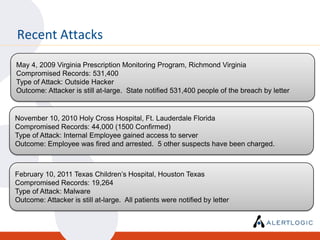
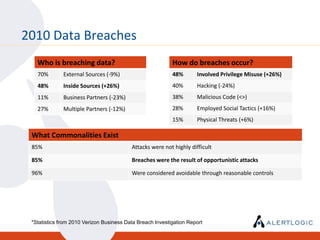
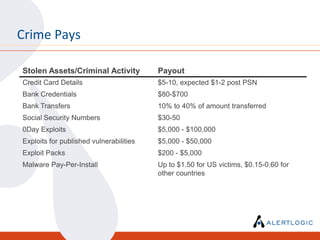
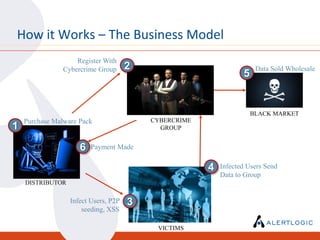
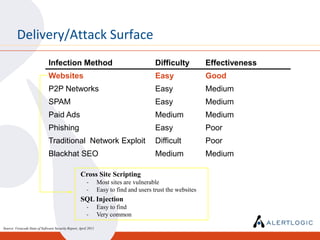
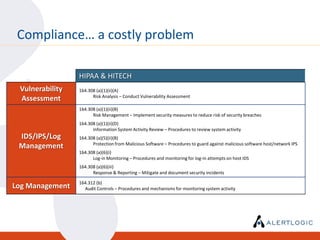
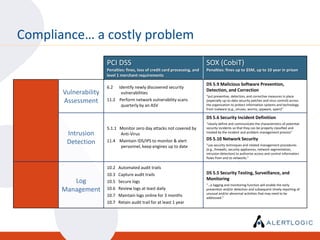
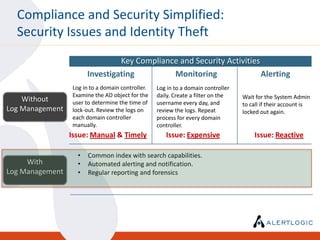
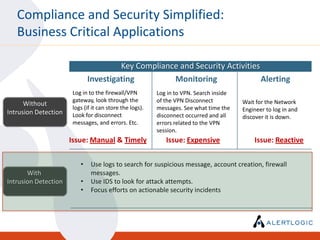
This document discusses the challenges of maintaining security and compliance. It notes that most breaches are opportunistic and avoidable through reasonable controls. It also discusses the business model of organized cybercrime and common attack methodologies. The document advocates for a security-first approach using log management, vulnerability scanning, and intrusion detection to help meet compliance requirements and detect security issues in a timely manner. Real-world examples are provided to illustrate how these technical controls can help investigate incidents and resolve audit findings.