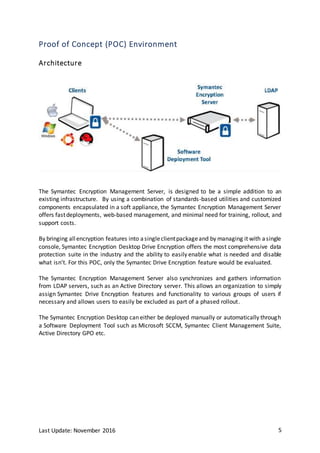
The document outlines a proof of concept for Symantec Drive Encryption, aimed at demonstrating its capabilities to a customer. It includes detailed components, system requirements, and success criteria for evaluating the encryption environment, emphasizing features like automated encryption, pre-boot authentication, and compatibility with different operating systems. Additionally, it provides insights into deploying the software both manually and through corporate deployment mechanisms.