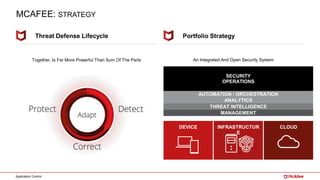
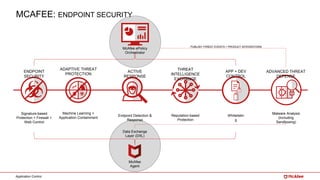
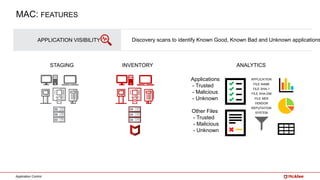
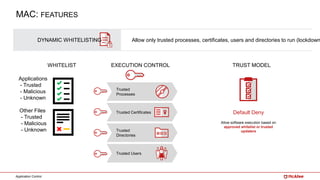
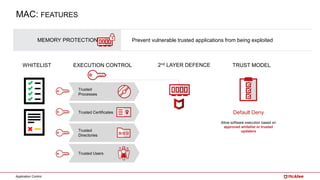
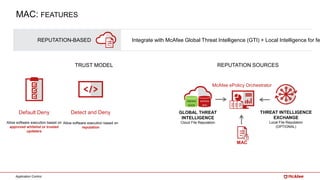
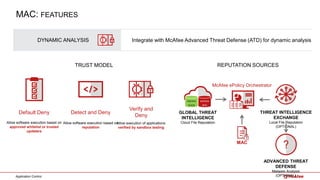
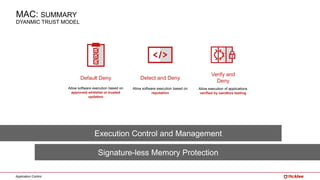
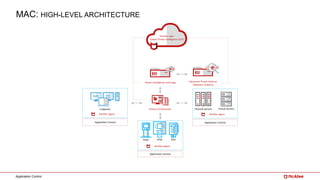
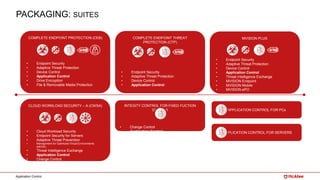
The document outlines McAfee's application control and managed whitelisting strategies, highlighting the company's longstanding presence in the security software industry and its offerings across various sectors. It details the features of McAfee's application control, including endpoint security, dynamic whitelisting, and integration with threat intelligence for enhanced protection against malware and other threats. The document also discusses licensing and packaging options for their solutions, ultimately presenting an integrated approach to security management.