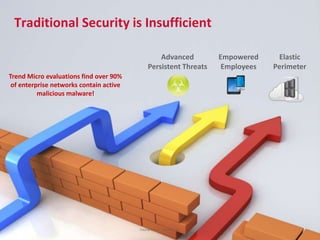
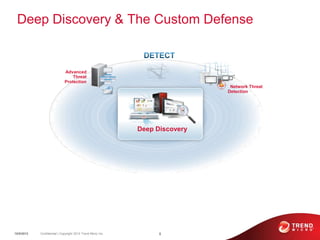
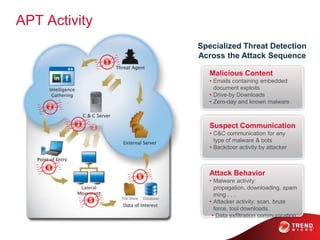
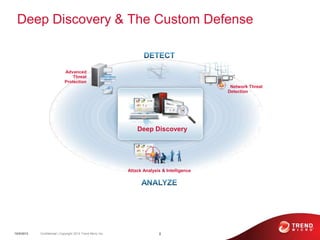
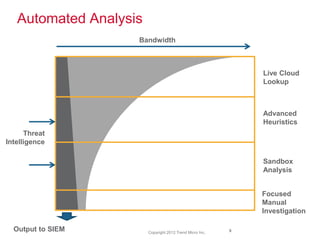
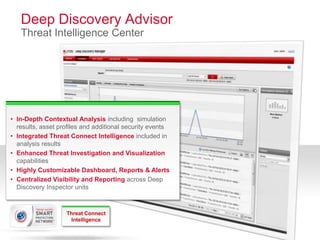
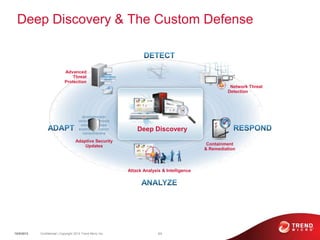
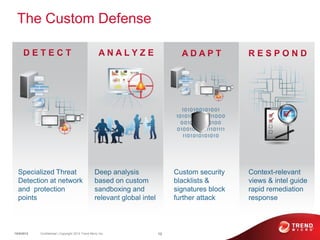
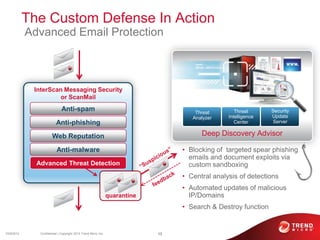
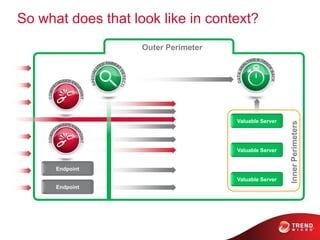
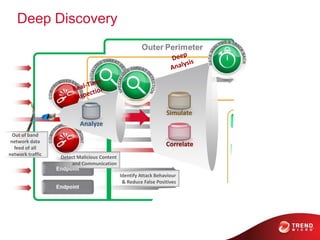
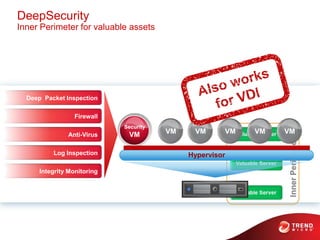
The document discusses advanced persistent threats and how traditional security methods are insufficient for dealing with them. It introduces Trend Micro's Deep Discovery and custom defense solutions, which use specialized threat detection, deep analysis, threat intelligence, and adaptive security updates to detect and block targeted attacks. This is done by monitoring networks for malicious content and communications, analyzing behaviors, and gaining insights to rapidly respond to and remediate threats.