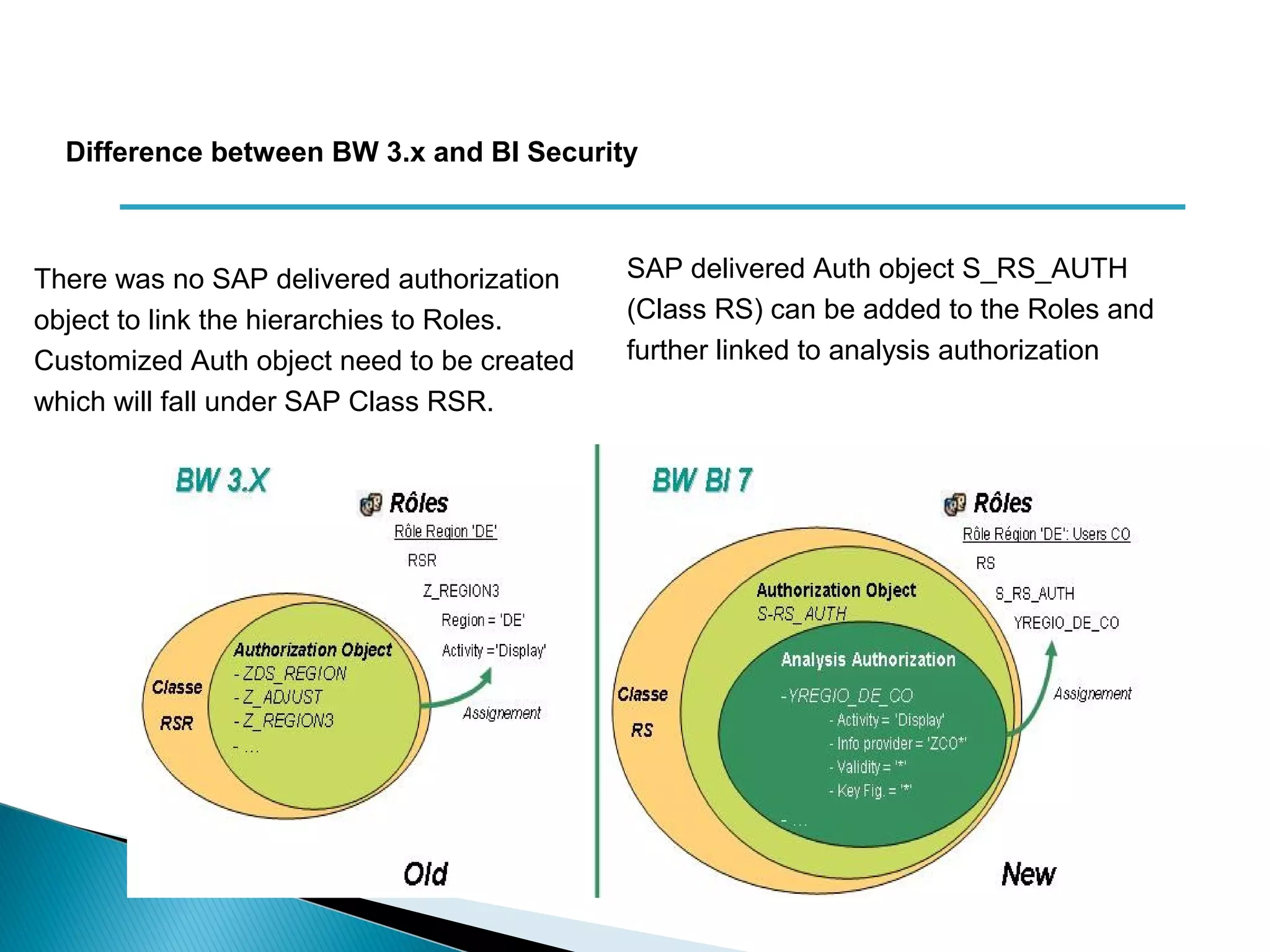
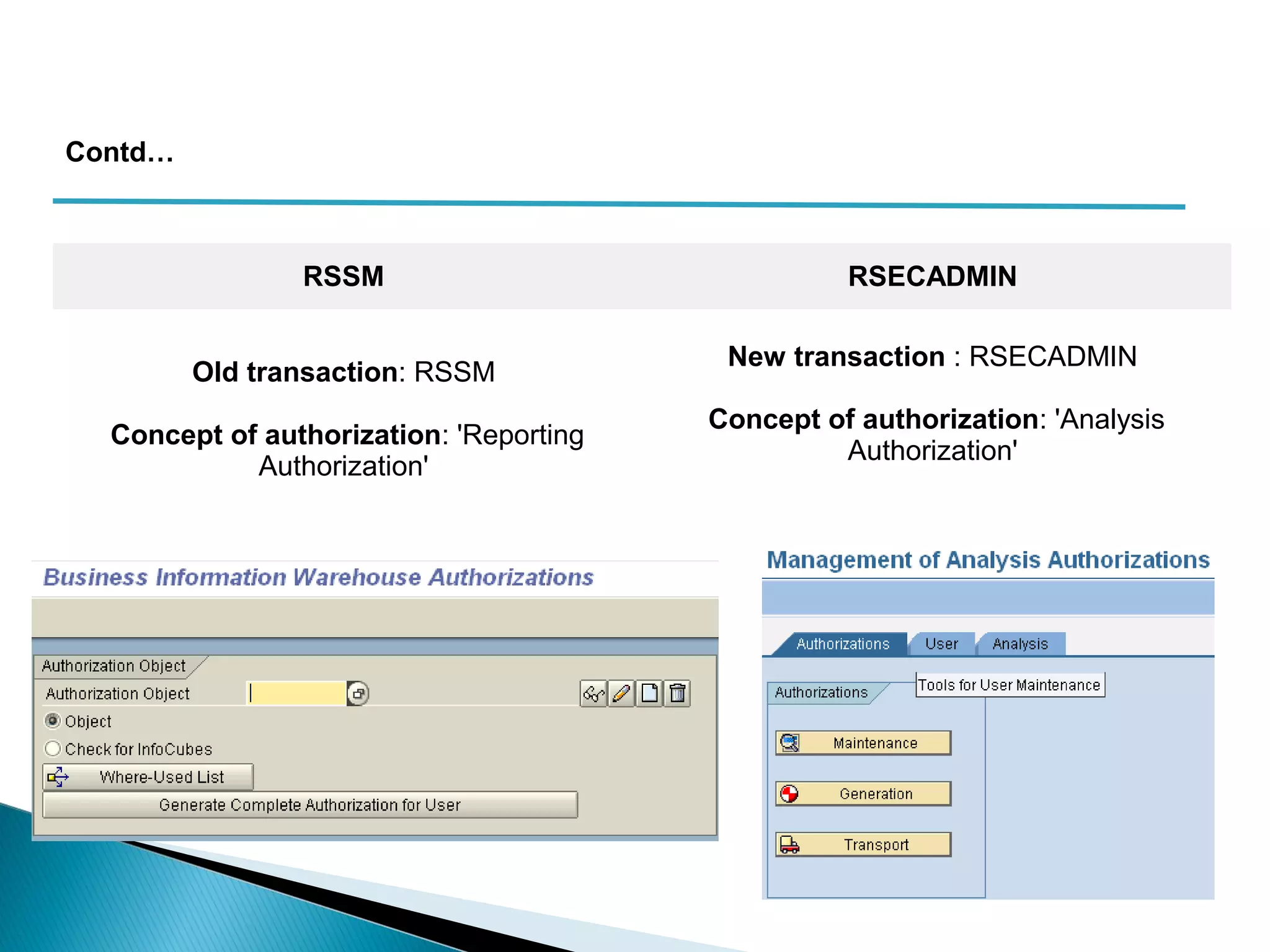
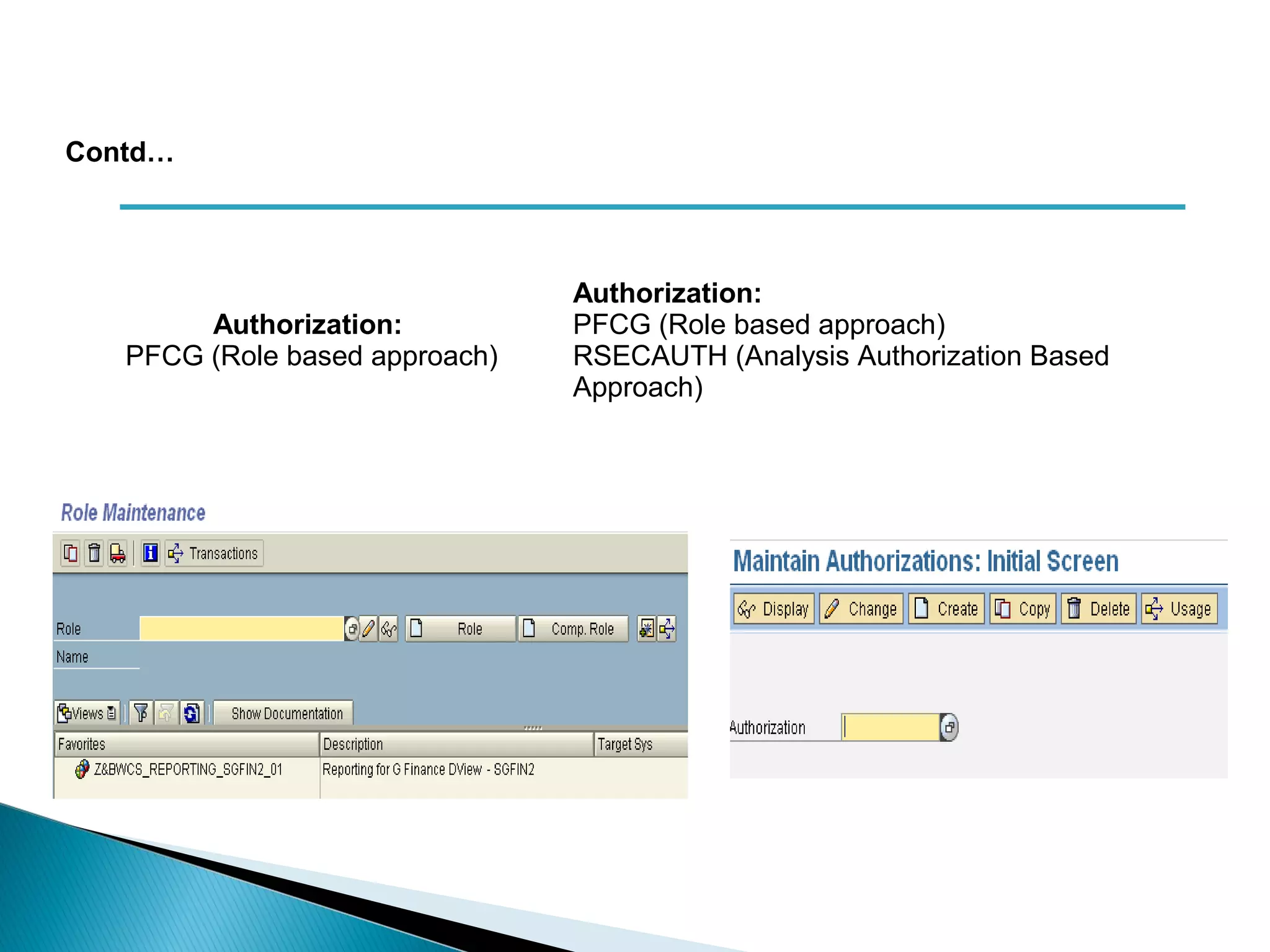
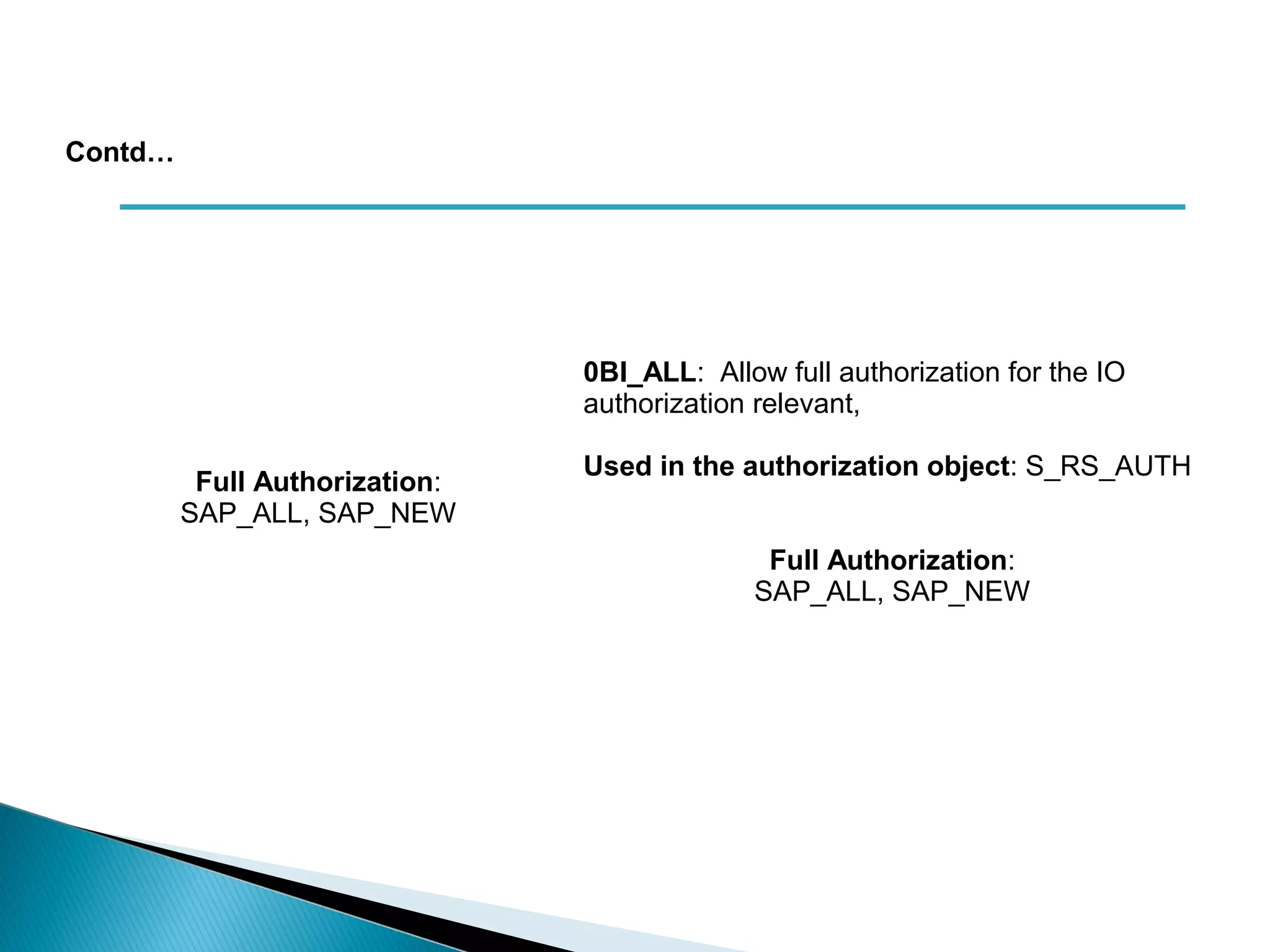
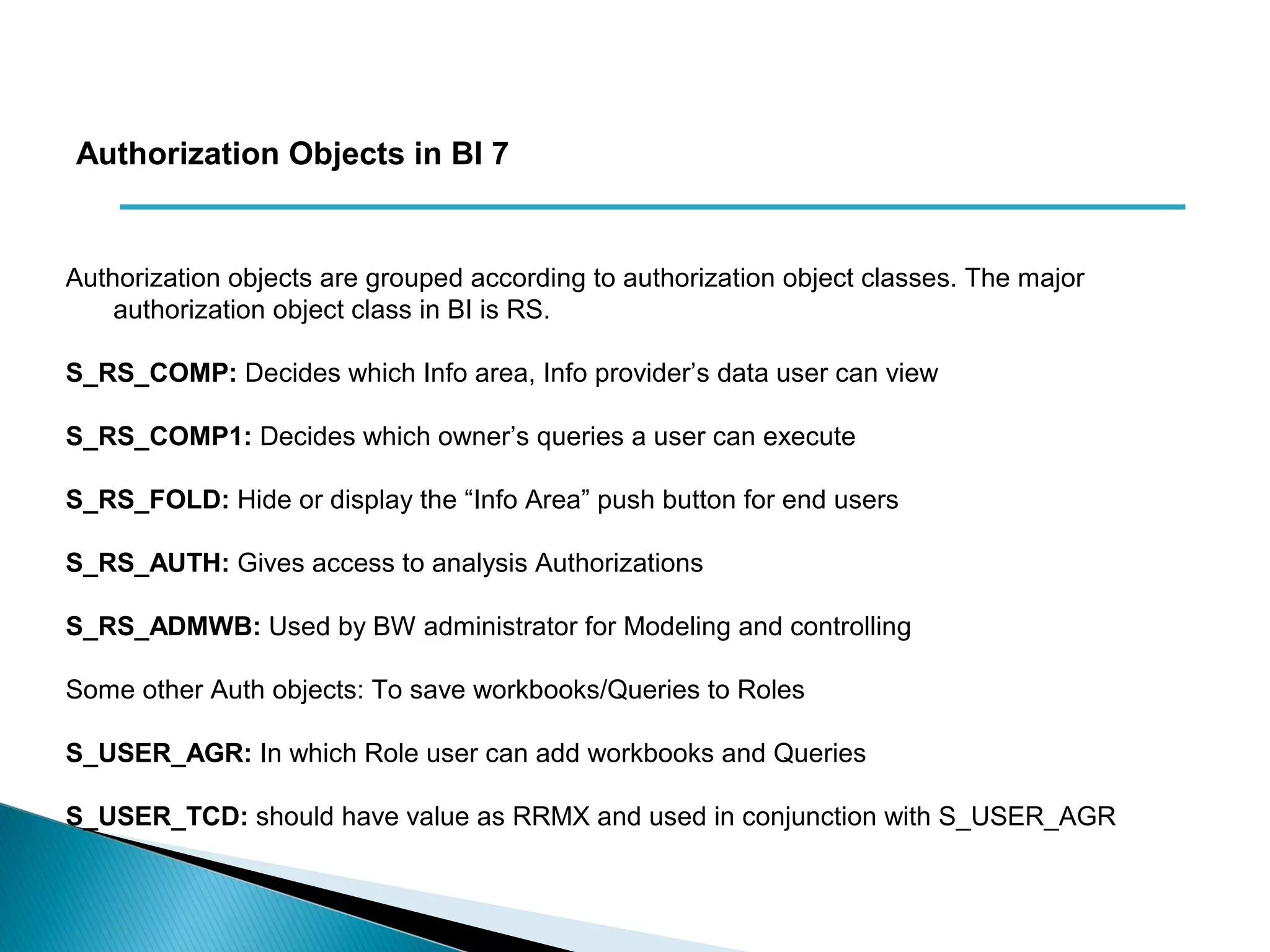
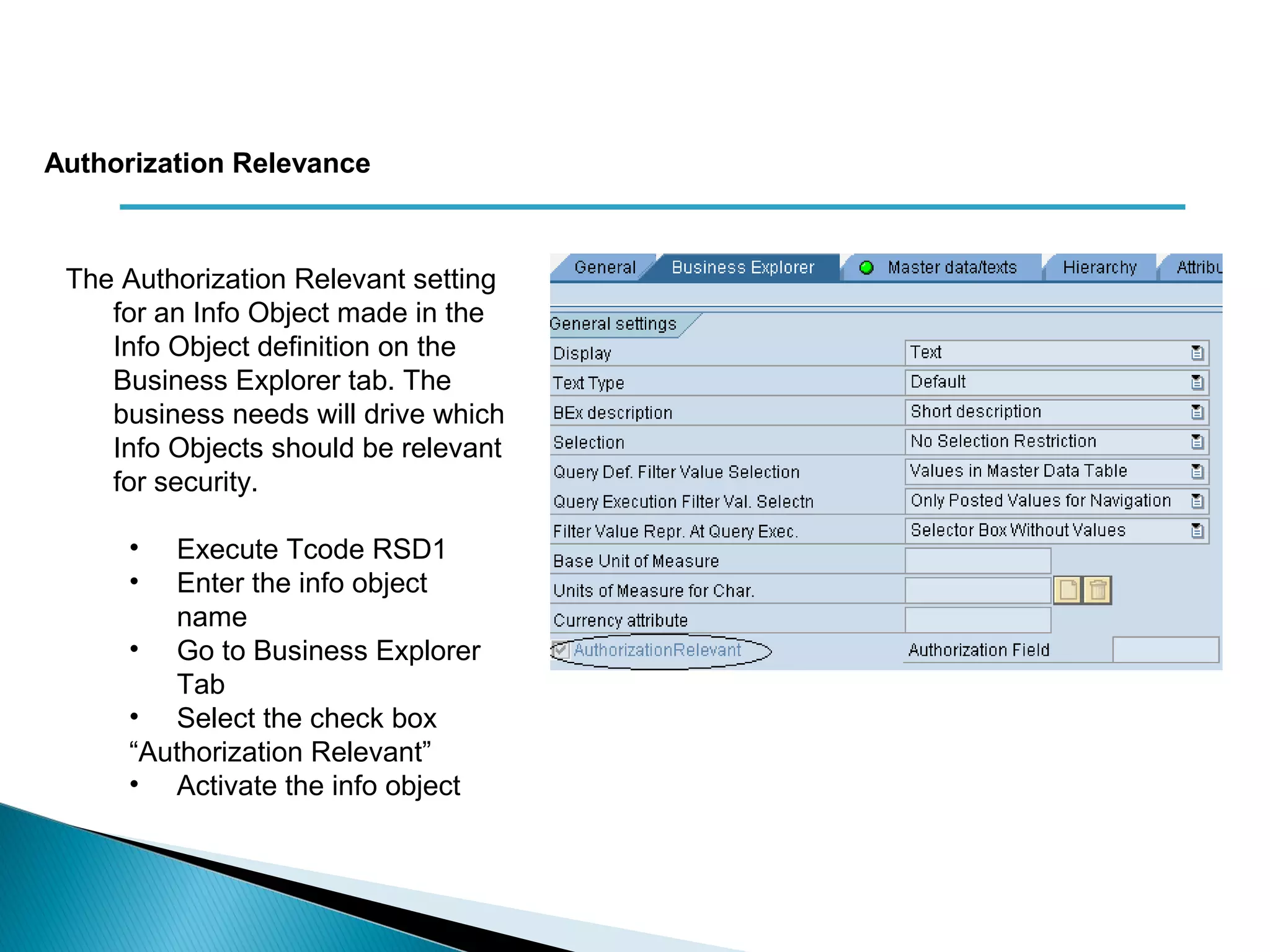
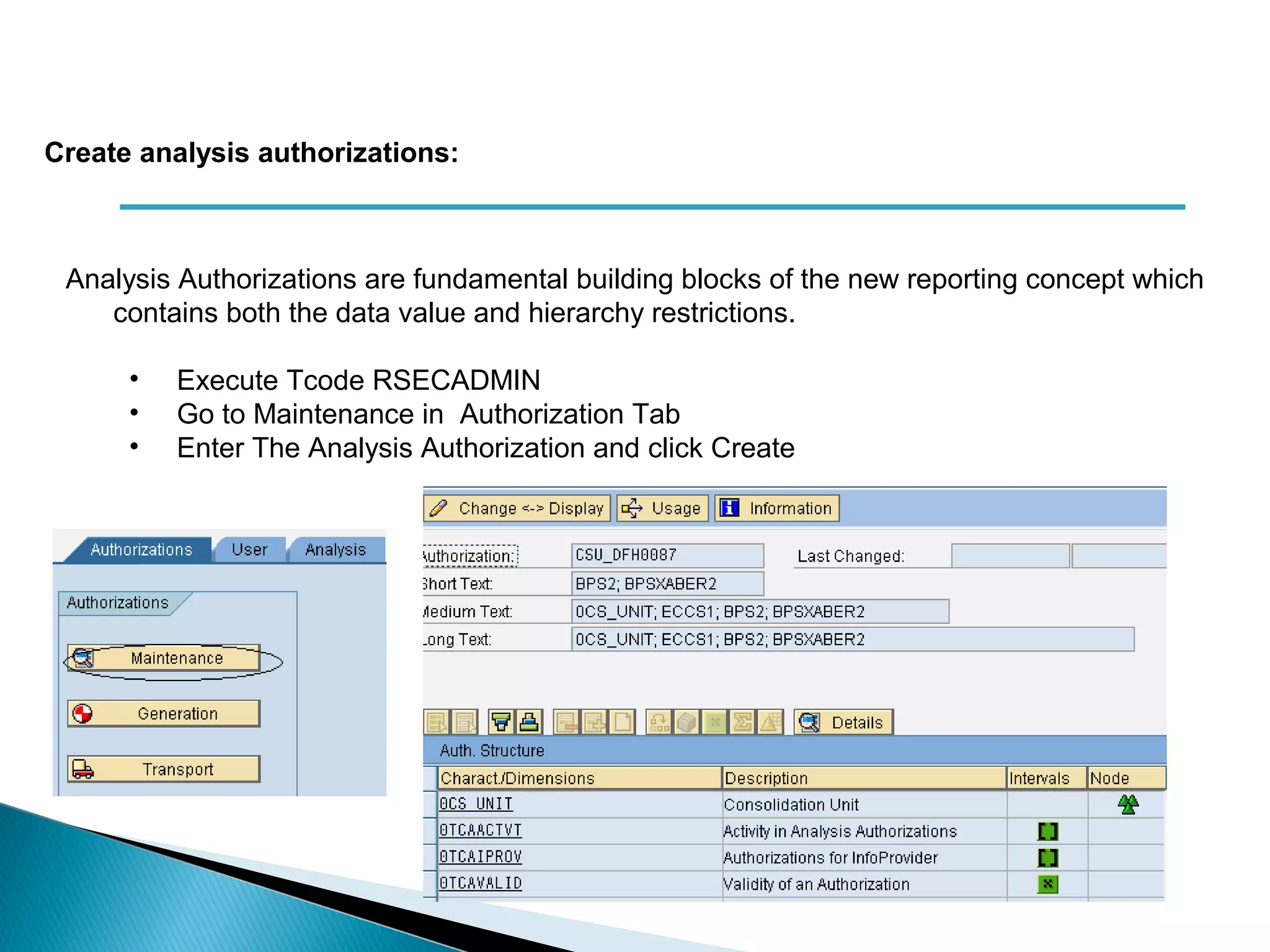
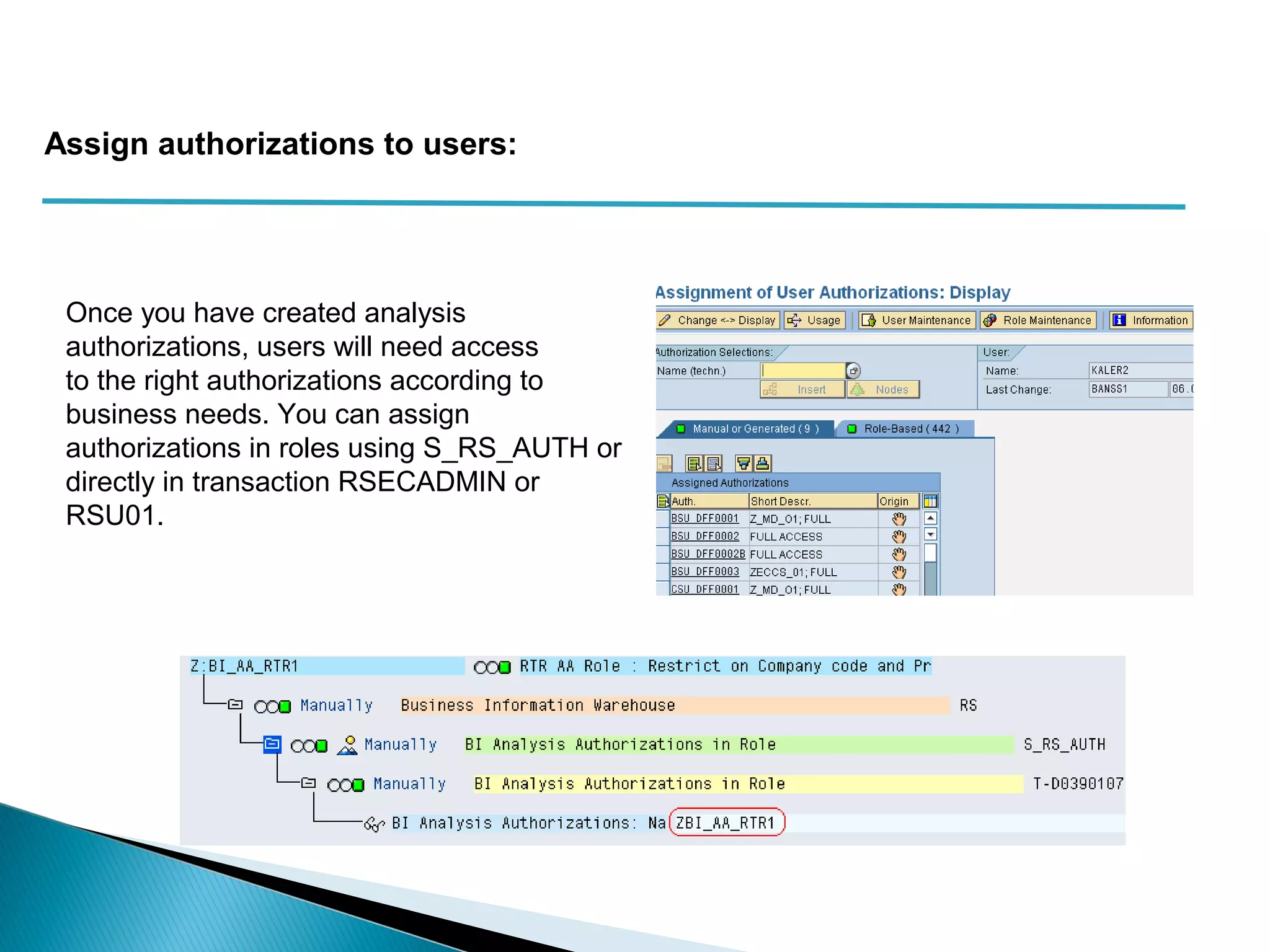
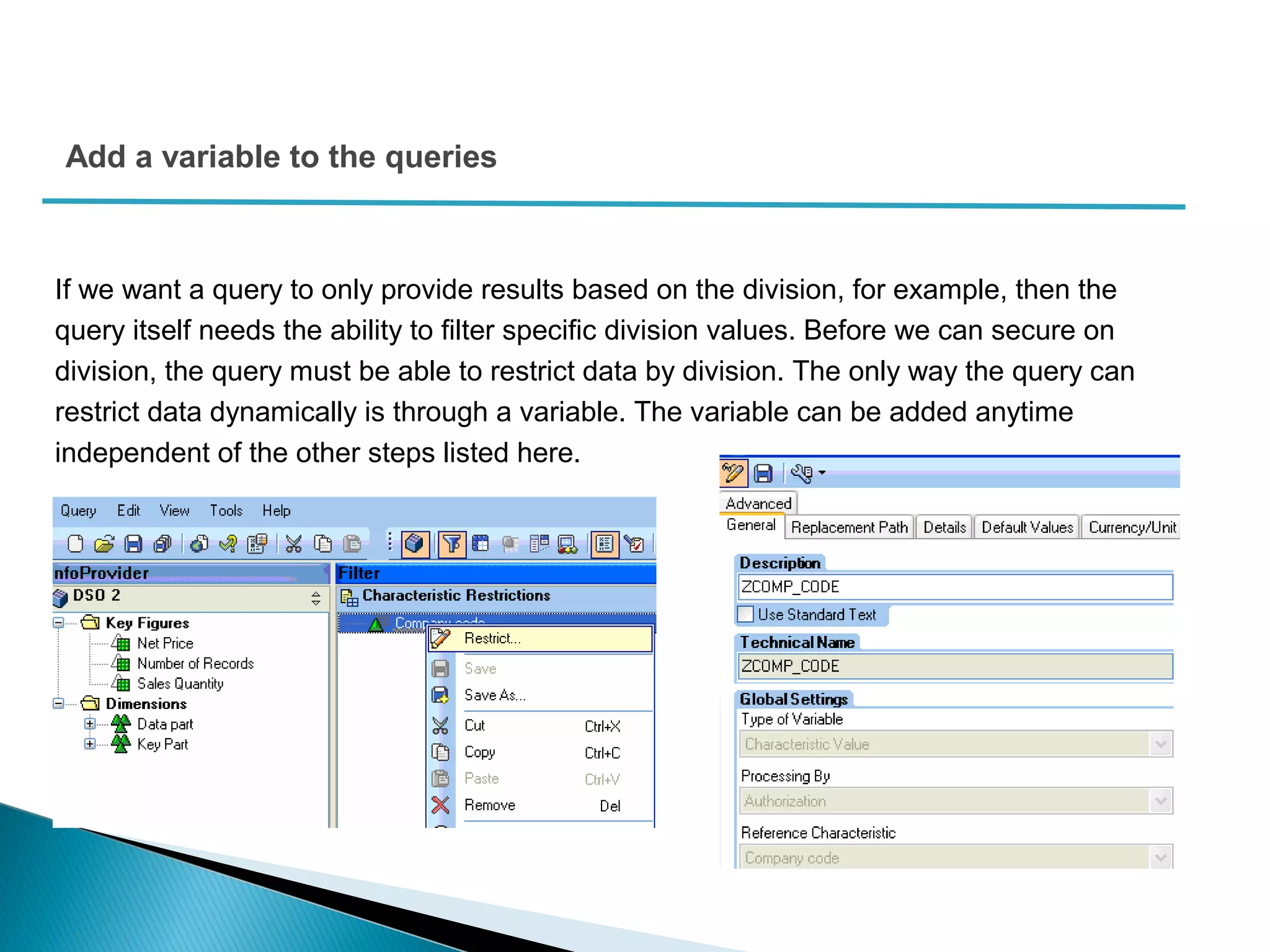
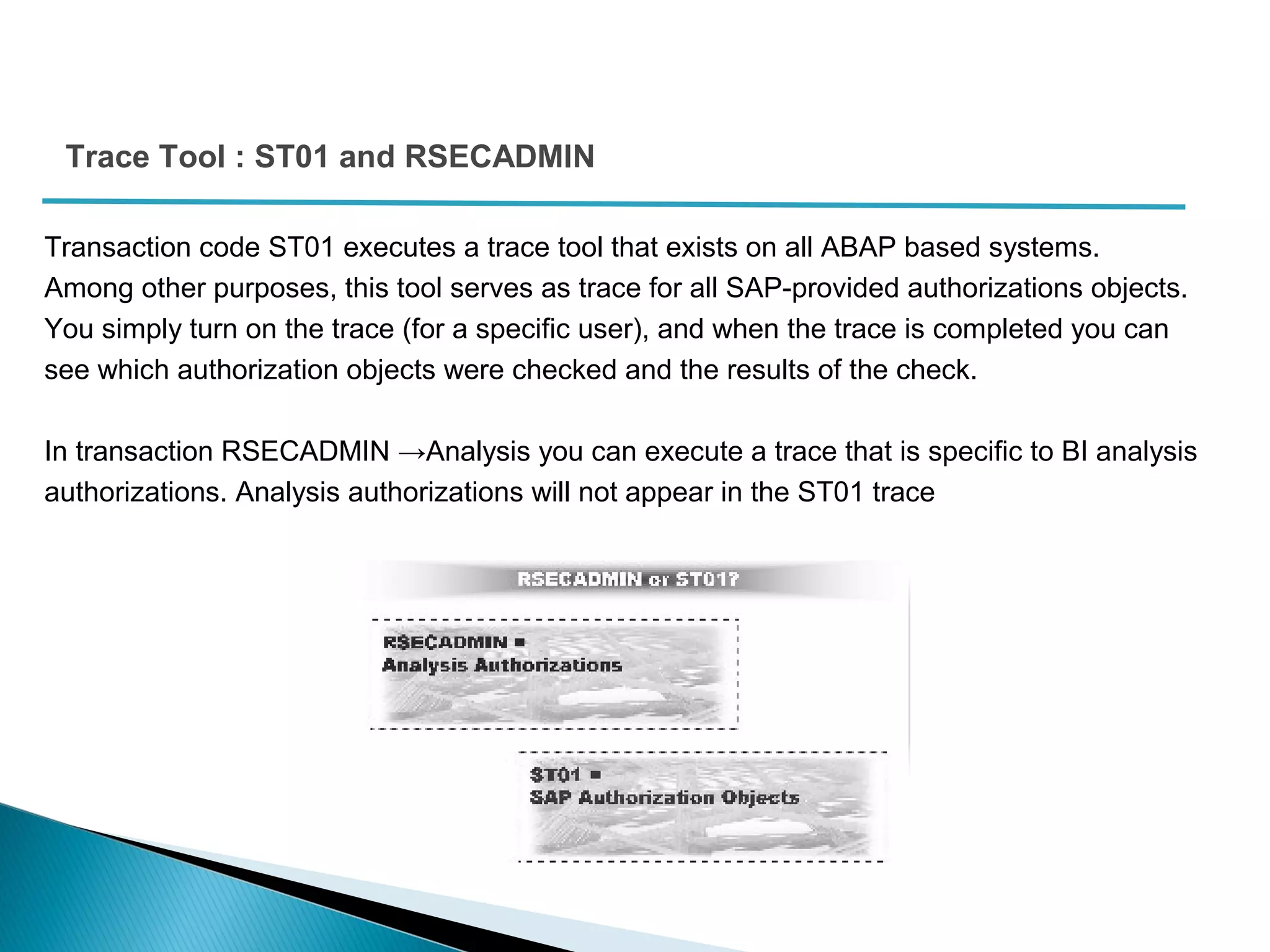
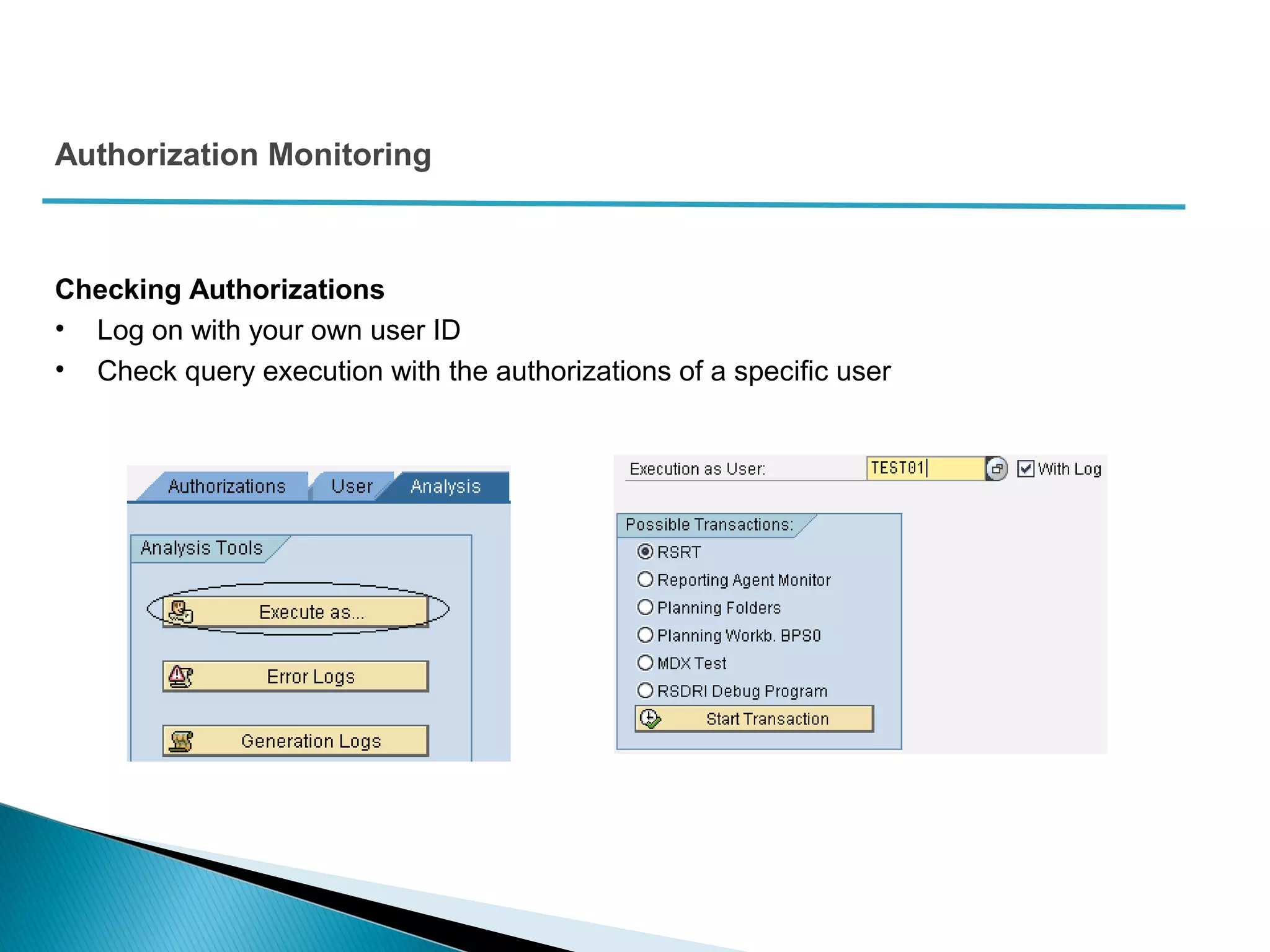
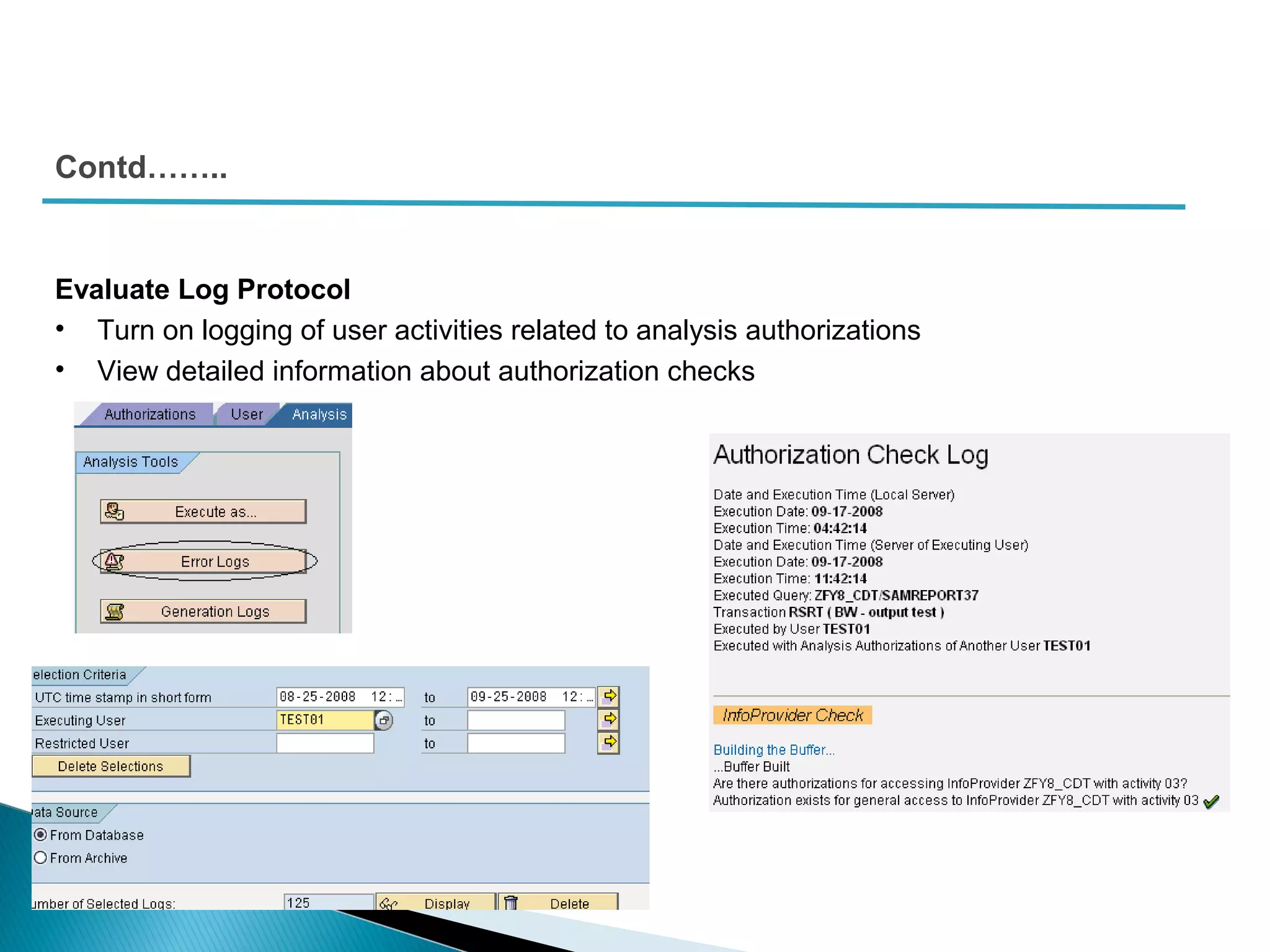
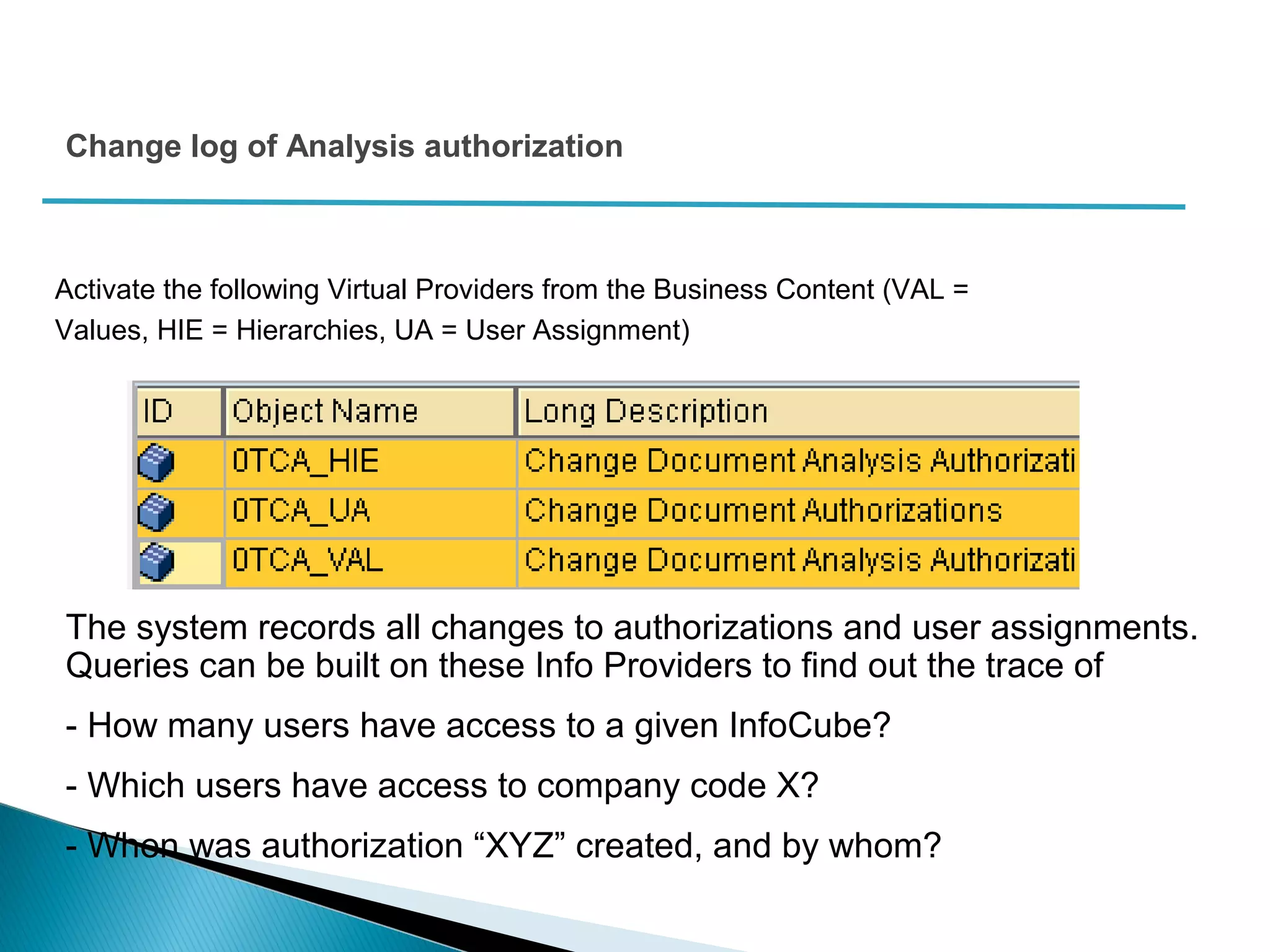
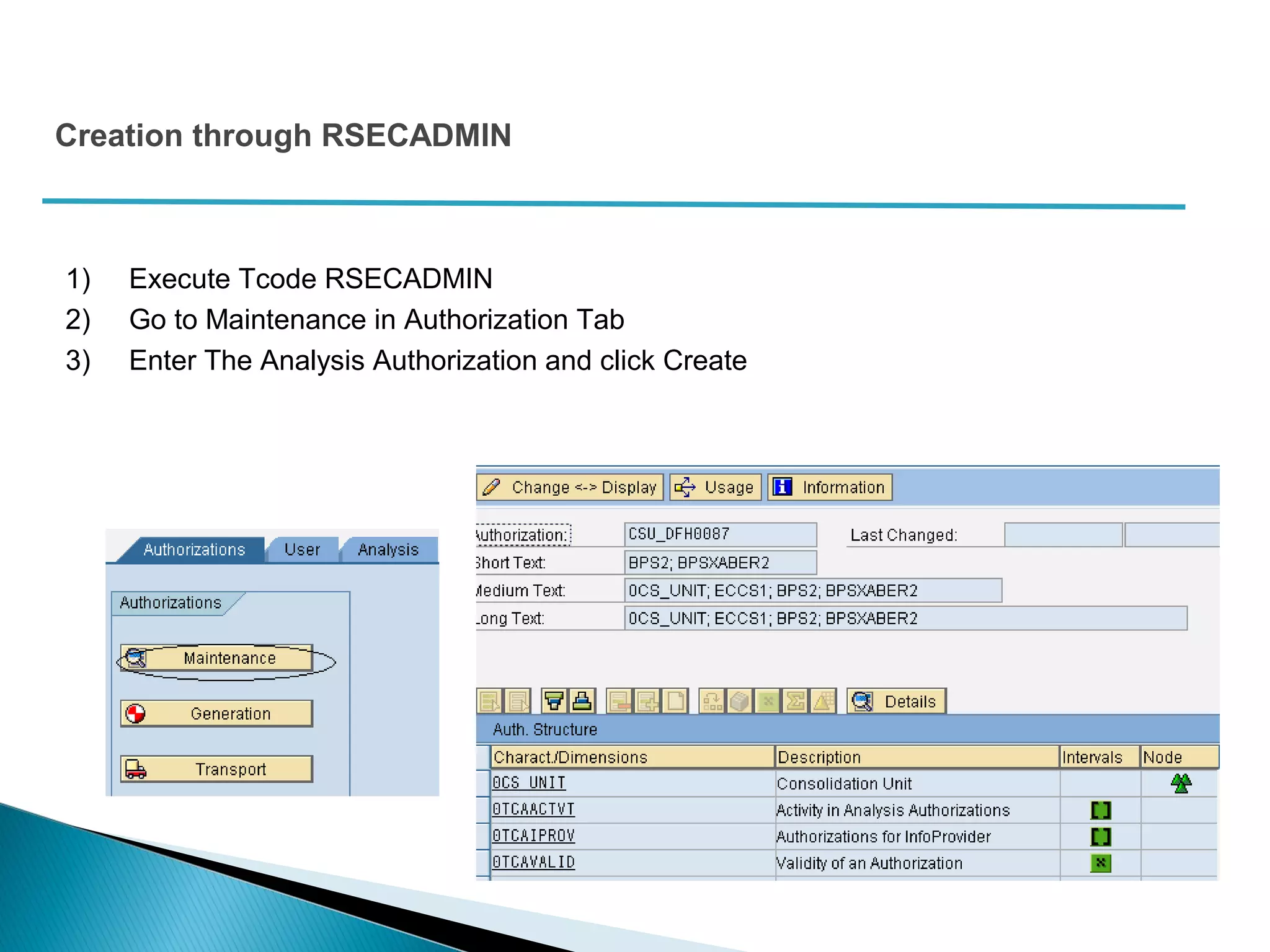
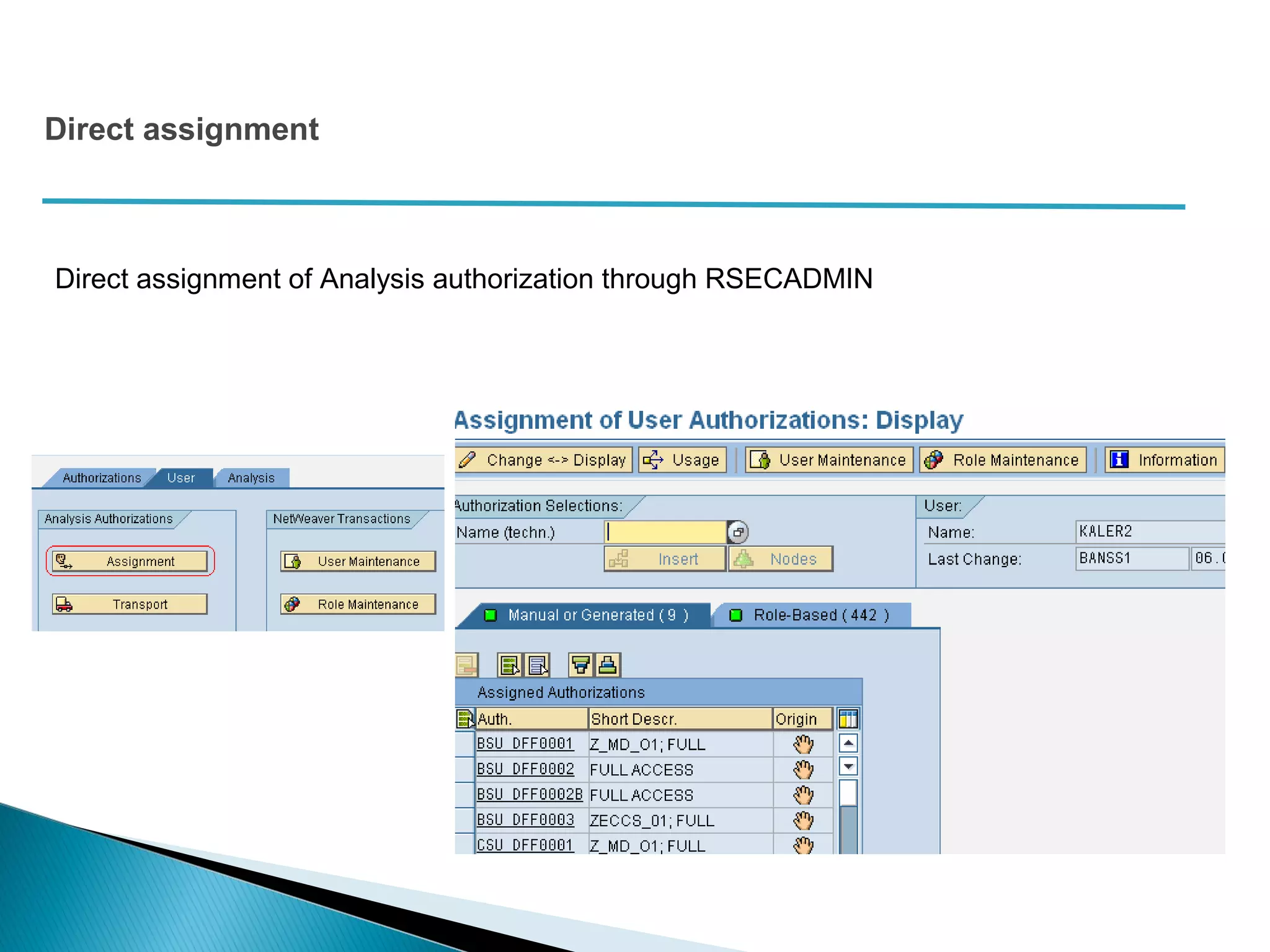
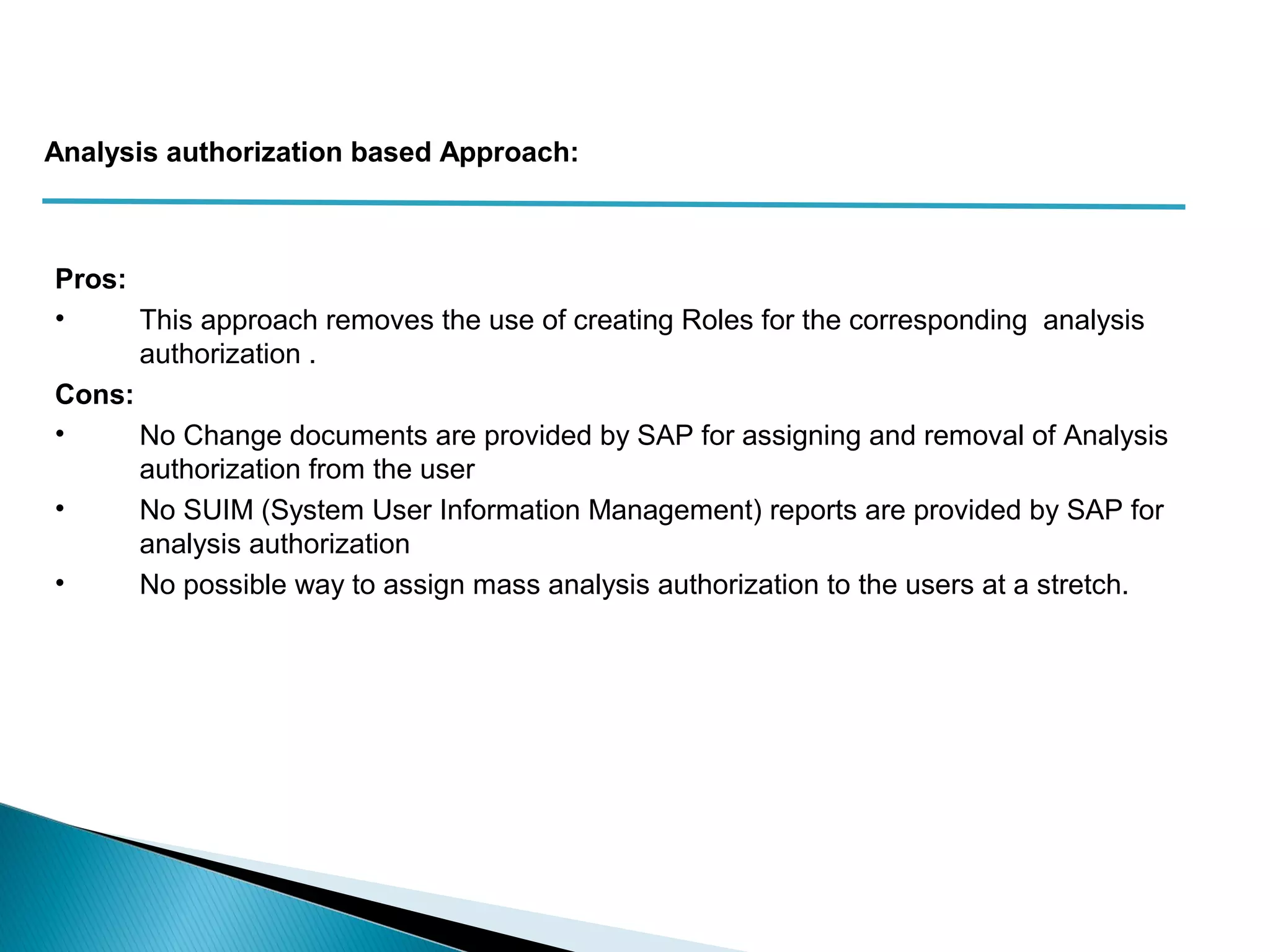
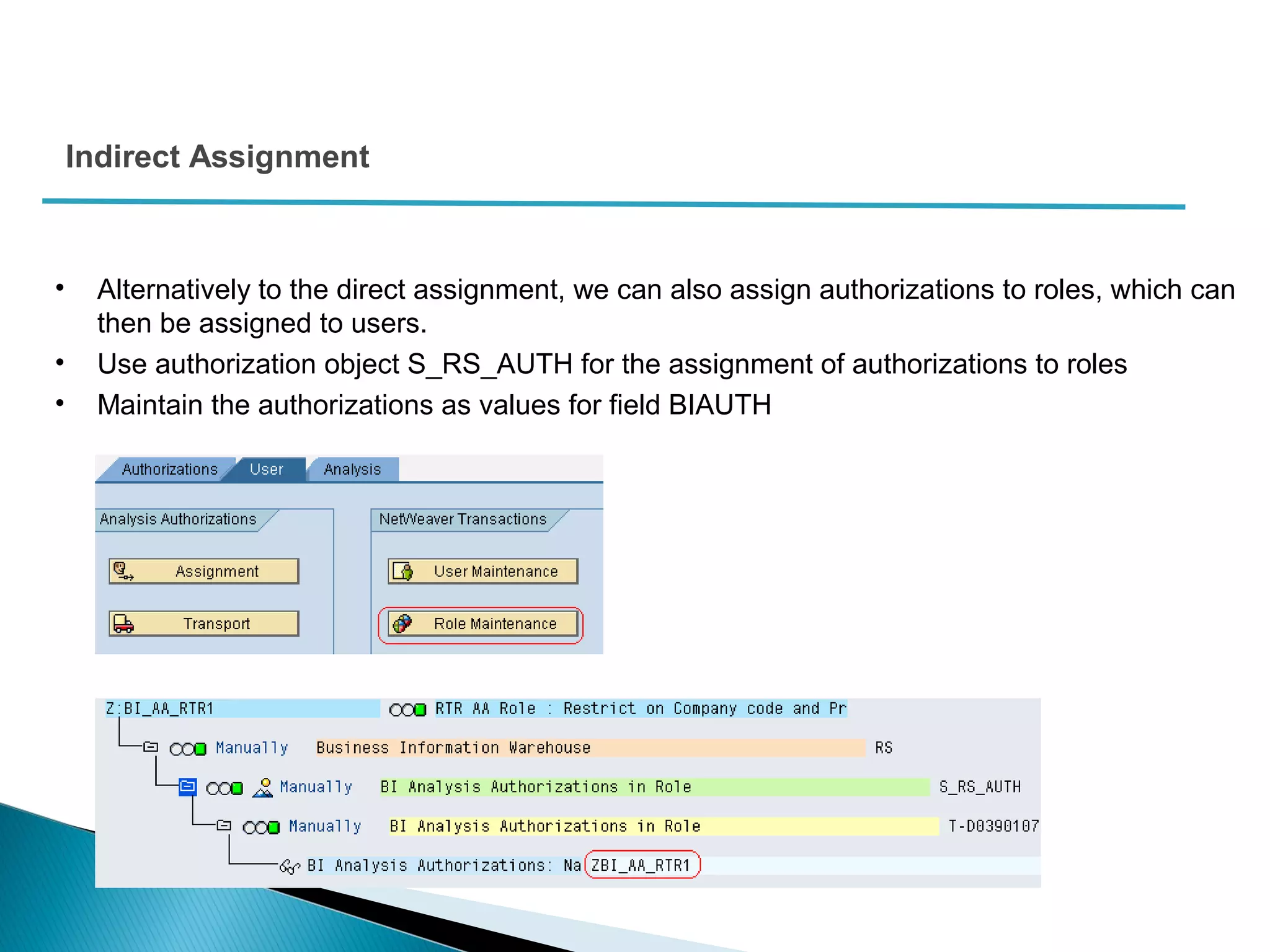
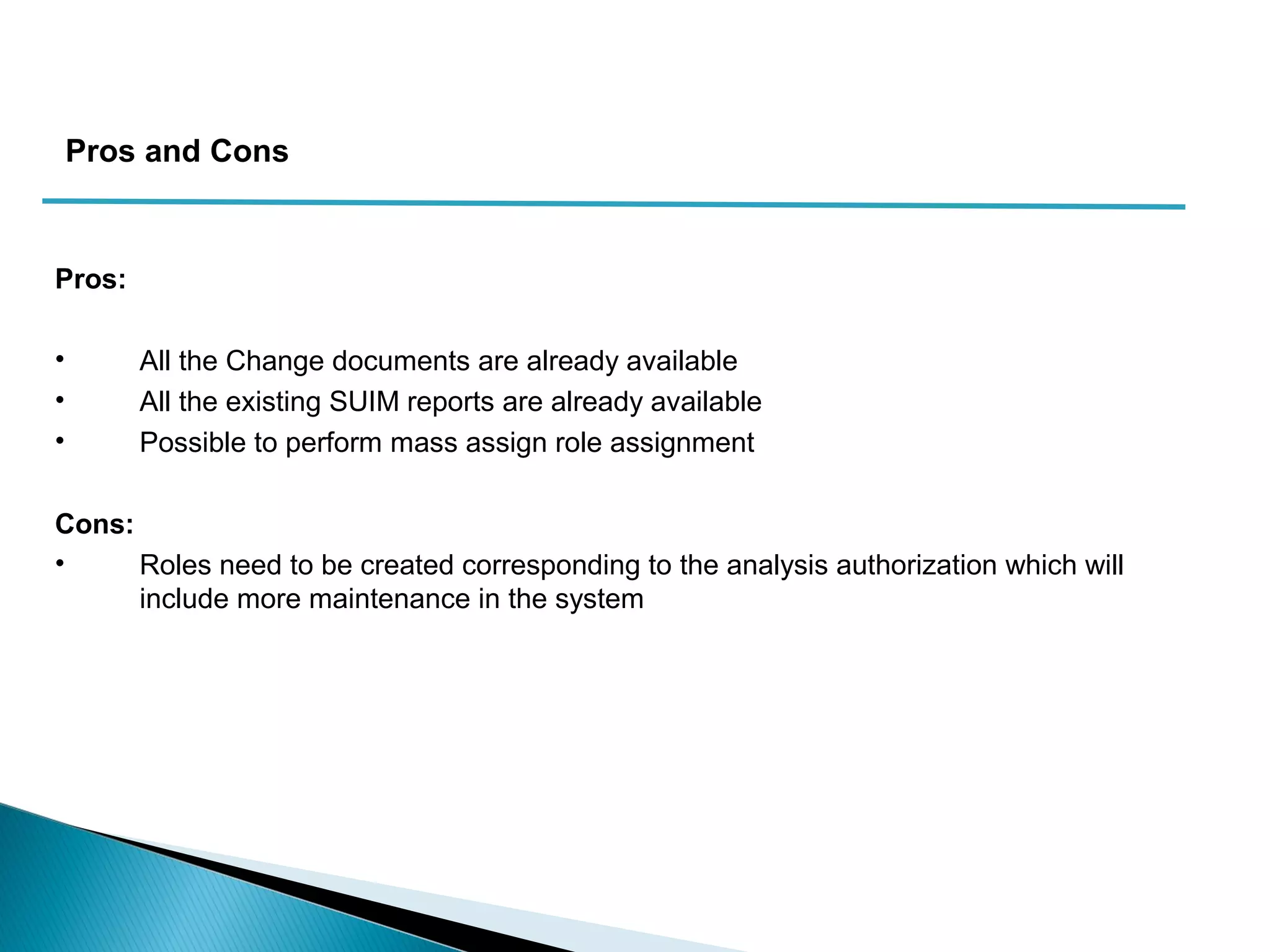
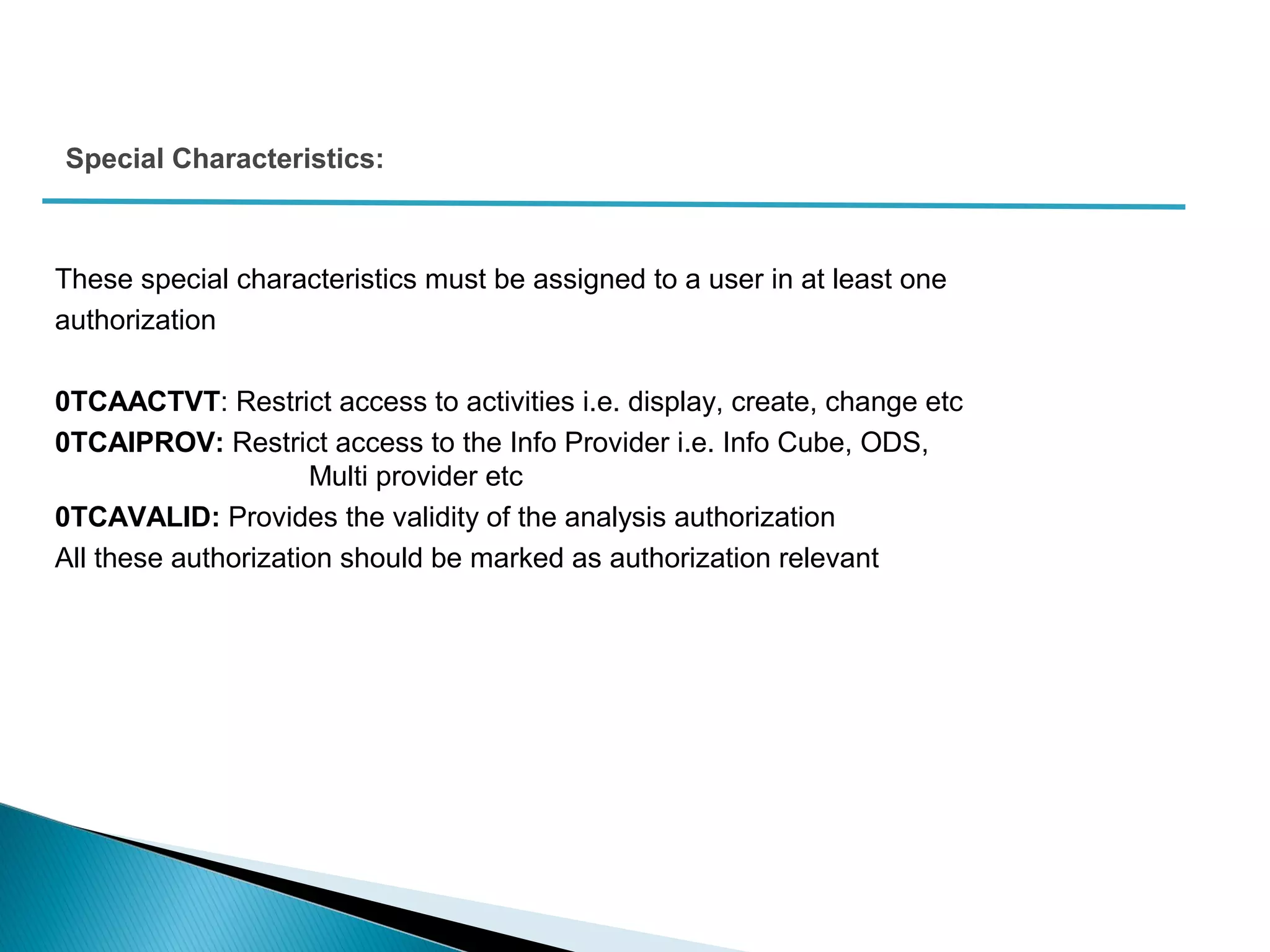
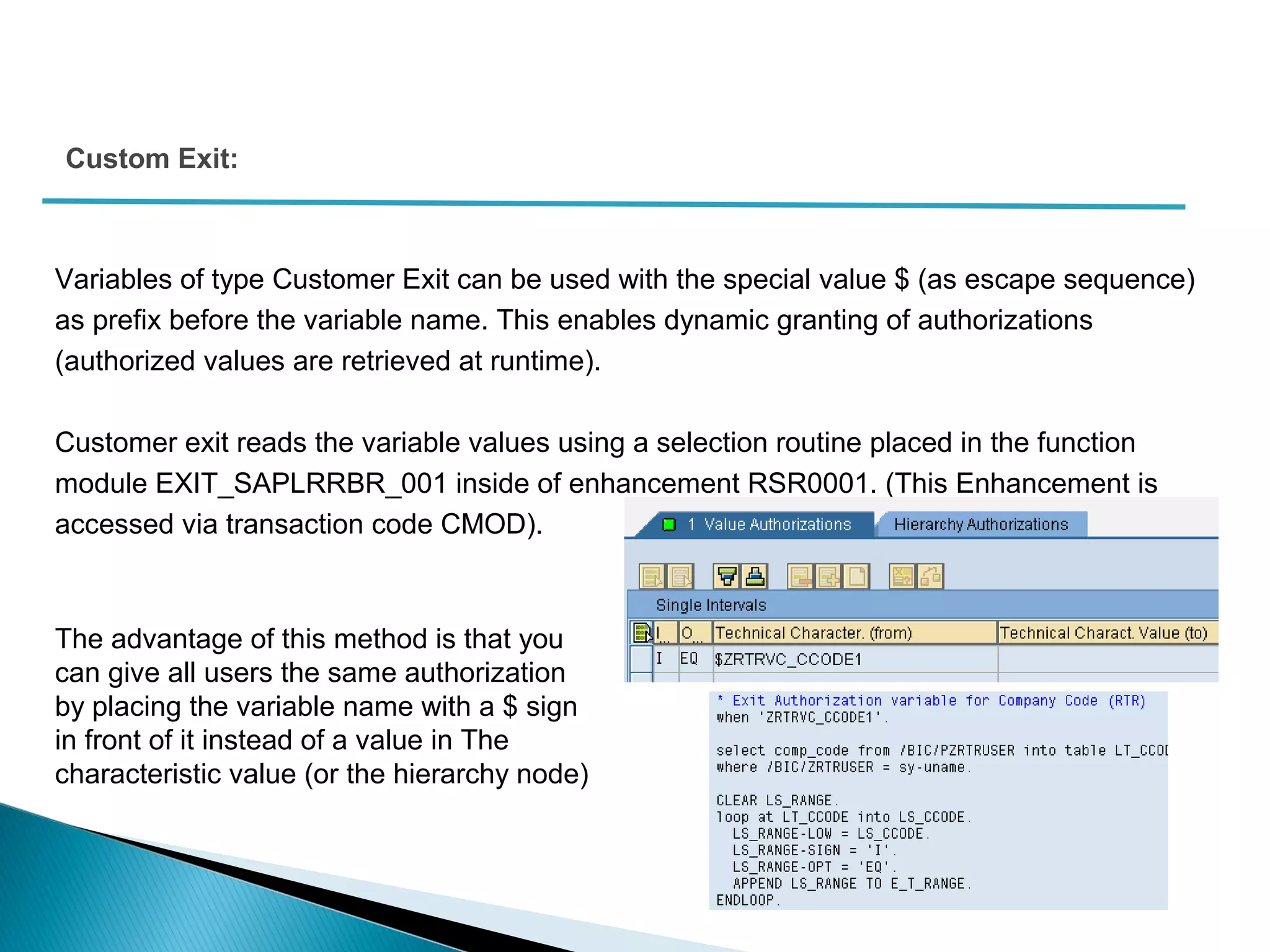
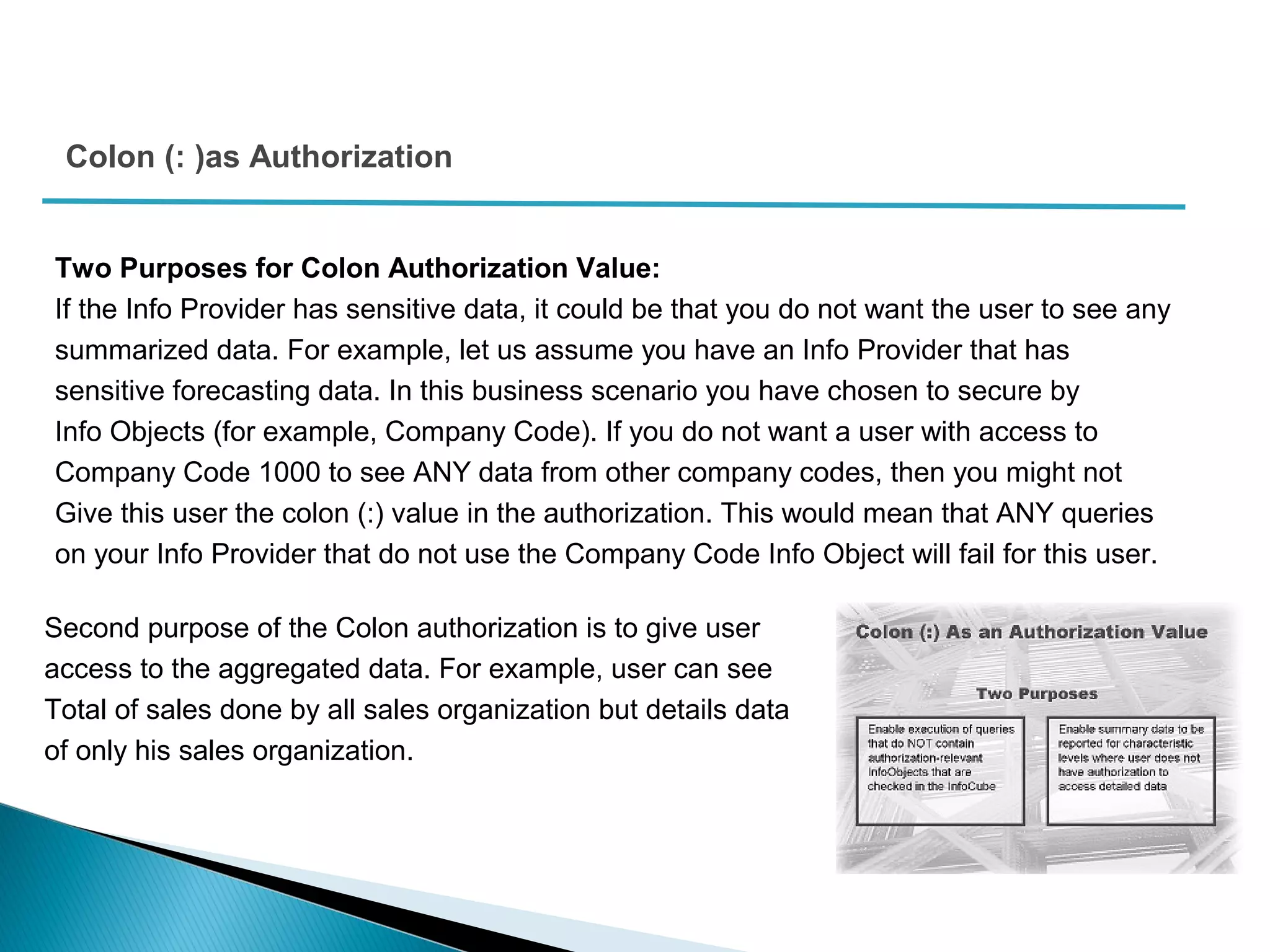
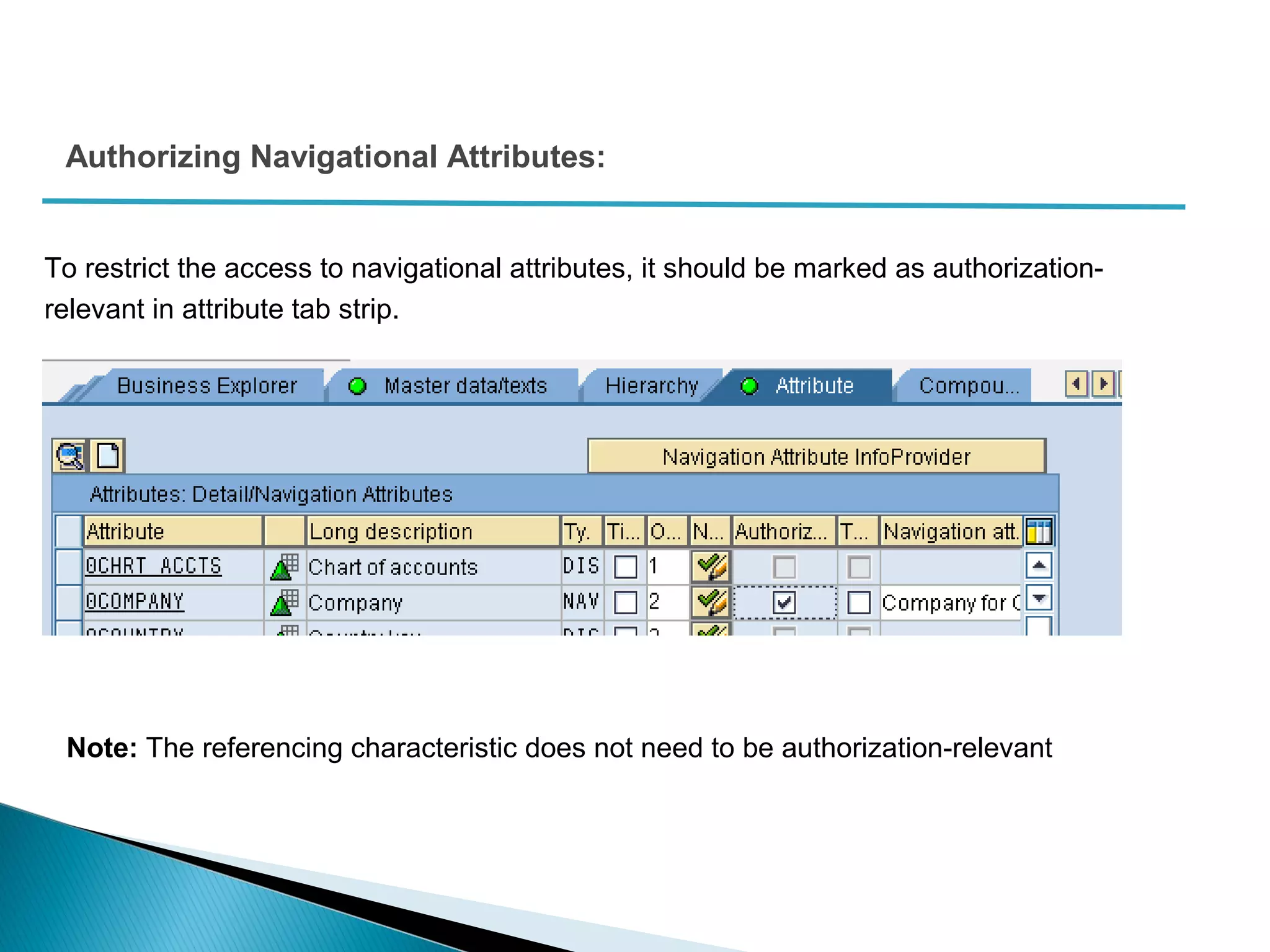
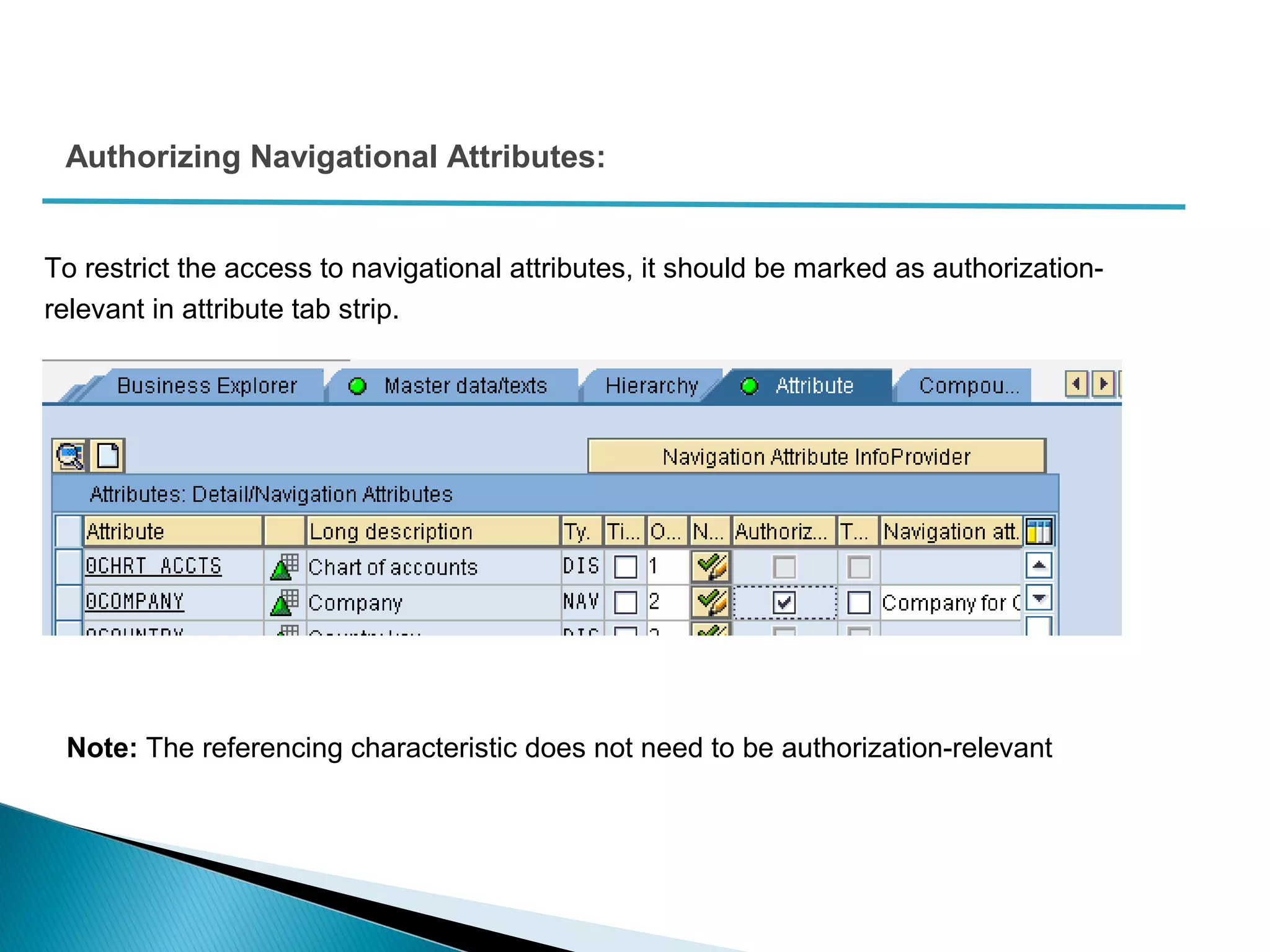
The document discusses various security concepts in SAP BI 7 including differences from BW 3.x, restricting reporting user access, authorization trace, creation and assignment of analysis authorizations, securing access to workbooks, additional security features in BI 7 like analysis authorizations and new authorization objects. It provides details on securing data access at different levels like InfoCube, characteristic, and key figure and describes options for securing data access like using queries or info objects.