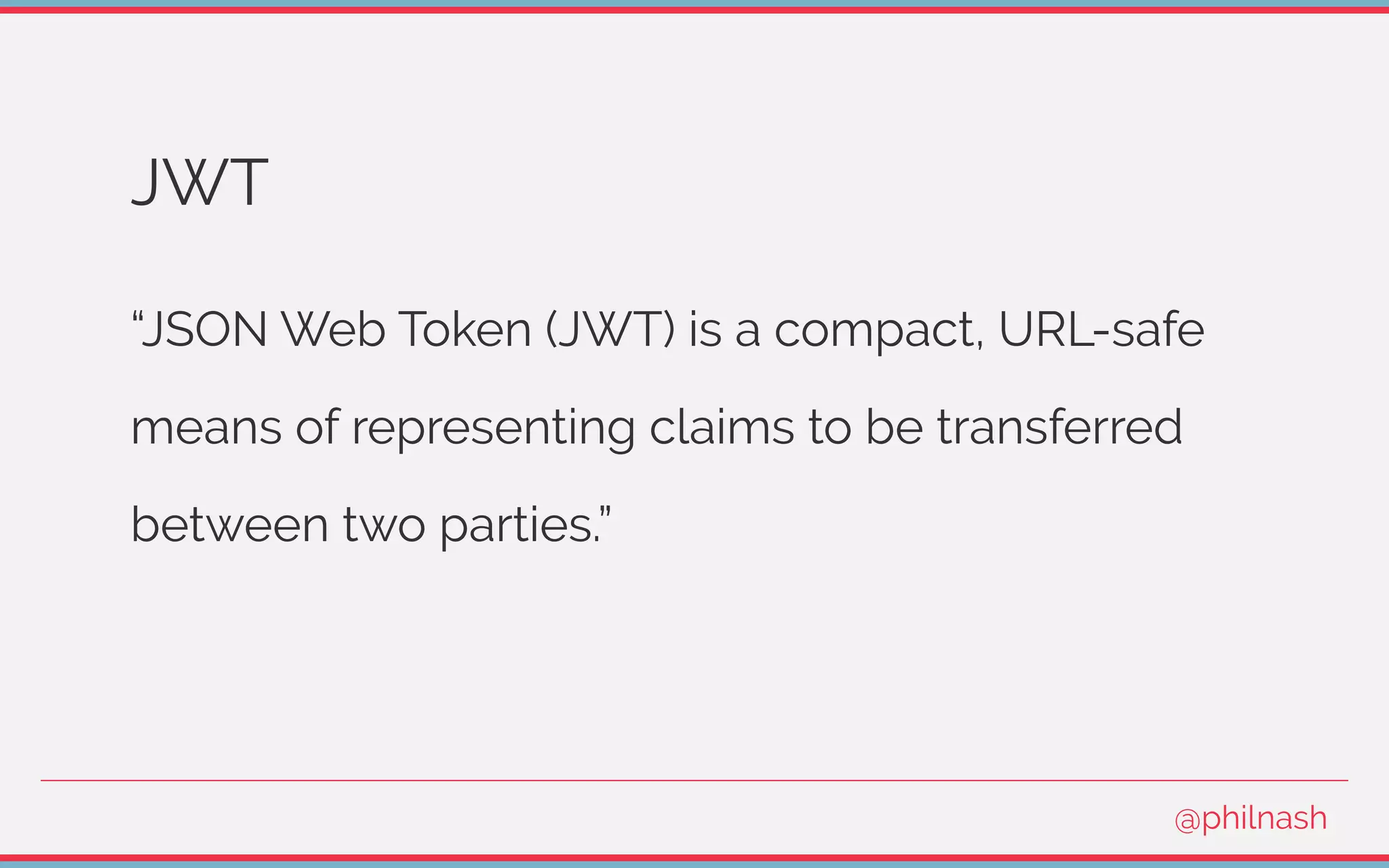
This document discusses JSON Web Tokens (JWT), explaining their purpose, structure, and use cases such as stateless sessions and microservice authentication. It covers how to create and verify JWTs, including encoding and signing processes, while highlighting potential pitfalls like public data and security concerns. The document also advises against using JWT for traditional session management, recommending best practices instead.













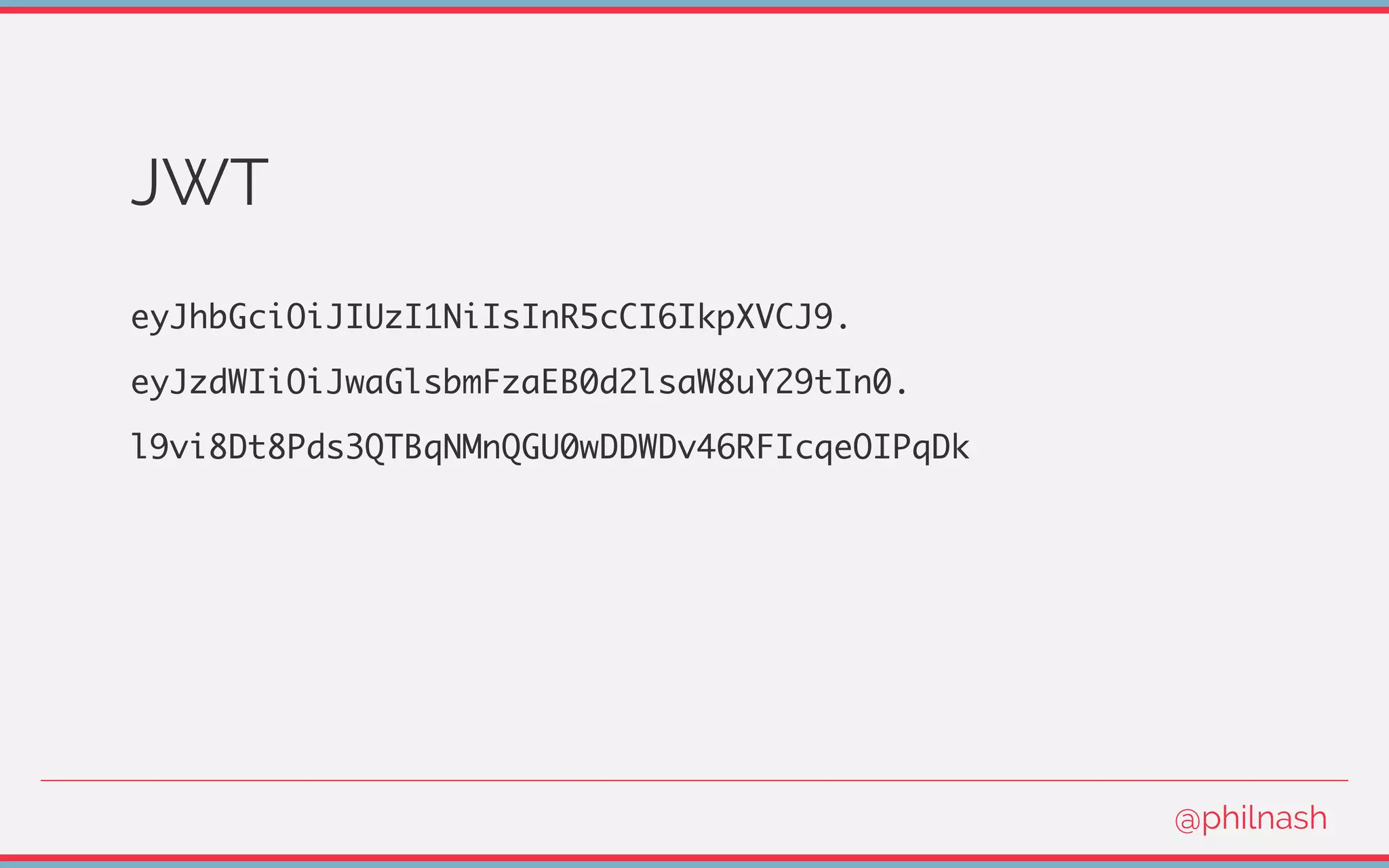
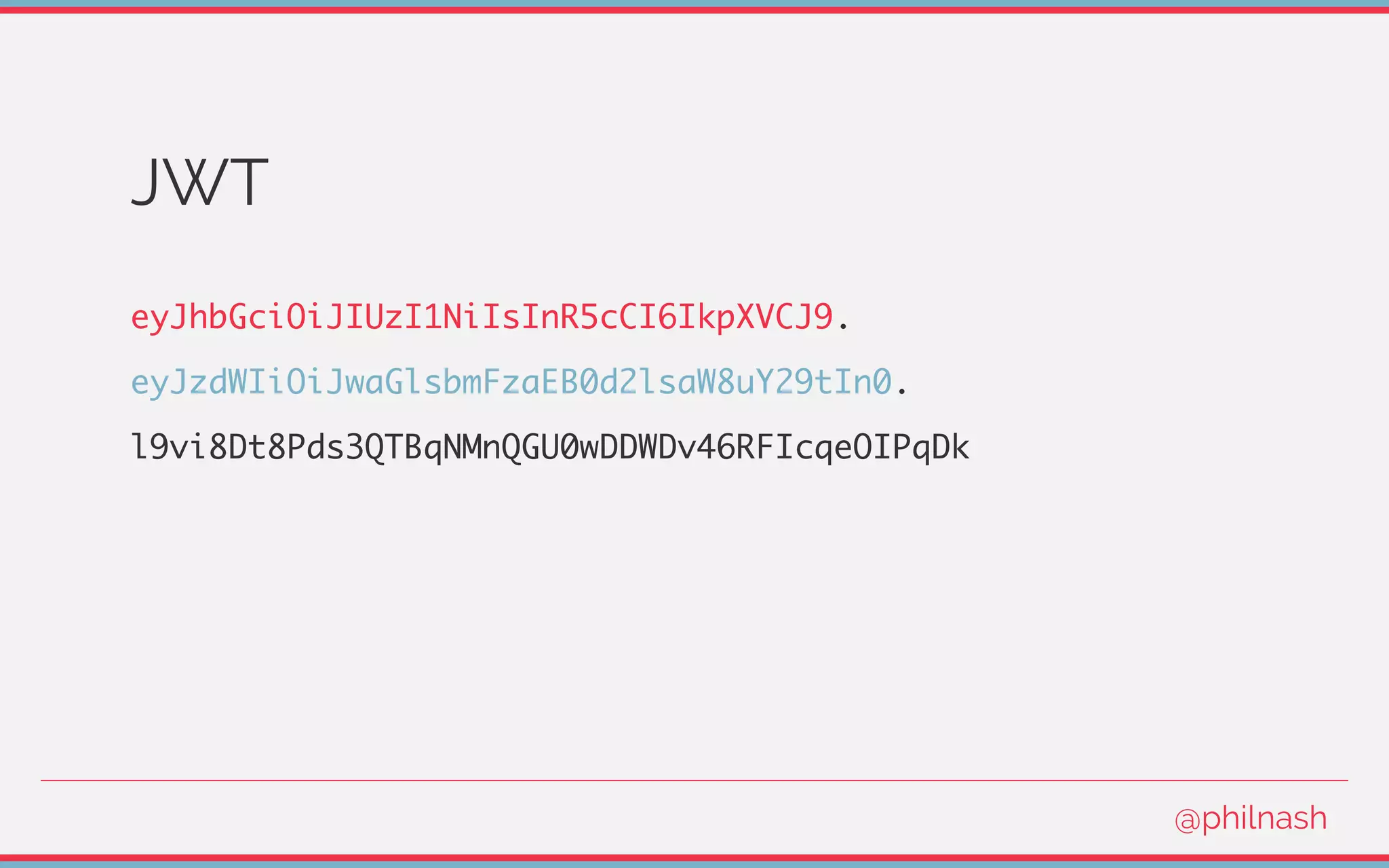
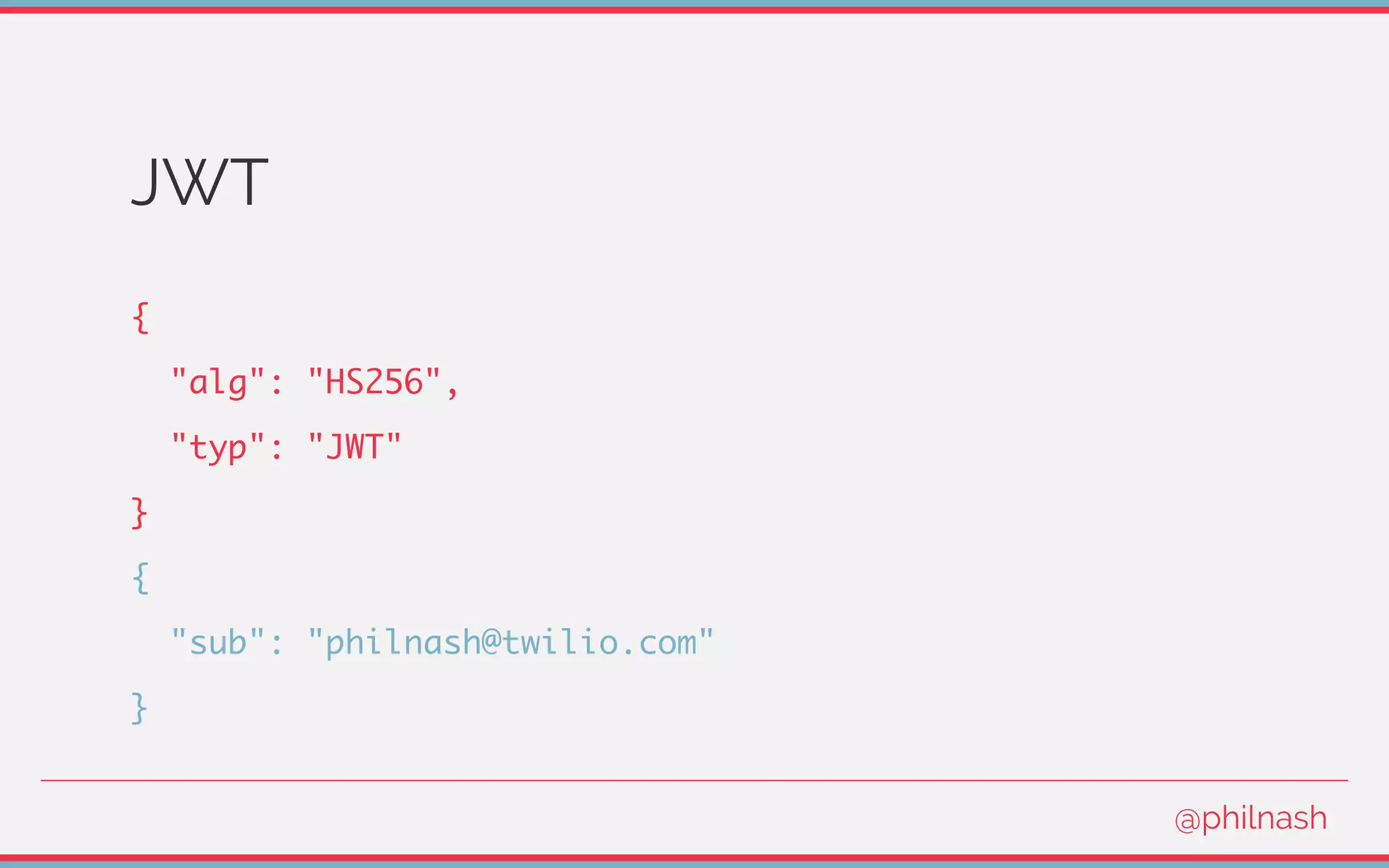







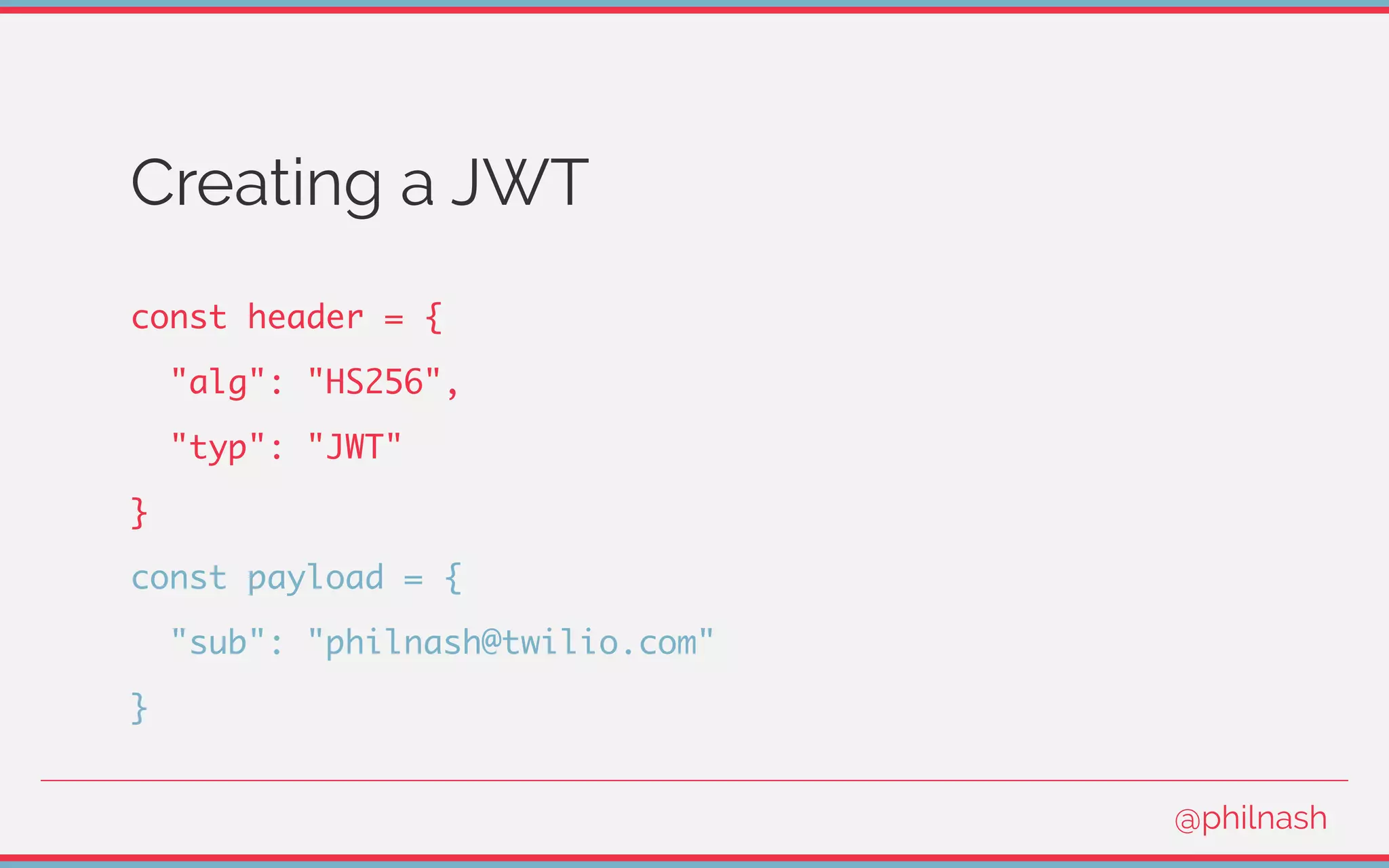

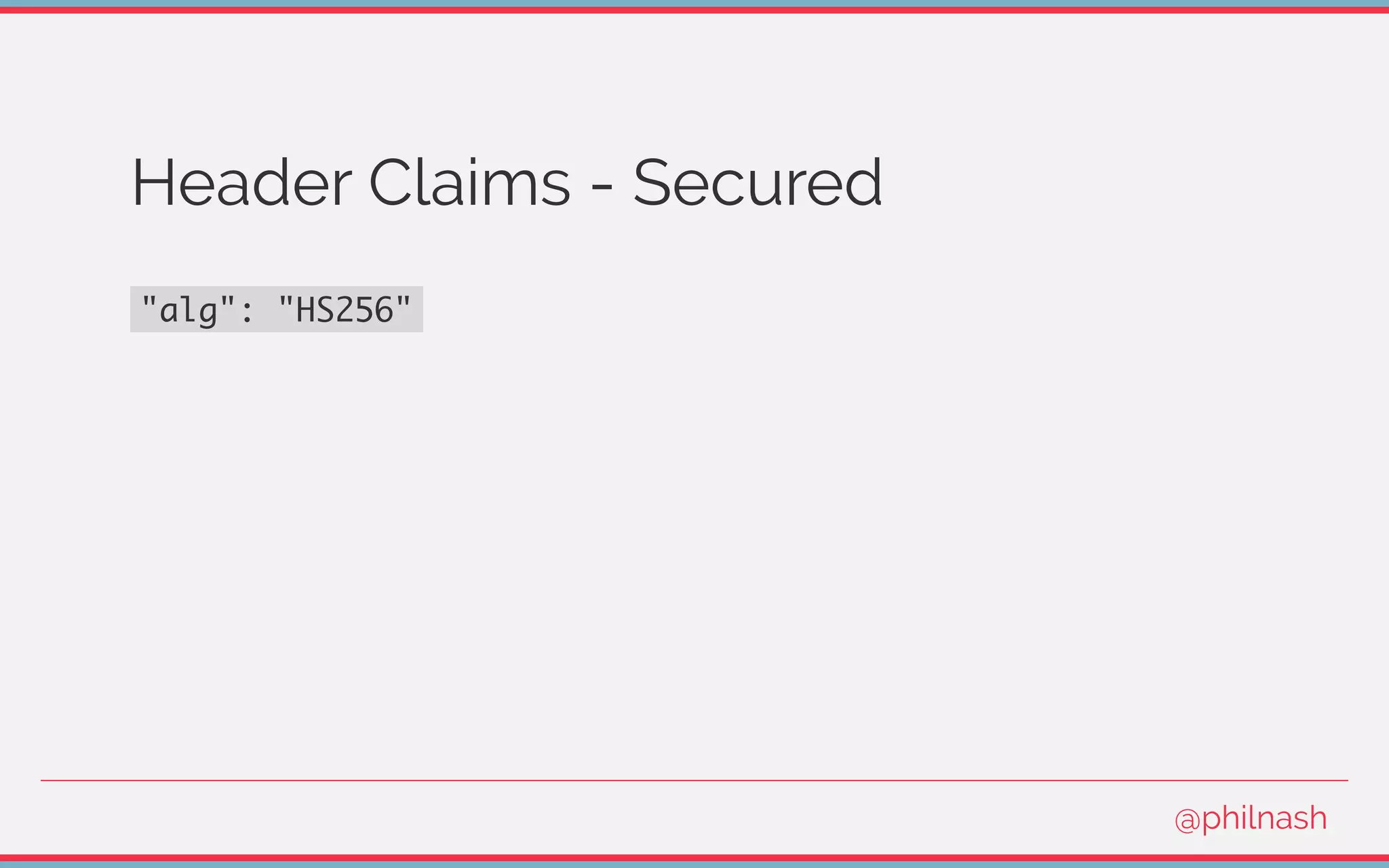
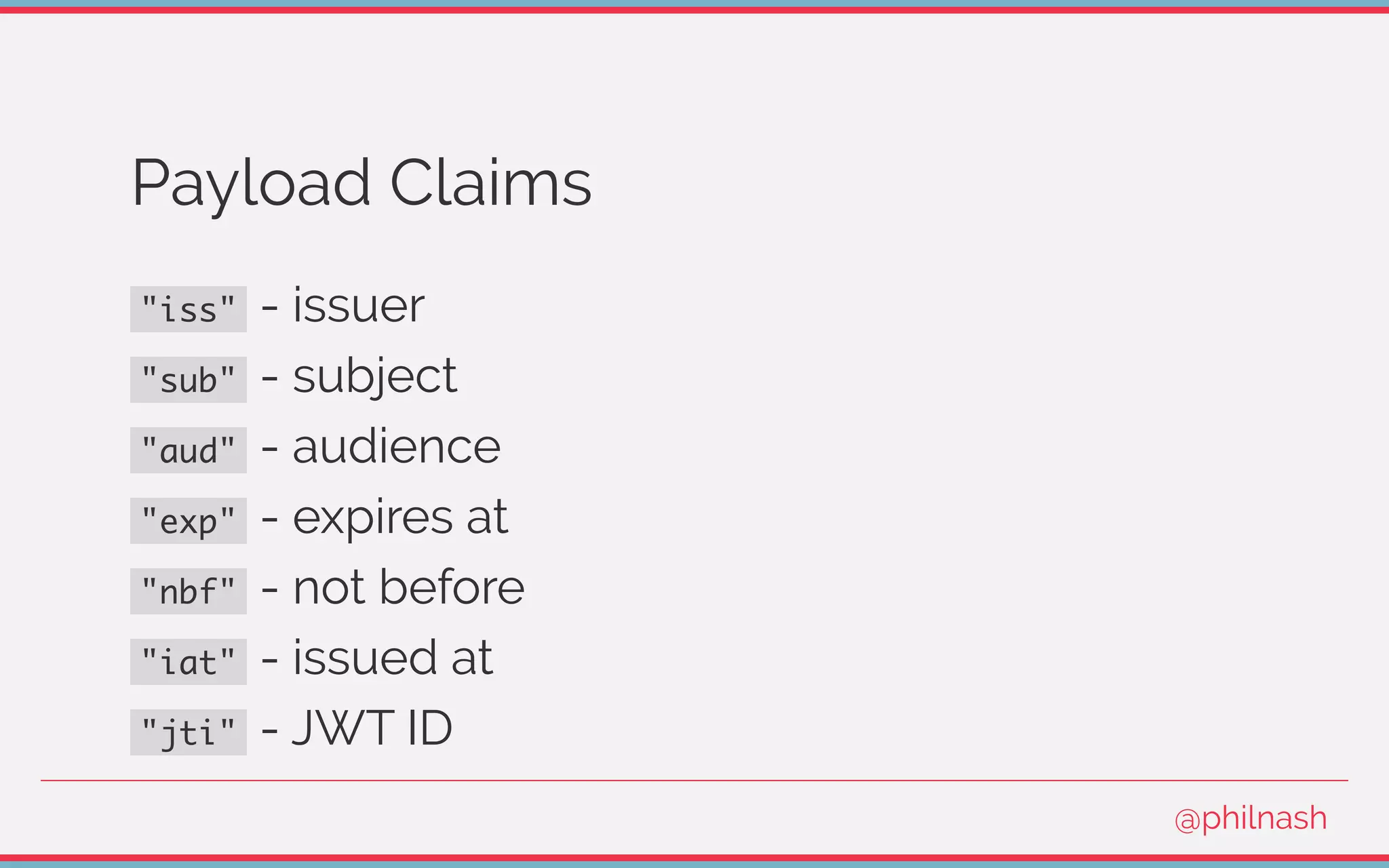
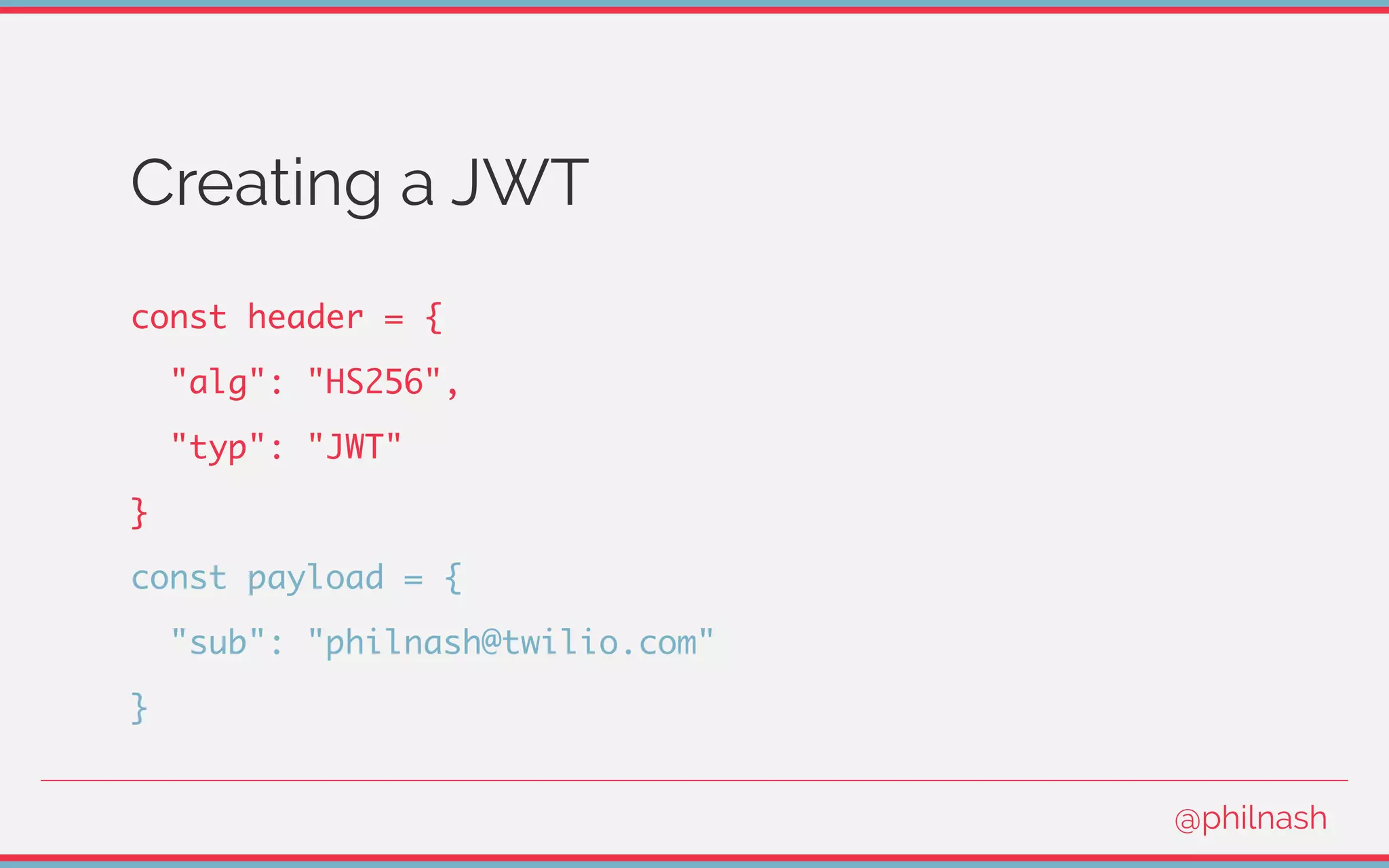
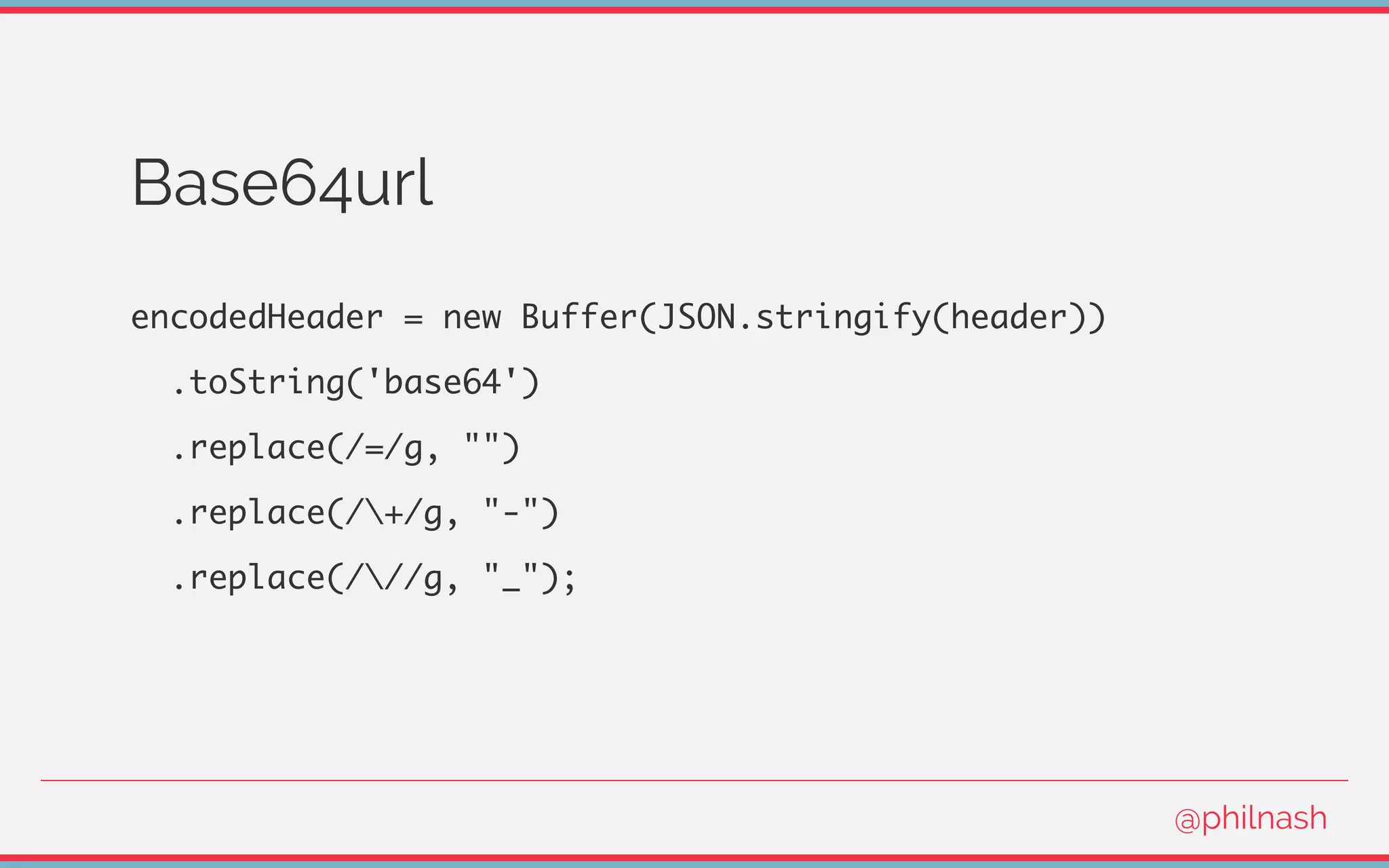
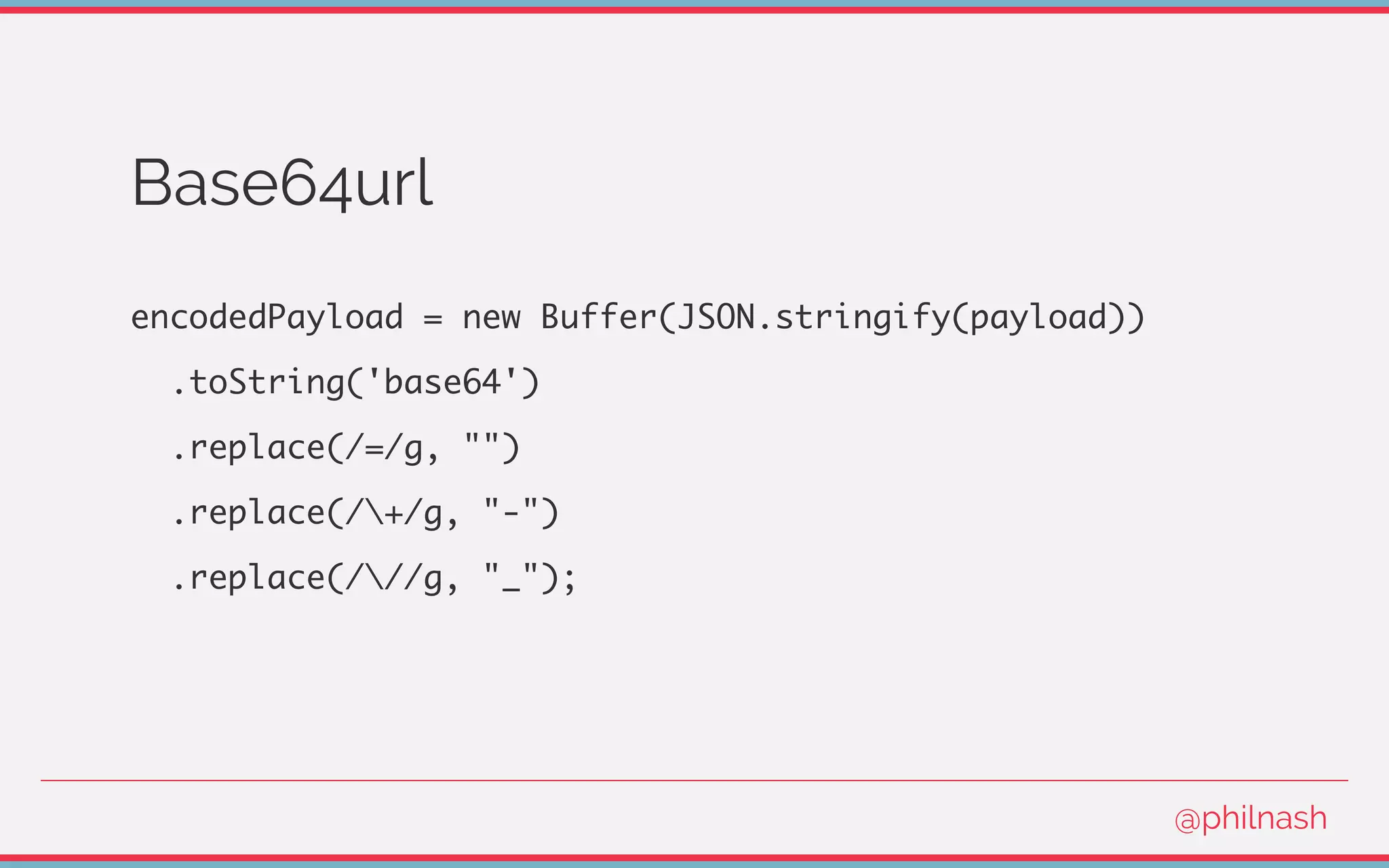

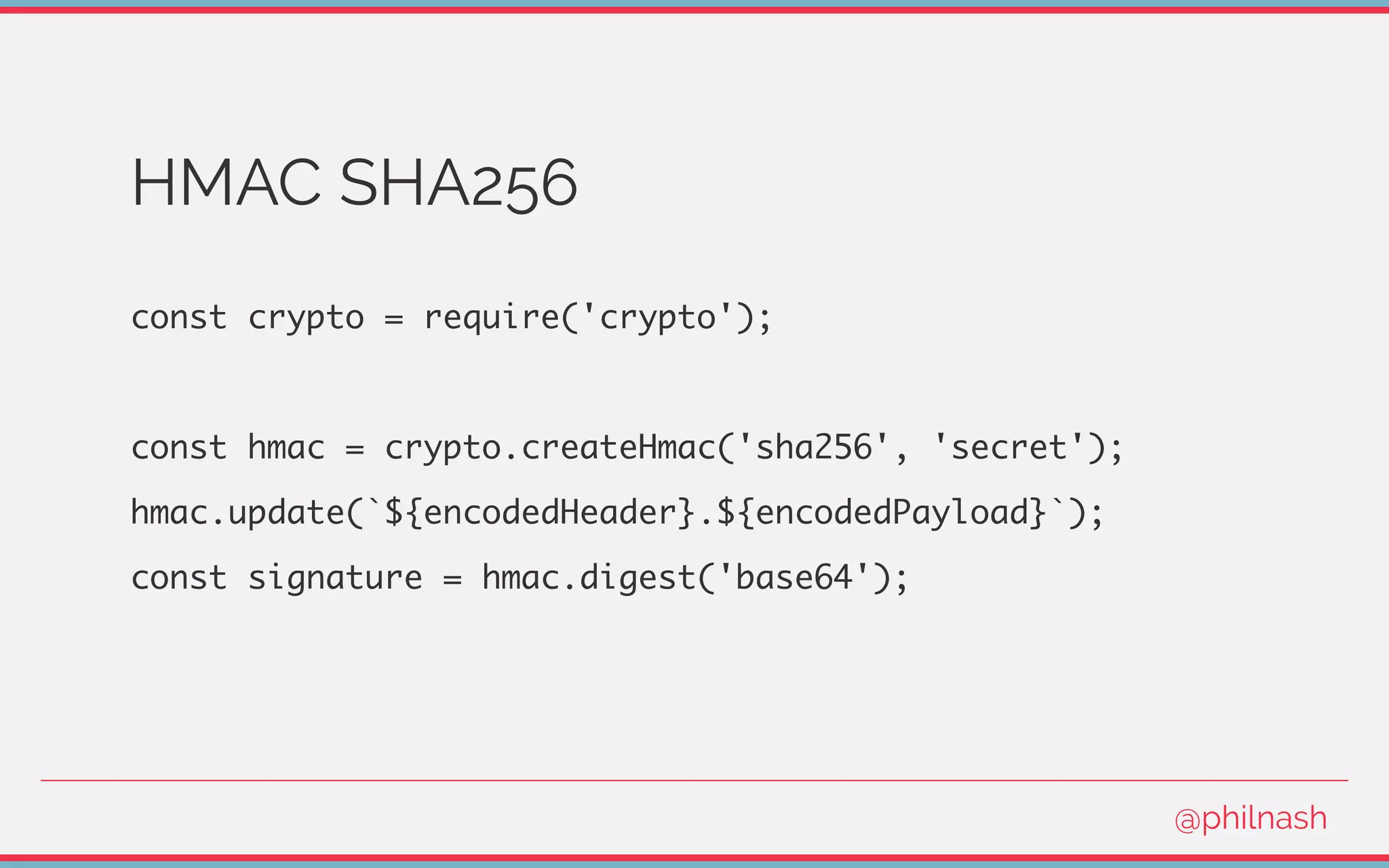
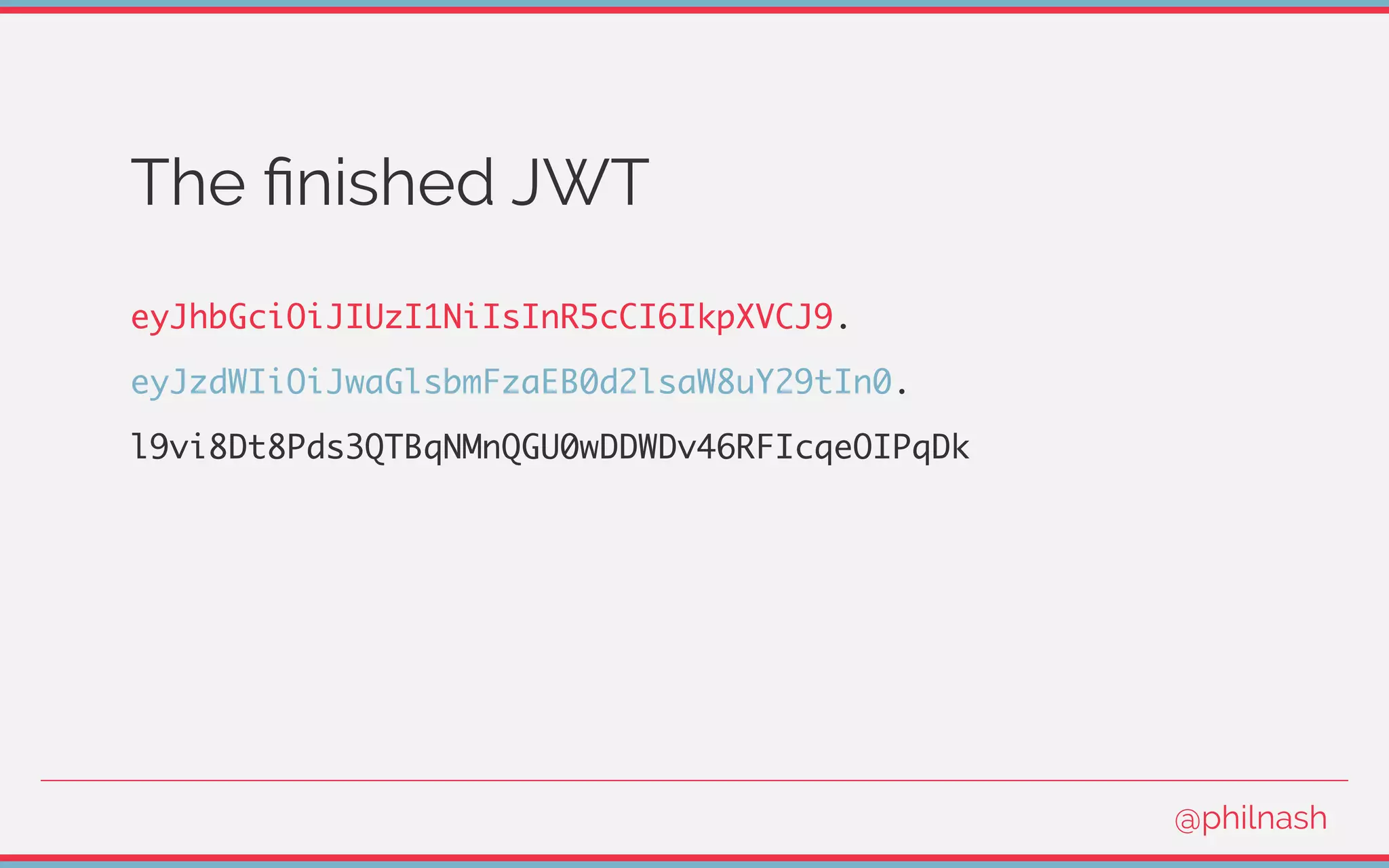

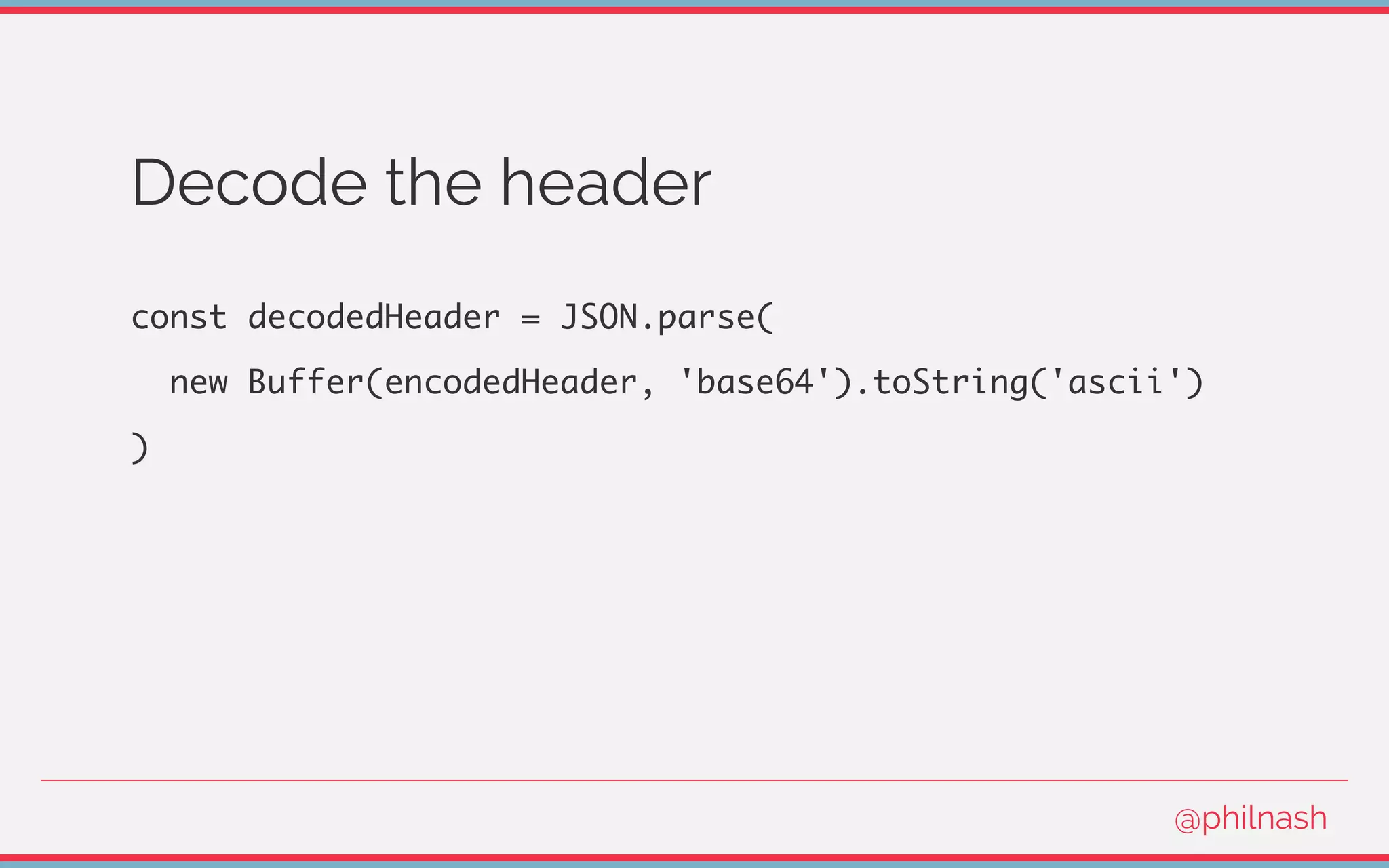
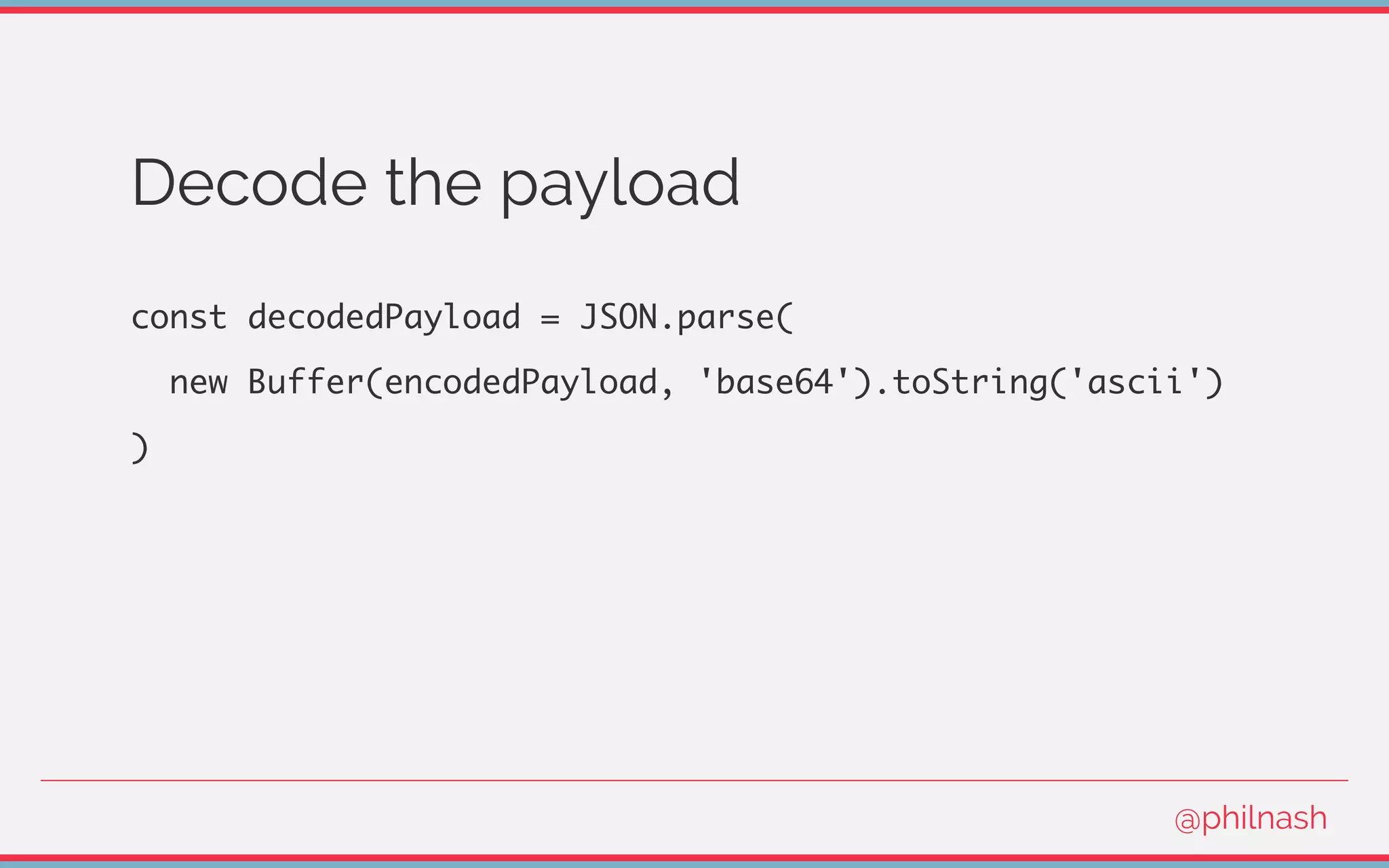
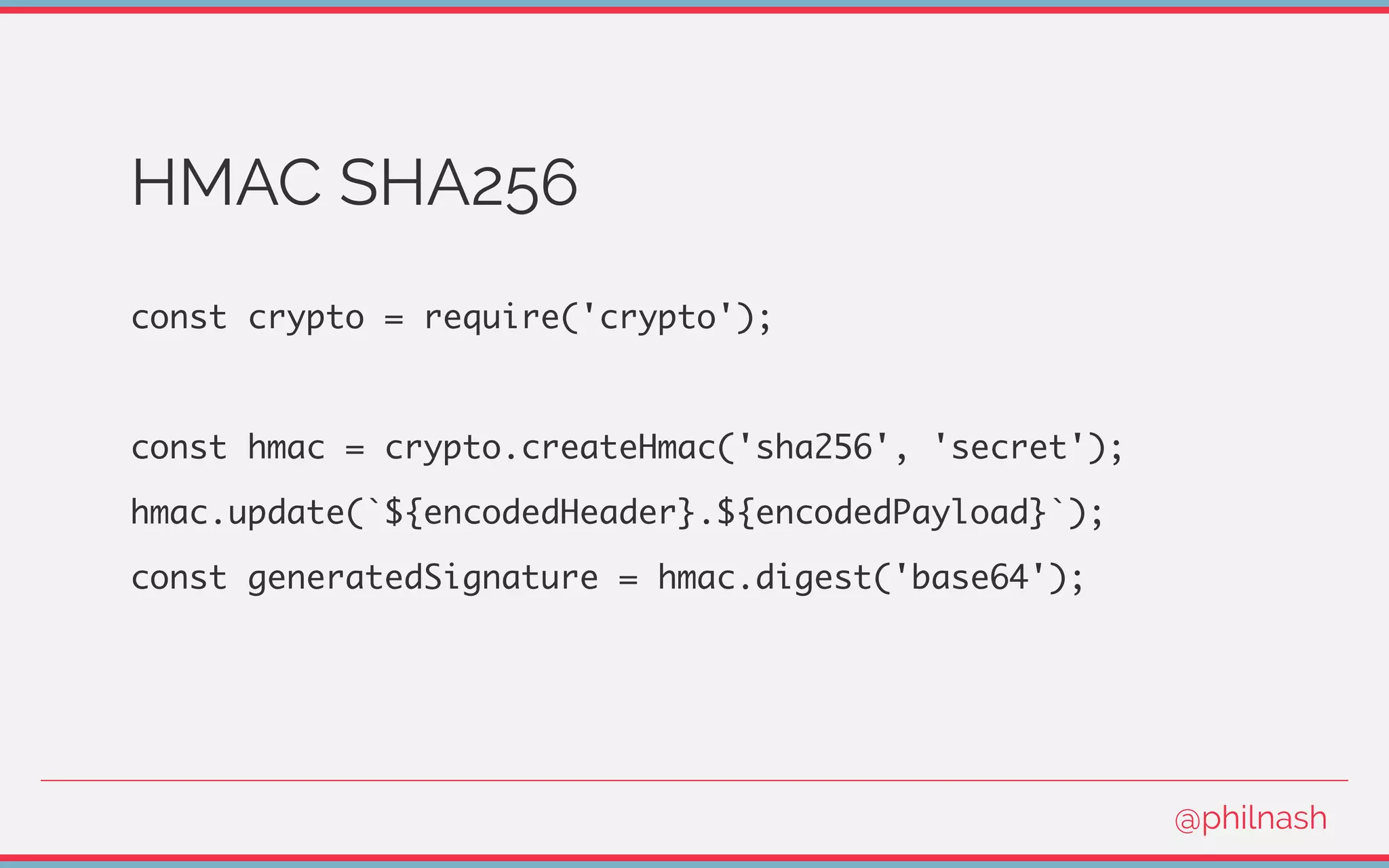
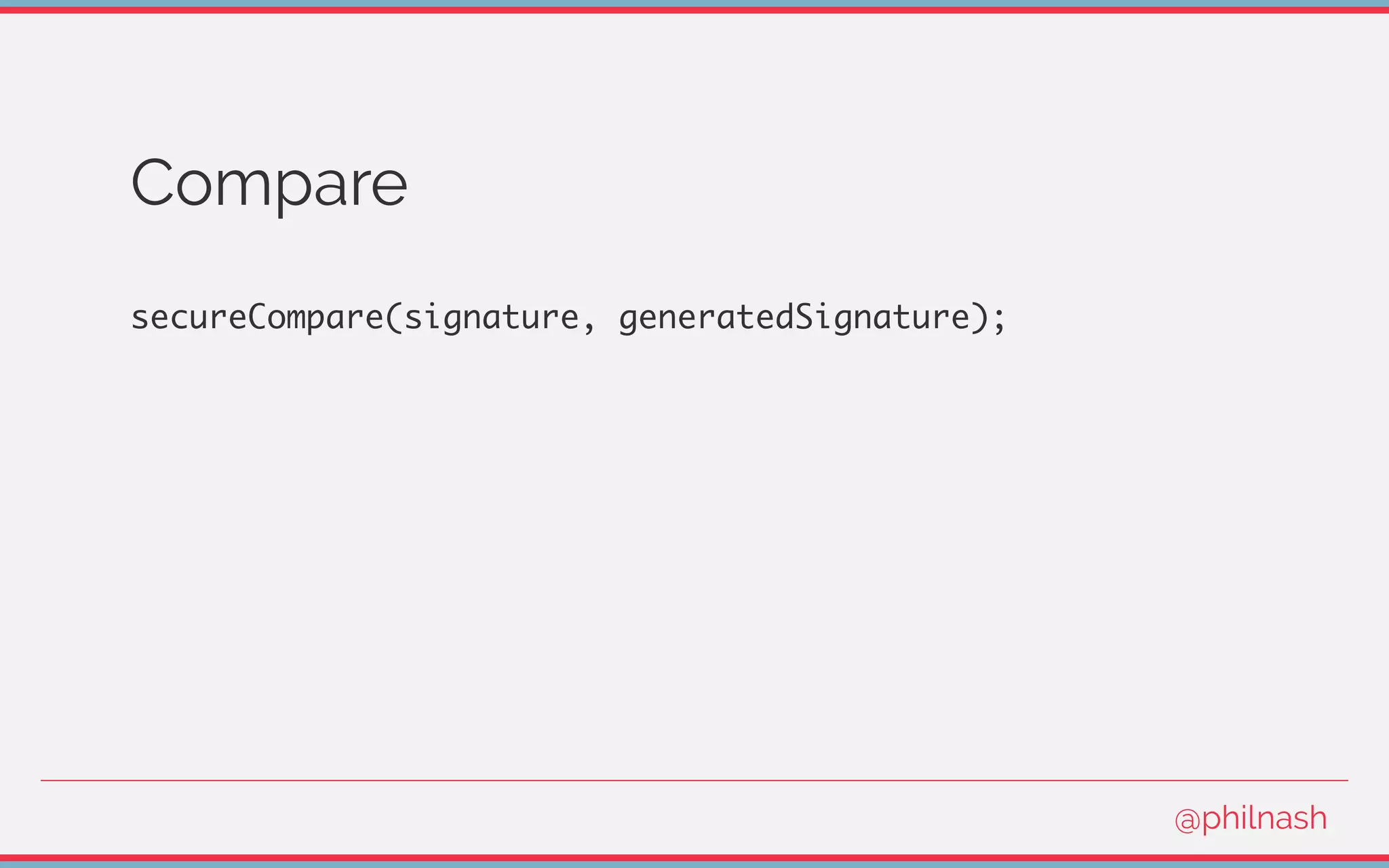
![Verifying a JWT
[
encodedHeader,
encodedPayload,
signature
] = jwt.split('.');
@philnash](https://image.slidesharecdn.com/bvtvsm4orlafqlkcaxxo-signature-753cb6f16dd9e78187c27f5c16d36b5d35566cf18d25ee83278c932237b78616-poli-170522152115/75/Jwt-wtf-Phil-Nash-Codemotion-Amsterdam-2017-47-2048.jpg)