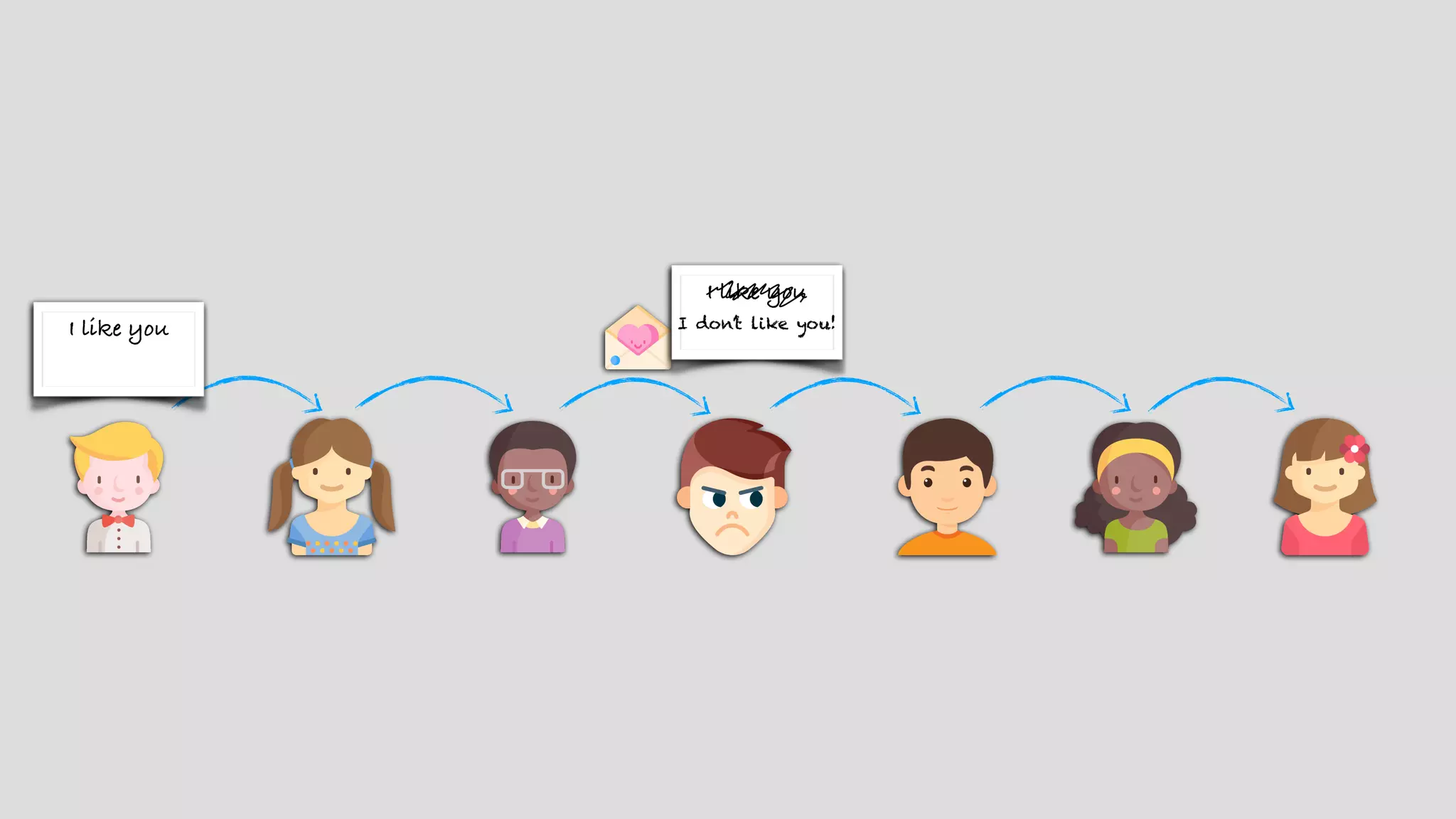
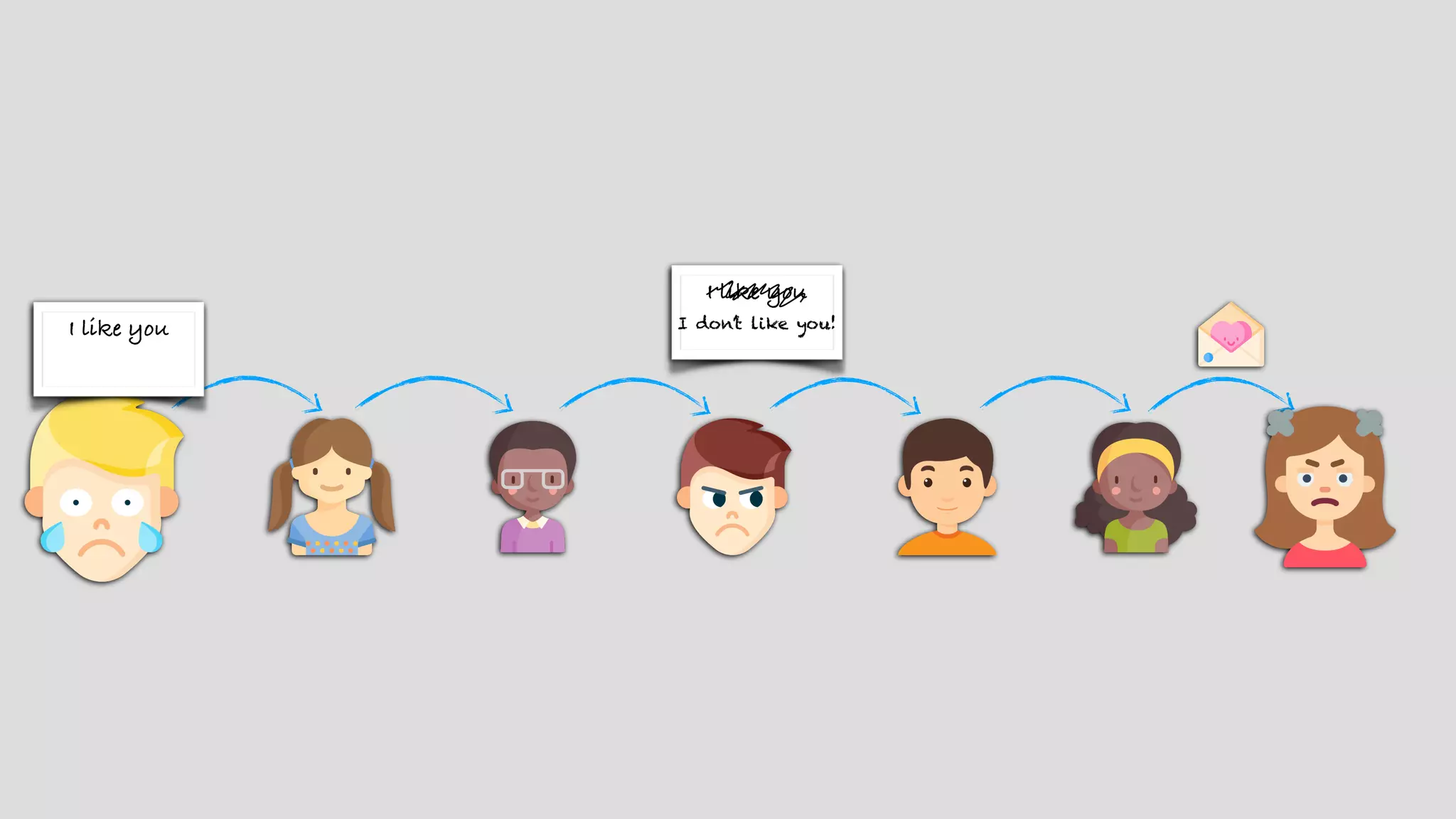
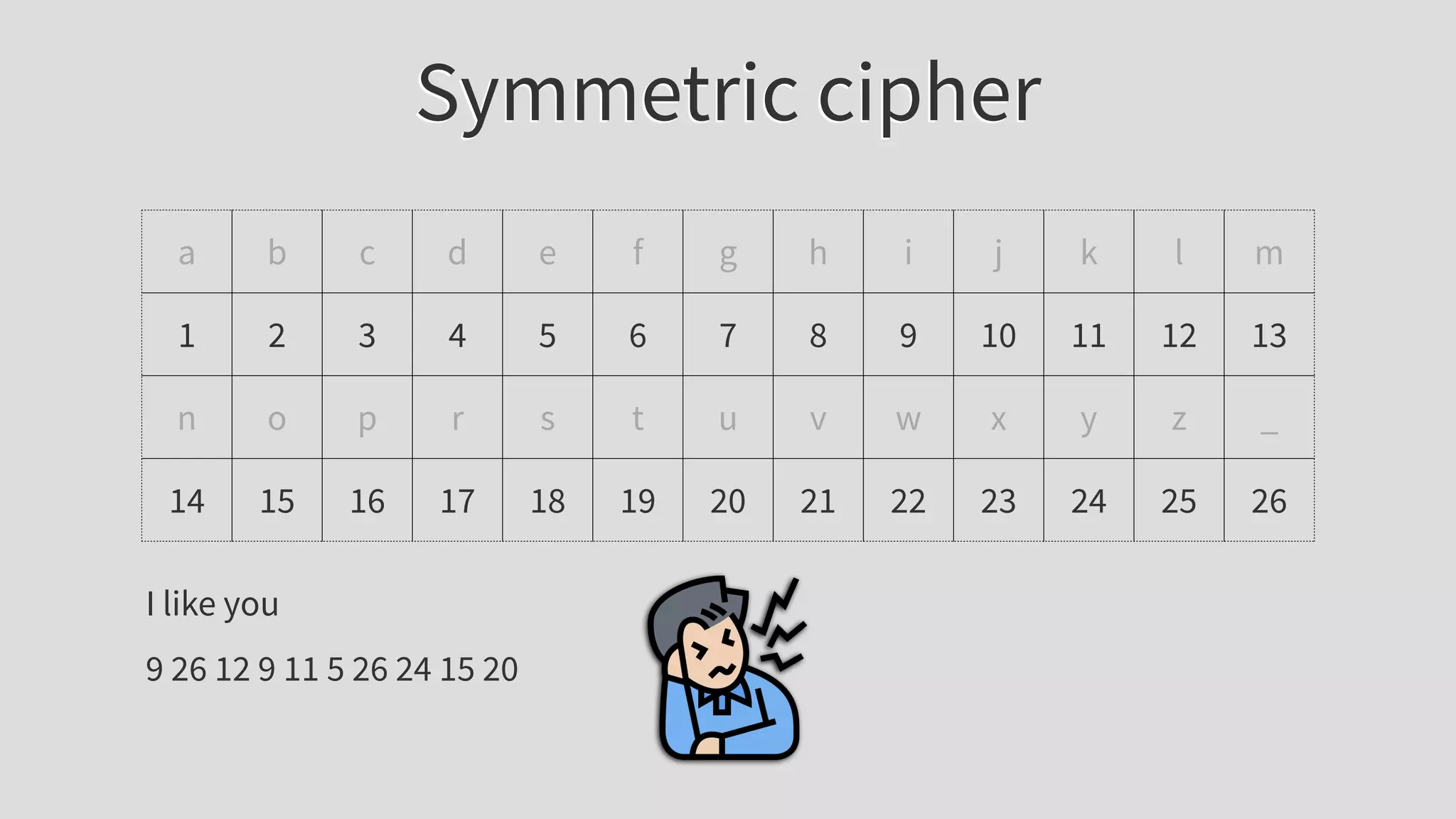
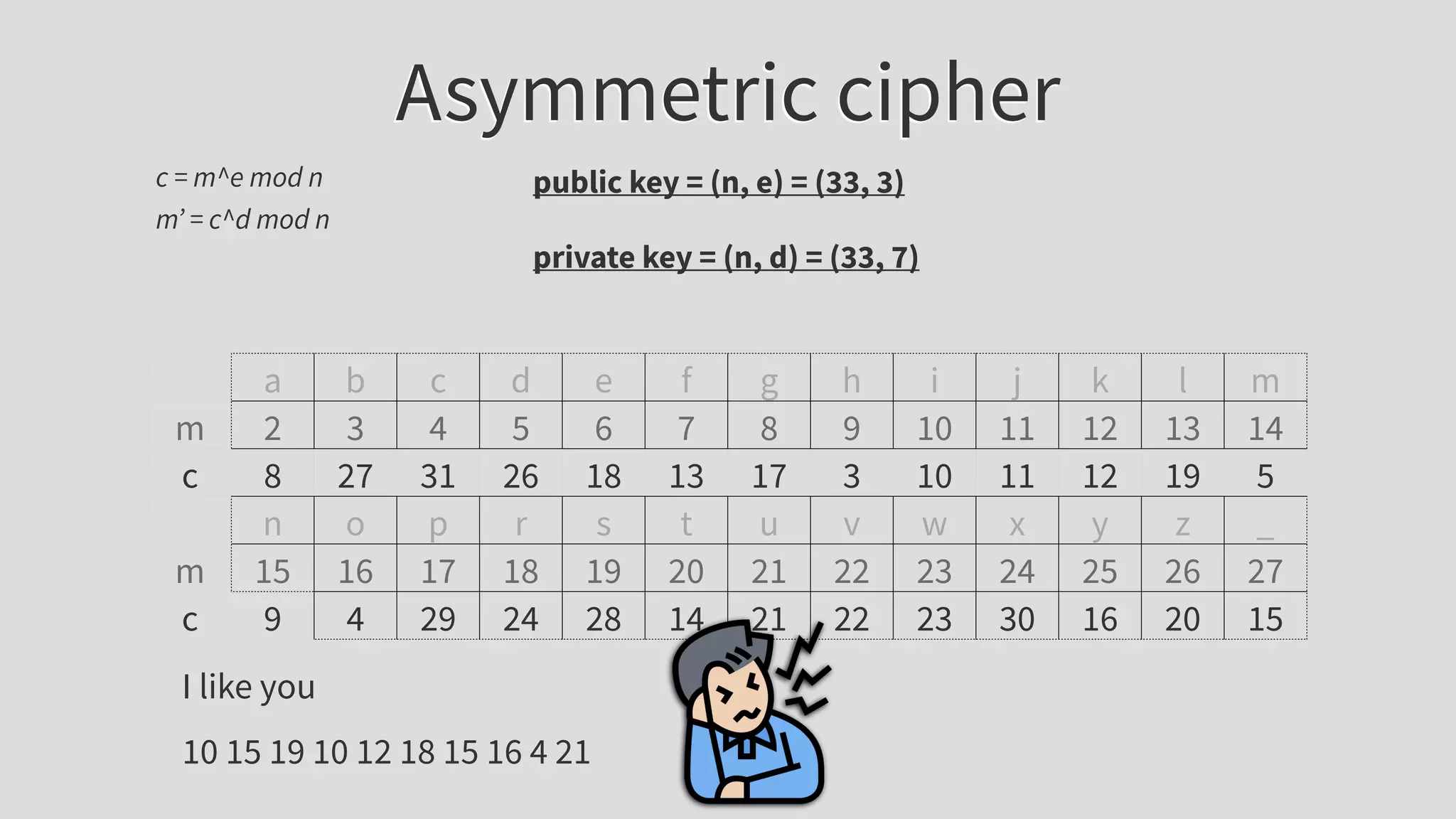
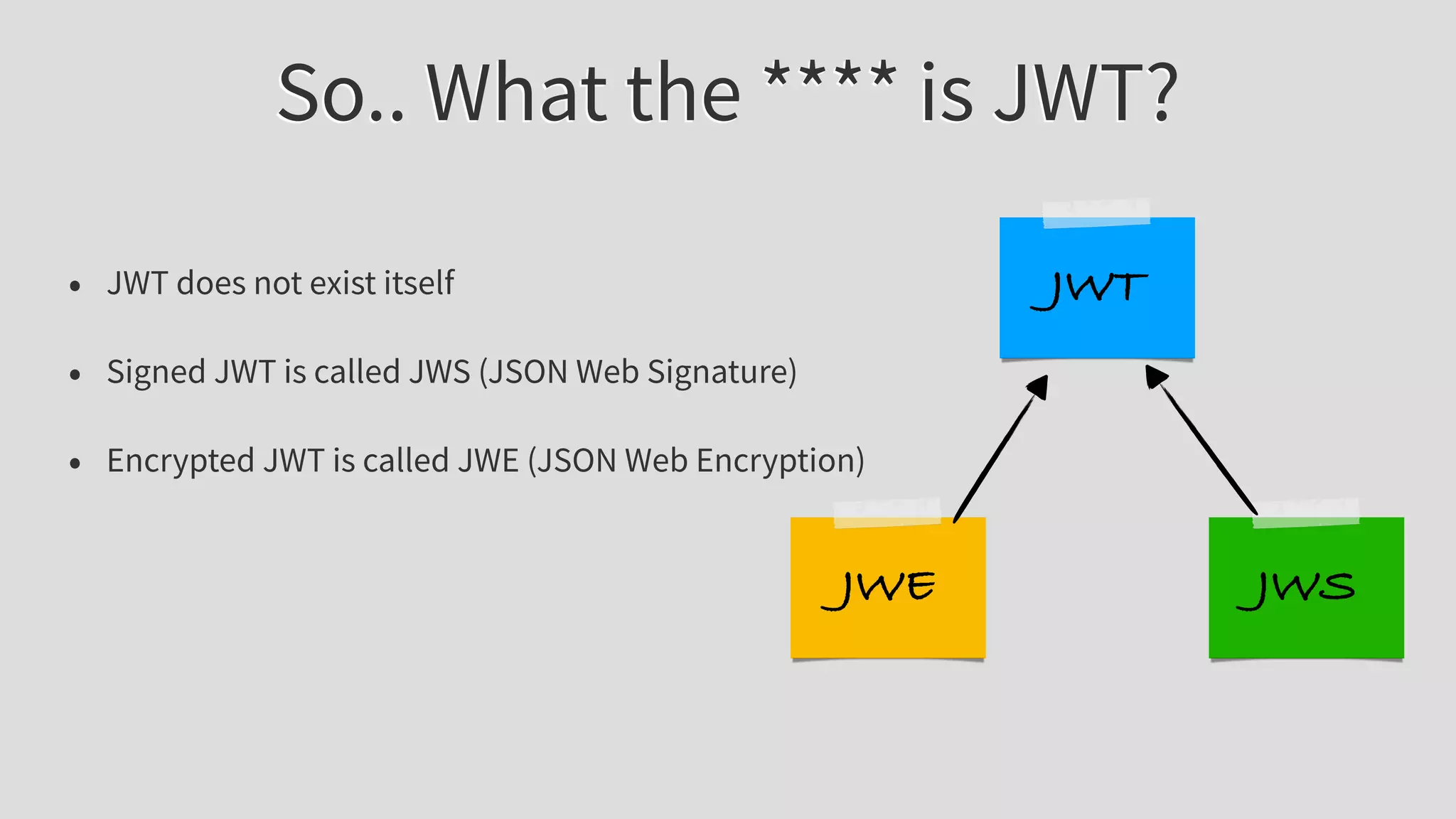
The document provides an extensive overview of JSON Web Tokens (JWT), including their structure and implementation using asymmetric and symmetric ciphers. It explains the various components like headers, payloads, and signatures, while also discussing JWT use cases, vulnerabilities, and validating signatures. Additionally, it outlines best practices for secure token handling and includes references to further reading and resources.




















![Custom claims
{
“alg":"RS512",
"typ":"JWT"
}
{
"name": "Maciej",
"surname": "Treder",
"privileges": ["booking_reschedule"],
"exp": 1594655553234
}
• Public claims - defined at will by those
using JWTs. To avoid collisions should
be defend in the IANA JSON Web Token
Registry
• Private claims - custom claims create to
share information between parties that
agree on using them](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-28-2048.jpg)
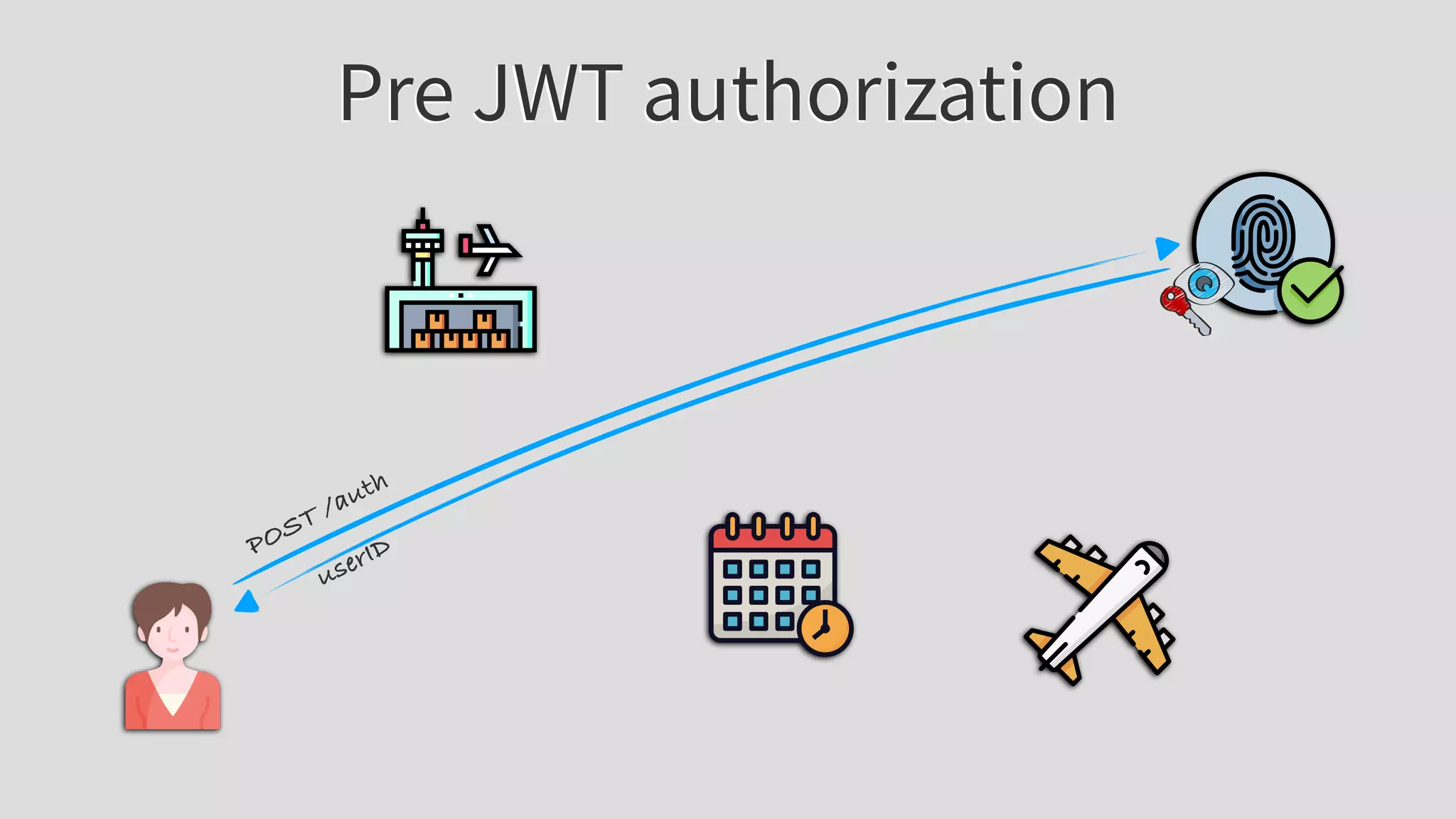

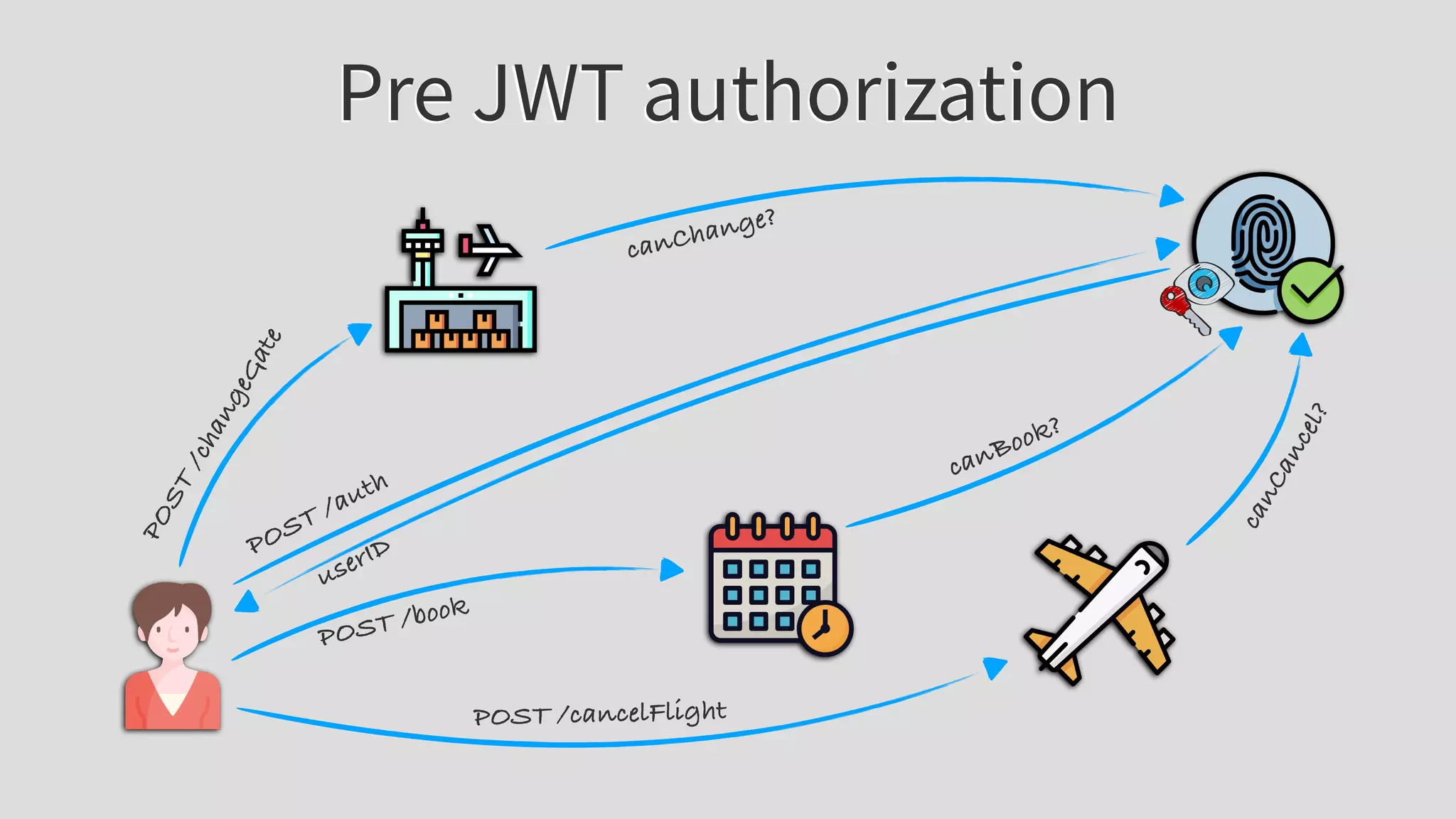

![JWT authorization
POST /auth
{privs: [“booking”], exp: 12345}](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-33-2048.jpg)
![JWT authorization
POST /auth
{privs: [“booking”], exp: 12345}
POST /book
POST/changeGate
POST /cancelFlight](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-34-2048.jpg)
![JWT authorization
POST /auth
{privs: [“booking”], exp: 12345}
POST /book
POST/changeGate
POST /cancelFlight](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-35-2048.jpg)
![JWT authorization
POST /auth
POST/changeGate
@PostMapping("/changeGate")
public ResponseEntity<Gate> changeGate(
@RequestHeader("jwt-token") Token token,
@RequestBody Gate gate
) {
DecodedToken decoded = decodeToken(token);
if(decoded.hasPrivilege("changeGate") && verifySignature(token)) {
changeGate(gate);
return this.flightDetails;
}
throw new AuthorizationFailureException();
}
{privs: [“booking”]}](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-36-2048.jpg)








![JWKS
{
"alg":"HS256",
"typ":"JWT",
"kid":"12",
"jku":"https://my-service.com/.well-known/jwks.json"
}
{
"privileges": ["booking_reschedule"]
}
NmTt6oAkllTqmLqR-QqKxIgIsIaZIRIc](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-45-2048.jpg)
![JWKS
{
"keys": [
{
"kty": "RSA",
"kid": "1",
"alg": "RS256",
"use": "sig",
"e": "AQAB",
"n": "ujZ1fTy2k-
xc6Fa3Bfqe1T78Zx_oWBkDS1TNgw8Jbvbzfj5wgK5
_xSK5ikNlkOXvBjrsVOnCCJXTNiHZxMtIfARbz91O-5n
cuNah1H6WntWrLmaVfiIMaaKoNjDzScG1cIjPITarEV
jDb0GI0eH9BKpFz8LUbVlcy2m7IOKbmDt6yusHsj7z
OfjlV55dT1FU-
q5bfyLXQyCf7Uy2JJAVEutWLMp3Ld53q9mvW47Lh
hXKl5pKKbLARJgkccpQdN0bURiggvYjs2SHmZgh6d
Ceap1mki4LB2aX-Z4TB-
u8GbLq51HPZSpK71rR0QzZozluS5aLE49ciQ6-5u7K
HWBbrQ"
}
]
}
Key type
Key ID
Algorithm
Usage
Exponent
Modulus](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-46-2048.jpg)
![JWKS
Standard attributes:
• kty - key type
• kid - key ID
• alg - algorithm [HMAC, RSA, …]
• use - usage
• e - exponent number
• m - modulus number
Chinese remainder algorithm:
• p, q - prime factors
• dp - d (mod p-1)
• dq - d (mod q-1)
• qi - q^-1 (mod p)
Certificate:
• x5c - x.509 certificate chain
• x5t - Thumbprint of the x.509 cert](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-47-2048.jpg)


![JWKS
{
"alg":"HS256",
"typ":"JWT",
"kid":"12",
"jku":"https://my-service.com/.well-known/jwks.json"
}
{
"privileges": ["change_gate"]
}
NmTt6oAkllTqmLqR-QqKxIgIsIaZIRIc](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-50-2048.jpg)






![jku
• Always verify the URL provided as a jku claim
{
"alg":"HS256",
"typ":"JWT",
"kid":"12",
"jku":"https://attacker.com/.well-known/jwks.json"
}
{
"privileges": ["change_gate"]
}](https://image.slidesharecdn.com/apidayslivenewyorkmaciejtreder-200809025659/75/apidays-LIVE-New-York-WT-is-JWT-by-Maciej-Treder-58-2048.jpg)





