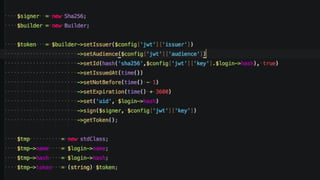
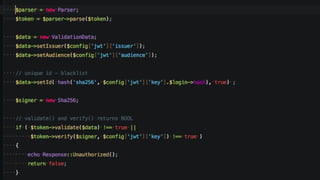
- JSON Web Tokens (JWTs) are a compact and self-contained way for securely transmitting information between parties as JSON objects. JWTs can be signed using a secret or public/private key pair to provide verification of the token.
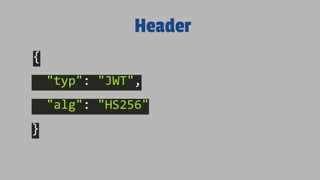
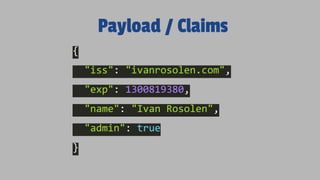
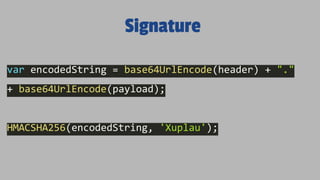
- JWTs contain encoded JSON objects comprising three parts - a header, claims, and signature. The header describes the token type and signing algorithm. Claims contain the user identity and other data. The signature ensures the token hasn't been altered.
- JWTs provide a number of advantages over traditional session cookies, including being more leightweight, easier to pass across domains, and not requiring server-side storage. They can also be used to implement stateless authentication for APIs.