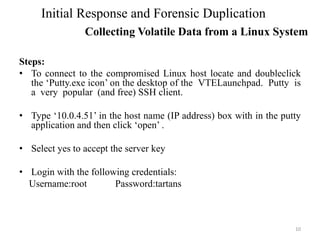
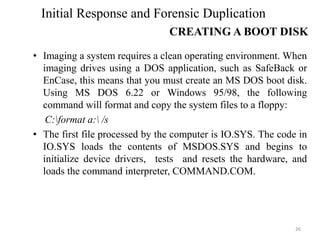
The document outlines the procedures for initial response and forensic duplication in digital investigations, emphasizing the importance of gathering volatile data without altering evidence. It details the necessary tools, methodologies, and steps required for effective data collection from compromised systems, both Windows and Linux. Additionally, it discusses best practices for creating qualified forensic duplicates to ensure admissibility in legal contexts.