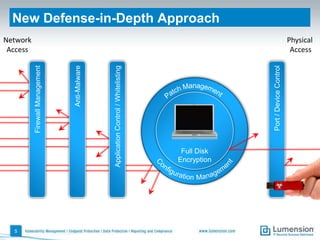
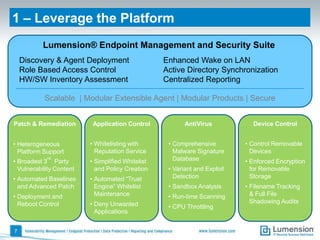
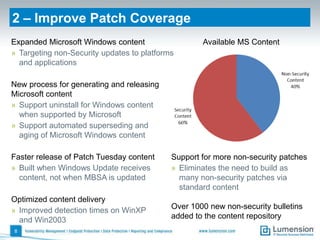
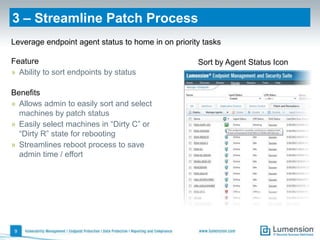
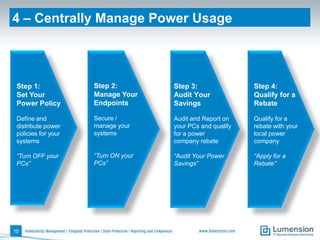
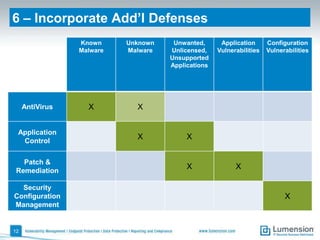
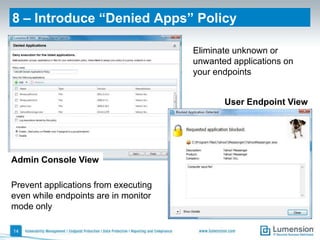
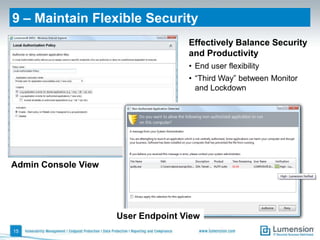
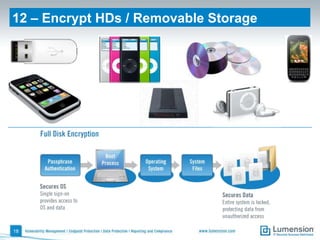
The document outlines 11 key security capabilities that organizations can implement using the Lumension Endpoint Management and Security Suite to address gaps in traditional defenses. It emphasizes leveraging tools for improved patch coverage, streamlining patch processes, enforcing security settings, managing power consumption, and incorporating additional defenses against vulnerabilities. The aim is to enhance security measures efficiently and effectively while providing actionable reporting and management capabilities.