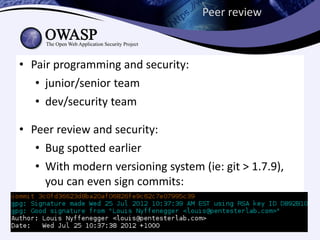
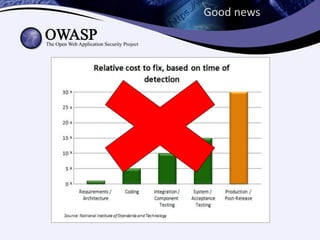
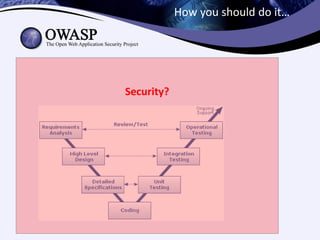
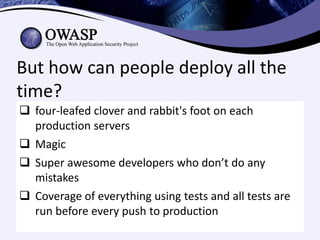
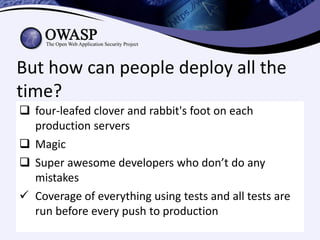
Test-driven security involves writing security-focused test cases to test for vulnerabilities during the development process. This helps enable continuous deployment by ensuring new code does not introduce security bugs. The key aspects discussed are:
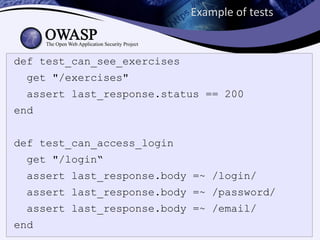
1) Having developers or security experts write test cases to validate common vulnerabilities like authentication failures, input validation, and authorization checks.
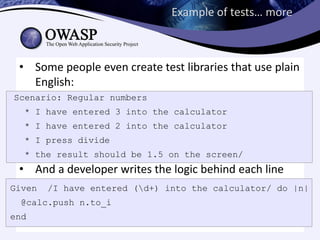
2) Involving non-technical team members like project managers in writing test cases using plain language to specify scenarios.
3) Integrating security testing into continuous integration pipelines to automatically catch issues during code reviews.












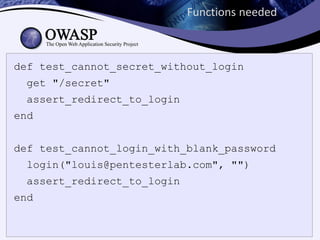
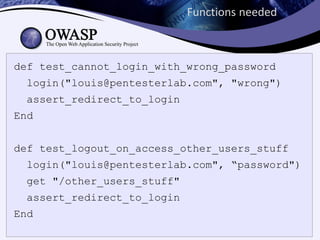
![Functions needed
def login(user,password)
creds = { :email => user,
:password => password }
post("/login", creds)
end
def assert_redirect_to_login
assert last_response.header["Location"] =~ //login$/
assert last_response.status == 302
end](https://image.slidesharecdn.com/owasp-tds-130228160429-phpapp01/85/Owasp-tds-19-320.jpg)