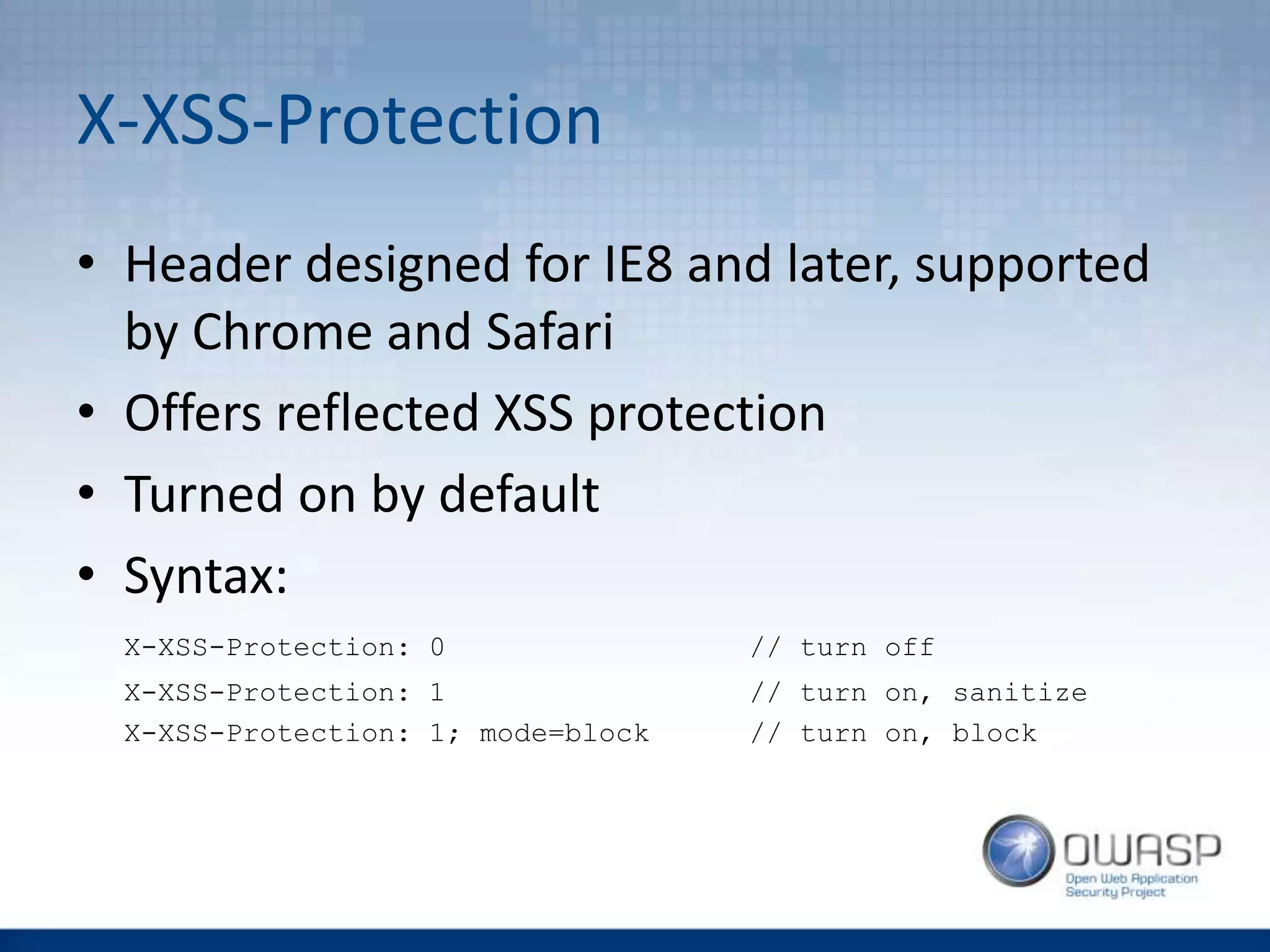
This document discusses HTTP security headers and techniques for preventing clickjacking and cross-site scripting attacks. It describes the X-Frame-Options header which prevents clickjacking by controlling framing. Content Security Policy (CSP) provides a more powerful alternative to X-Frame-Options and can also prevent cross-site scripting attacks by whitelisting allowed script sources. The document compares X-Frame-Options, CSP directives, and how each addresses different attack vectors. It concludes with recommendations on CSP implementation and testing.








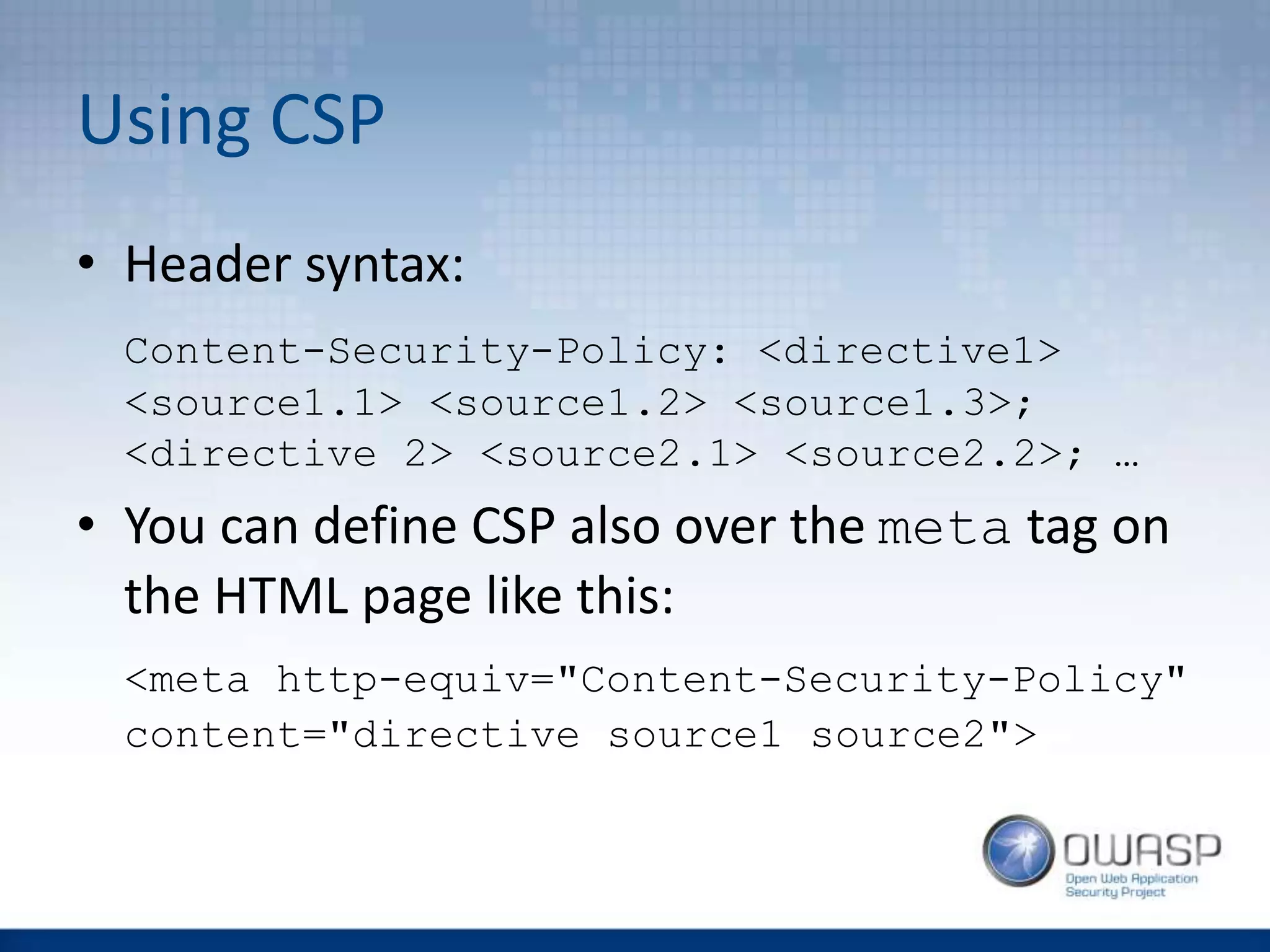
![CSP Directives VS Clickjacking
• default-src
• script-src, style-src, img-src,
font-src, media-src, connect-src,
object-src
• child-src, frame-ancestor
• form-action
• plugin-types
• report-uri [-Report-Only]](https://image.slidesharecdn.com/owaspwebapplicationsecurityheaders1-160429210343/75/Wroclaw-2-Web-Application-Security-Headers-17-2048.jpg)
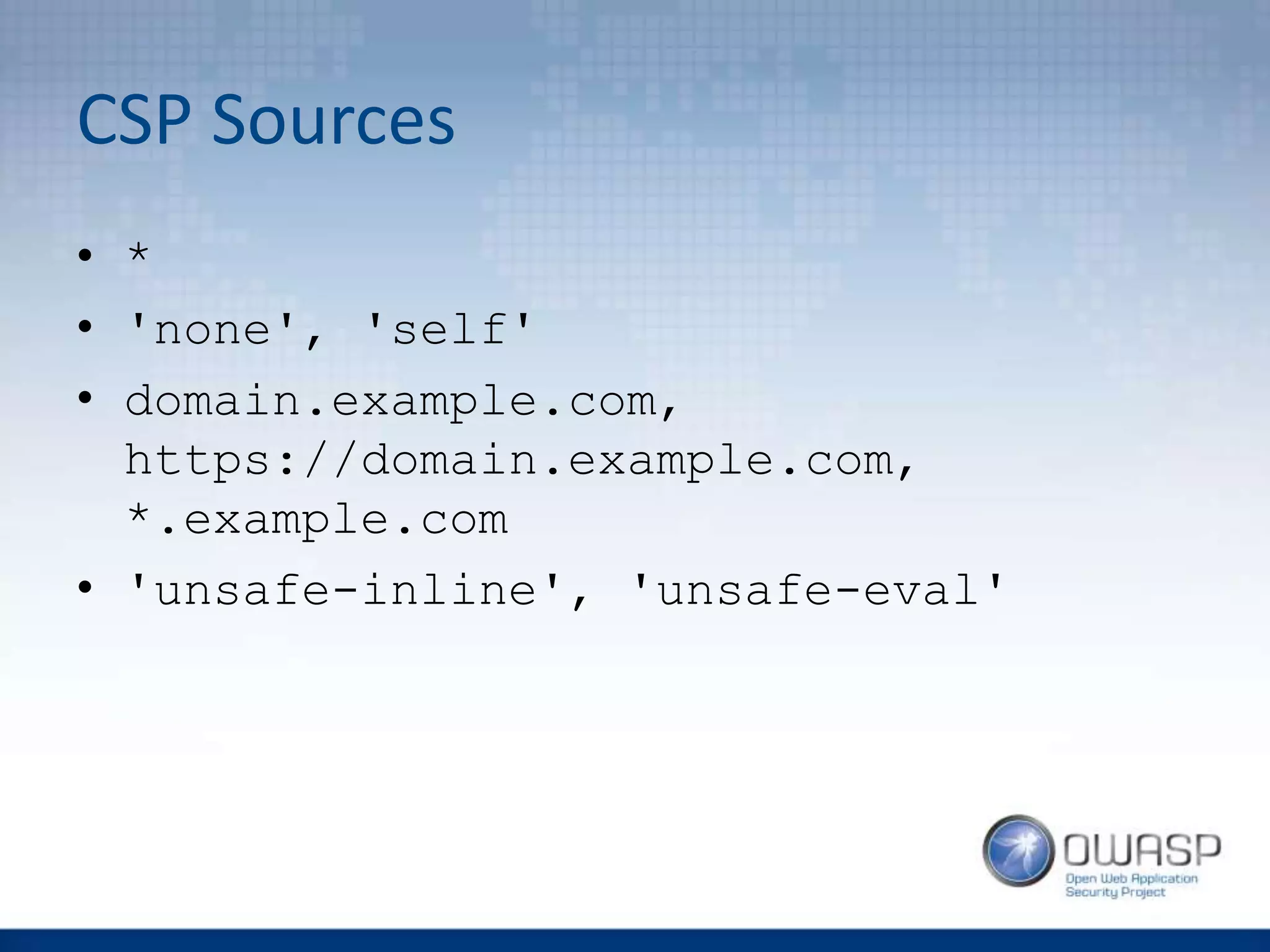
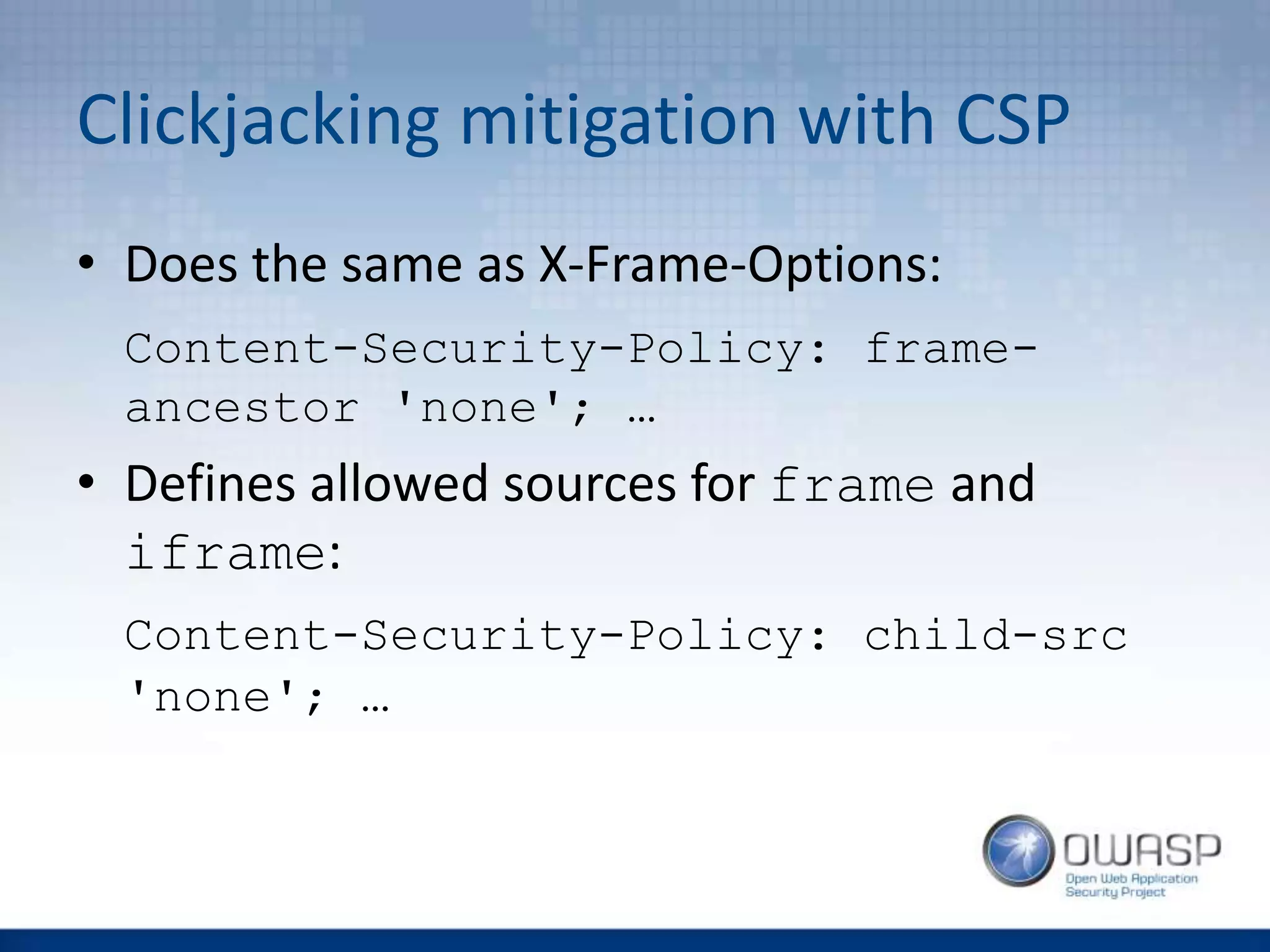

![CSP Directives VS XSS
• default-src
• script-src, style-src, img-src,
font-src, media-src, connect-src,
object-src
• child-src, frame-ancestor
• form-action
• plugin-types
• report-uri [-Report-Only]](https://image.slidesharecdn.com/owaspwebapplicationsecurityheaders1-160429210343/75/Wroclaw-2-Web-Application-Security-Headers-26-2048.jpg)
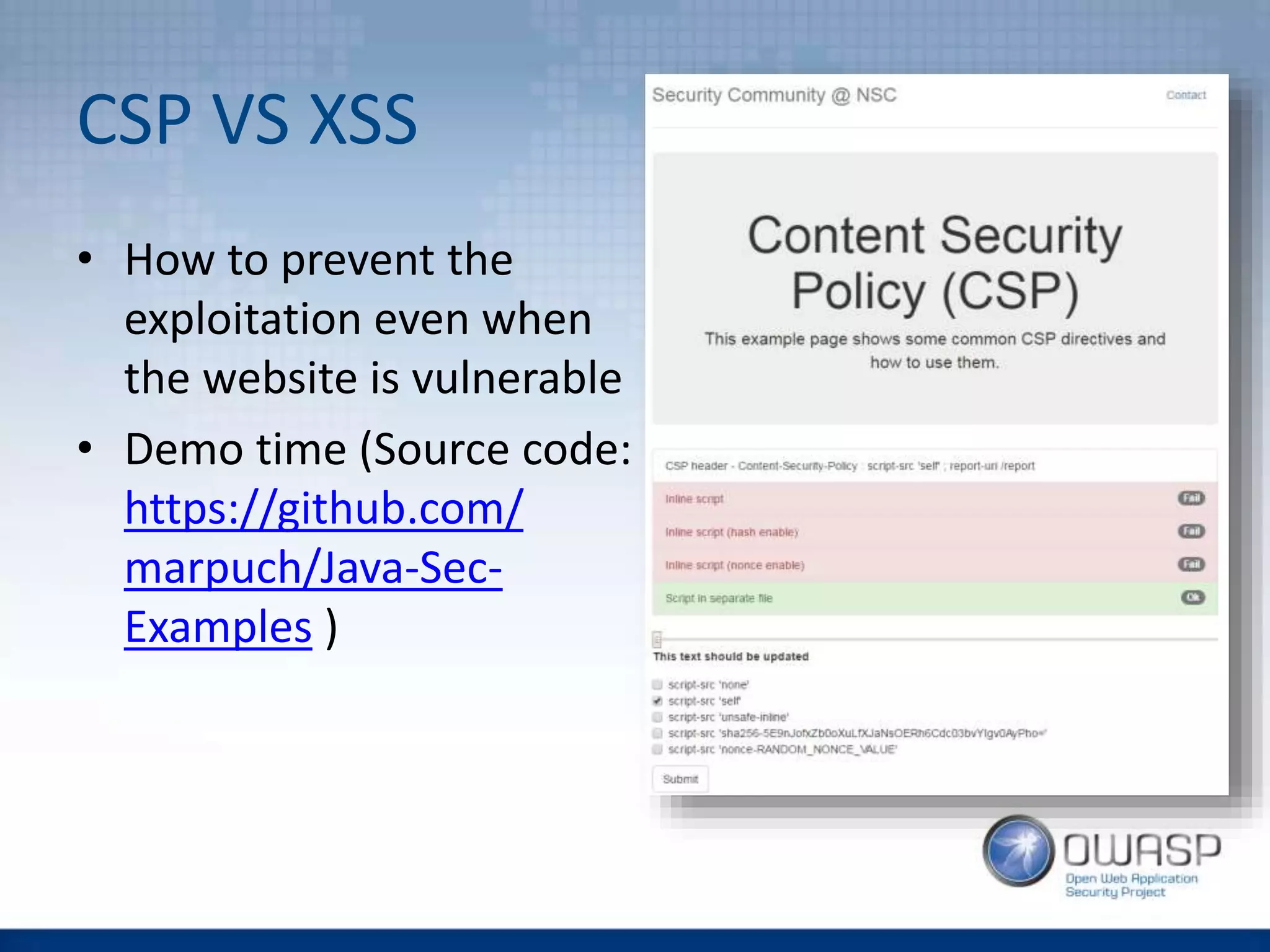
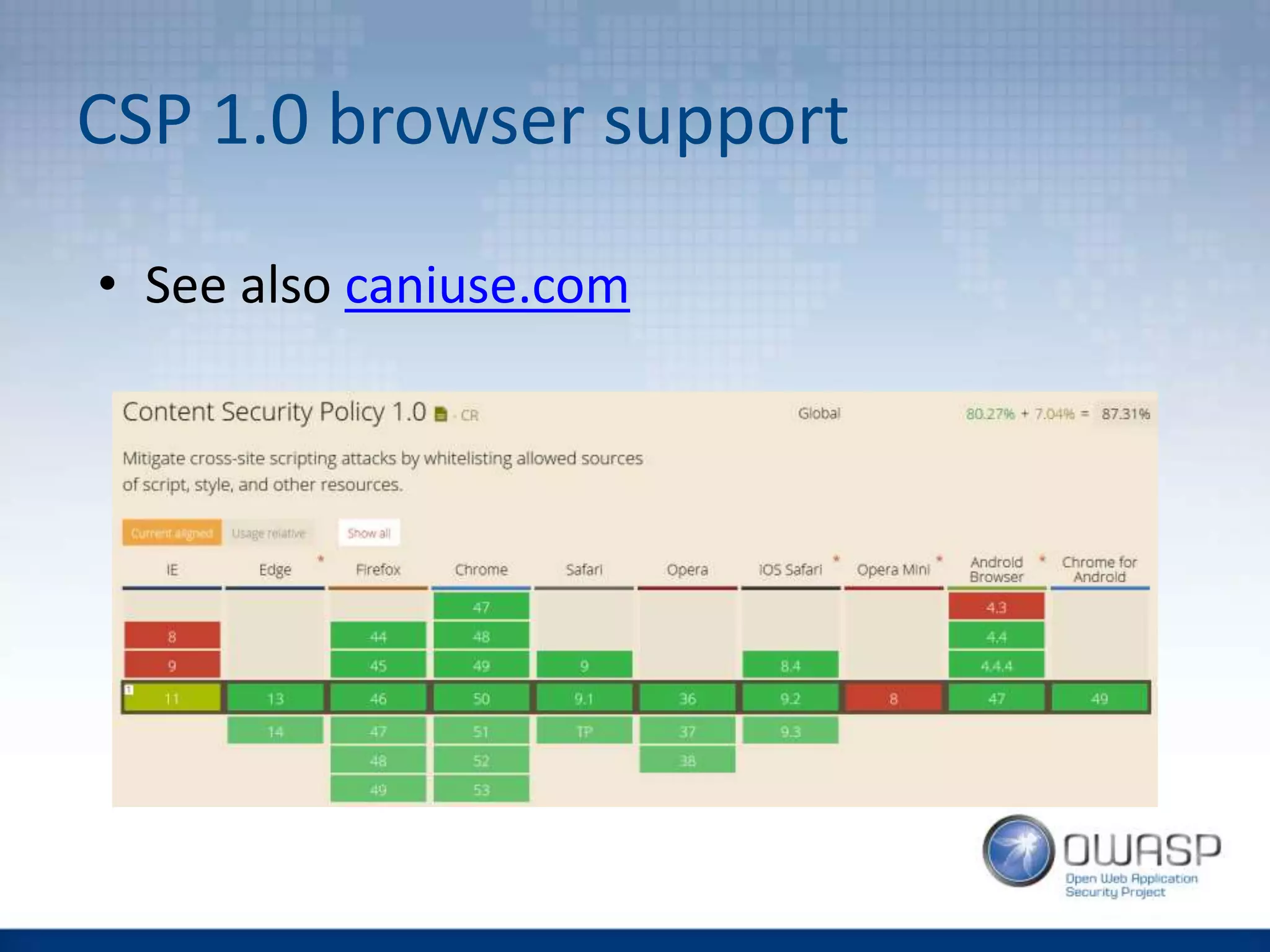

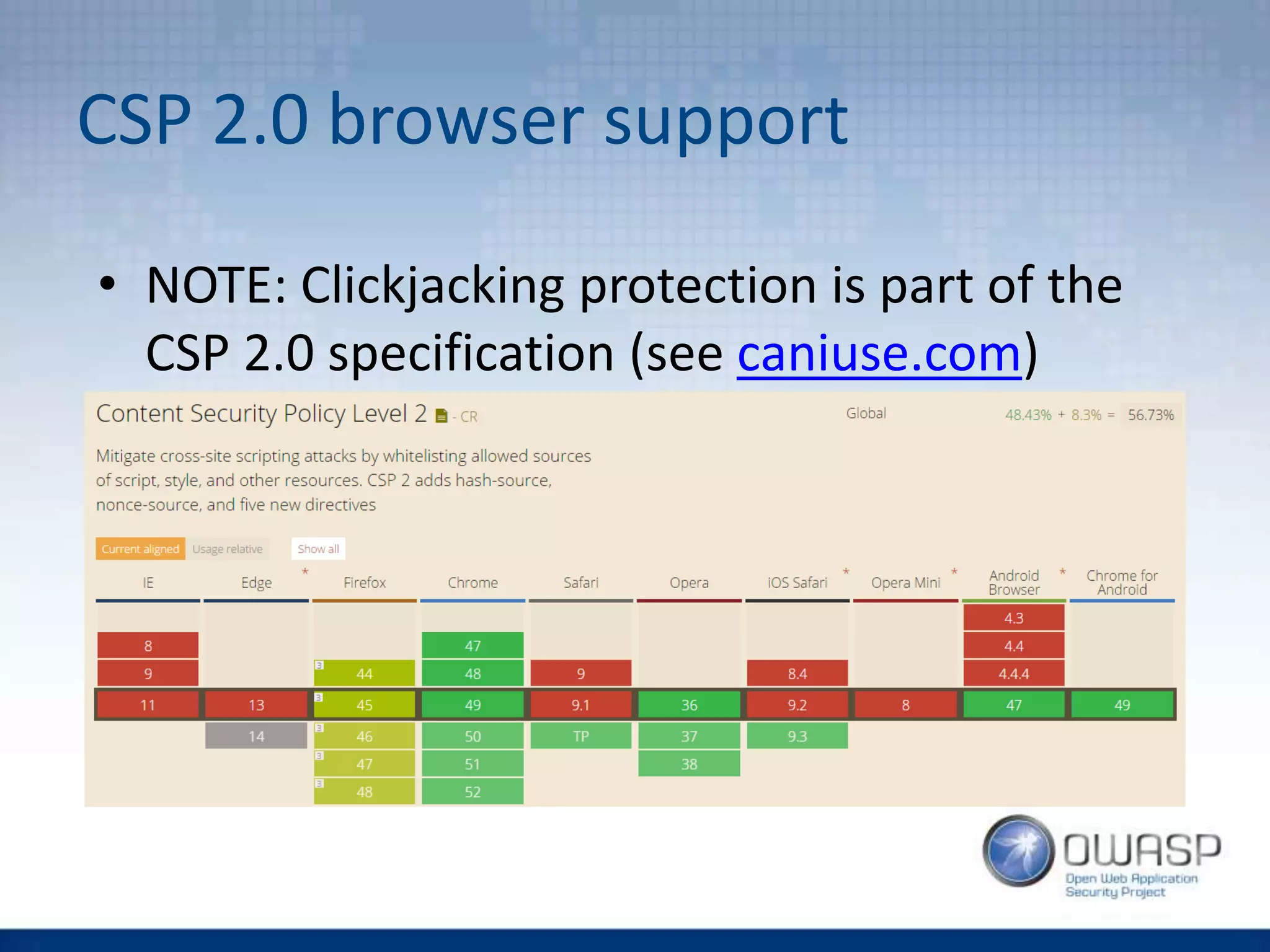
![CSP - Implementation
• You want your developer team to be aware of
CSP to detect problems early
• It is better to turn this feature on in your
software stack (then e.g. web server), but be
aware – it is somehow still a new feature:
“Spring Security does not provide support for this [CSP] as the specification is not
released and it is quite a bit more complicated. However, you could use the static
headers feature to implement this. To stay up to date with this issue and to see how you
can implement it with Spring Security refer to SEC-2342”](https://image.slidesharecdn.com/owaspwebapplicationsecurityheaders1-160429210343/75/Wroclaw-2-Web-Application-Security-Headers-30-2048.jpg)