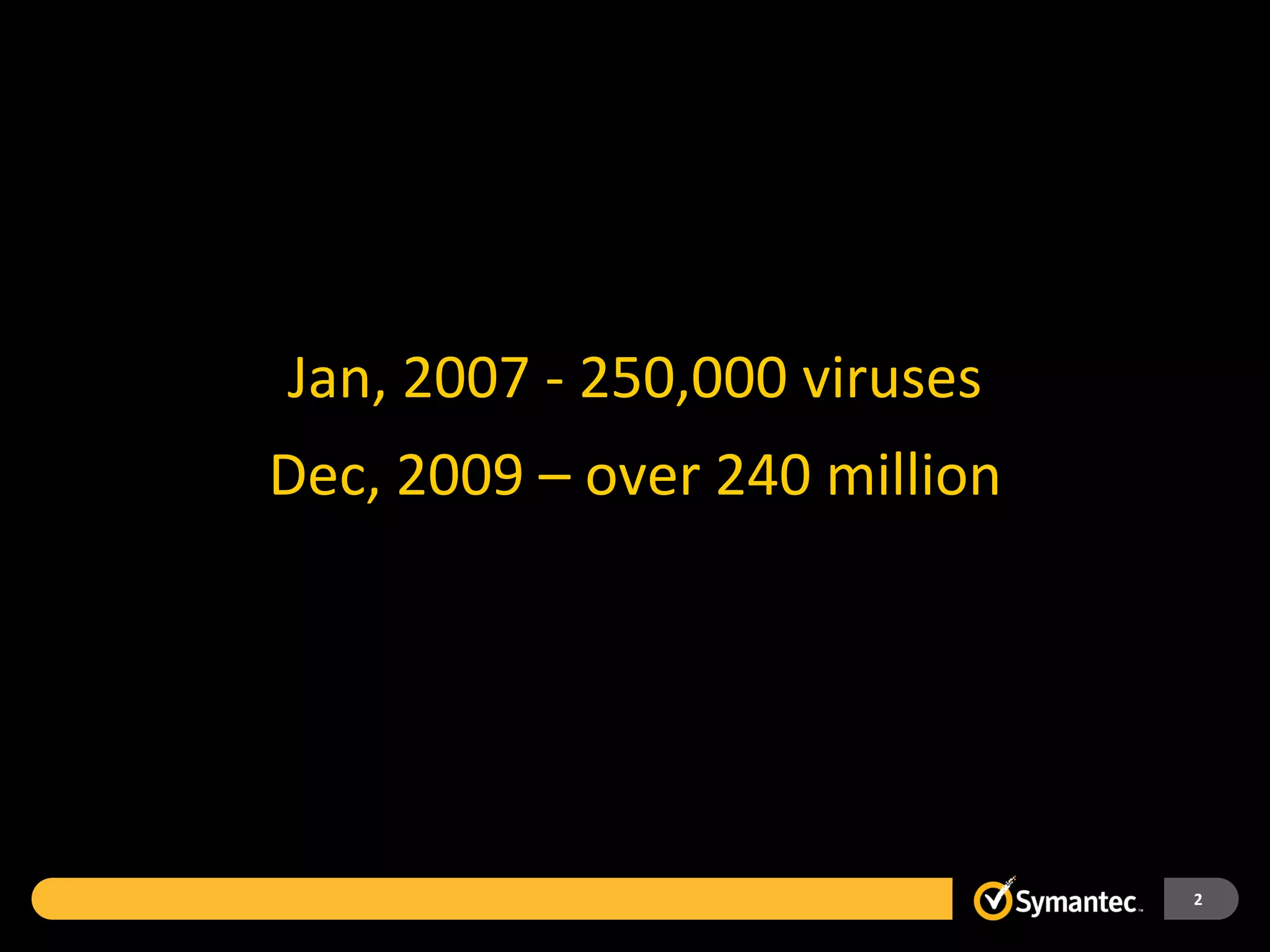
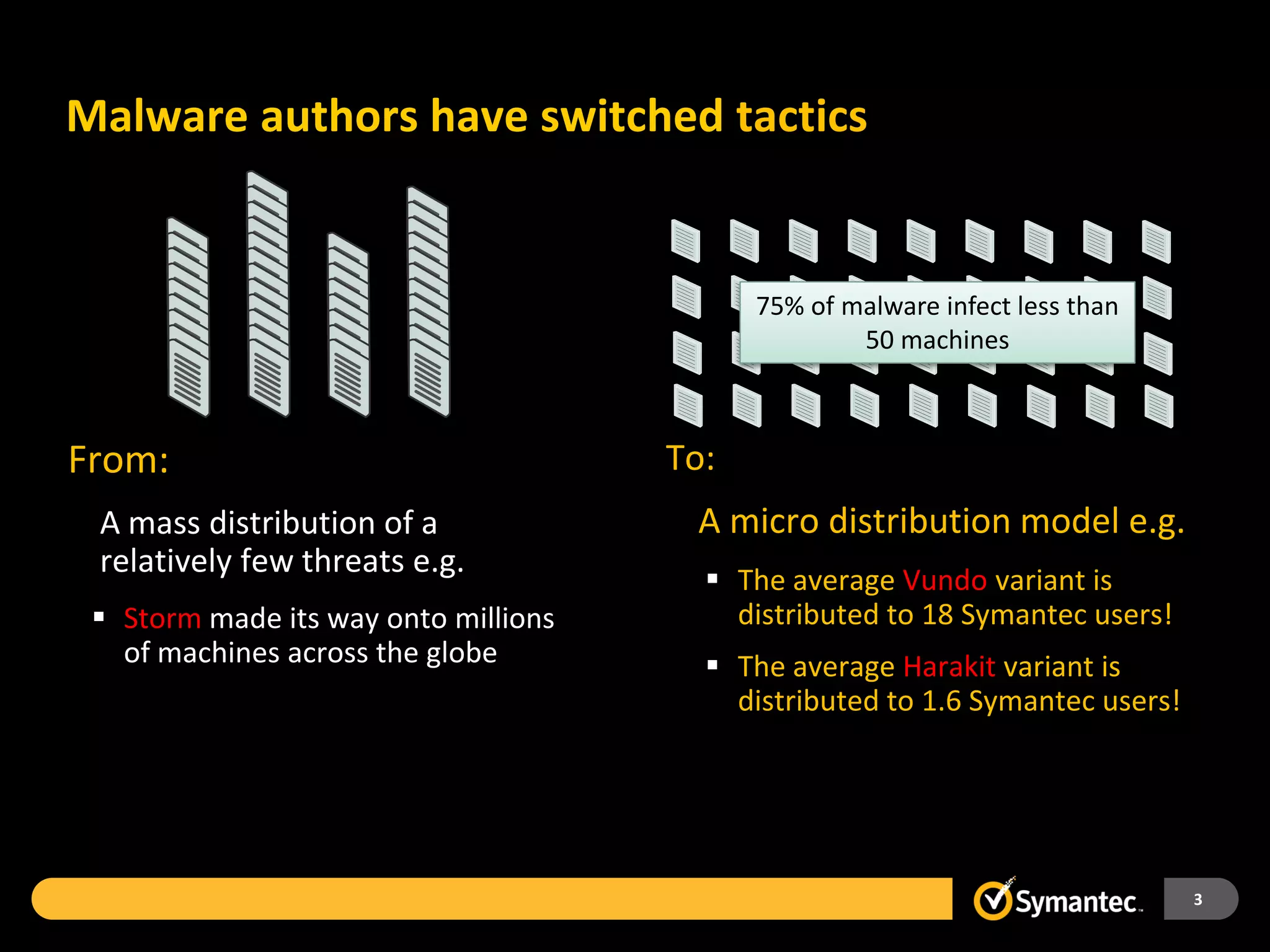
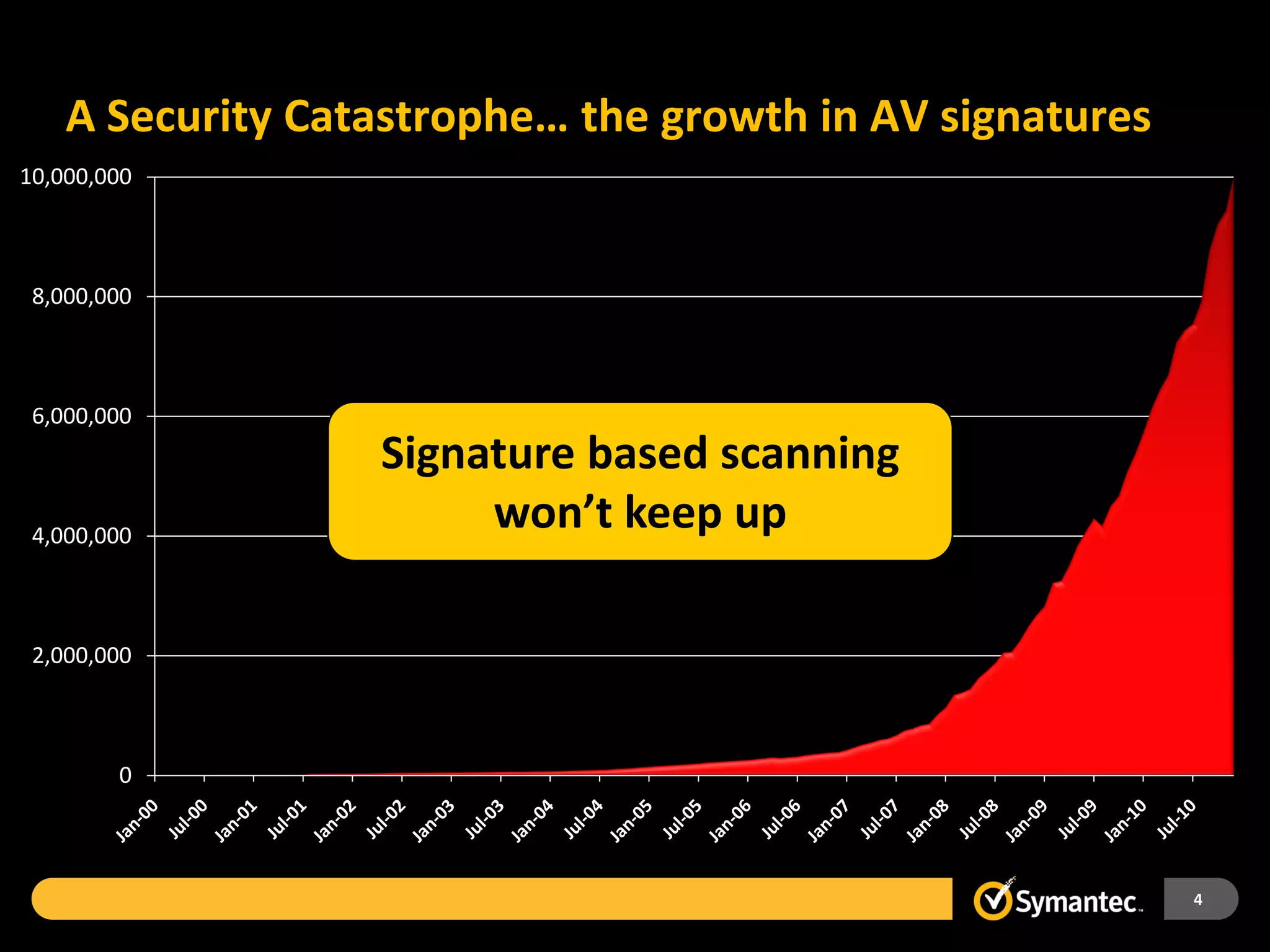
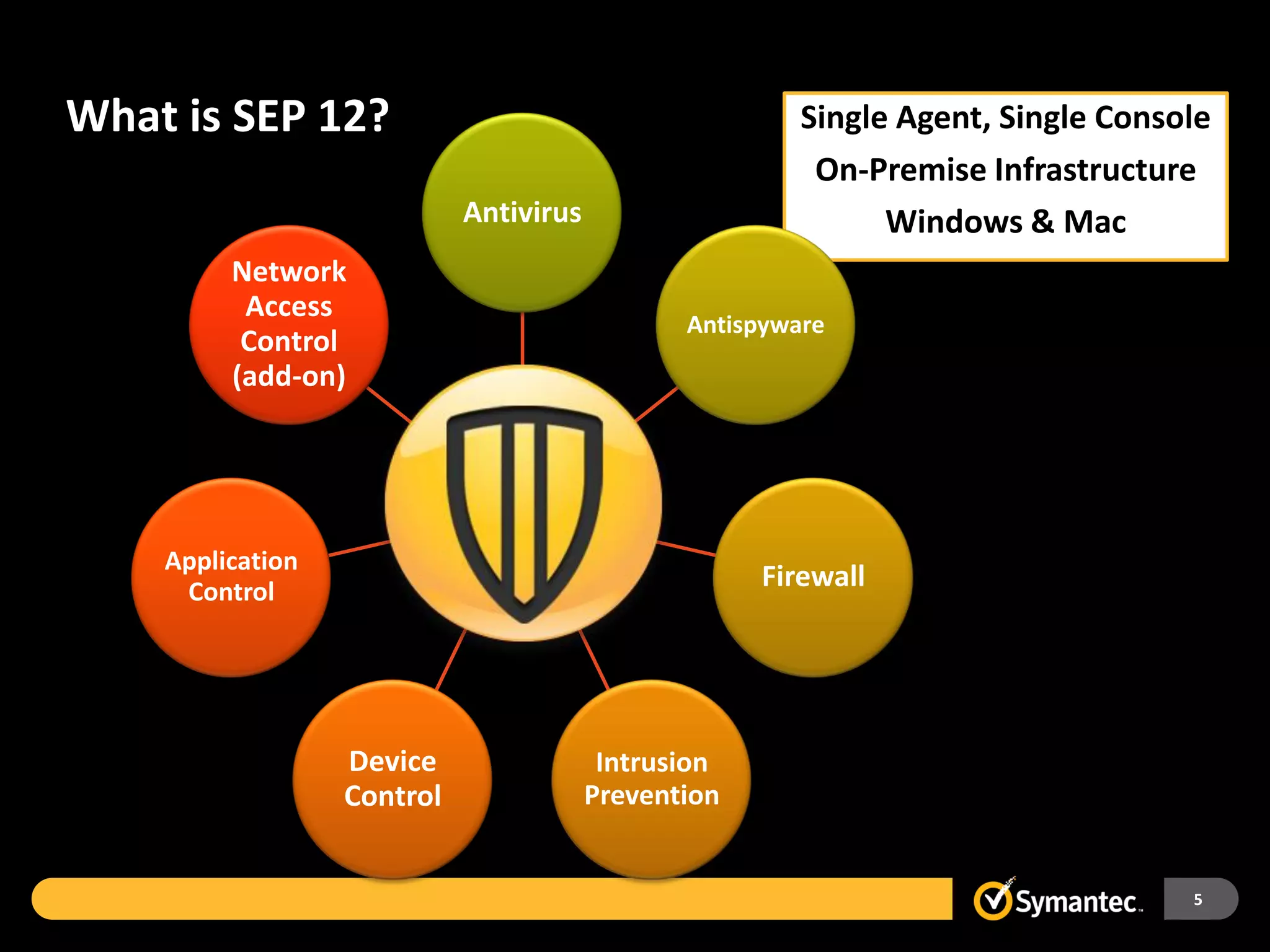
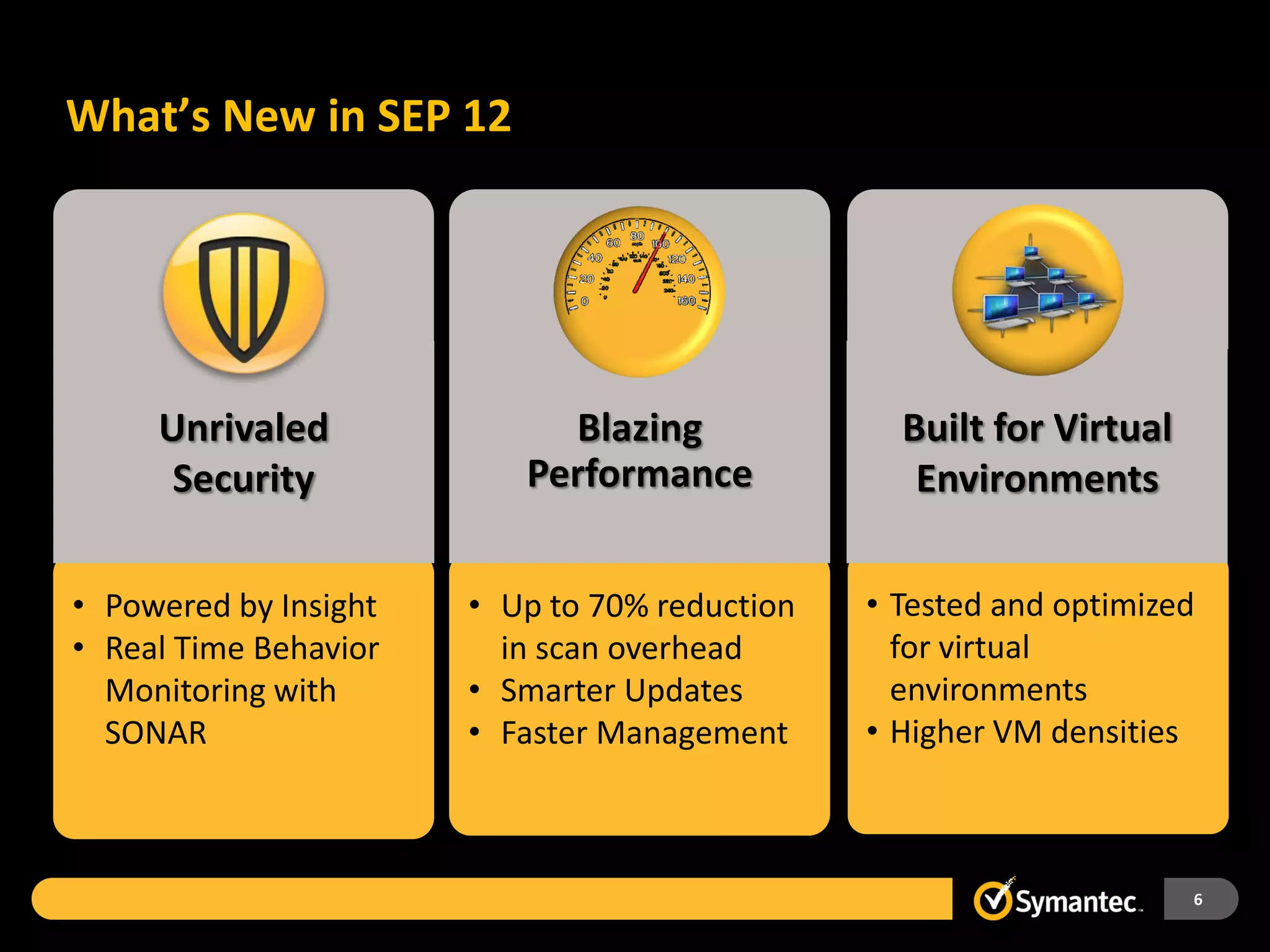
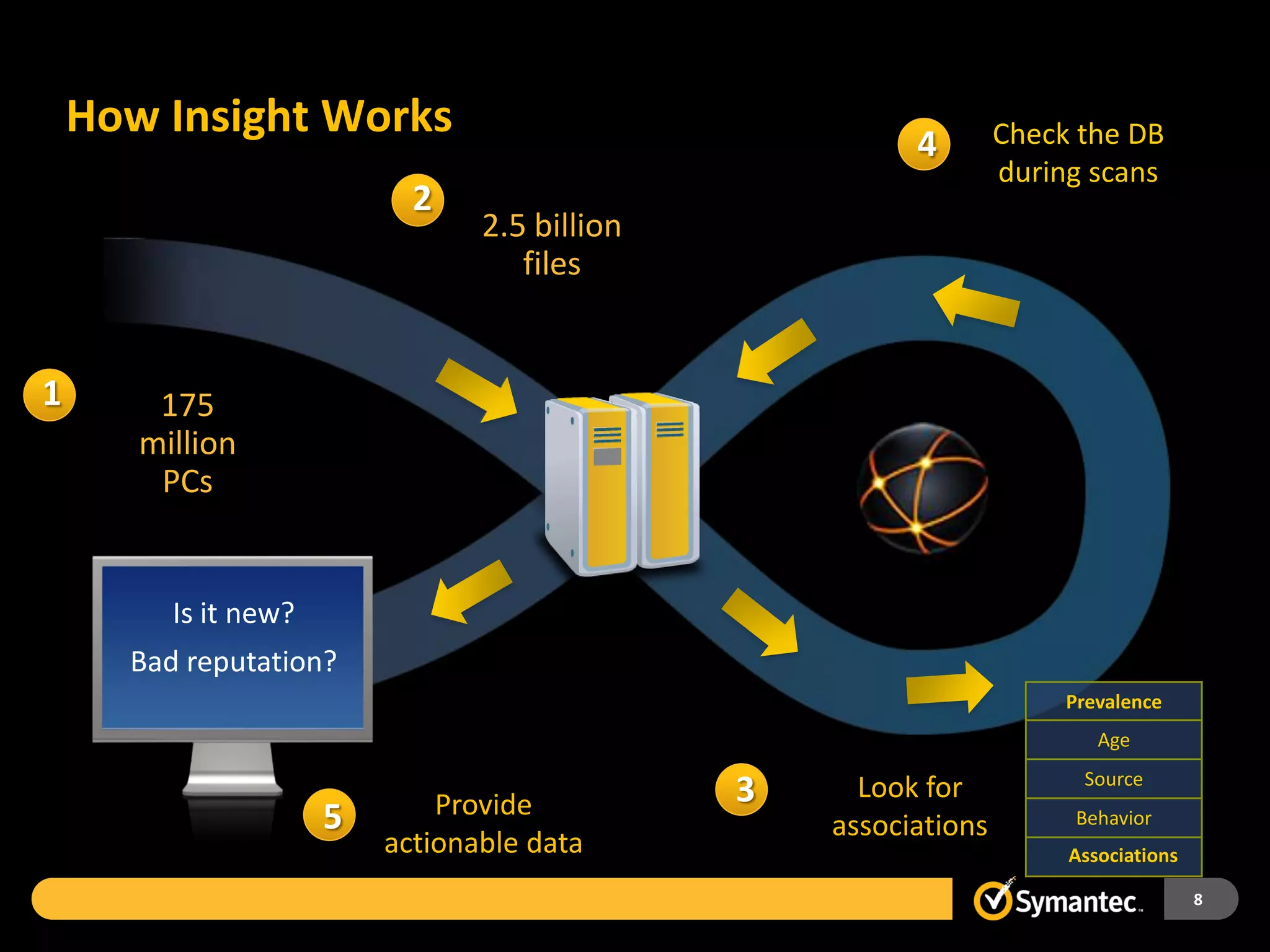
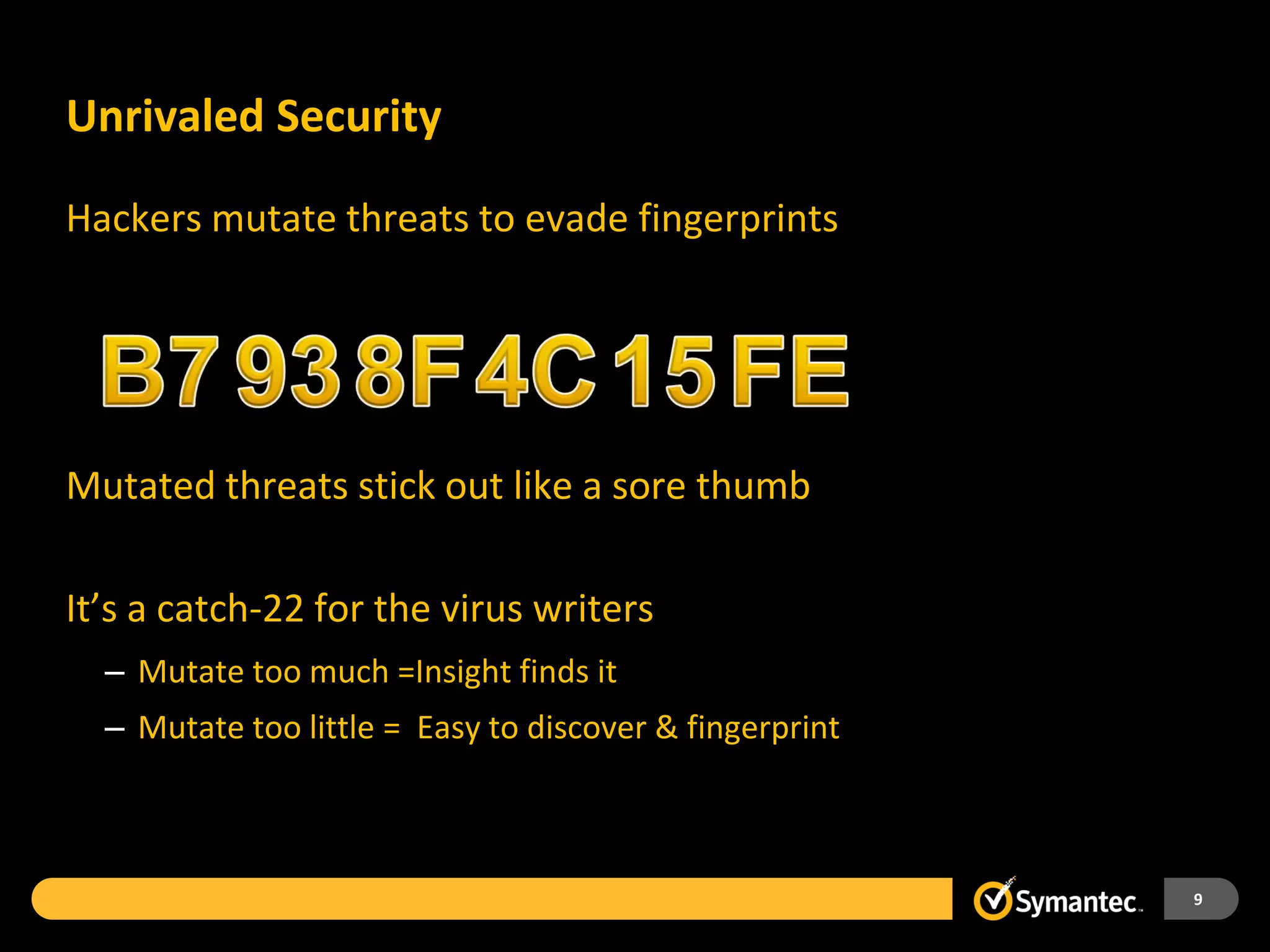
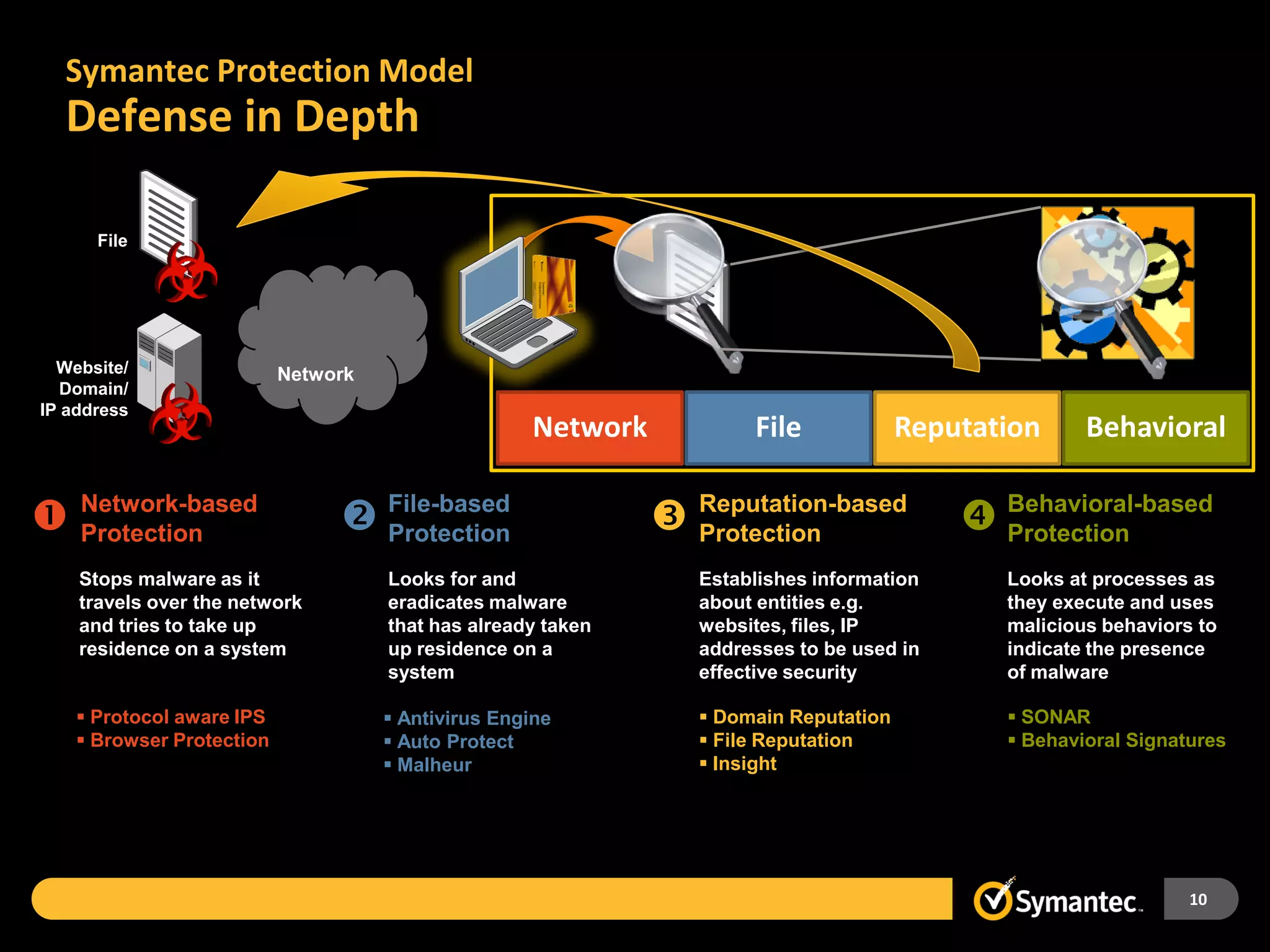
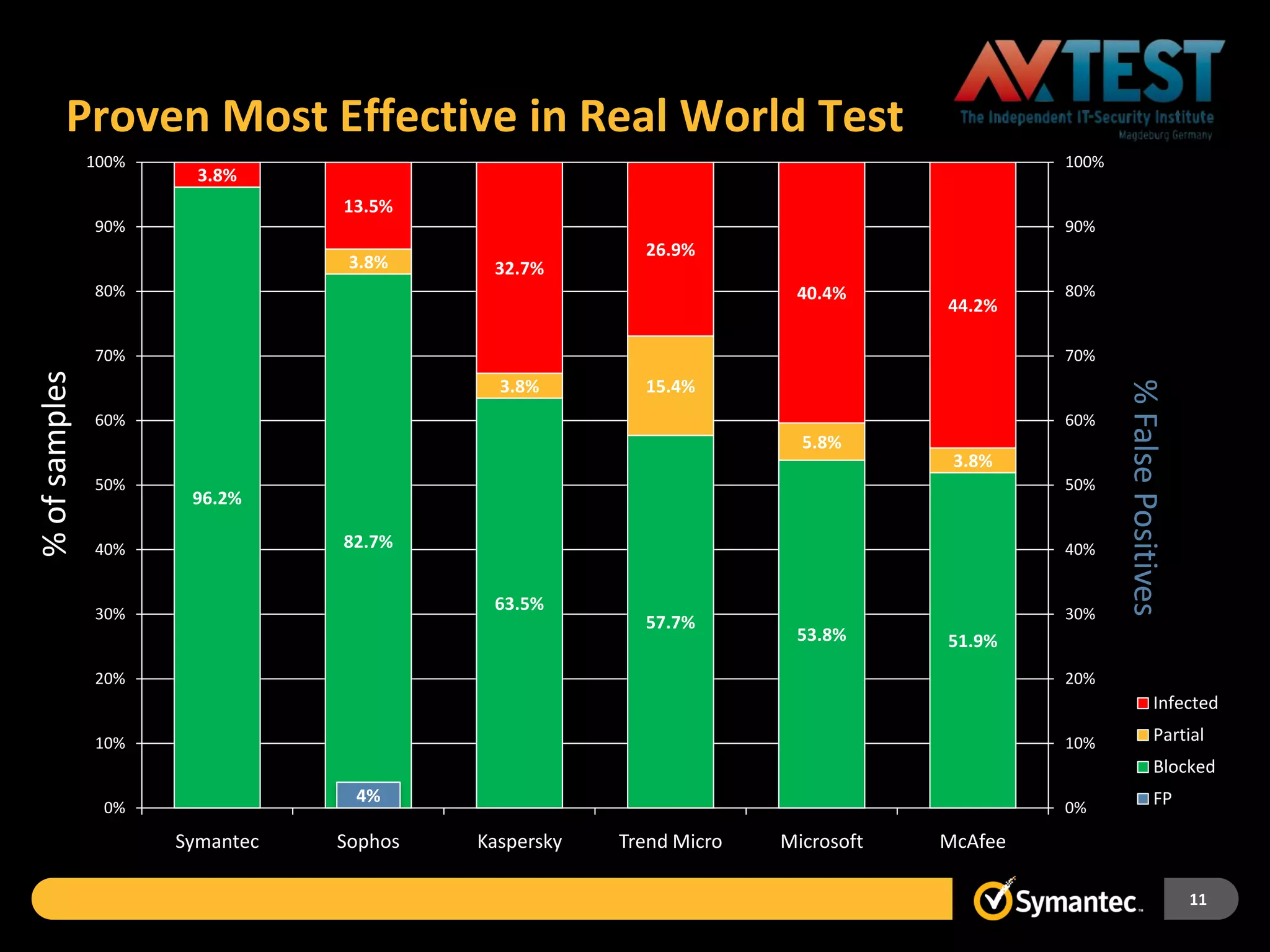
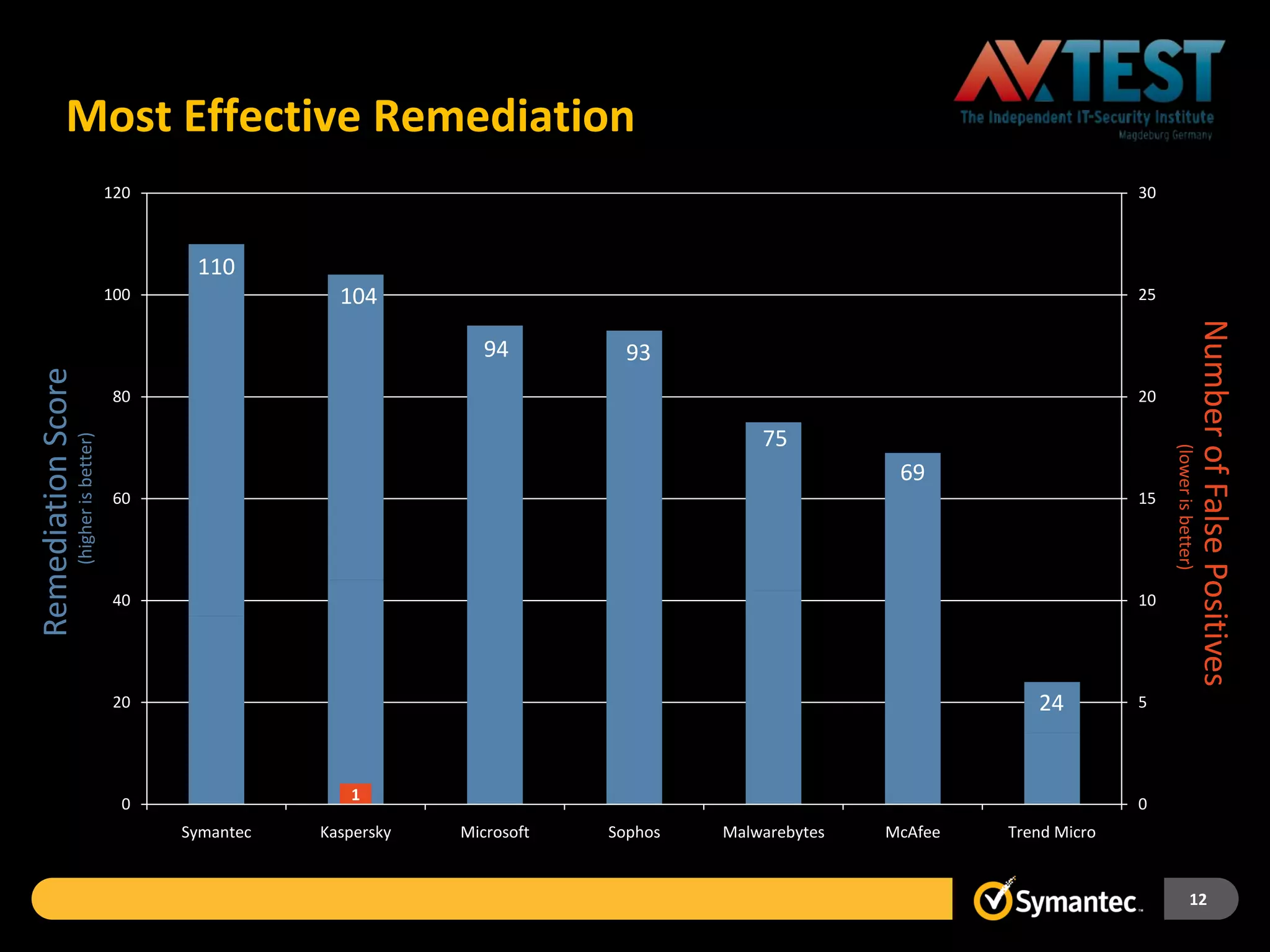
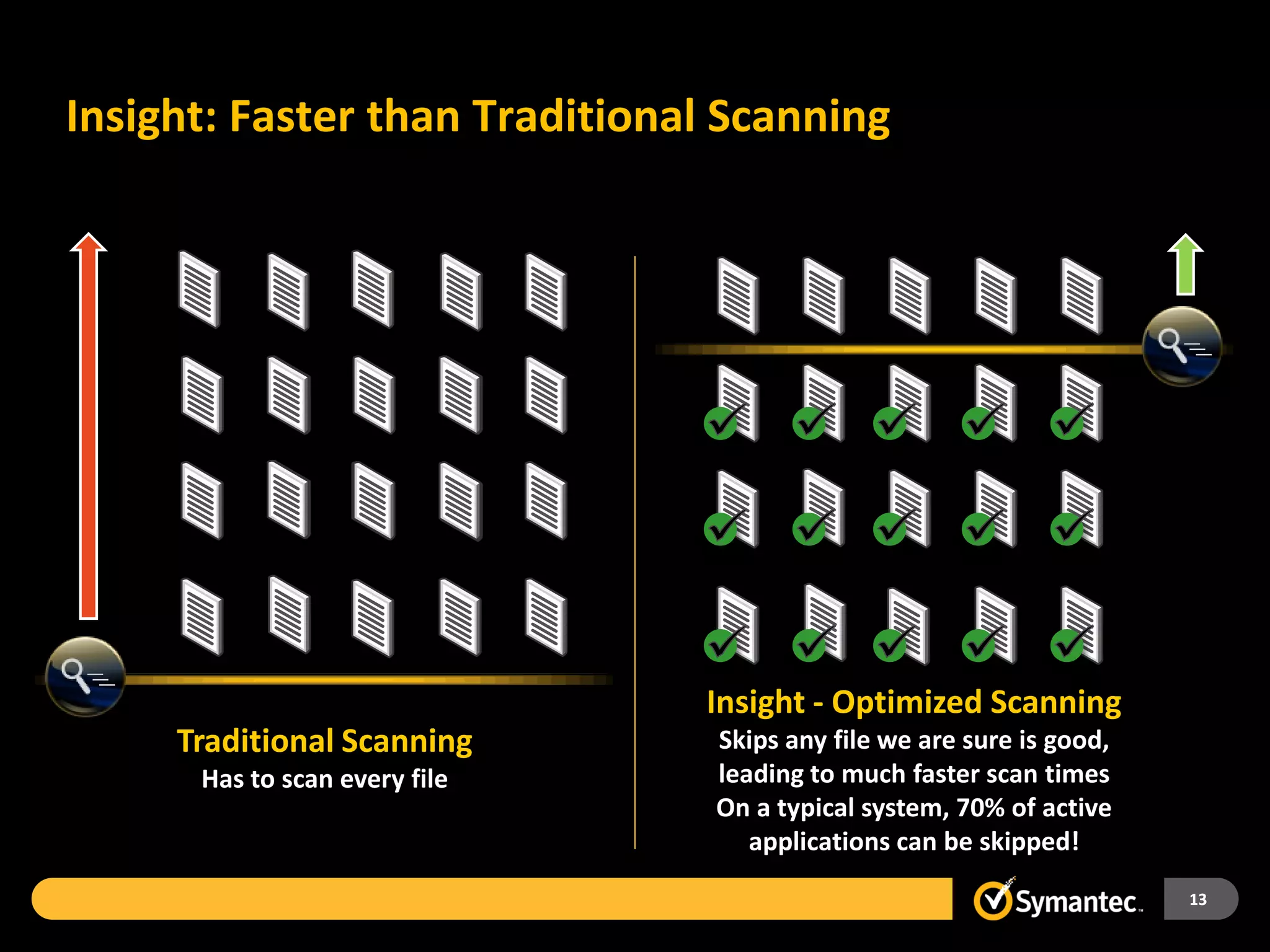
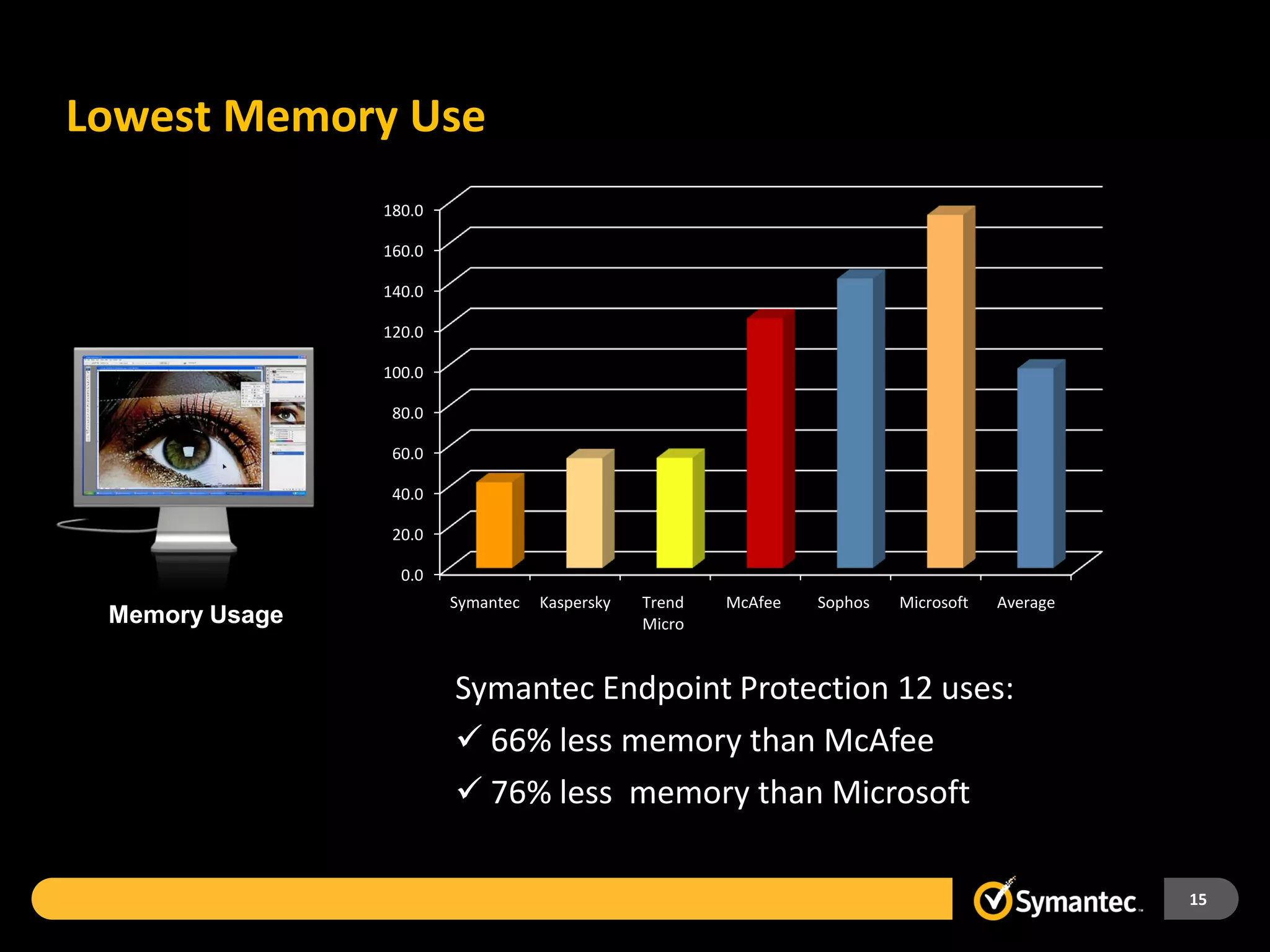
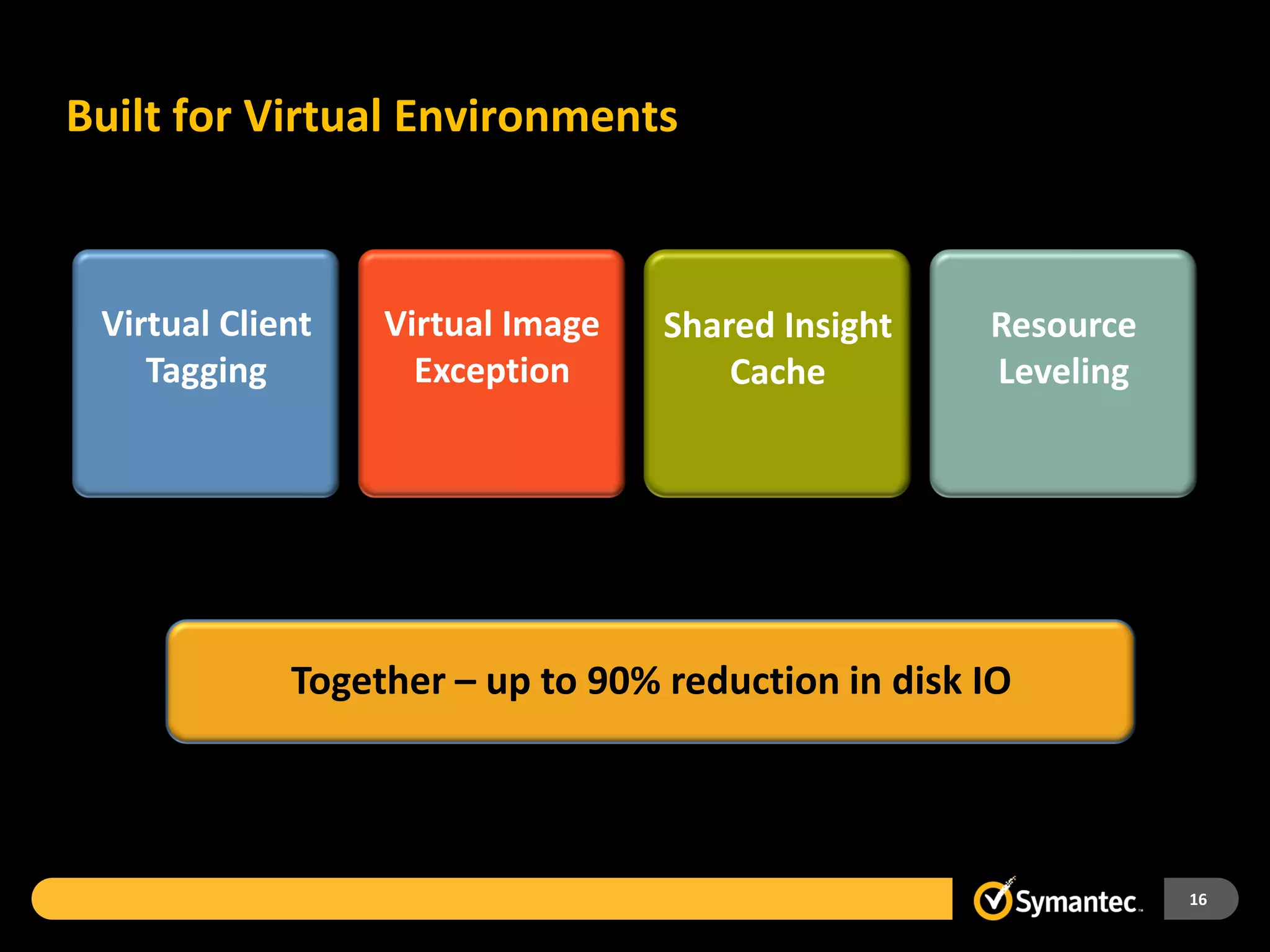
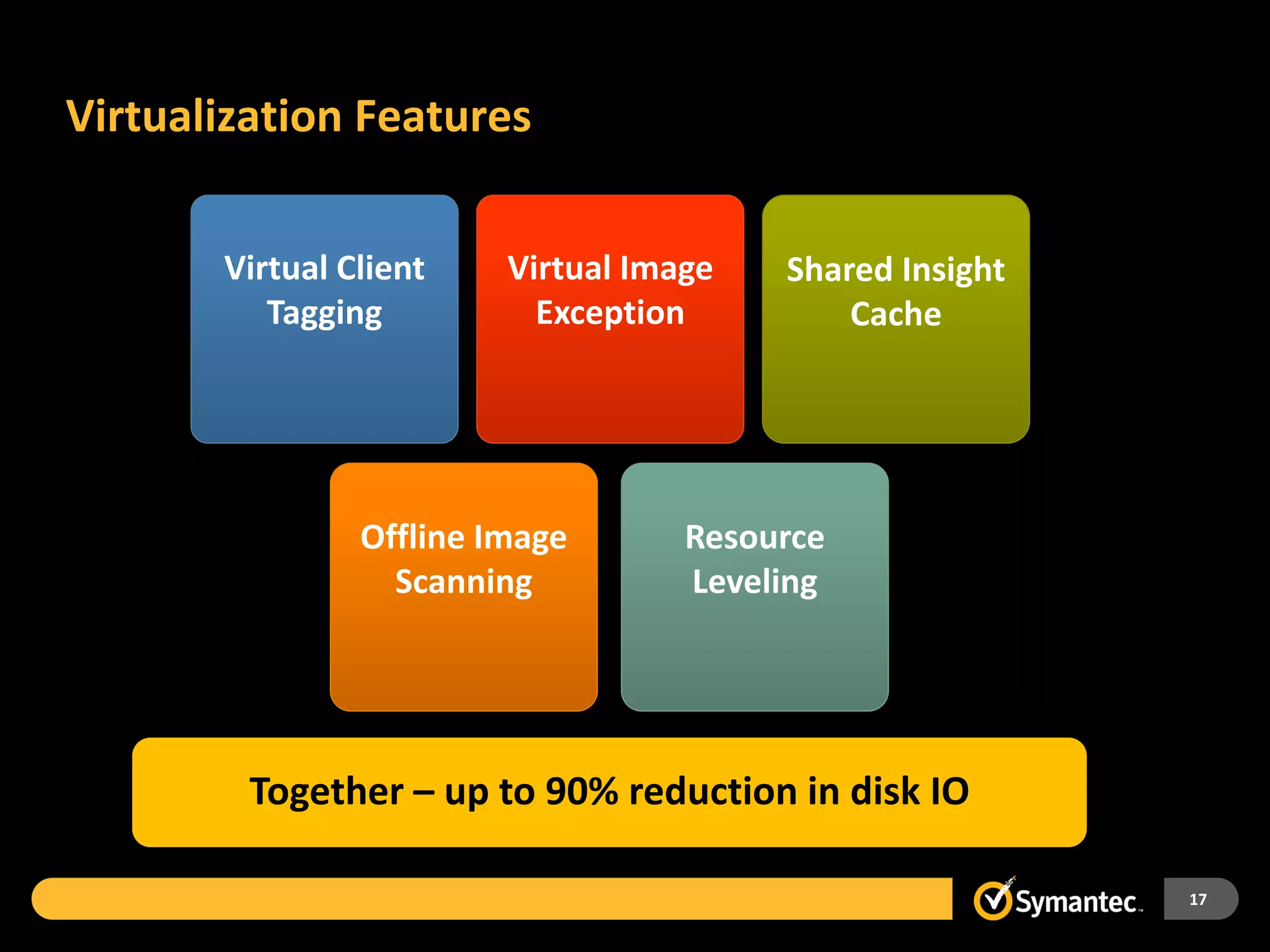
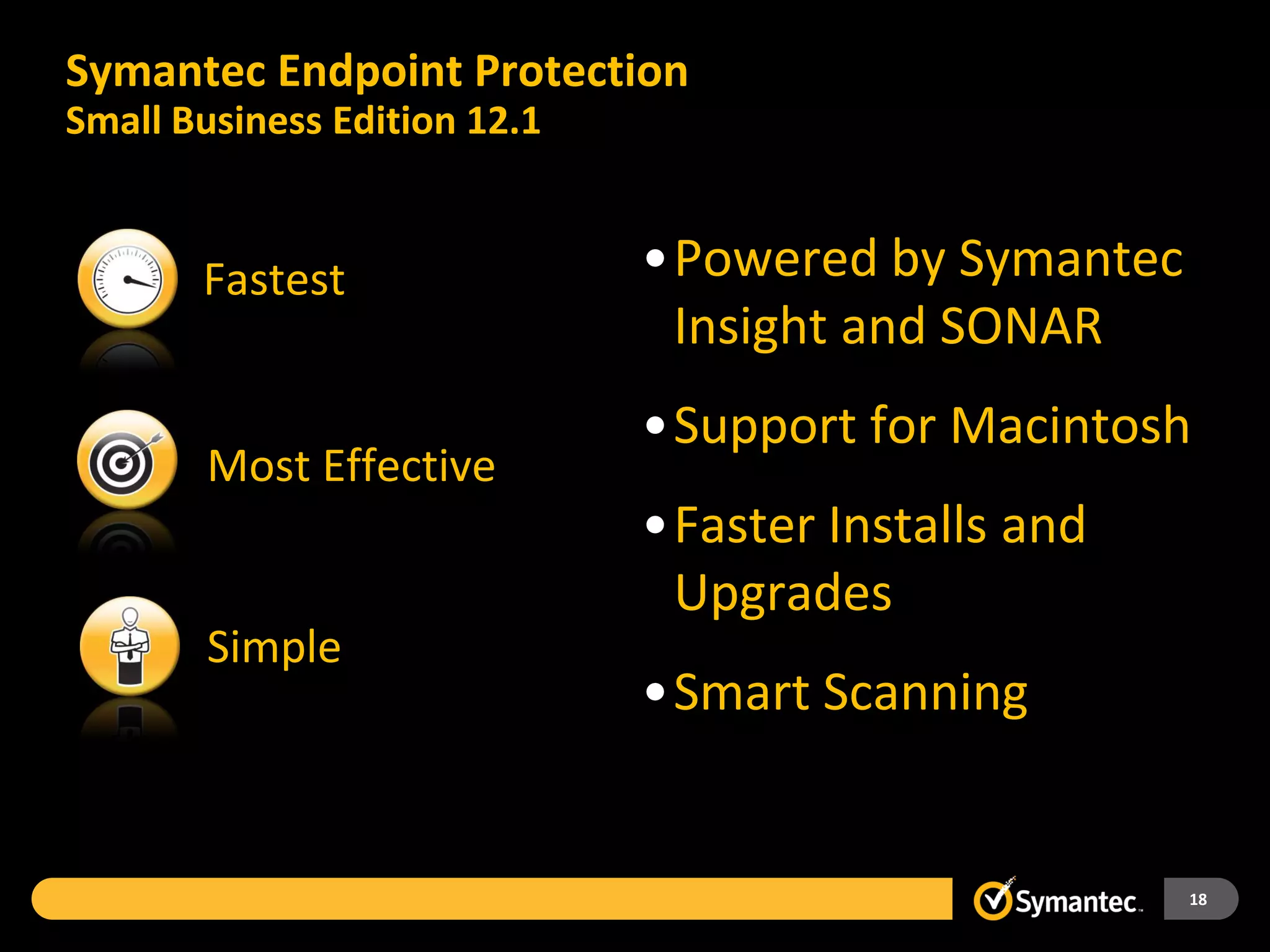
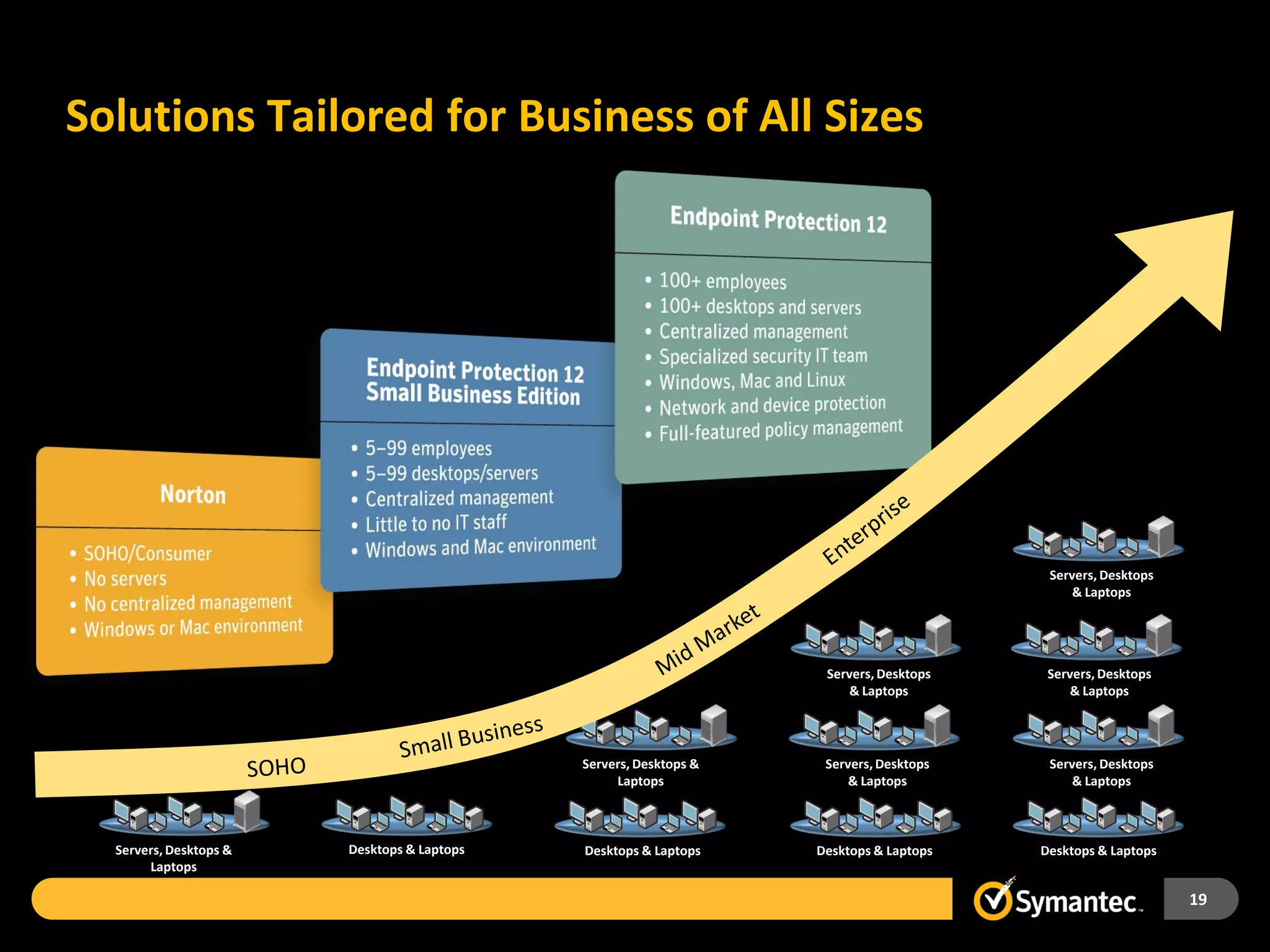
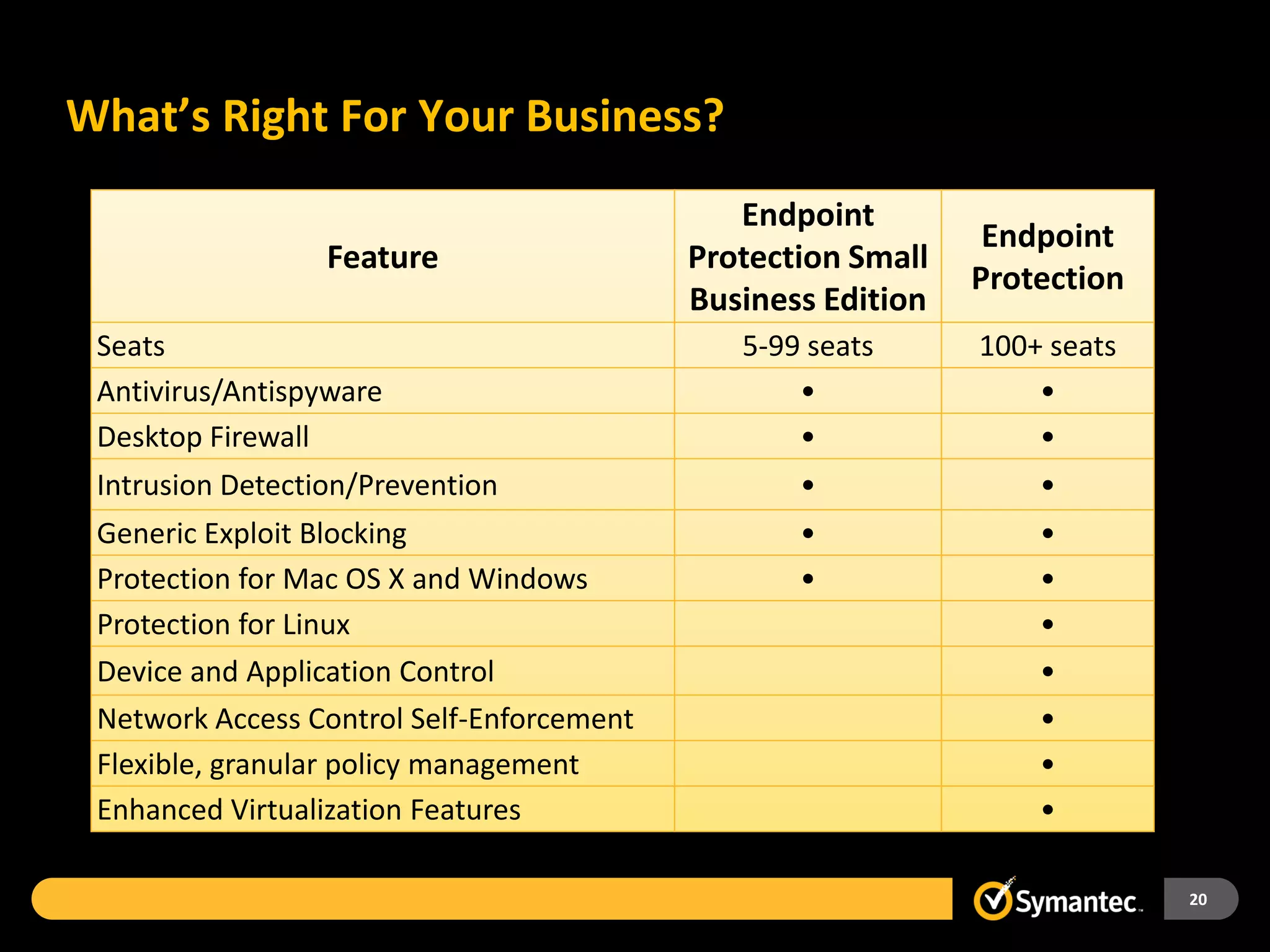
Symantec Endpoint Protection 12 provides a single agent and console for antivirus, antispyware, firewall, and other protections across Windows and Mac devices. It uses a new Insight technology powered by data from over 175 million endpoints to detect emerging and mutated threats that evade traditional signature-based scanning. Insight analyzes factors like file age, frequency, location, and community reputation ratings to proactively protect against new threats. Testing shows Symantec provides the most effective security with fewer false positives than competitors like Sophos, Kaspersky, Trend Micro, Microsoft, and McAfee.