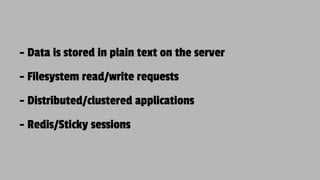
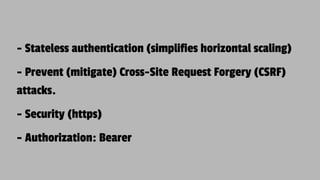
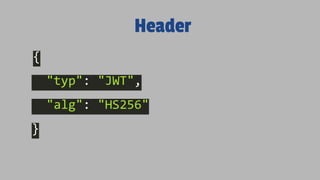
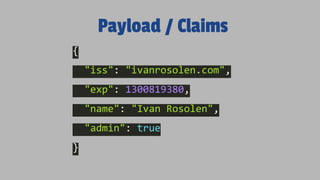
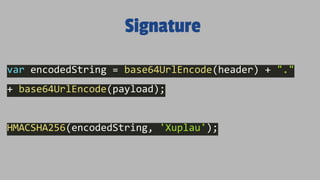
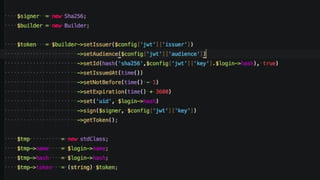
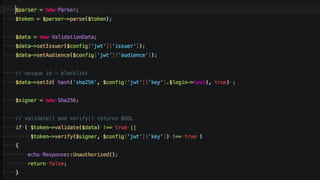
The document discusses JSON Web Tokens (JWTs) and their application in authentication and authorization, along with various related technologies and concepts, such as OAuth, CSRF protection, and stateless authentication. It outlines the structure of a JWT including the header, claims, and signature, and emphasizes their advantages in cross-language compatibility and security. Additionally, it provides resources for further learning and practical examples of JWT implementation.