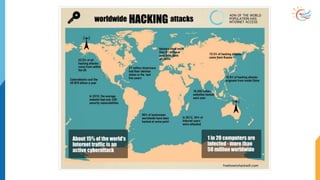
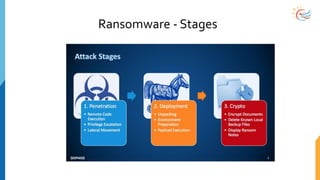
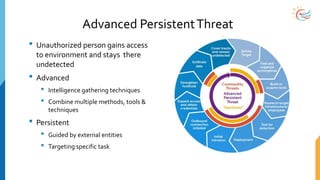
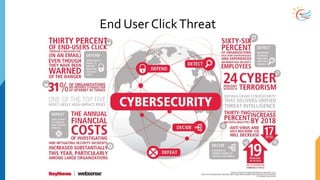
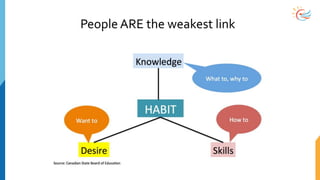
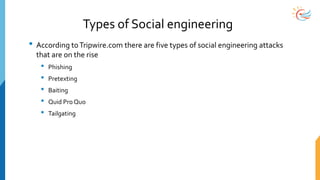
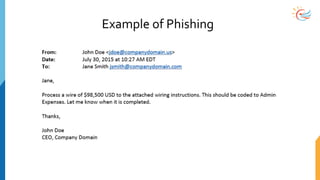
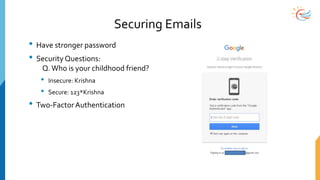
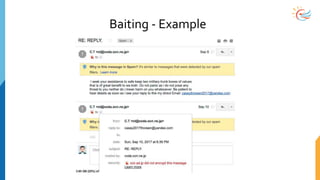
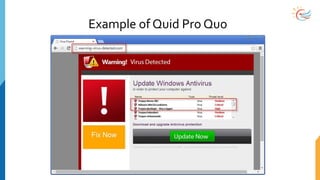
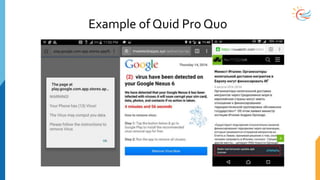
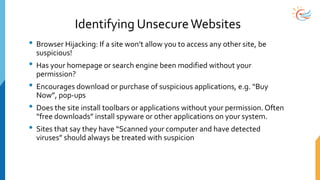
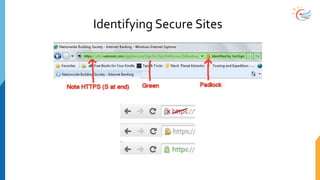
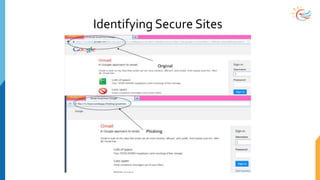
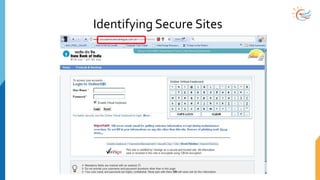
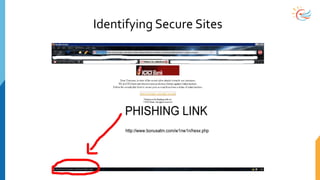
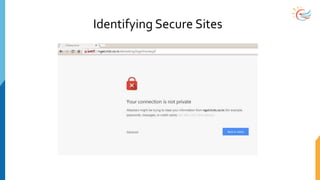
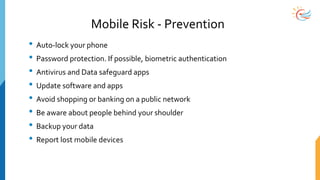
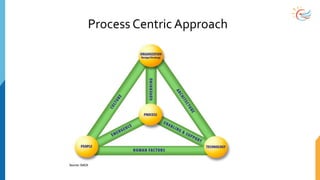
This document provides a comprehensive overview of cybersecurity awareness for executives and non-IT professionals, covering the landscape of cybercrime, types of threats, and measures of protection. It outlines the importance of cyber security practices and training, as well as the legal framework governing cyber activities in India. Additionally, it highlights common cyber threats, social engineering tactics, prevention strategies, and the critical role of human behavior in maintaining cybersecurity.