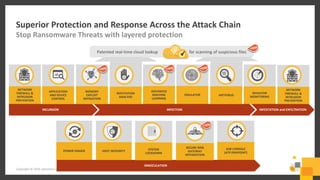
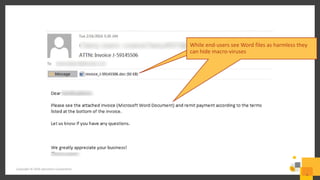
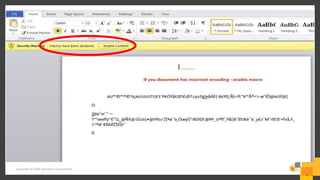
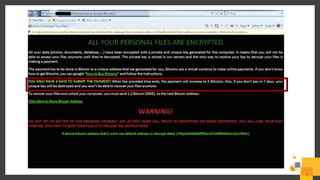
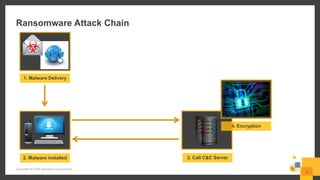
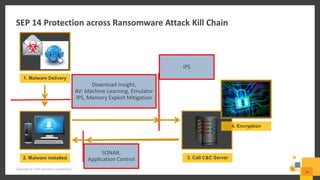
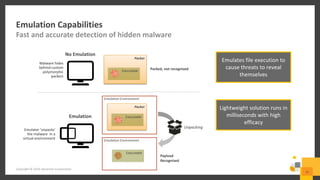
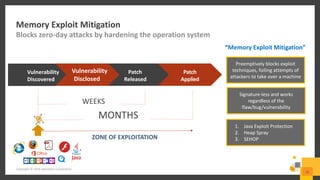
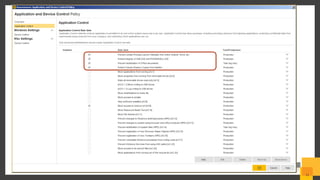
The document outlines a webinar series by Symantec focusing on endpoint protection against ransomware, emphasizing various strategies and technologies to mitigate risks. Key topics include the ransomware attack chain, detection capabilities, and protective measures such as user education, email security, and comprehensive backup solutions. It also highlights the use of advanced machine learning and behavior-based prevention methods to enhance security.