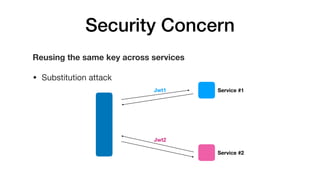
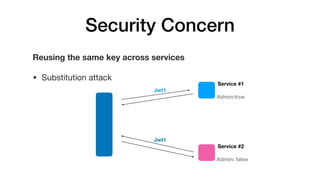
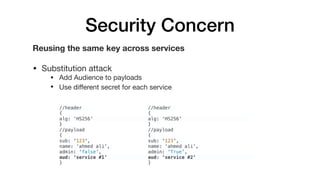
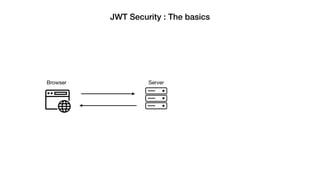
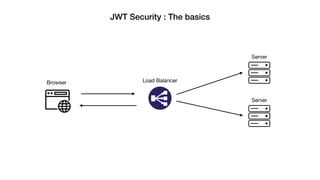
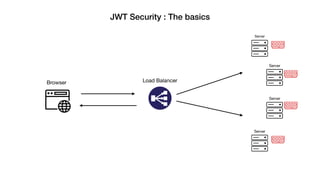
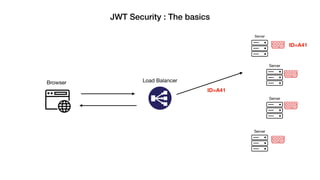
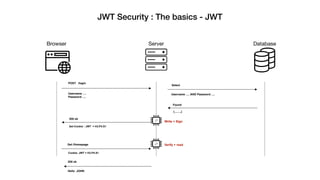
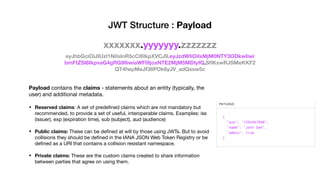
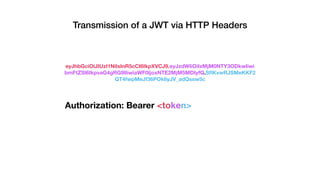
JSON Web Tokens (JWTs) are a compact way to securely transmit information between parties as a JSON object signed with a secret or public/private key pair. JWTs have three parts - a header specifying the signing algorithm, a payload containing claims, and a signature. The document discusses the structure and security concerns of JWTs such as information leakage, weak algorithms, and attacks that modify the algorithm or signature.






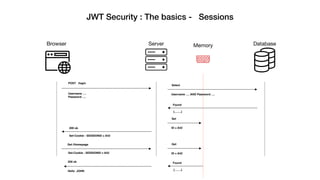


















![Security Concern
Changing the algorithm from RS256 to HS256
const decoded = jwt.verify(
token,
publickRSAKey,
{ algorithms: ['HS256' , 'RS256'] } //accepted both algorithms
)
//header
{
alg: 'RS256' => 'HS256'
}
//payload
{
sub: '123',
name: ‘ahmed ali’,
admin: 'false' => 'true'
}
modification that attacker can make:](https://image.slidesharecdn.com/jwt-security-191110090923/85/Jwt-Security-37-320.jpg)