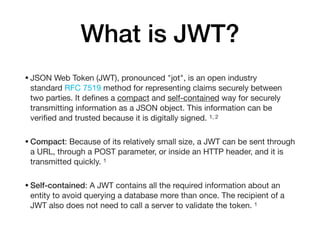
JWTs are a compact way to securely transmit information between parties as a JSON object that can be digitally signed and verified. A JWT contains a header, payload, and signature. The payload contains claims about an entity that are used to generate the signature. Flask JWT extensions make it easy to generate and verify JWTs to authenticate users and restrict access to protected routes in Flask applications. Access tokens are short-lived JWTs that grant access to resources, while refresh tokens allow new access tokens to be generated after expiration. Blacklists are used to revoke compromised tokens before expiration.








![JWT in a Flask API
from flask import Flask, jsonify, request
from flask_jwt_extended import (
JWTManager,
jwt_required,
create_access_token,
get_jwt_identity,
)
app = Flask(__name__)
# Setup the Flask-JWT-Extended extension
app.config["JWT_SECRET_KEY"] = "super-secret" # Change
this!
jwt = JWTManager(app)
Imports and Setup](https://image.slidesharecdn.com/jwtwithflask-slidedeck-alanswenson-190424204630/85/Jwt-with-flask-slide-deck-alan-swenson-12-320.jpg)
![JWT in a Flask API
# Provide a method to create access tokens. The create_access_token()
# function is used to actually generate the token, and you can return
# it to the caller however you choose.
@app.route("/login", methods=["POST"])
def login():
if not request.is_json:
return jsonify({"msg": "Missing JSON in request"}), 400
username = request.json.get("username", None)
password = request.json.get("password", None)
if not username:
return jsonify({"msg": "Missing username parameter"}), 400
if not password:
return jsonify({"msg": "Missing password parameter"}), 400
if username != "test" or password != "test":
return jsonify({"msg": "Bad username or password"}), 401
# Identity can be any data that is json serializable
access_token = create_access_token(identity=username)
return jsonify(access_token=access_token), 200
Login Route](https://image.slidesharecdn.com/jwtwithflask-slidedeck-alanswenson-190424204630/85/Jwt-with-flask-slide-deck-alan-swenson-13-320.jpg)
![JWT in a Flask API
# Protect a view with jwt_required, which requires a
# valid access token
# in the request to access.
@app.route("/protected", methods=["GET"])
@jwt_required
def protected():
# Access the identity of the current user with
# get_jwt_identity
current_user = get_jwt_identity()
return jsonify(logged_in_as=current_user), 200
if __name__ == "__main__":
app.run()
Protected Route](https://image.slidesharecdn.com/jwtwithflask-slidedeck-alanswenson-190424204630/85/Jwt-with-flask-slide-deck-alan-swenson-14-320.jpg)



