This document provides an overview of data security, including:
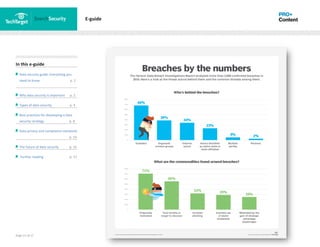
1) It discusses why data security is important, citing average costs of data breaches and examples of high-profile breaches.
2) It describes different types of data security technologies like encryption, perimeter security, data loss prevention, and more.
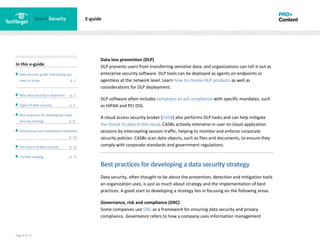
3) It offers best practices for developing a data security strategy, such as governance, risk and compliance frameworks; addressing insider threats; improving password security; and database protection.
4) It also covers major data privacy and compliance standards and envisions how AI/automation will be key to future compliance efforts.