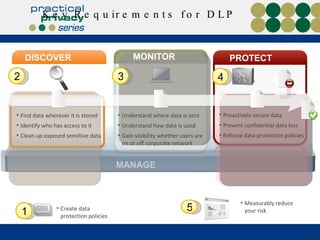
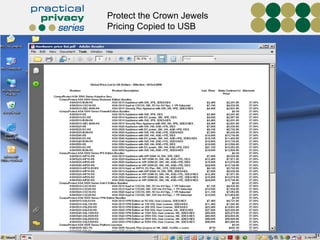
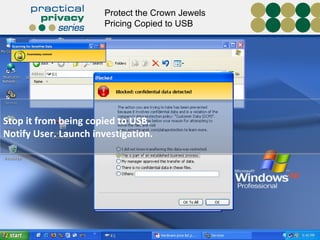
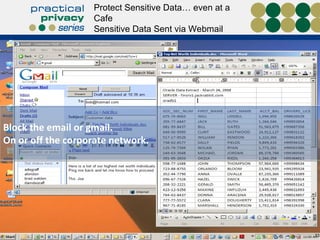
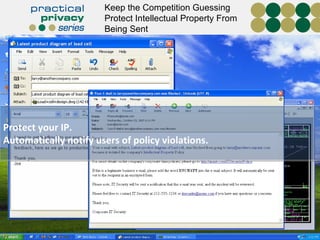
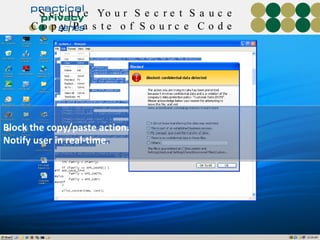
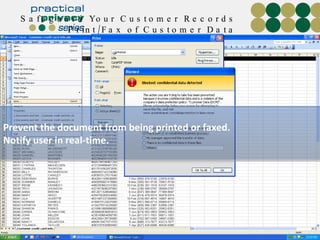
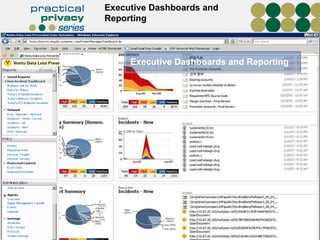
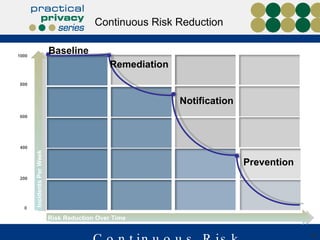
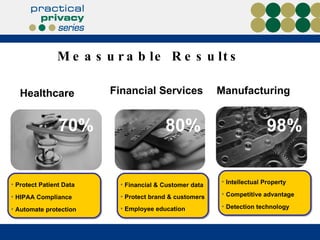
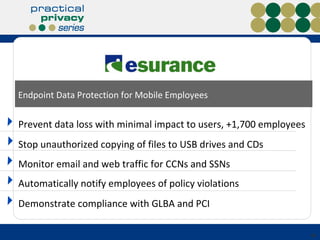
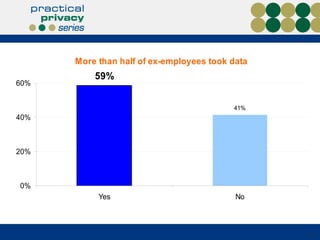
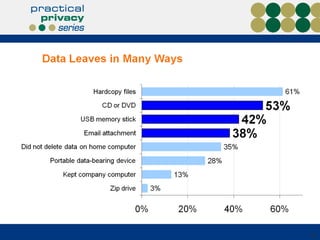
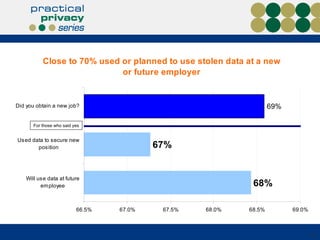
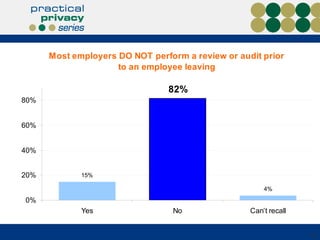
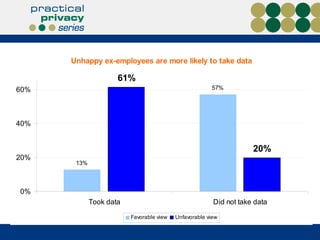
The document discusses the risks of data loss during corporate downsizing, revealing that 59% of exiting employees took company data, including sensitive information, through various methods. It emphasizes the need for organizations to implement strategic governance, technology controls, and employee training to protect corporate data effectively. Recommendations include establishing robust policies and leveraging Data Loss Prevention (DLP) technology to safeguard sensitive information against unauthorized access and leaks.




















![Thank You Constantine Karbaliotis [email_address] 416.402.9873](https://image.slidesharecdn.com/datalossduringdownsizing-100215110322-phpapp01/85/Data-Loss-During-Downsizing-27-320.jpg)