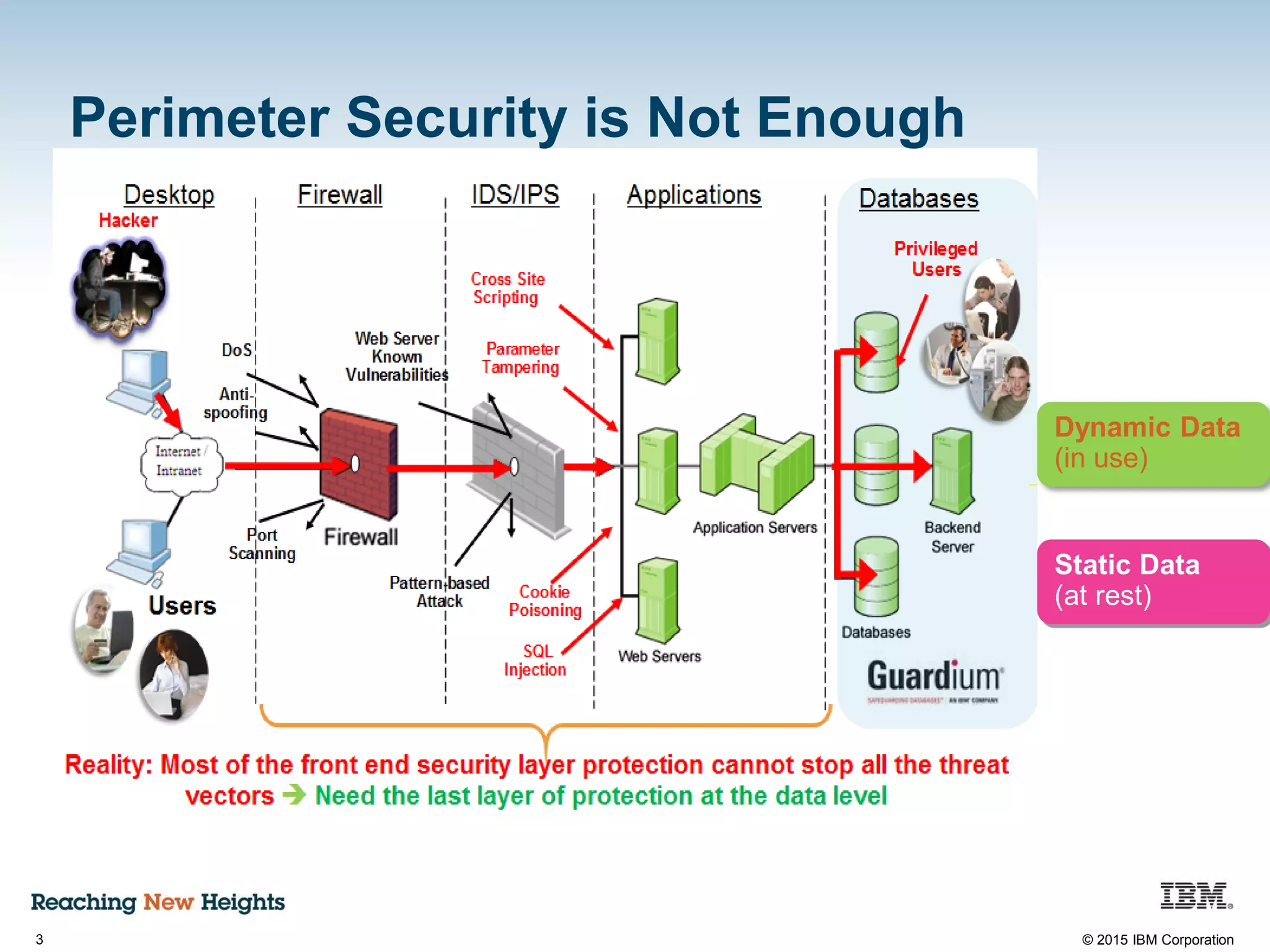
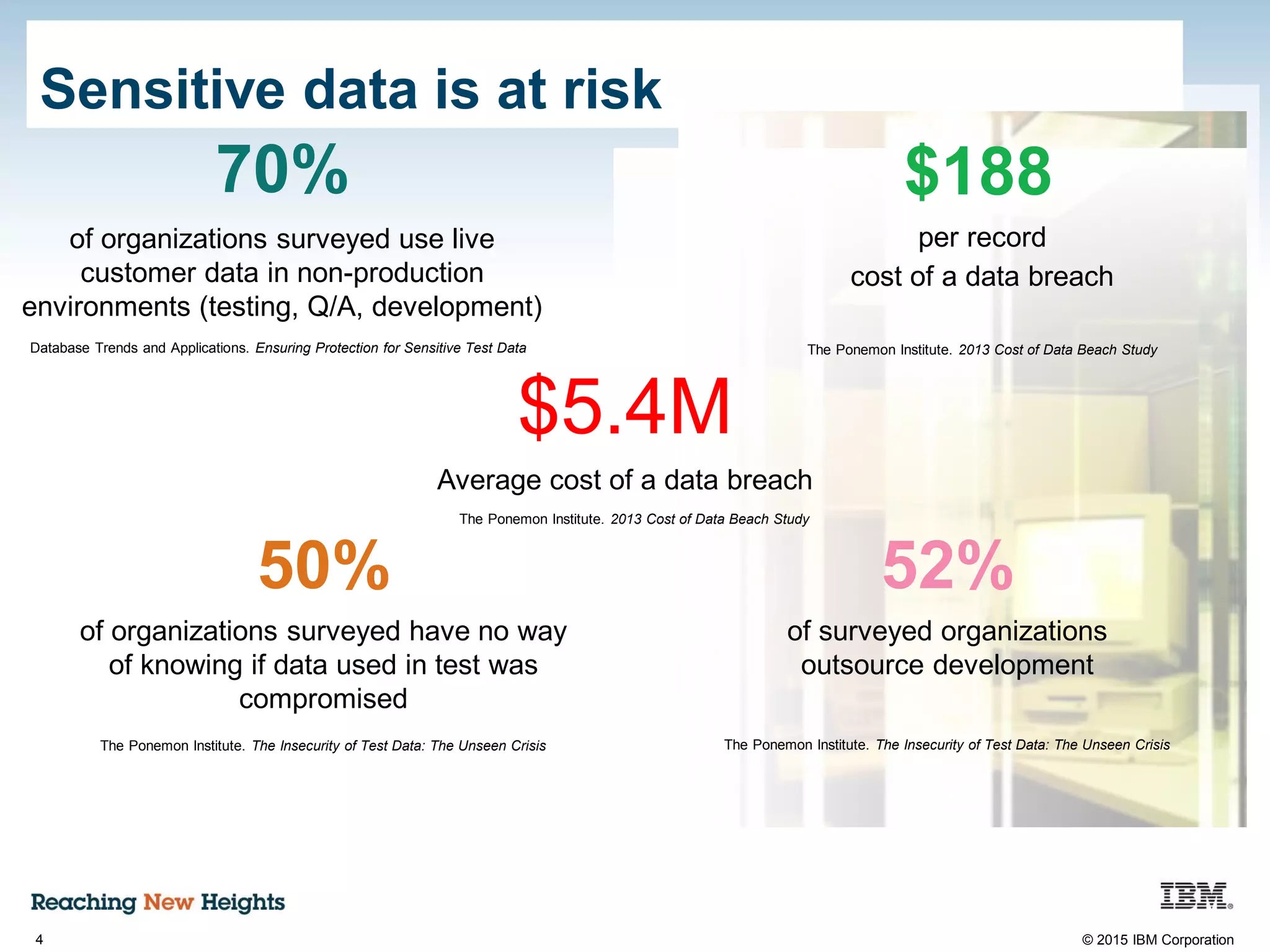
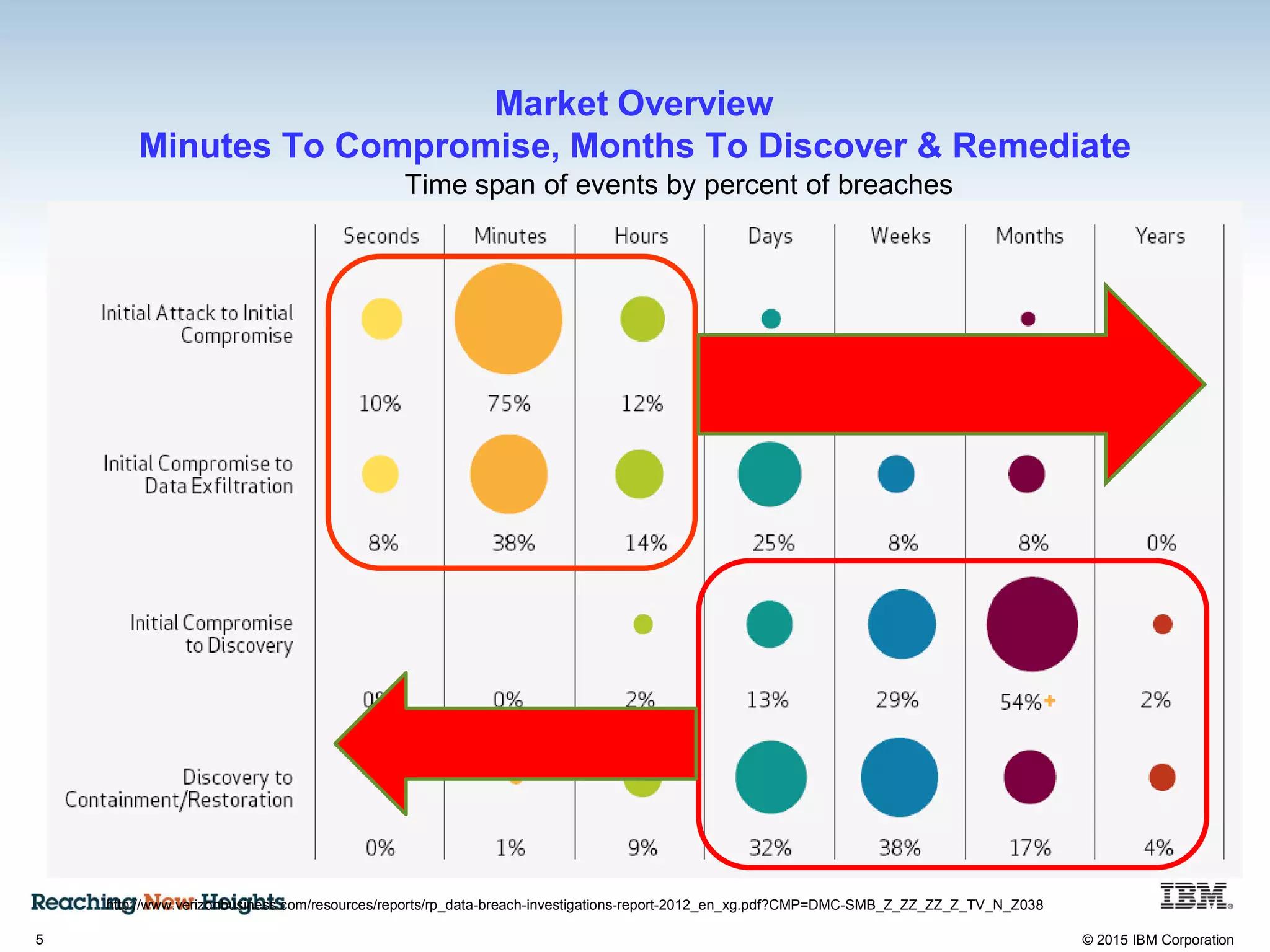
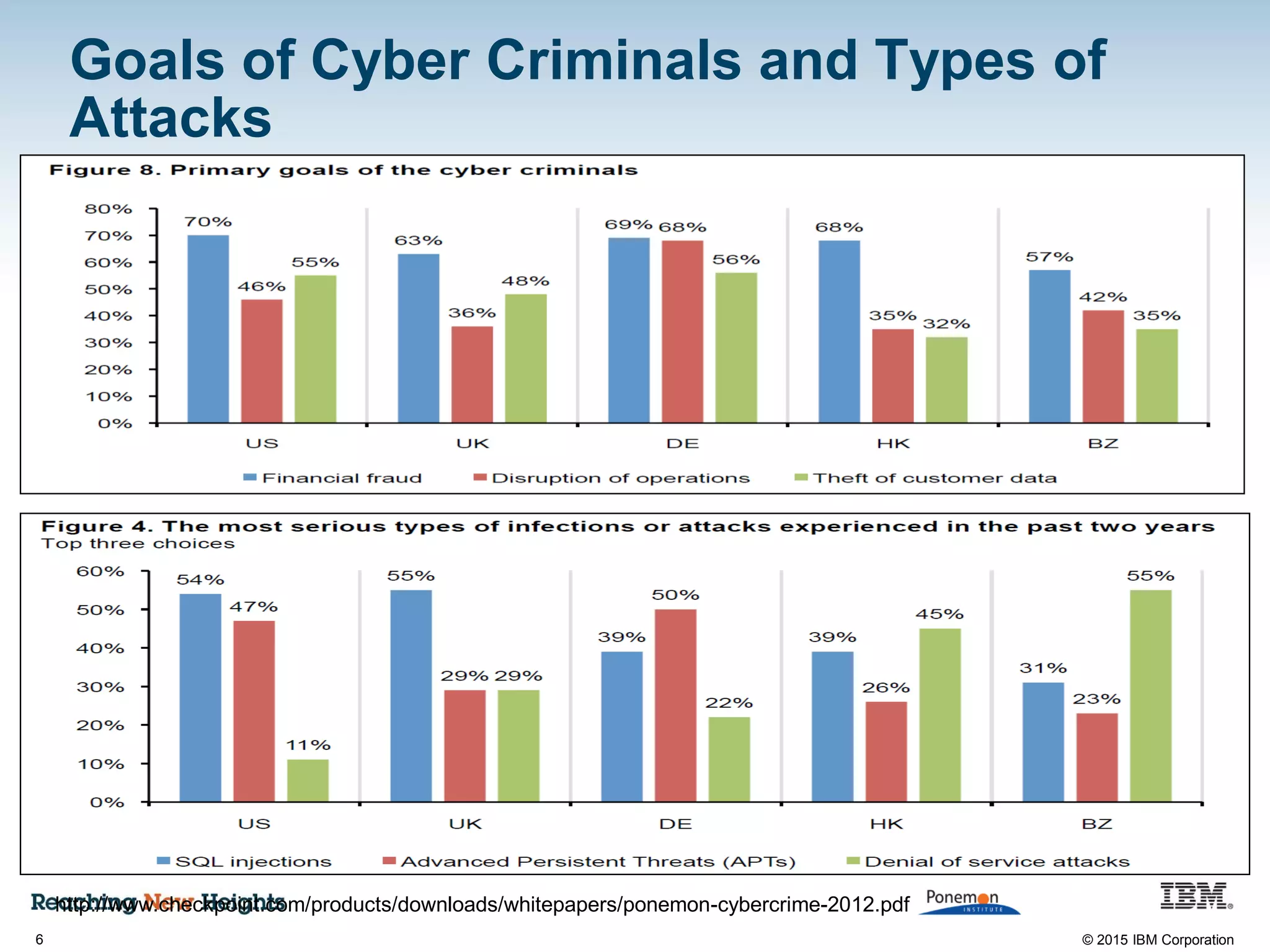
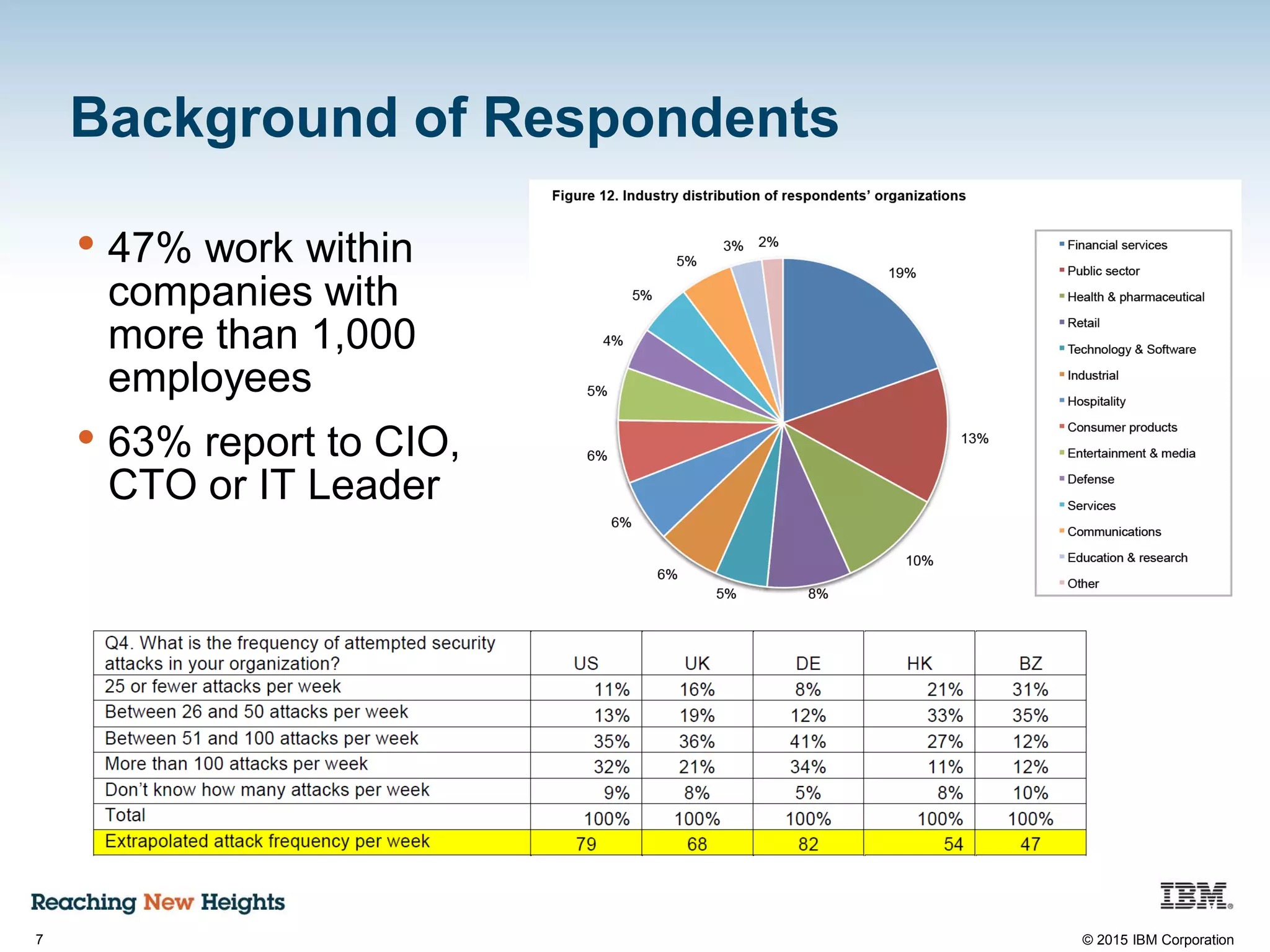
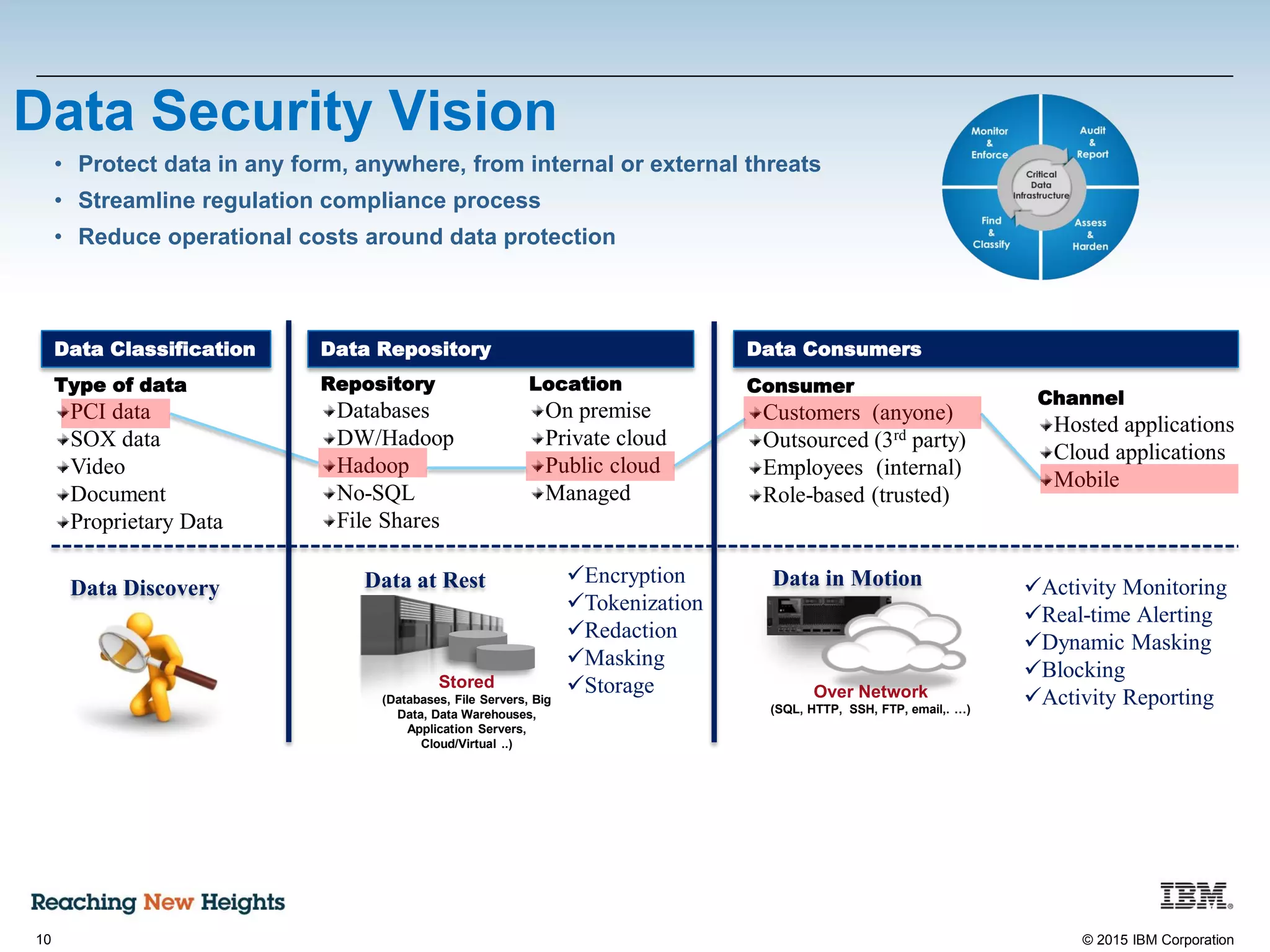
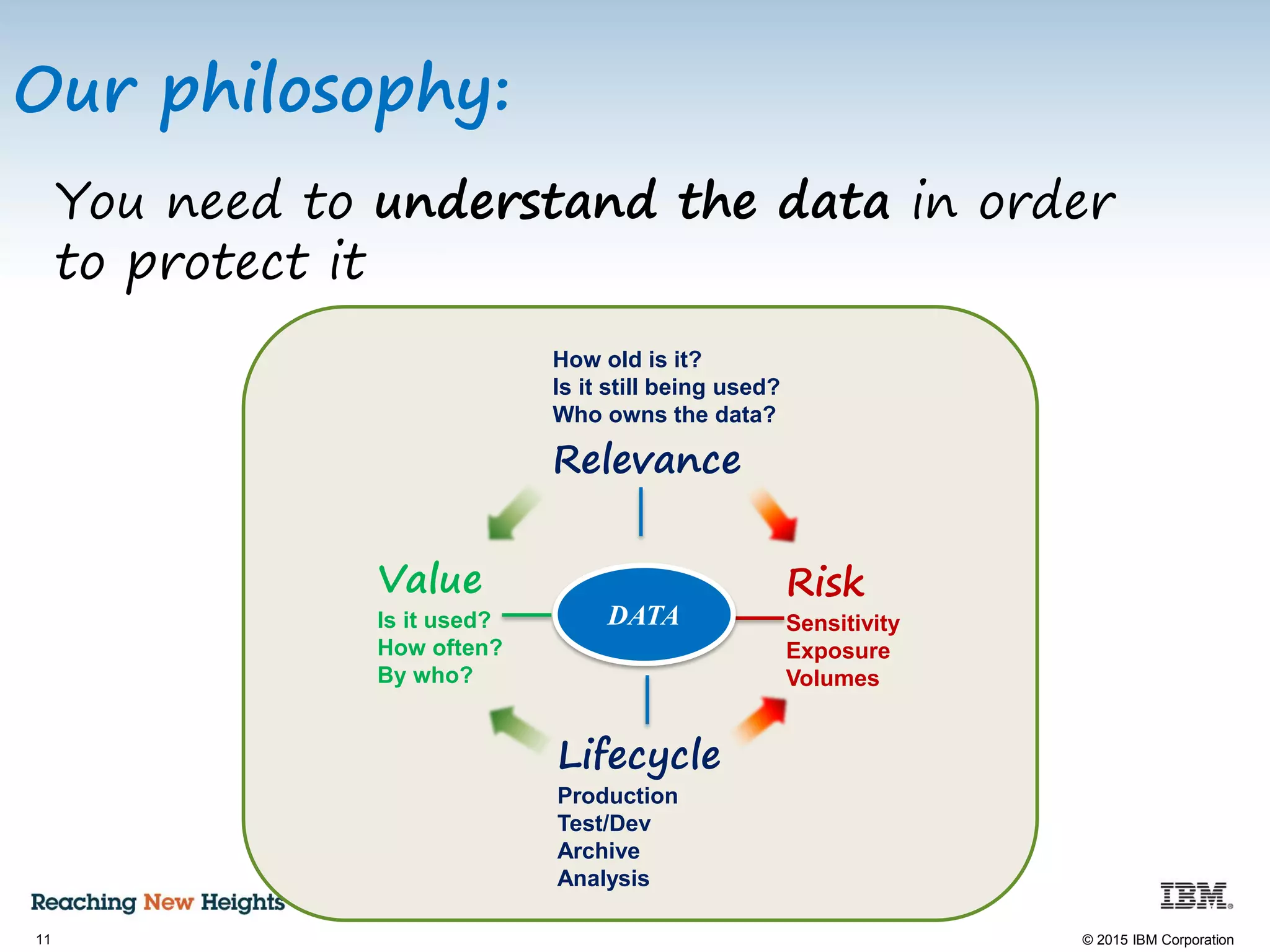
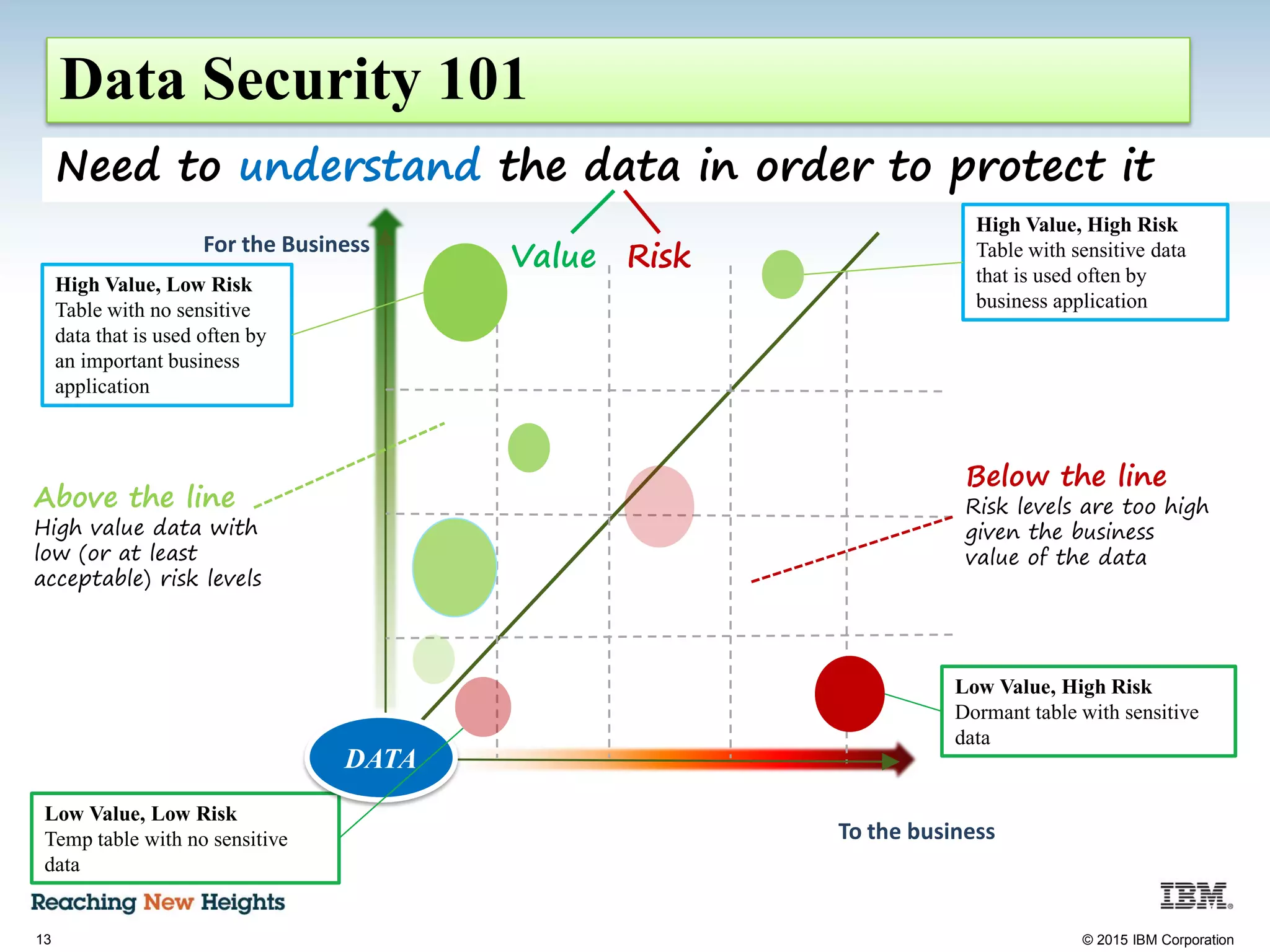
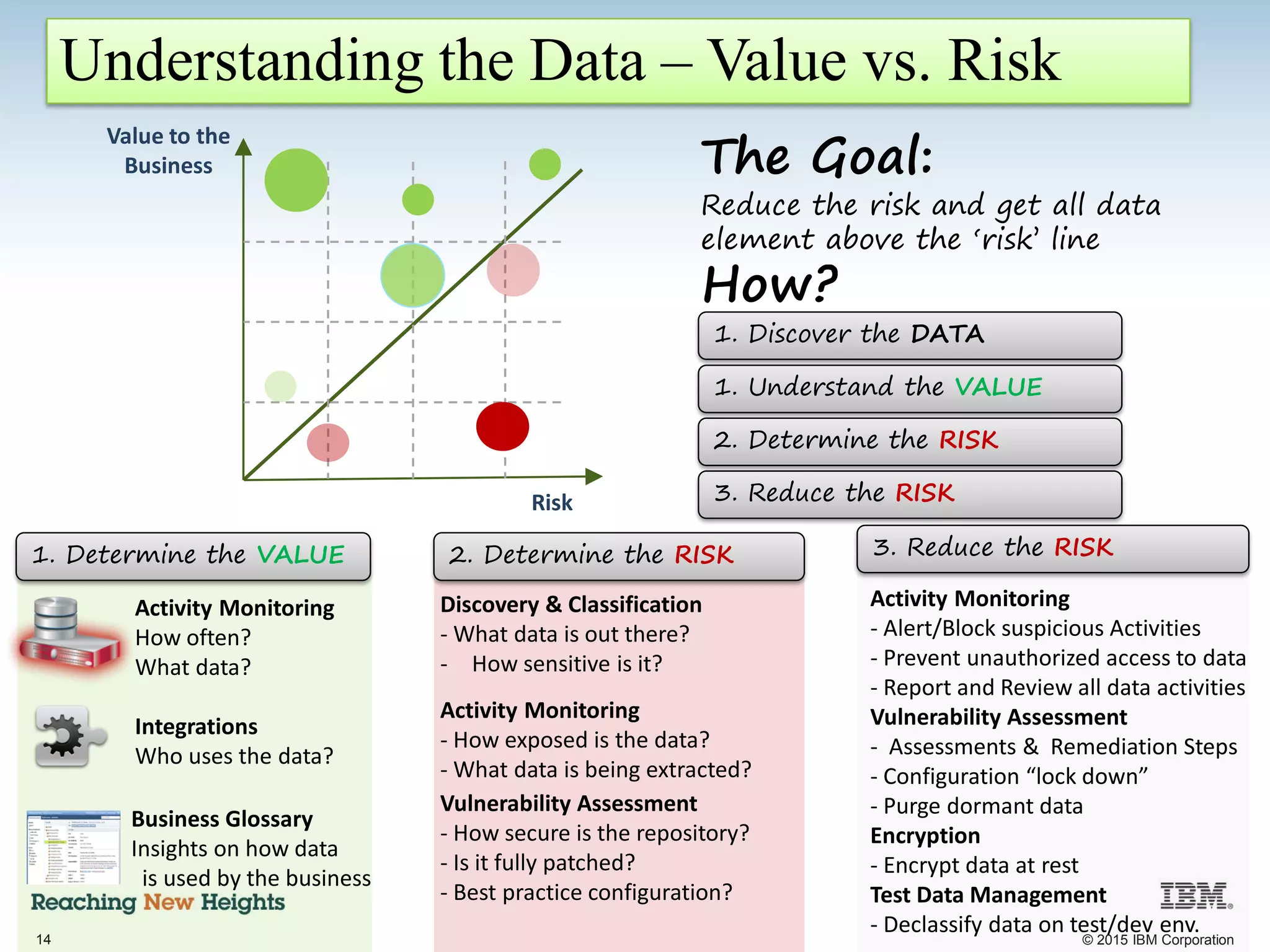
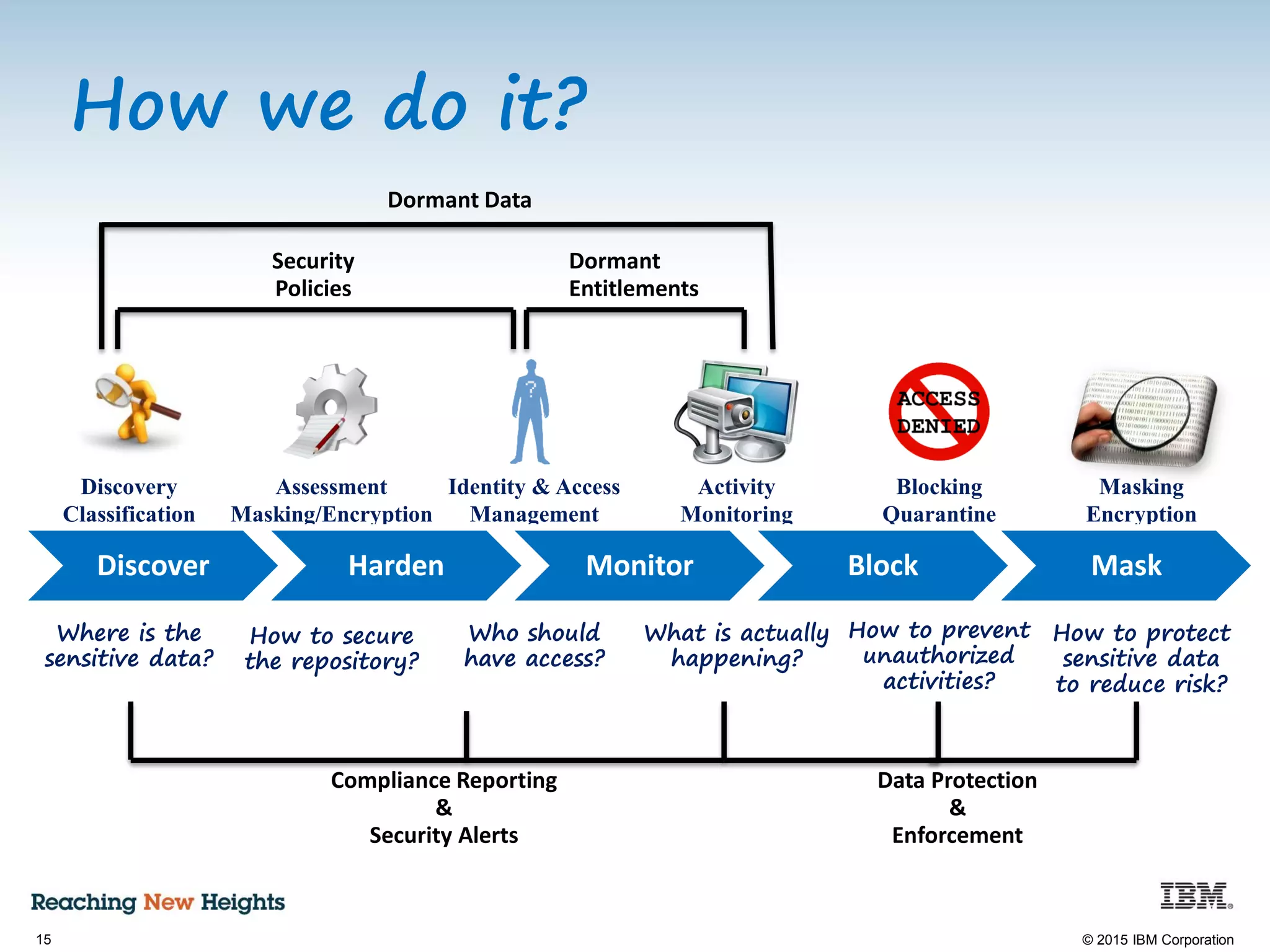
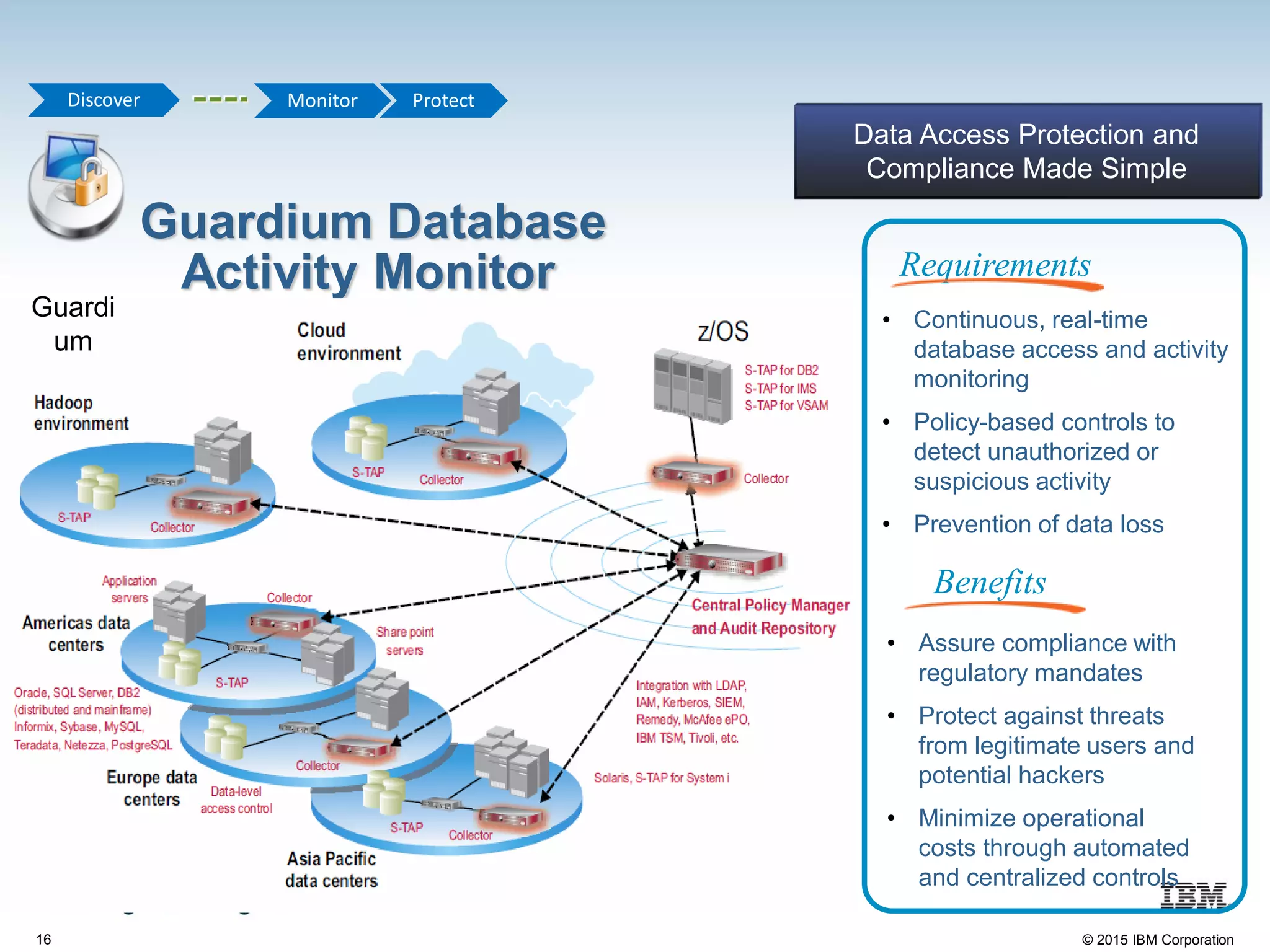
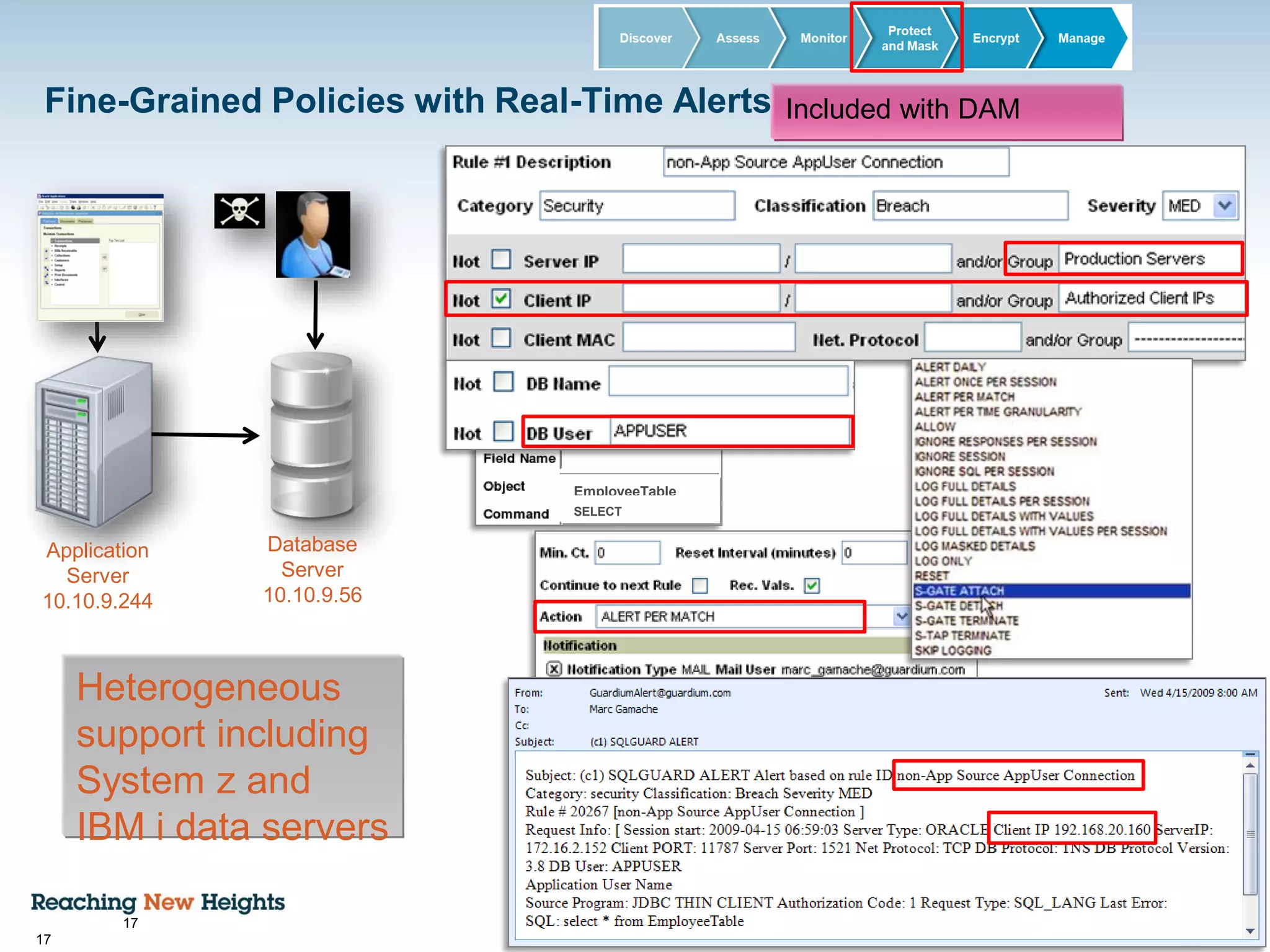
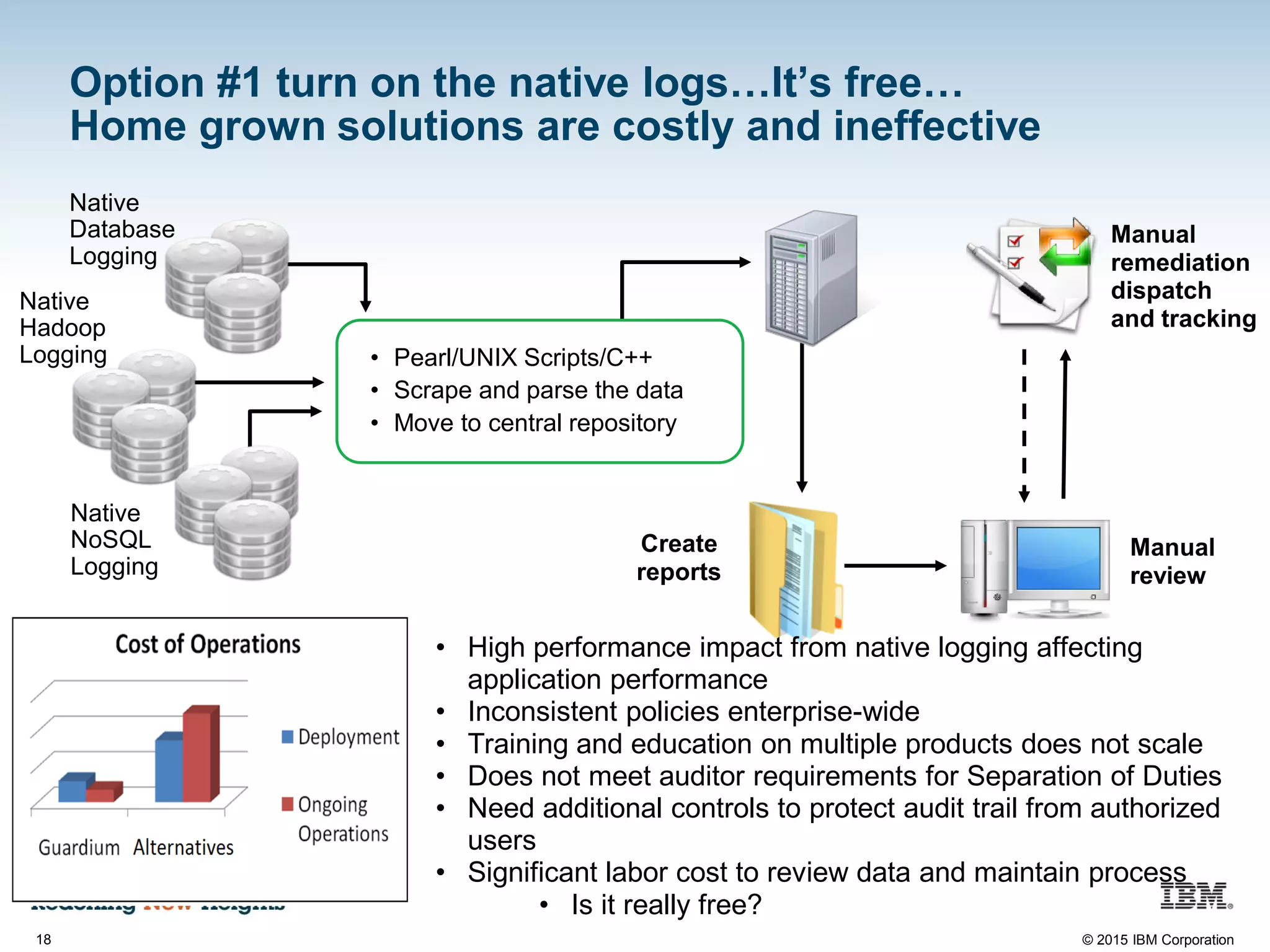
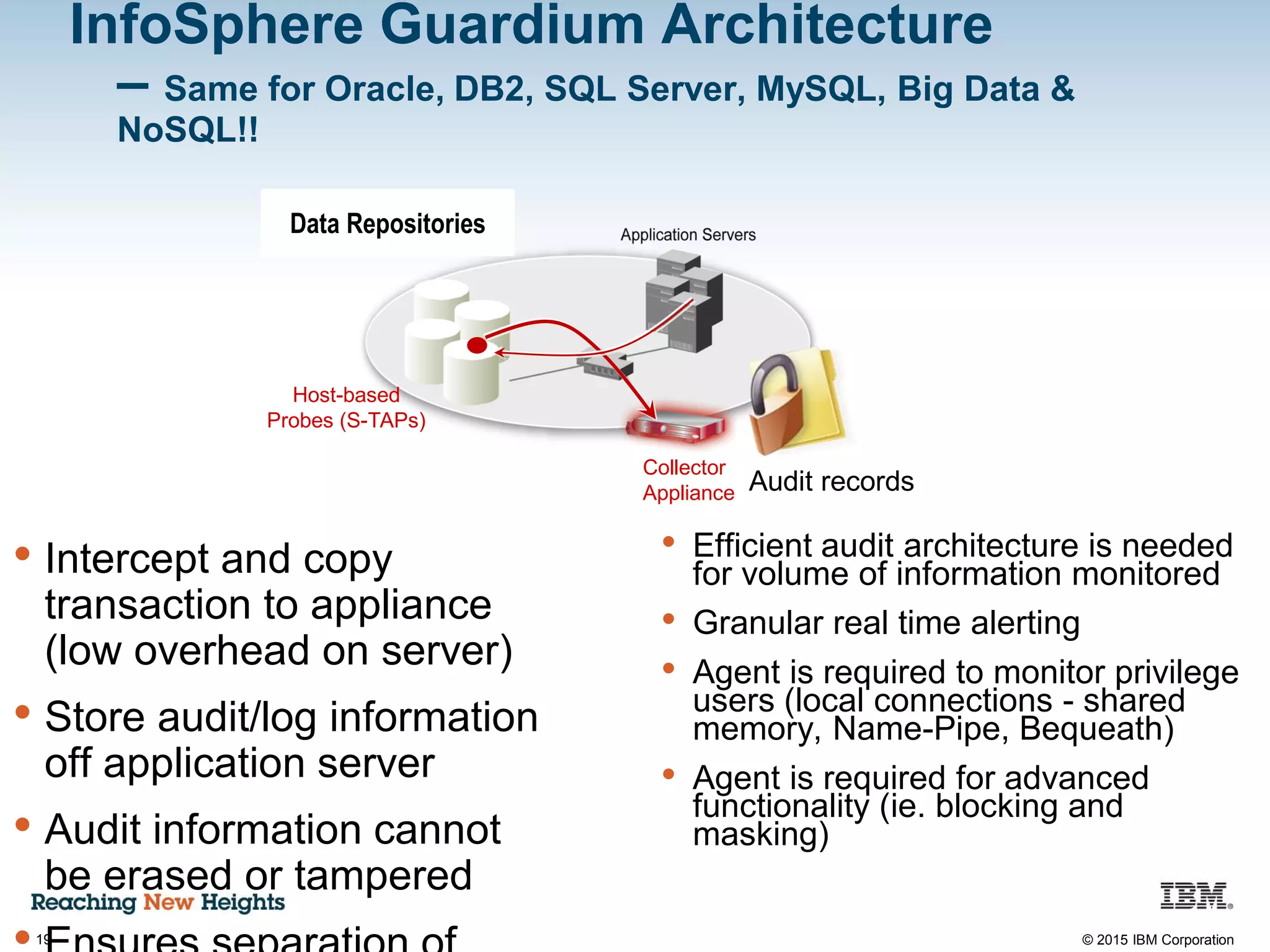
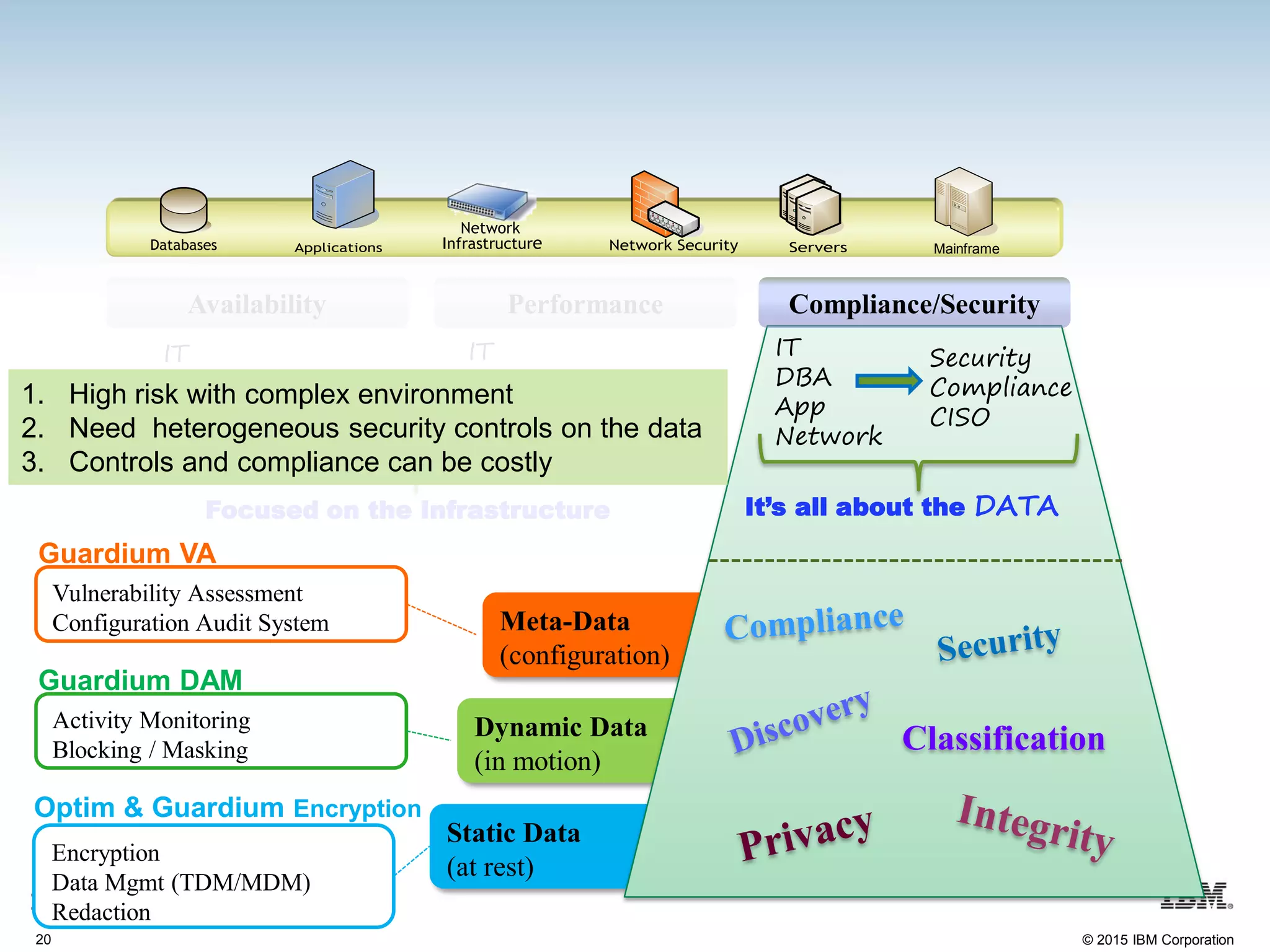
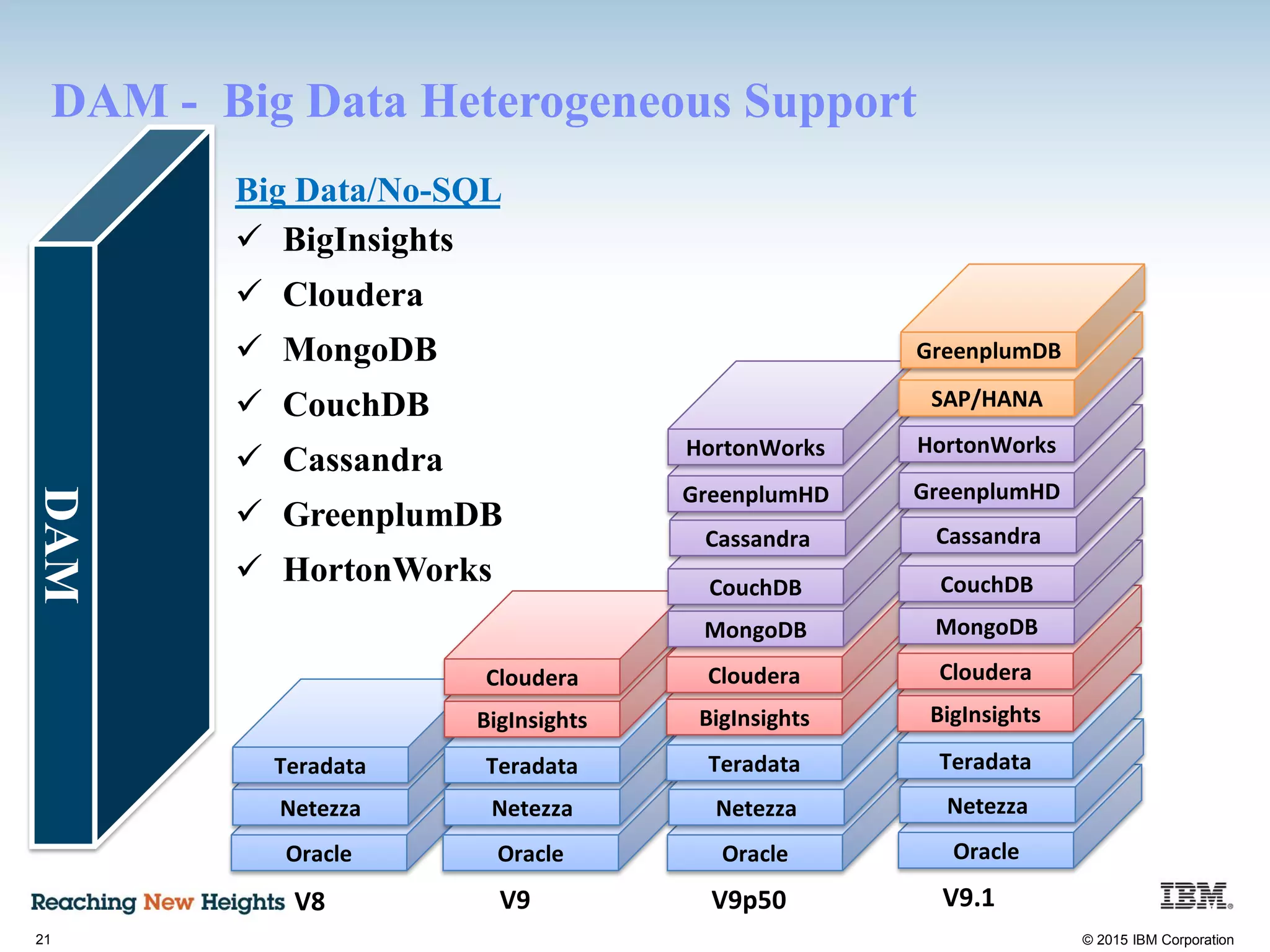
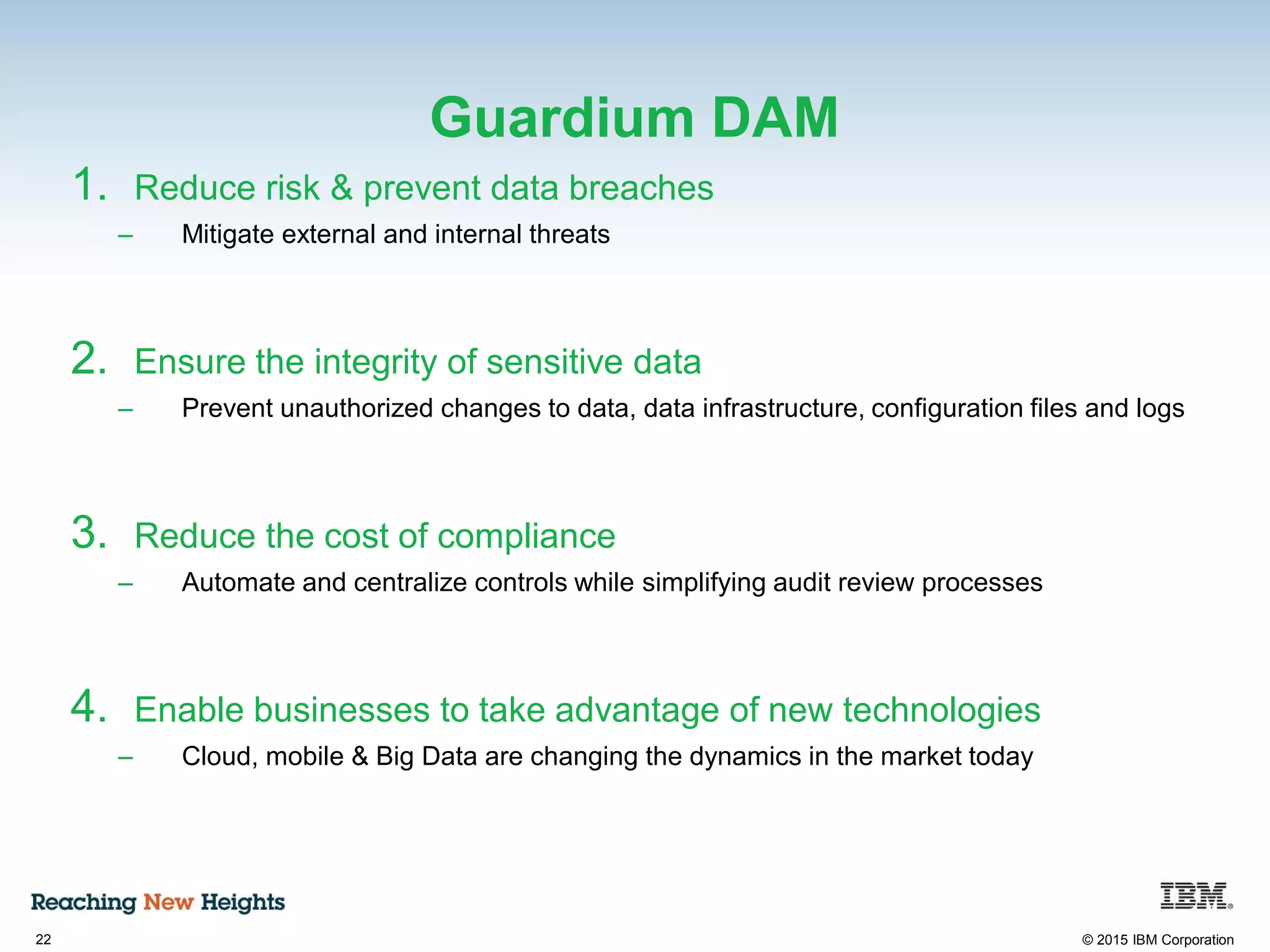
The document discusses the importance of data security, emphasizing the need for robust monitoring and protection, particularly for sensitive data in mobile, cloud, and big data environments. It highlights that a significant percentage of data breaches are preventable through proper controls and that IBM's Guardium offers comprehensive solutions for real-time database monitoring and compliance. Key benefits of Guardium include its non-invasive nature, heterogeneous support across platforms, and cost-effectiveness in automating compliance processes.