Step by step exercise for bw 365
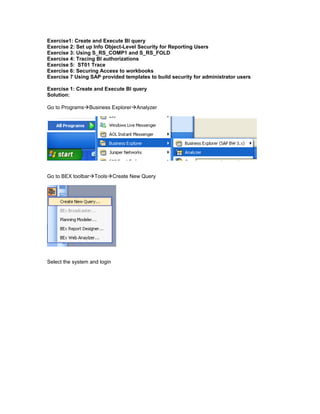
- 1. Exercise1: Create and Execute BI query Exercise 2: Set up Info Object-Level Security for Reporting Users Exercise 3: Using S_RS_COMP1 and S_RS_FOLD Exercise 4: Tracing BI authorizations Exercise 5: ST01 Trace Exercise 6: Securing Access to workbooks Exercise 7 Using SAP provided templates to build security for administrator users Exercise 1: Create and Execute BI query Solution: Go to ProgramsBusiness ExplorerAnalyzer Go to BEX toolbarToolsCreate New Query Select the system and login
- 2. Select “New Query” Select the Info Provider on which query need to be created Select the Cube and click Open
- 3. Drag and drop the characteristics/key figures from left window to right Rows/columns and Free Characteristics And then click to save the query. Select the Role Enter the description and technical name and Click SAVE Login using Bex Analyzer and then run the Query and Result will be displayed as below
- 4. Exercise 2: Set up Info Object-Level Security for Reporting Users Solution: The steps to implement authorization level security: • Make the info object as authorization relevant • Create analysis authorization on that info object • Assign analysis authorization to user (directly or through Role) • Add a variable to the Query Create a user Execute SU01 and give the user name and click Create Enter User First Name and Last Name Go to Logon Tab and then Enter Initial Password; enter the same password in Repeat Password
- 5. Go to Roles Tab and then add Role “REPORTING_BASIC” and Click Save Note: If REPORTING_BASIC role is not existing in the system then can be uploaded in the below way to the system. This Role contains access to Basis Transaction codes needed by a reporting user. Upload a Role: • Copy the below role to your desktop REPORTING_BASIC. SAP • Execute Tcode PFCG and then Select RoleUpload Click Ok
- 6. Select the Role and Click OPEN And then click ok on the message Go to the change mode of the Role by clicking Go to authorization tab by clicking change authorization data Click Save and Then Generate
- 7. And role is now uploaded and activated in the system Define the Info Object as authorization relevant Execute RSA1, Go to InfoProvider, expand the info are and then double click on your info object or Execute Tcode RSD1, enter info object name Go to change mode and then Business Explorer tab, check “authorization Relevant”
- 8. Save and activate the info object. Create Analysis authorization
- 9. • Execute Tcode RSECAUTH • Enter Name of analysis authorization ZCOMP_CODE and Click Create • Enter short, medium and long description and click to insert mandatory characterstics Double click on 0TCAACTVT, then click Value authorization tab and enter the below values and go back Double click on 0TCAVALID, then click Value authorization tab and enter the below values and go back And then Double click on 0TCAIPROV, then click Value authorization tab and enter the below values and go back
- 10. Enter 0COMP_CODE And then Double click to specify the values Note: This value defines the restriction of your info object to some specific values. You can select any value depending upon the data that is available in your info object And then click Save. Assign Authorization to User Execute Tcode RSU01, enter user name and click Change Enter analysis auth name and click Insert
- 11. And then Click Save Add a variable to a Query Go to Query Designer. Open existing query. Drag Company Code to char restriction tab Right click on Company Code and select Restrict Select variables from the drop down list. Click Create Specify Description for Variable, Technical name and Processing Type in General Tab
- 12. Specify the below mentioned details in “Details” tab Move the variable from left window to Selection list and click OK
- 13. Save the Query. Login using Reporting_## and select the query to execute using Bex Analyzer It will be prompted for the variable value Result will be displayed only for company Code 1000 and 1101 Exercise 3: Using S_RS_COMP1 and S_RS_FOLD Solution: Create a new role REPORTING_BASIC_NEW by copying the REPORTING_BASIC role Execute Tcode PFCG and then Enter Role Name The Role Copy Enter the new Role name and click copy selectively Go to Change mode of the Role, authorization tab, click Change authorization data
- 14. • Expand the Business Information Warehouse object class and then authorization object Business Explorer – Components Enhancements to the Owner (Object S_RS_COMP1). • Choose Change • Next to the Owner (Person Responsible) give the userid of the query owner • For e.g. if we give userid of Anil here and assign this role to REPORTING-## user then REPORTING-## will be only able to view the queries created by Anil. Click Save and Then Generate and click ok to accept the default profile Assign the Role to REPORTING-## user
- 15. Execute SU01 and click Change Go to Roles Tab and Delete the existing role and add new one and click Save • Log on to the Bex Analyzer as REPORTING-## and note which queries the user can access through Info Area • User should be able to see the queries created by user Anil Hide Info Area Push button for reporting users using S_RS_FOLD Change role REPORTING_BASIC_NEW through PFCG and click Change authorization Data
- 16. Click manually to add S_RS_FOLD auth object Enter object and click Ok Select the Value, Save and Generate the Role This will hide the Info Area Push button for the users, so that they are not able to view the Info Providers
- 17. Exercise 4: Tracing BI Authorizations Solution: Create any new user with access to Role REPORTING_BASIC_NEW and let user execute ZTEST_QUERY2. User will get below authorization error: We need to put a trace on to analyze the error. Execute RSECADMIN and then go to Analysis Tab. Click on Error Logs Click “Configure Log Recording”
- 18. Add the user name and click “Add User” and Click Save Login as REORTING_1 and let the user execute the same query until user get “No authorization” error message: To Check the Trace Execute RSECADMIN and then go to Analysis Tab. Click on Error Logs Click Display
- 19. Error log will be something like below: Trace is checking info object 0COMP_CODE in user’s profile which is missing
- 20. Exercise 5: ST01 Trace Solution: Login as an admin user and Execute ST01 Make sure Authorization check is selected and there is no General Filters And click on Trace On Execute Tcode RSA1 and go to the specific Info Provider under modeling tab Right click and Select “Create InfoCube”
- 21. Enter name, description and copy from and then click “Create” Select Activate Execute ST01 and Press “Analysis” Enter user id and limit the records for authorization check only and click Execute And you will be able to see the trace log for authorization checks that happened against your profile Exercise 6: Securing Access to workbooks Part 1 Open an existing query and try to save it to Roles Tab using REPORT_1 user id
- 22. Since No roles are assigned to your end, you will not able to assign it. Part 2 Execute Tcode PFCG Enter Role name REPORTING_WORKBOOK_01 and click Create Enter description and Save. Go to authorization tab Click on Change Authorization data Click manually to add the authorization objects
- 23. Add S_USER_AGR and S_USER_TCD and click Ok Maintain the values as below And generate the Role Go to Menu Tab and created Folder Sales
- 24. Enter name as Sales and Click OK Now assign the Role to User Reporting_1 and click on User comparison and save the role Part 3 Execute the Query using BEX Analyzer and save the results Go to Roles Tab Workbook roleSales Folder Enter the Workbook name and click SAVE
- 25. Part 4 Go to PFCG and enter the Role name REPORTING_WORKBOOK_01 Go to Menu Tab and click Report Add the workbook id
- 26. And save the Role Exercise 7: Use SAP Provided Template to Build Security Solution: Execute PFCG and enter name and click Create Enter Description and Go to Authorization tab, and click change authorization data
- 27. Select the role S_RS_RDEAD and Select Adopt reference You can expand the required Class and then auth object to see the specific values
