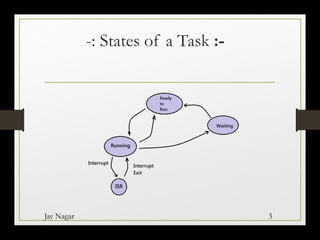
The document discusses the different states a task can be in within an embedded system (ES). It describes three main states:
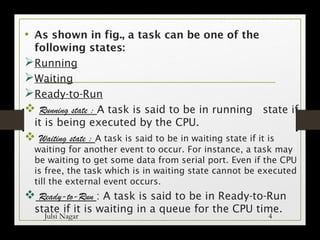
1) Running state: When a task is currently being executed by the CPU.
2) Waiting state: When a task is waiting for an external event such as data from a serial port before it can run.
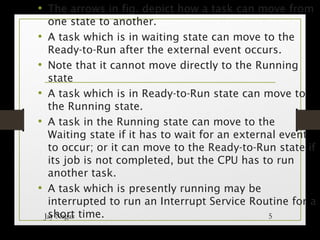
3) Ready-to-Run state: When a task is waiting in a queue to be allocated CPU time. Tasks transition between these states, such as moving from Waiting to Ready-to-Run once the external event occurs. An interrupt service routine can also trigger a task state change. Each task requires a stack to store its local variables and registers during state transitions or