This document provides an introduction and overview of computer security and privacy. It discusses how computer security aims to protect information from unauthorized access while allowing intended use. Privacy involves protecting personal information. The document then covers physical security, network security, basic security objectives of confidentiality, integrity and availability. It provides examples of security policies, mechanisms, and goals of prevention, detection and recovery. Finally, it discusses the brief history of computer security and privacy and covers early efforts to address these issues through standards, legislation and security controls.

















![25
“The most robustly secured computer that is left
sitting unattended in an unlocked room is not at all
secure !!” [Chuck Easttom]
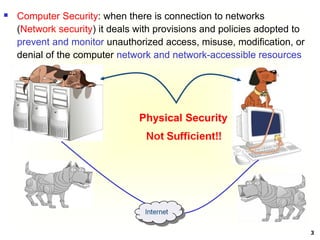
Physical security is the use of physical controls to protect
premises, site, facility, building or other physical asset of an
organization [Lawrence Fennelly]
Physical security protects your physical computer facility (your
building, your computer room, your disks and other media)
[Chuck Easttom]
Physical security was overlooked in the past few years by
organizations because of the emphasis placed on improving
cyber security
1.4 Physical Security](https://image.slidesharecdn.com/chapter1-introduction-231018033240-ee7555d5/85/Chapter-1-Introduction-pdf-25-320.jpg)